
Major Cyberattacks Targeting Cryptocurrency & NFT Industry
The volatility of Bitcoin’s value and the wider cryptocurrency market not only draws traders and investors but also entices a variety of threat actors eager to exploit this lucrative space. From ransomware gangs and APT groups to hacktivists and opportunistic cybercriminals, both individuals and firms in the crypto and NFT industries face relentless targeting. As adoption grows, many users—particularly newcomers—lack the expertise to protect their assets effectively, while firms often struggle to keep pace with the rapidly evolving threat landscape, leaving critical systems and platforms exposed.
Dark web forums further amplify these risks, offering tools like phishing kits, exploit packages, and vulnerability disclosures that make it easier to attack wallets, exchanges, and decentralized platforms. For attackers, the billions of dollars circulating in cryptocurrencies and NFTs represent an irresistible opportunity, with quick and high-value payoffs fueling their operations.

A cybercriminal targeting blockchain and a victim losing hacked cryptocurrency, symbolizing digital asset vulnerability. (Generated By DALL-E)
The risks are staggering. According to SlowMist, a blockchain security firm, 2024 alone saw over 410 incidents in the sector, leading to losses exceeding $2 billion. Though fewer breaches occurred compared to the previous year, the financial impact remains immense. This highlights the increasing sophistication of cyberattacks targeting the industry, underscoring the need for proactive security measures and heightened awareness.
As the list of major cyberattacks against crypto and NFT firms grows, it serves as a critical reminder: whether for individuals or organizations, vigilance and robust preparation are essential to safeguarding the future of these industries in an ever-hostile digital landscape.
Key Threats Facing the Cryptocurrency and NFT Industry
1. Ransomware Attacks
Ransomware groups frequently target firms in the crypto industry due to the ease of demanding and transferring ransom payments in digital currencies. These attacks can paralyze operations, with attackers often threatening to release sensitive data or halt trading platforms unless their demands are met.
2. Advanced Persistent Threats (APTs)
State-sponsored APT groups are increasingly targeting cryptocurrency platforms and NFT marketplaces. These groups use sophisticated techniques to infiltrate systems, often with long-term objectives such as stealing intellectual property, acquiring digital assets, or even destabilizing financial ecosystems.
3. Dark Web Enablement
The dark web serves as a marketplace for tools, services, and intelligence that enable attacks on the crypto industry. Phishing kits, credential dumps, and exploit disclosures make it easier for both novice and experienced attackers to target firms and individuals.
4. Phishing and Social Engineering
Hackers often use phishing emails, fake websites, or social engineering tactics to deceive employees or users into revealing private keys, credentials, or approving unauthorized transactions. These methods are simple yet highly effective, particularly against firms without rigorous employee training programs.
5. Smart Contract Exploits
Vulnerabilities in smart contracts, which underpin most decentralized applications and NFT marketplaces, are a major risk. Attackers exploit flaws in coding to drain funds, manipulate prices, or disable platforms.
6. Insider Threats
Employees with privileged access to systems can pose a significant risk, whether intentionally or through negligence. Weak internal controls or disgruntled employees can lead to data leaks, theft of digital assets, or sabotage.
7. Regulatory Non-Compliance
While not a direct cyber threat, failure to comply with regulatory requirements can expose firms to penalties and attacks. Criminal groups often exploit loosely regulated platforms for money laundering and other illicit activities, increasing reputational and operational risks.
Dark Web and Phishing Threats in the Cryptocurrency and NFT Industry
SOCRadar’s analysis highlights the evolving cyber threats targeting various industries, with the cryptocurrency and NFT sector facing increasing risks.
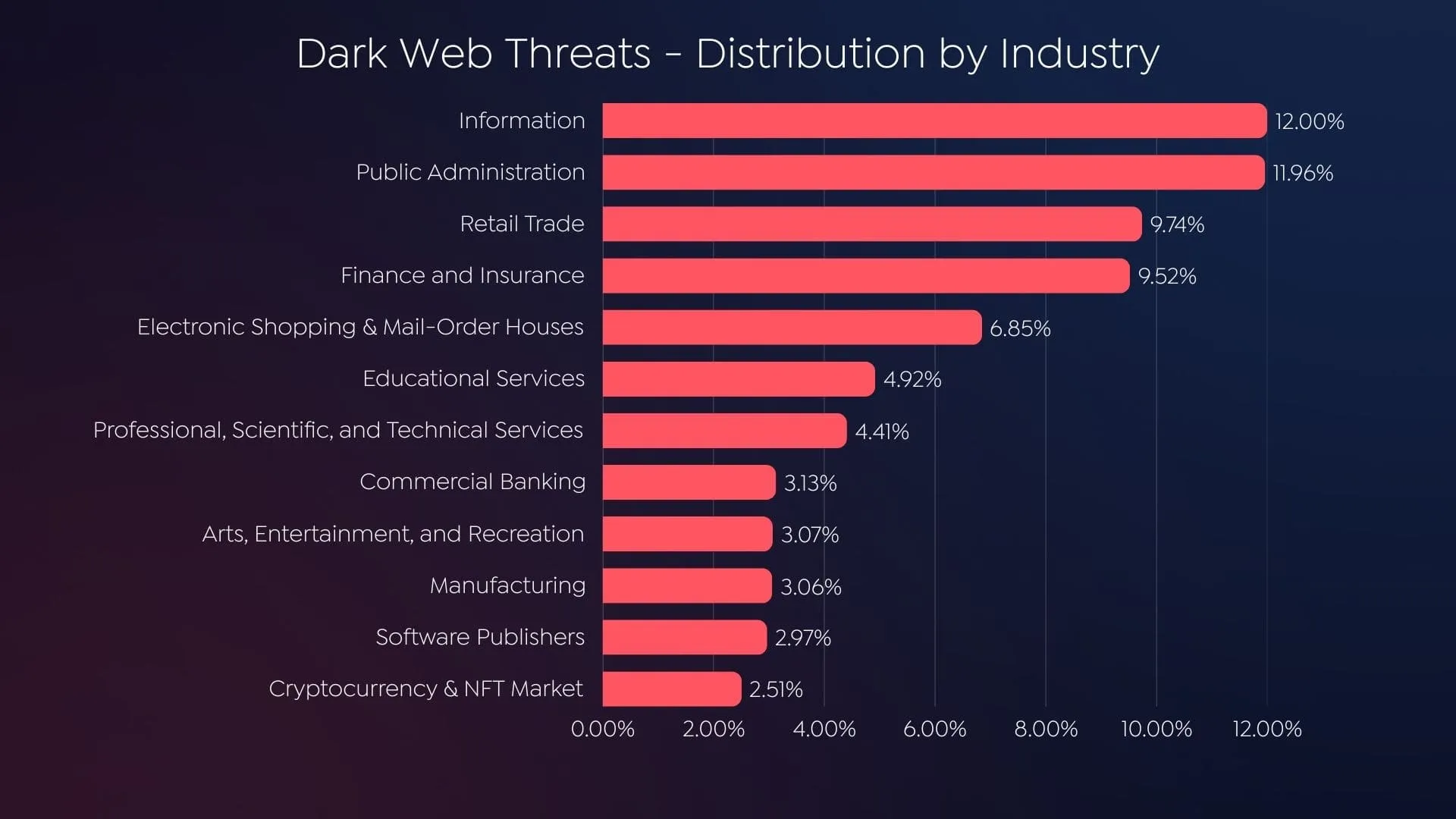
Dark Web Threats – Distribution by Industry 2024 (SOCRadar)
The chart reveals that while sectors like information services (12.00%) and public administration (11.96%) dominate dark web activity, the cryptocurrency and NFT market, accounting for 2.51%, remains a notable target. Tools such as phishing kits, exploit packages, and shared vulnerabilities circulating on dark web forums are critical enablers for attacks on crypto platforms and users.
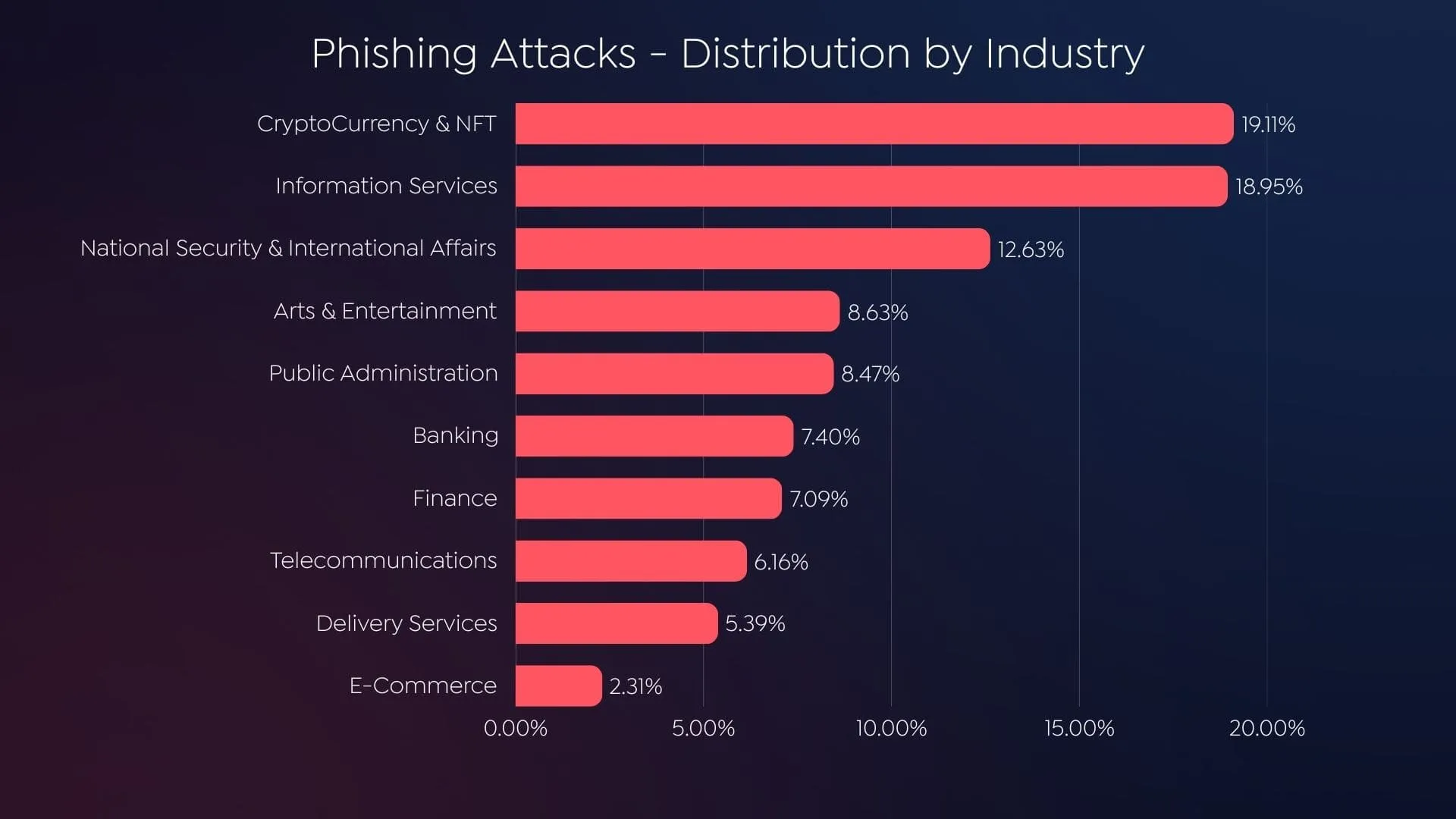
Phishing Attacks – Distribution by Industry 2024 (SOCRadar)
Phishing attacks paint an even clearer picture of the threat landscape. According to the second chart, the cryptocurrency and NFT industry stands as the most targeted sector, accounting for 19.11% of phishing incidents. This surpasses even traditionally high-risk sectors like information services (18.95%) and national security (12.63%). Attackers exploit the decentralized nature of cryptocurrencies, targeting both individuals and firms to compromise wallets and trading platforms for financial gain.
SOCRadar’s findings underscore the urgency for action. As threat actors ramp up their efforts, businesses in the cryptocurrency and NFT space must strengthen their defenses. Proactive measures, including advanced threat intelligence, phishing awareness, and enhanced security protocols, are essential to staying ahead of these persistent attacks and protecting the digital asset ecosystem.
The Most Significant Cyberattacks Shaping the Cryptocurrency and NFT Landscape
The Ronin Network Hack: A Turning Point in DeFi Security
In March 2022, the Ronin Network, a critical blockchain infrastructure for the popular NFT-based game Axie Infinity, fell victim to one of the largest hacks in the history of decentralized finance (DeFi). The attackers exploited vulnerabilities in the network’s security framework to steal approximately 173,600 ETH and 25.5 million USDC, approximately valued at $624 million based on cryptocurrency prices at the time of the breach.

The attack was meticulously planned and executed. It remained undetected for six days until a user reported being unable to withdraw 5,000 ETH from the Ronin bridge. This prompted an investigation that revealed the scale of the breach. The attackers had gained access to five of the nine validator nodes required to approve transactions, exploiting a combination of compromised private keys and lingering permissions.
In late 2021, during a period of high user activity, the Axie DAO allowed Sky Mavis, the parent company of Ronin Network, to sign transactions on its behalf temporarily. Although this program ended in December, the permissions were not revoked. The attackers took advantage of this oversight, compromising Sky Mavis’s systems and generating signatures from the validators to authorize two massive withdrawals.
The Ronin Network hack has been attributed to the Lazarus Group, a state-sponsored hacking group linked to North Korea. U.S. authorities, including the FBI, identified the Lazarus Group as the perpetrators of the breach. The group is known for its sophisticated cyberattacks targeting cryptocurrency platforms, often with the goal of funding North Korea’s sanctioned regime and nuclear weapons program.
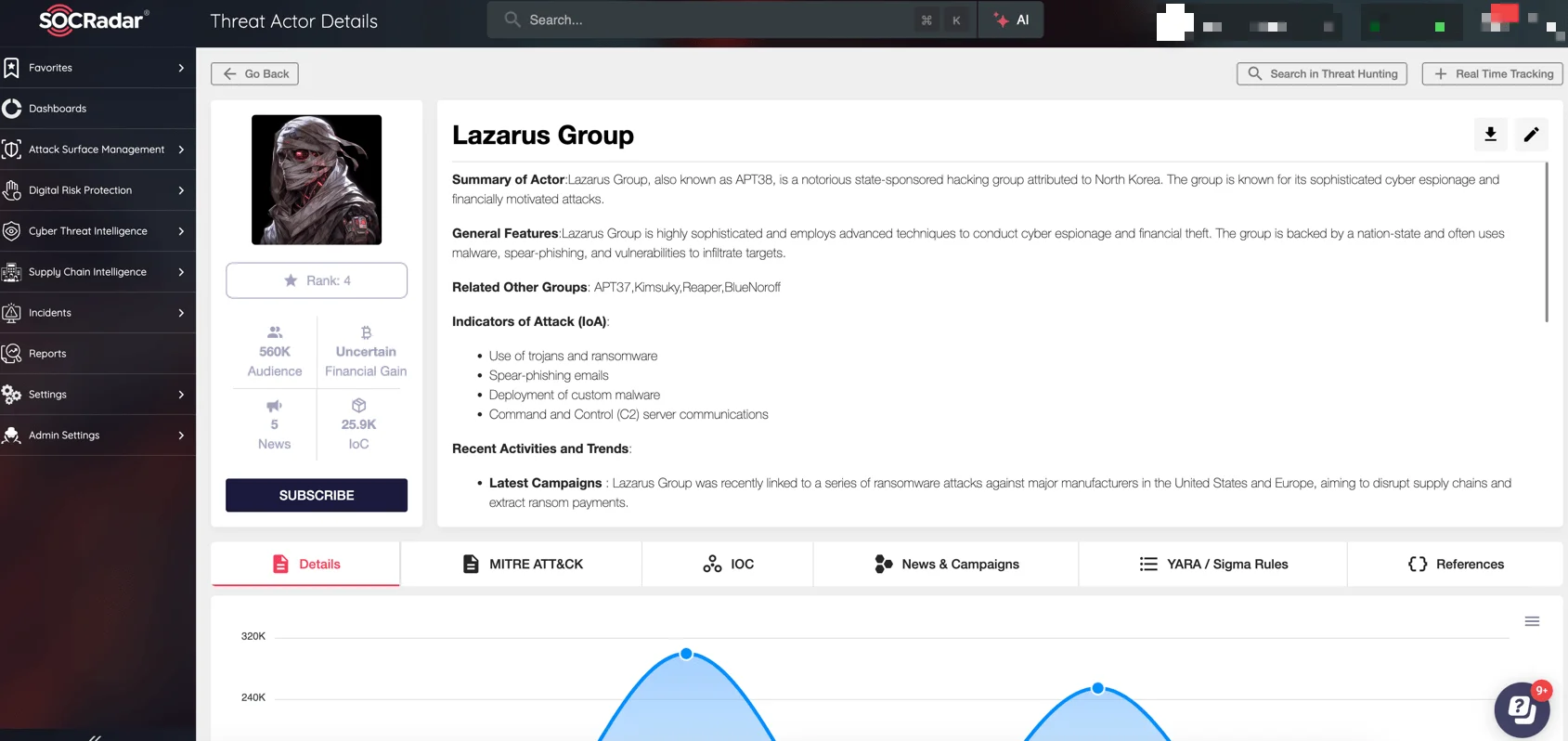
SOCRadar Threat Actor Intelligence
To combat such sophisticated threats, organizations must adopt proactive defense measures, informed by actionable intelligence. SOCRadar’s Threat Actor Intelligence module is designed to meet this need, offering unparalleled insights into the Tactics, Techniques, and Procedures (TTPs) of threat actors targeting the cryptocurrency and NFT industries.
The Poly Network Heist: A $613 Million Cryptocurrency Breach
In August 2021, Poly Network, a decentralized finance (DeFi) platform specializing in cross-blockchain token transfers, experienced a significant security breach. Hackers exploited a vulnerability in the platform’s smart contract system, resulting in the unauthorized transfer of approximately $613 million worth of digital assets to three private wallets.

The stolen funds encompassed over 12 different cryptocurrencies, including Ether and Bitcoin derivatives. Within 48 hours of the incident, the attackers began returning the assets, claiming their intent was to “expose vulnerabilities” in the platform. Poly Network addressed the individual as “Mr. White Hat” but refrained from confirming the hacker’s stated motives.
The FTX Breach: A $600 Million Incident Amid Bankruptcy
In November 2022, the cryptocurrency exchange FTX experienced a significant security breach just hours after filing for bankruptcy. This incident, one of the largest in cryptocurrency history, resulted in an estimated $400 to $600 million being siphoned from the platform’s wallets. The timing of the breach heightened concerns over FTX’s security protocols during a critical period of financial uncertainty.

The breach was reportedly executed through SIM swap attacks, a method where attackers impersonate victims to gain control of their phone numbers. This allowed them to intercept multi-factor authentication codes, granting access to FTX accounts. Over several hours, unauthorized transactions drained significant funds from the exchange.
By the end of the breach, approximately $477 million in assets had been confirmed stolen, with some estimates suggesting losses could be as high as $600 million.
The Mt. Gox Breach: A Defining Moment in Cryptocurrency History
In February 2014, Mt. Gox, the world’s largest Bitcoin exchange at the time, abruptly ceased operations, revealing a devastating security breach that shook the cryptocurrency industry. Approximately 850,000 Bitcoins, valued at hundreds of millions of dollars then, were lost. This included 740,000 Bitcoins belonging to customers and 100,000 owned by the company itself. While 200,000 Bitcoins were later recovered in an old wallet, the majority of the stolen assets remained missing.

The breach was not an isolated incident but the culmination of years of vulnerabilities, with hacking activities traced back as early as 2011. Over this period, Mt. Gox suffered multiple breaches, yet systemic issues in its management left these losses undetected until it was too late. Critical lapses, such as unencrypted private keys and a lack of robust security protocols, made the exchange highly susceptible to theft.
When the full extent of the breach became apparent, Mt. Gox filed for bankruptcy, leaving thousands of customers without access to their funds. The incident exposed the dangers of poor management and inadequate security measures in cryptocurrency exchanges, serving as a stark reminder of the risks in the early stages of digital finance.
The Mt. Gox breach remains a pivotal moment in cryptocurrency history, highlighting the need for stringent security practices, regulatory oversight, and transparent operations to build trust in the growing digital asset ecosystem.
The Bitfinex Breach: A Landmark Loss in Cryptocurrency
In August 2016, the Bitfinex cryptocurrency exchange was breached, resulting in the theft of 119,756 Bitcoin valued at $72 million. Hackers exploited vulnerabilities to execute unauthorized transactions, transferring the funds to a single wallet. The breach caused a sharp drop in Bitcoin’s value and exposed security flaws even in exchanges using advanced protection measures like multi-signature security.

After the breach, small amounts of the stolen Bitcoin were moved to the Dark Web for laundering. Initially, funds were sent to the marketplace AlphaBay, a platform for illicit goods and services. When AlphaBay was shut down by international law enforcement, the laundering shifted to Hydra, another Dark Web marketplace. These movements complicated efforts to trace and recover the stolen Bitcoin but also provided investigators with critical leads as transaction logs and marketplace data were uncovered during law enforcement operations.
These dark web activities underscore the persistent and evolving threats facing the cryptocurrency and NFT industries. To gain a deeper understanding of these risks, including trends in dark web-enabled attacks, phishing campaigns, and compromised data patterns, we invite you to explore SOCRadar’s 2024 Cryptocurrency & NFT Threat Landscape Report. This detailed report offers actionable intelligence and practical recommendations to help organizations strengthen their defenses and stay ahead in the dynamic digital asset ecosystem.

SOCRadar’s 2024 Cryptocurrency & NFT Threat Landscape Report
The Coincheck Breach: A $534 Million Loss in NEM Tokens
On January 26, 2018, Coincheck, a major cryptocurrency exchange, experienced one of the largest breaches in cryptocurrency history. Approximately $534 million worth of NEM tokens were stolen after hackers exploited vulnerabilities in the exchange’s security infrastructure.

The breach began at 2:57 AM local time but went undetected for over eight hours, allowing hackers to transfer 523 million NEM tokens from Coincheck’s hot wallet—a type of wallet connected to the internet and more vulnerable to attacks. The delay in detection and the decision to store such a large amount of assets in a hot wallet drew widespread criticism.
Investigations revealed significant lapses in Coincheck’s security practices, including a reliance on hot wallets rather than more secure cold wallets and insufficient staffing to maintain robust security protocols.
The Euler Finance Breach: A $197 Million Flash Loan Exploit
On March 13, 2023, Euler Finance, a decentralized finance (DeFi) protocol on Ethereum, suffered a devastating flash loan attack, resulting in the theft of approximately $197 million. The hackers exploited a vulnerability in Euler’s liquidity mechanics, taking advantage of inconsistencies in the platform’s token-burning function. This allowed them to manipulate collateral and debt ratios, draining funds in USDC, wBTC, stETH, and DAI.
The attack was enabled through Tornado Cash, which the hackers used to fund gas fees and create contracts for the exploit. They borrowed $30 million in DAI via a flash loan from Aave and deposited $20 million into Euler, generating eTokens as collateral. By repeatedly borrowing and repaying funds, they amplified their returns and siphoned off assets before laundering a portion through Tornado Cash.
In a surprising turn, the hacker, identifying as Jacob, returned the majority of the stolen funds in the weeks following the breach. Over multiple transactions, they refunded 54,000 ETH and $10 million in DAI, accompanied by encrypted messages apologizing for the attack. On April 4, Euler Finance announced the completion of its community investigation and shared plans to restore affected user assets.
The Euler Finance breach underscores the ongoing risks of flash loan attacks and the vulnerabilities in DeFi protocols. It also highlights the importance of enhanced security mechanisms to protect user funds and maintain trust in decentralized ecosystems.
DMM Bitcoin Breach: A $300 Million Cryptocurrency Loss
On May 31, DMM Bitcoin, a cryptocurrency exchange based in Japan, experienced a major breach resulting in the theft of approximately $305 million worth of Bitcoin (48 billion yen). The exchange took immediate action to secure its platform and initiated an investigation to uncover the breach’s cause.

To mitigate further risks, DMM Bitcoin restricted new account registrations, paused cryptocurrency withdrawals, and limited trading activities to selling and settlement orders. Withdrawals of Japanese yen were also delayed as part of the precautionary measures. The exchange apologized to its users and committed to restoring services once enhanced security measures were implemented.
Analysts tracking the stolen funds reported that the Bitcoin was distributed across multiple wallets now under surveillance. If verified as a coordinated theft, this breach would be among the largest in cryptocurrency history. Experts suggest such attacks often exploit weaknesses in security systems or platform vulnerabilities.
DMM Bitcoin has pledged to replenish the stolen funds with support from its partners, emphasizing the critical need for strong security practices to protect digital assets and uphold trust in cryptocurrency exchanges.
WazirX Breach: $230 Million Lost in a Major Cryptocurrency Incident
In July 2024, WazirX, a prominent cryptocurrency exchange in India, confirmed a significant security breach that resulted in the theft of $230 million in digital assets. The attack targeted a multi-signature wallet managed with external custody infrastructure, exploiting a vulnerability in the transaction process to gain unauthorized control over the funds.

Initial findings revealed that the breached wallet had been created outside the core ecosystem of the custody provider, with no impact on wallets managed internally. Analysts reported that the stolen assets were quickly converted into Ether using decentralized platforms, with some suggesting similarities to previous incidents linked to well-known threat actors. These patterns have raised concerns about the growing sophistication of such attacks in the cryptocurrency space.
In response, WazirX implemented immediate measures, including suspending trading activities, notifying regulatory bodies, and launching a bug bounty program. The exchange is offering a 10% reward for actionable intelligence that could lead to the recovery of stolen assets. This proactive approach underscores WazirX’s commitment to addressing the breach and enhancing platform security.
BingX Breach: Over $44 Million Stolen in Crypto Heist
On September 20, 2024, Singapore-based cryptocurrency platform BingX suffered a significant security breach, resulting in the theft of over $44 million in digital assets. The attack, detected through unusual network activity, prompted immediate emergency procedures, including asset transfers to secure funds and safeguard users.

In collaboration with blockchain security firm SlowMist, BingX confirmed losses amounting to $44.7 million, with calculations still underway. Despite the breach, BingX Chief Product Officer Vivien Lin assured users that trading operations remain unaffected. Withdrawals and deposits have been temporarily delayed but are expected to resume within 24 hours. BingX has pledged to cover losses using its capital, minimizing the impact on users and maintaining business continuity.
Unveiling Dark Web Threats to the Cryptocurrency and NFT Industry
The dark web serves as a breeding ground for cybercriminal activities, offering a platform for the sale and exchange of phishing kits, exploit tools, stolen credentials, and detailed vulnerability disclosures. For the cryptocurrency and NFT industry, this underground marketplace poses a persistent and evolving threat.
SOCRadar’s Dark Web News module actively monitors these activities, providing real-time insights into emerging risks before they escalate. By identifying potential threats early, organizations can take proactive measures to safeguard their platforms, users, and assets.
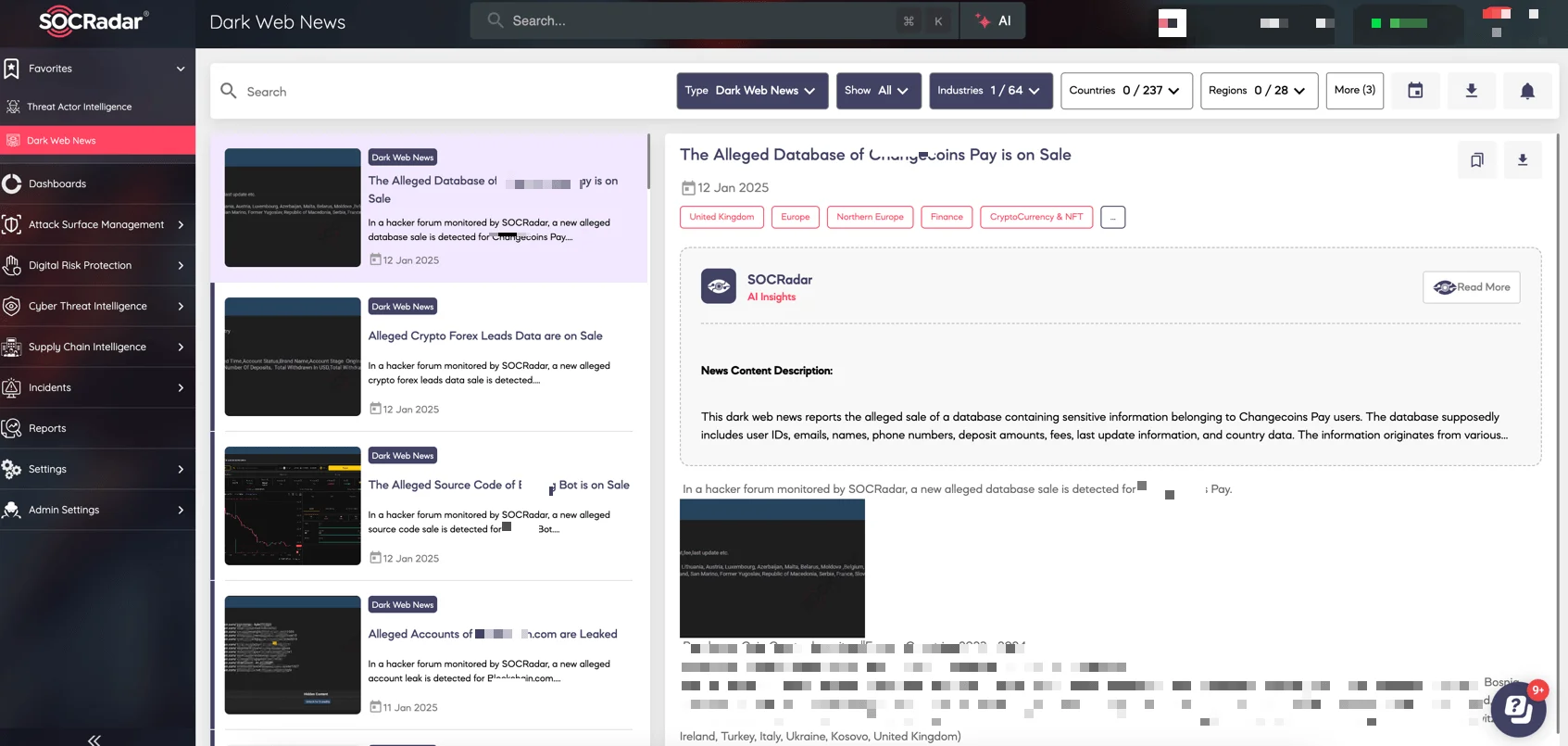
SOCRadar Dark Web News
Let’s dive into some key findings from the dark web that highlight the risks facing the cryptocurrency and NFT sectors.
A New Crypto Drainer Service Targeting the Solana Network
SOCRadar’s Dark Web Team has uncovered a new discussion on a hacker forum, highlighting an alleged crypto drainer service designed to target the Solana network.
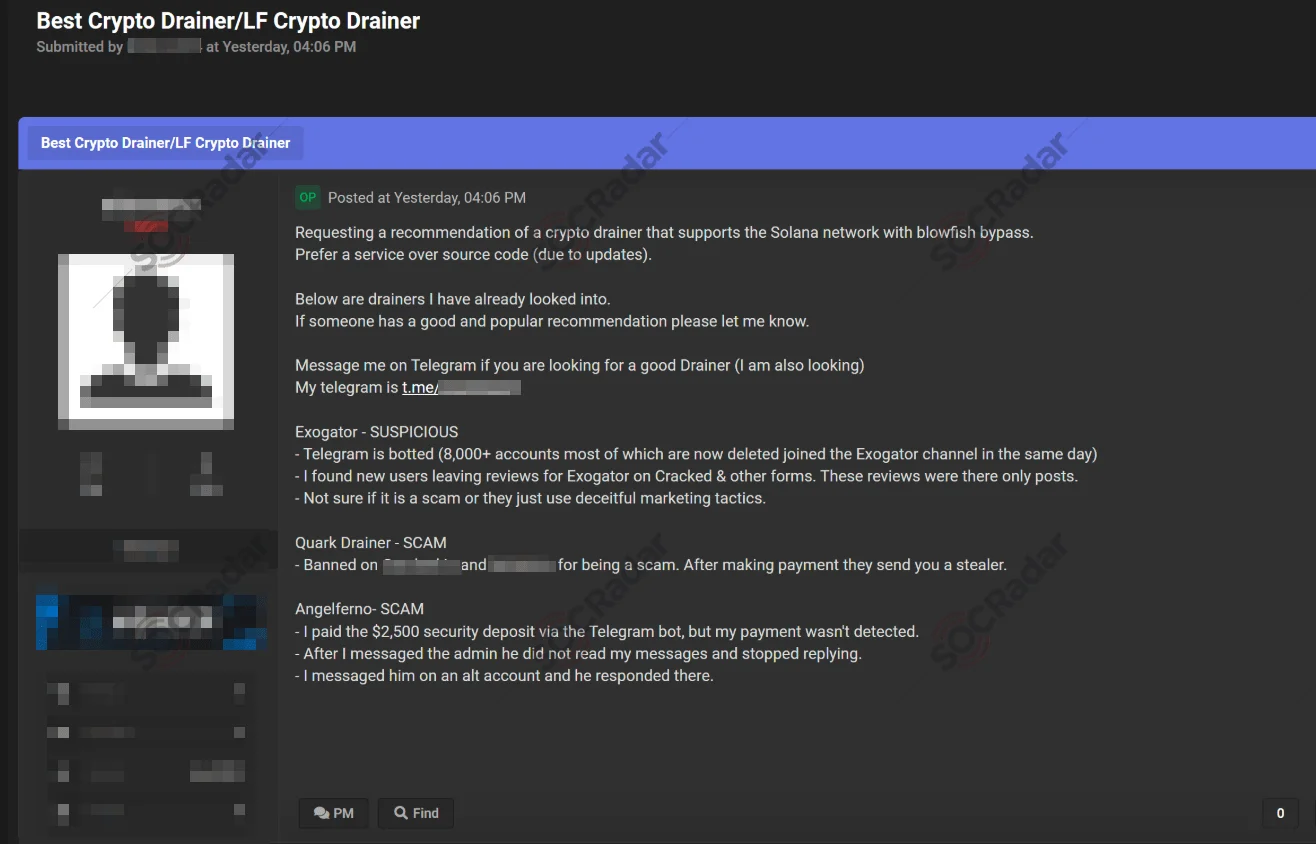
A dark web forum post discussing a crypto drainer service for the Solana network
The post requests recommendations for a reliable drainer service capable of bypassing Blowfish encryption, prioritizing services over source code due to the need for regular updates. This discussion showcases the ongoing demand for tools that enable attackers to steal cryptocurrency with greater efficiency.
Alleged 0-Day Vulnerability Sale Targeting Cryptocurrency Smart Contracts
SOCRadar’s Dark Web Team has identified a new post on a hacker forum advertising the sale of a critical zero-day vulnerability targeting a cryptocurrency’s Ethereum-based smart contract. The seller claims the vulnerability involves reentrancy, a well-known exploit that enables attackers to drain funds from a vulnerable smart contract by taking advantage of improperly sanitized call() functions within the code.
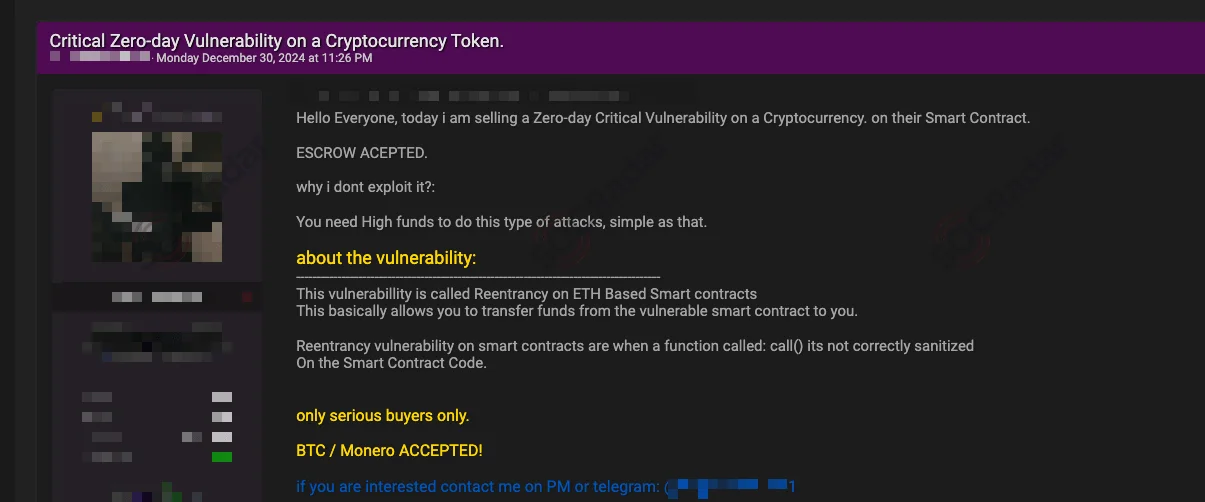
A dark web post offering a critical Ethereum smart contract vulnerability
The post explicitly mentions that the seller is not exploiting the vulnerability due to the need for substantial funds to execute such an attack. Instead, they are offering the exploit for sale, accepting payment in Bitcoin or Monero. To build trust, the seller has also indicated willingness to use an escrow service for the transaction.
Recruitment Post for Crypto Rug Pull Scheme
SOCRadar’s Dark Web Team has uncovered a recruitment post on a hacker forum seeking partners to orchestrate large-scale crypto rug pull scams. The post targets investors willing to contribute at least 1 ETH to fund the launch of fraudulent projects across six blockchain networks: Solana, Base, Tron, Sui, Aptos, and TON.
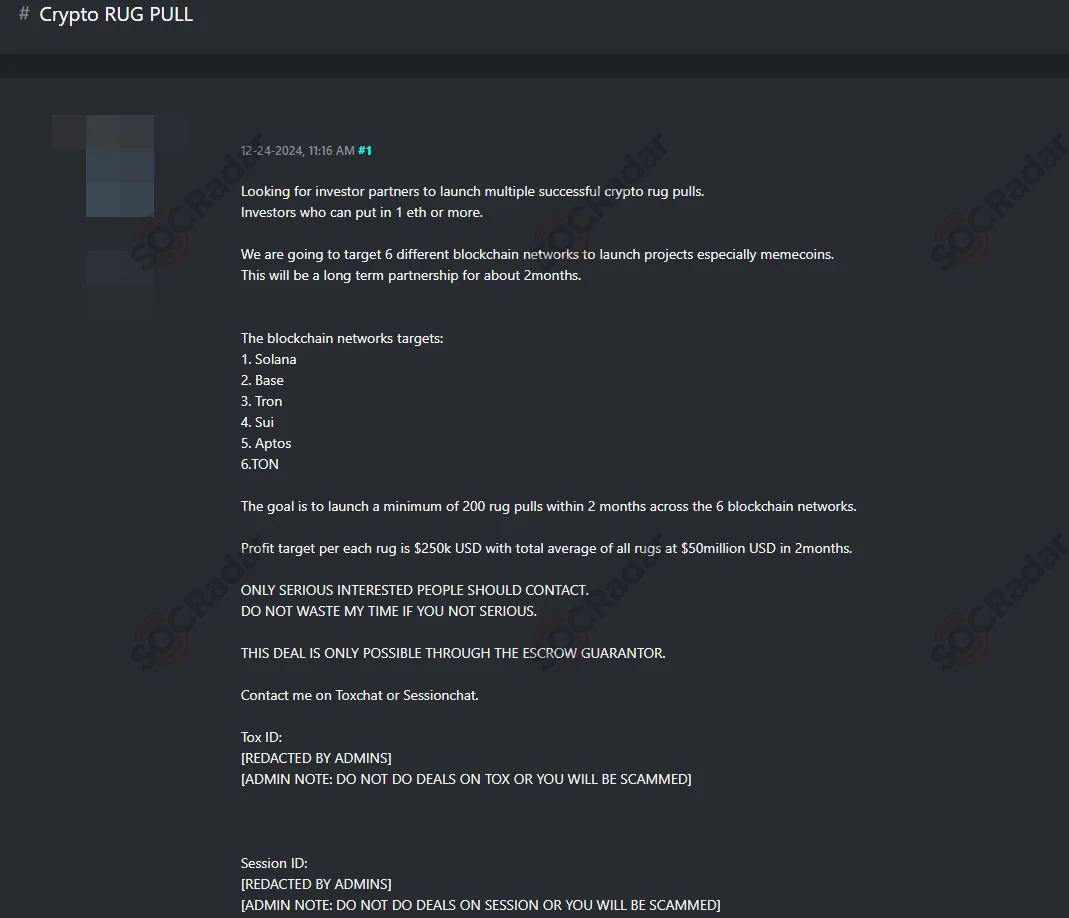
A dark web post recruiting partners for a large-scale crypto rug pull scheme targeting multiple blockchain networks
The scheme aims to execute 200 rug pulls within two months, focusing primarily on memecoins. The post claims a profit target of $250,000 per scam, with an estimated total of $50 million over the campaign duration. The poster highlights the use of escrow services for transactions and requests contact through Toxchat or Sessionchat, despite admin warnings about scams on these platforms.
These developments highlight the escalating risks faced by the cryptocurrency and NFT sectors as cybercriminals increasingly exploit vulnerabilities in blockchain networks, decentralized platforms, and individual user practices. From phishing attacks to sophisticated exploit kits advertised on dark web forums, threat actors are targeting the core of the digital asset ecosystem. With tactics evolving and becoming more sophisticated, the need for proactive measures has never been greater.
SOCRadar Dark Web Monitoring
With SOCRadar Dark Web Monitoring, organizations can stay ahead of these threats. By actively monitoring dark web activity, SOCRadar provides real-time insights into emerging vulnerabilities, malicious tools, and evolving attacker strategies. This intelligence empowers firms to address risks before they escalate, safeguarding digital assets and maintaining trust in the rapidly growing cryptocurrency and NFT industries.
Key Capabilities of SOCRadar’s Dark Web Monitoring:
- Proactive Threat Detection: Real-time tracking of dark web activities targeting blockchain networks and crypto ecosystems.
- Vulnerability Alerts: Early identification of exploits and tools being shared or sold, enabling timely mitigation.
- Industry-Specific Insights: Focused intelligence tailored to the unique challenges of the cryptocurrency and NFT sectors.
- Actionable Reports: Detailed analysis to support decision-making and enhance incident response efforts.
Stay informed and secure with SOCRadar—your partner in navigating the ever-evolving cyber threat landscape.




































