
Microsoft SQL Servers Infected by the New Malware: Maggie
Maggie has emerged as a brand-new malware. The backdoor has already spread to hundreds of computers and is specifically designed to attack Microsoft SQL servers.
DCSO CyTec analysts found the Maggie malware, and data shows that some nations—including the United States, India, South Korea, and China—have higher distribution rates.
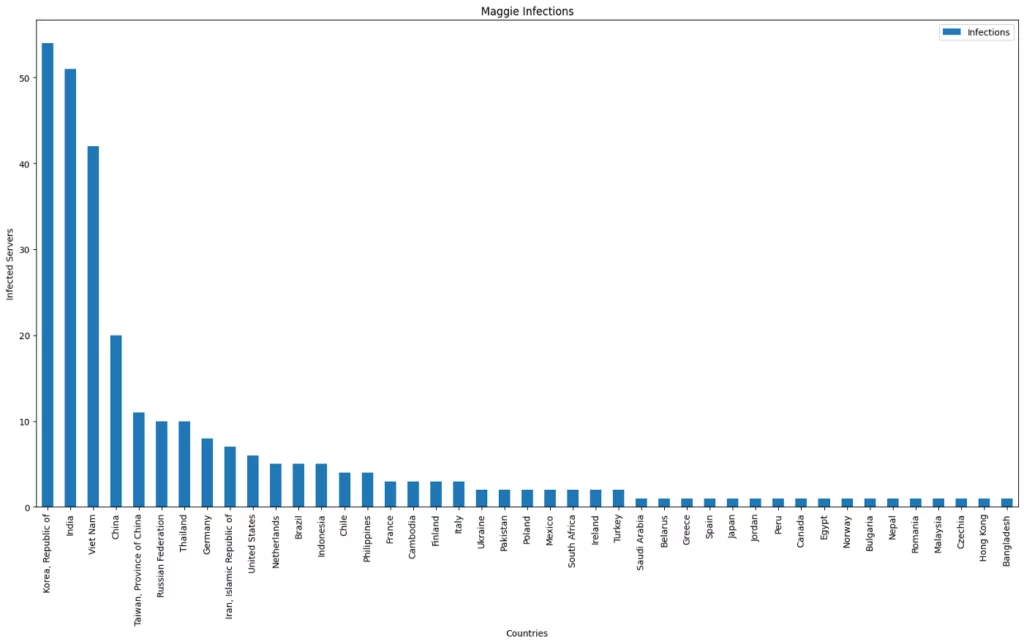
The Maggie’s backdoor user was discovered in 285 servers in 42 countries out of nearly 600,000 servers scanned.
Maggie Malware Capabilities
The malware managed by SQL queries and supports 51 commands, including running programs, executing processes, interacting with files, installing remote desktop services, and configuring port forwarding.
It can brute-force administrator logins to other Microsoft SQL servers with SqlScan and WinSockScan commands. A hardcoded backdoor user is added to the server if it is successful.
The malware also gives instructions for arguments that the attackers could add to some of the commands.
Maggie covers itself as an Extended Stored Procedure DLL (sqlmaggieAntiVirus_64.dll). These files employ an API to allow remote users to make arguments in SQL queries. The file is digitally signed by DEEPSoft Co. Ltd., a South Korean business.
Four exploit commands are also included in the command list:
- Exploit AddUser
- Exploit Run
- Exploit Clone
- Exploit TS
It is suggested that attackers might use some known vulnerabilities. These exploit, the analysts could not test commands since they seem to rely on a DLL that is not included with Maggie.
Maggie as a Network Bridge Head
Because Maggie has TCP redirection ability, it can act as a network bridge head from the Internet to any IP address that the compromised MSSQL server can access.
If the source IP address matches a user-specified IP mask, the malware can reroute any incoming connection (on any port the MSSQL server is listening on) to a previously determined IP and port.
Any connecting IP can utilize the server without any intervention from or knowledge of Maggie, thanks to the implementation’s ability to enable port reuse, which makes the redirection transparent to authorized users.
Maggie also includes SOCKS5 proxy functionality for more complicated network operations.
IoCs
ESP DLLs:
f29a311d62c54bbb01f675db9864f4ab0b3483e6cfdd15a745d4943029dcdf14
a375ae44c8ecb158895356d1519fe374dc99c4c6b13f826529c71fb1d47095c3
eb7b33b436d034b2992c4f40082ba48c744d546daa3b49be8564f2c509bd80e9
854bb57bbd22b64679b3574724fafd7f9de23f5f71365b1dd8757286cec87430
RAR SFX with Maggie:
4311c24670172957b4b0fb7ca9898451878faeb5dcec75f7920f1f7ad339d958
d0bc30c940b525e7307eca0df85f1d97060ccd4df5761c952811673bc21bc794
URLs:
hxxp://58.180.56.28/sql64[.]dll
hxxp://106.251.252.83/sql64[.]dll
hxxp://183.111.148.147/sql64[.]dll
hxxp://xw.xxuz.com/VV61599[.]exe
hxxp://58.180.56.28/vv61599[.]exe
Hardcoded User-Agent:
Mozilla/4.0 (compatible)
File paths:
C:ProgramDataSuccess.dat
Success.dat
Failure.dat
AccessControl.Dat
TTPs
T1110 Brute Force
T1090 Connection Proxy




































