MalDoc in PDF: A Novel Method to Distribute Malicious Macros
Since Microsoft disabled Macros by default, threat actors have actively experimented with alternative attack methods. They utilize various other file structures to distribute malicious content to their victims. Notably, notorious malware strains like Emotet, QakBot, and IcedID have already leveraged such tactics.
Recently, researchers unveiled a novel technique for evading antivirus detection: embedding a malicious Microsoft Word file within a PDF file. This devious method, coined “MalDoc in PDF” by JPCERT/CC, reportedly featured in an observed real-world attack in July 2023.
How Does the MalDoc in PDF Method Work?
Researchers discovered that MalDoc in PDF files, which combine PDF and Word structures, can open in Word, triggering malicious VBS macros. It works by appending an MHT file from Word with an embedded macro to the PDF object, producing a PDF file that can also be opened in Word.
In simpler terms, these PDFs have a Word document attached, with a VBS macro. If you open them in Microsoft Office as a Word document, the macro designed to download an MSI file can download and execute it.
Security researcher Will Dorman shared his insights on Twitter (X), emphasizing that traditional Macro protections remain intact. When a document is downloaded from the internet or email, it carries a Mark of the Web (MotW), requiring users to manually exit Protected View, only to discover that macros are disabled. See the original Tweet below:
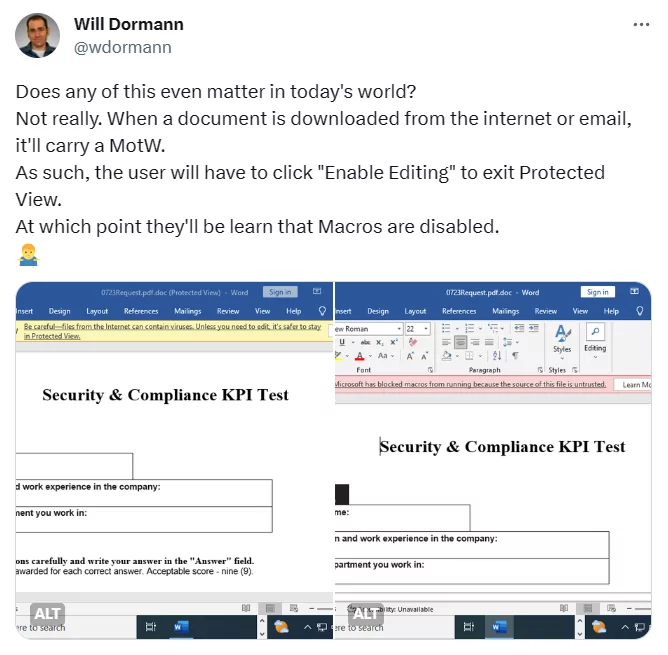
Dormann has also noticed evidence indicating that the MalDoc in PDF method was being tested with a file named “DummymhtmldocmacroDoc.doc” in May.
For more, see this demo video showcasing a MalDoc in PDF attack, provided by JPCERT/CC.
Microsoft to Retire WordPad: Implications for RTF Files
In an announcement on September 1, 2023, Microsoft has declared that WordPad will no longer receive updates and is slated for removal in a forthcoming Windows release.
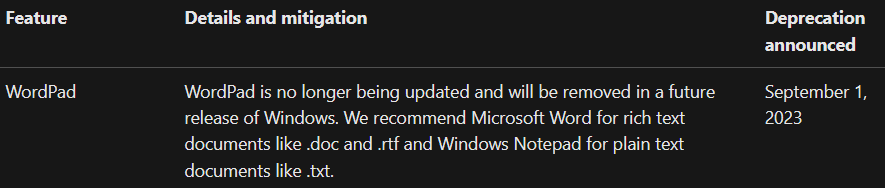
Microsoft’s decision to deprecate WordPad before its 30th anniversary could have significant implications since RTF files will now be opened through Word. The potential for RTF files to contain macros raises concerns about the applicability of macro protection measures to RTF files downloaded from the internet.
For further insights into the potential cybersecurity implications of Microsoft’s decisions, you can also explore our blog post, Microsoft Products as an Attack Vector.
Is the MalDoc in PDF Technique Truly Novel?
While the concept of embedding macros in Word documents within PDFs may appear novel at first glance, it is not an entirely new strategy. A video from eight years ago, for instance, showcases that this approach was in use even then.
This practice is part of a broader category known as polyglots – files that encompass two distinct formats, capable of being interpreted and executed as multiple file types depending on the application handling them.
Although embedding one file type within another has a history, attackers have deployed polyglot files to bypass detection, making this specific technique – MalDoc in PDF – a noteworthy and innovative development, according to JPCERT/CC.
Indicators of Compromise (IoCs)
JPCERT/CC has identified the following indicators of compromise associated with activities involving the MalDoc in PDF method.
Command and Control (C2):
- https[:]//cloudmetricsapp[.]com
- https[:]//web365metrics[.]com
Malware Hash (SHA2-256):
- ef59d7038cfd565fd65bae12588810d5361df938244ebad33b71882dcf683058
- 098796e1b82c199ad226bff056b6310262b132f6d06930d3c254c57bdf548187
- 5b677d297fb862c2d223973697479ee53a91d03073b14556f421b3d74f136b9d
Recommendations
JPCERT/CC researchers mentioned OLEVBA as a countermeasure for MalDoc in PDF attacks. OLEVBA is a malicious Word file analysis tool that outputs the embedded macros. However, it is necessary to detach the Word document from the PDF file to enable analysis by such tool.
Furthermore, practicing safe file usage when downloading from the internet remains paramount. Despite protective measures such as MotW and Microsoft’s default macro disabling, threat actors can still employ social engineering strategies to deceive unsuspecting individuals and employees.
Stay Informed on Cyber Threats with SOCRadar
While it is crucial to educate your staff about recent phishing scams, staying informed about the latest tactics, techniques, and procedures (TTPs) employed by threat actors is equally essential.
To achieve this, you can leverage the SOCRadar platform. SOCRadar continuously monitors threat actors and malware to provide you with actionable insights. By staying updated on the newest cyber threats and TTPs, you can ensure your readiness to counteract them, effectively safeguarding your organization.