Microsoft Exchange Server Vulnerability Trend in 2022
By SOCRadar Research
Microsoft Exchange Server, a widely used email and calendar server for businesses, holds critical information vital to an organization’s functioning. Exchange servers can contain the PII of the users and sensitive data regarding the organization. This wide usage and the sensitivity of the data make it a common vector for threat actors to gain initial access. As it will be investigated in the article moving forward, APTs and ransomware groups were the most active threat actors leveraging from the Exchange Server vulnerabilities. For this reason, in addition to the rise in cyberattacks in recent years, protecting it against potential threats is crucial.
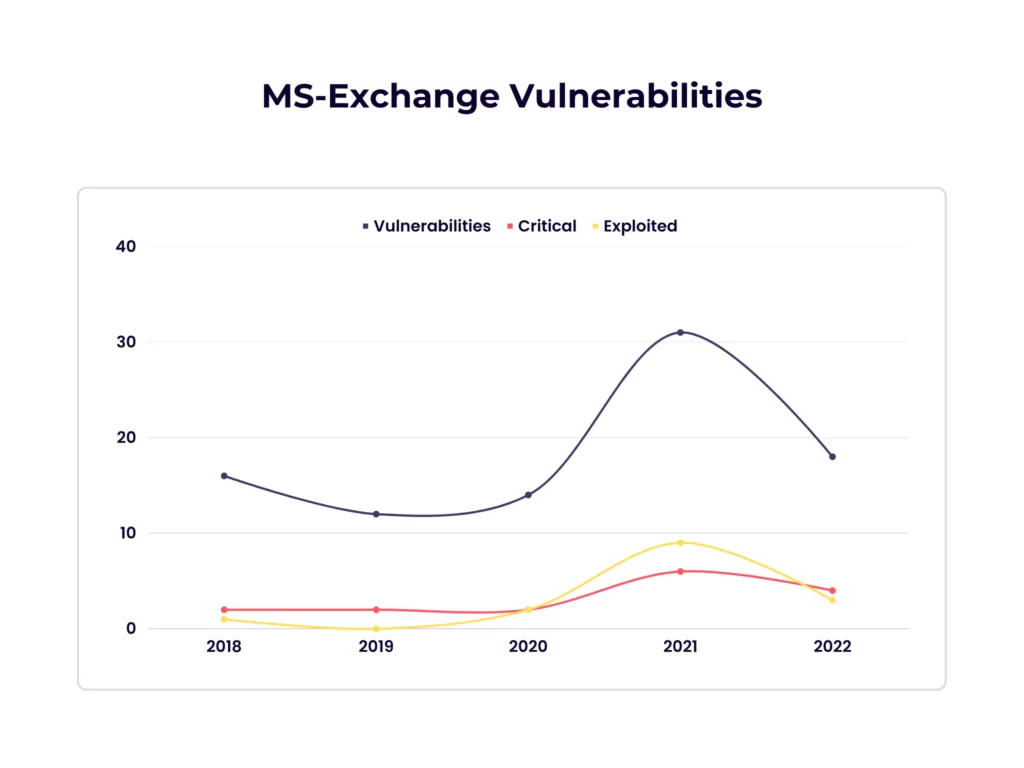
From 2018 to 2022, cybersecurity researchers disclosed 91 Microsoft Exchange Server vulnerabilities. The highest number of vulnerabilities was seen in 2021 (31), but 2022 is the second with 18 recorded vulnerabilities. As seen in the graph below, even though there was a big difference in the number of vulnerabilities between 2021 and 2022, the number of critical vulnerabilities is quite close. Exchange Server users have faced significant challenges with 4 Critical and three known exploited vulnerabilities in 2022.
Overview
While some rely on older, unpatched vulnerabilities, threat actors are increasingly tracking high-profile vulnerabilities and exploiting them to gain an initial foothold in an organization. The timeframe from vulnerability discovery to exploitation is getting shorter – it can practically coincide with revealing the vulnerabilities and the access that can be achieved by exploiting them. According to Gartner’s report, the average time it takes from detecting a vulnerability to emerging an exploit has dropped from 45 days to 15 days in the last decade. The quickness of the threat was seen with Hafnium leveraging the ProxyLogon vulnerability chain to capitalize on vulnerable systems as soon as it was available.
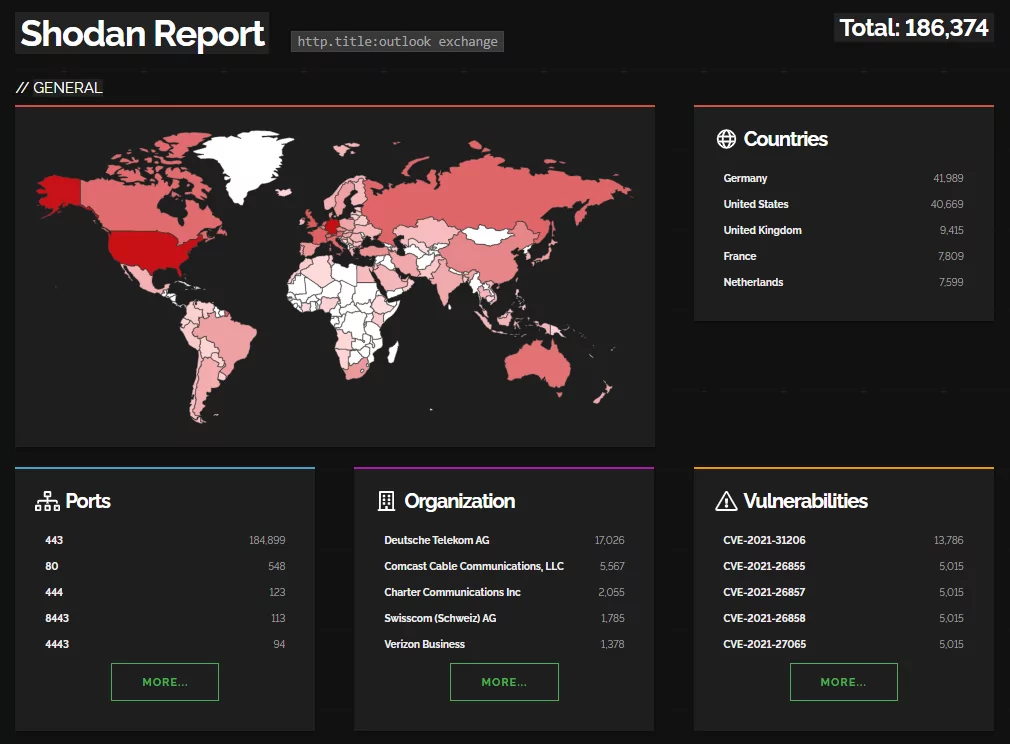
According to Shodan, around 185.000 publicly facing Microsoft Exchange servers with an exposed Outlook web app. Among these, more than 40.000 have vulnerabilities present, and about 25.000 are in the known exploited vulnerabilities (KEV) catalog of CISA.
Unlike the CVE scoring, SOCRadar scores the vulnerabilities dynamically with the SVRS (SOCRadar Vulnerability Risk Score). This system considers elements such as social media, news, code repositories, dark/deep web, attribution with threat actors, and malware to actively score a vulnerability. Below you can see the top vulnerabilities for the Microsoft Exchange Server according to the SOCRadar Vulnerability Intelligence module.
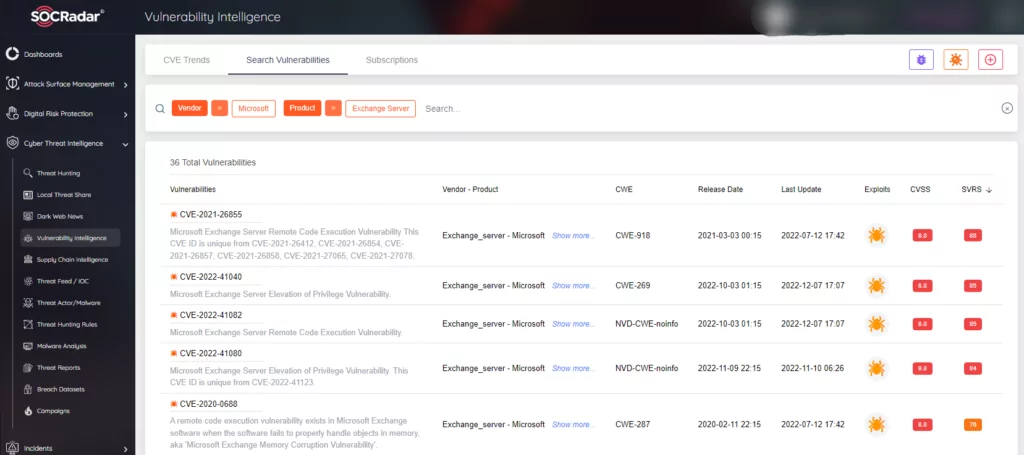
Top Vulnerabilities
According to our analysis and observation, three vulnerability chains stand out among others regarding Microsoft Exchange Server. They have been abused since their disclosure and will probably be abused in the foreseeable future.
ProxyShell
ProxyShell is a chain of attacks that leverage three vulnerabilities in Microsoft Exchange Servers running on-premises. These attacks allow for pre-authenticated remote code execution (RCE). Orange Tsai from the DEVCORE Research Team discovered and made the exploitation chain public. With ProxyShell, a threat actor without authentication can execute arbitrary commands on the Microsoft Exchange Server through an open port 443. You can find an example diagram explaining the vulnerability chain below.
ProxyShell consists of 3 vulnerabilities:
- CVE-2021-34473: Pre-auth Path Confusion leads to ACL Bypass
- CVE-2021-34523: Elevation of Privilege on Exchange PowerShell Backend
- CVE-2021-31207: Post-auth Arbitrary-File-Write leads to RCE
You can check this post by Microsoft to remediate against ProxyShell.
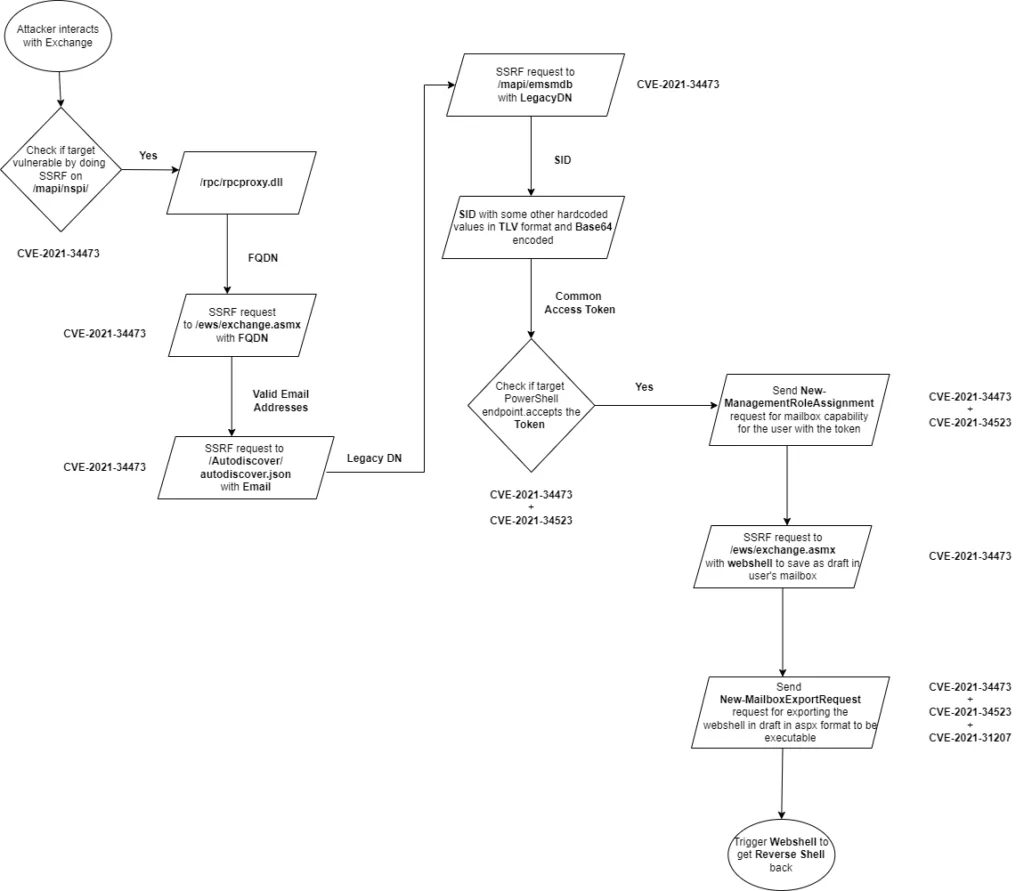
ProxyLogon
ProxyLogon vulnerability refers to four zero-day vulnerabilities found in the Exchange Server. Just as in the ProxyShell, Orange Tsai from DEVCORE uncovered the ProxyLogon. By chaining four vulnerabilities, attackers can execute code remotely on the target and upload a webshell to it. You can find an example diagram explaining the vulnerability chain below.
ProxyLogon consists of 4 vulnerabilities:
- CVE-2021-26855: Server Side Request Forgery (SSRF)
- CVE-2021-26857: Remote Code Execution Vulnerability(RCE)
- CVE-2021-26858 and CVE-2021-27065: Post-auth Arbitrary-File-Write leads to RCE
You can check this post by Microsoft to remediate against ProxyLogon.
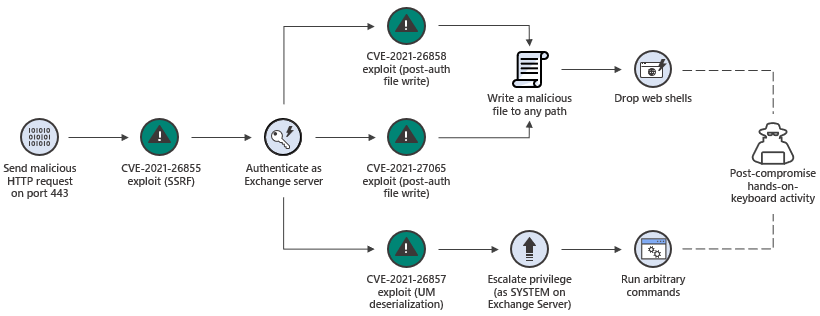
ProxtNotShell
ProxyNotShell was discovered in Microsoft’s exchange server and was put in the category of SSRF with the CVE-2022–41040; along with this, another vulnerability was categorized as RCE with the CVE-2022–41082. The reason it is called ProxyNotShell, named by the researcher Kevin Beaumont, comes from its similarity to ProxyShell. When it was first discovered, researchers thought that it might not be a new zero-day, but after the triage period, Microsoft deemed it as new zero–day. An example diagram explaining the vulnerability chain can be found below.
Microsoft has released an update for the vulnerability, which you can check here.
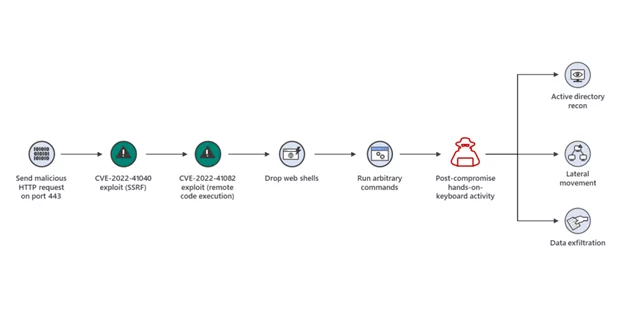
Prominent Activities in 2022
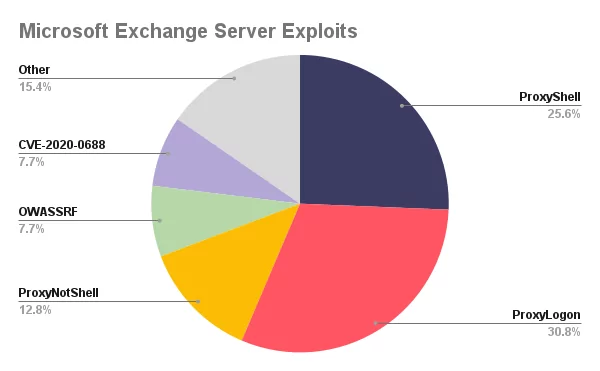
In 2022, there was heaps of malicious activity targeting Microsoft Exchange Server vulnerabilities. The most leveraged ones deducted from the publicly exposed attacks are ProxyShell, ProxyLogon, and ProxyNotShell vulnerability chains. The graph below shows that 69% of the publicly available attacks were managed through these vulnerabilities. In these, only ProxyNotShell was disclosed in 2022. Threat actors were already abusing the other two vulnerabilities before 2022 started.
Vulnerabilities of the Exchange Servers were mostly exploited by APTs and ransomware groups, such as ToddyCat APT, BlackCat, and Play Ransomware groups. These two types of groups conducted most of the attacks observed in 2022. Historically, APT actors have used common but effective tactics ranging from spear phishing, brute force, and exploiting known vulnerabilities to gain initial access to victim networks. With the rise of relatively easy-to-exploit vulnerabilities in 2021 and 2022, threat actors leveraged heavily from the prevalence and easiness of it.
Throughout 2022, SOCRadar Dark Web Team observed multiple instances of sales and posts regarding Microsoft Exchange Server vulnerabilities on the dark web.

A timeline of some of the critical events for the Microsoft Exchange Server can be seen below.
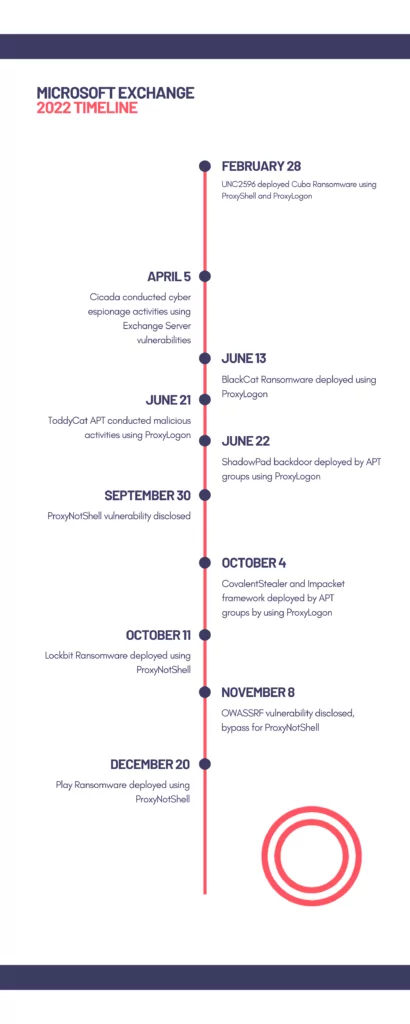
CovalentStealer and Impacket Framework Ssed to Steal Data from US Defense Organization
On October 4, 2022, the U.S. Government released an alert regarding the theft of sensitive data from a US organization in the Defense Industrial Base. The compromise is thought to be lasted for about ten months, and multiple advanced persistent threat (APT) groups likely compromised the organization.
The threat actors combined custom malware called CovalentStealer, the open-source Impacket collection of Python classes, the HyperBro remote access trojan (RAT), and well over a dozen ChinaChopper webshell samples. They most likely exploited the ProxyLogon vulnerability chain to gain initial access to the target.
BlackCat Ransomware Leverages ProxyShell
On April 18, 2022, TrendMicro investigated an incident regarding BlackCat Ransomware. BlackCat (aka AlphaVM or AlphaV) is a ransomware family written in the Rust programming language and operated under a ransomware-as-a-service (RaaS) model. In the examined incident, they identified the exploitation of the ProxyShell vulnerability chain. In addition to TrendMicro’s observations, Microsoft also observed BlackCat leveraging Exchange Server vulnerabilities.
Conclusion
Microsoft Exchange Server is used by millions worldwide. As in the nature of email servers, it is the gateway of organizations to the outside world. It holds critical information, which makes it a valuable target for threat actors, but more significantly, it can serve as initial access for cyber attacks. Because of this, it must be secured. To secure Exchange Server, organizations should implement best security practices as follows.
- Regularly apply security patches. In the case of Exchange Server, Microsoft releases security patches for vulnerabilities in a quick fashion. So, keeping the system updated helps immensely.
- Implement IAM to better manage access to sensitive information.
- Implement monitoring for suspicious activity. In the case of Microsoft Exchange Server, threat actors mostly leverage SSRF vulnerabilities. With proper security monitoring, you can protect against SSRF by blacklisting certain domains and IP addresses.
- Train employees on how to recognize and report phishing emails. In this aid, you can check the suspected emails on SOCRadar Labs Email Analyzer to help deduce whether an email is phishing.
- Most importantly, vulnerabilities should be tracked continuously and taken action if they pose a considerable threat. SOCRadar provides Attack Surface Management which helps gain visibility into external-facing digital assets. With it, security teams can track the vulnerabilities in the environment. Knowing which vulnerabilities are present in the organization can limit the possible attack surface threat actors may exploit.