
FARGO Ransomware Targets Vulnerable Microsoft SQL Servers
Microsoft SQL database servers are the target of a new ransomware attack campaign called FARGO ransomware. FARGO, also known as TargetCompany, aims to double-extort victims.
This year’s ransomware attacks against MS-SQL instances included dropping Cobalt Strike beacons and bandwidth theft. Database owners are cautioned about these kinds of attacks because database disruption can severely affect organizations’ management.

About FARGO Ransomware
FARGO is a new variant of the TargetCompany ransomware. Because it used to use a .mallox file extension, it was also known as the Mallox in the past. Midway through June 2021, this crypto-ransomware began to operate. It can spread globally and is aimed at English-speaking people.
The ransomware encrypts the data located on the victim’s computer using a combination of ChaCha20, AES-128, and Curve25519 algorithms. It then displays a message that demands payment in Bitcoin to decrypt the data.
In addition to critical productivity files like .doc, .docx, .xls, and .pdf, the FARGO ransomware will search your computer for pictures, movies, and other media. To prevent you from opening the files, ransomware encrypts them and changes their extension to include .FARGO.
Drive-by downloads, malicious attachments and links in spam emails and messages, untrusted download channels like unofficial and freeware sites, online fraud, cracking tools, and fake updates are some of the distribution techniques that are most frequently used.
You can find a complete list of detections on VirusTotal.
Ransomware Infection
Ransomware infection starts when a vulnerable MS-SQL task downloads a .NET payload using cmd and PowerShell.
The payload’s primary purpose is to fetch the ransomware and malware. It creates a .BAT file in addition, which ends particular tasks.
FARGO ransomware is injected into a Windows process called AppLaunch[.]exe, in which it tries deleting some registry keys and ends other database tasks. It also deactivates recovery with a command.
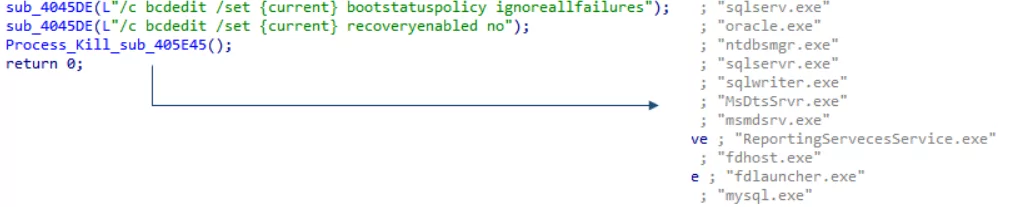
To avoid making a compromised system completely unusable, the FARGO ransomware does not encrypt every directory. Therefore, ransomware does not affect some system directories, boot files, Tor browser, thumbnail database, and some user settings.
The locked files have the .Fargo3 extension. On ransom note, threat actor threatens to leak stolen files on their Telegram channel if the ransom is not paid.
IoCs
MD5:
d687eb9fea18e6836bd572b2d180b144
b4fde4fb829dd69940a0368f44fca285
c54daefe372efa4ee4b205502141d360
4d54af1bbf7357964db5d5be67523a7c
41bcad545aaf08d4617c7241fe36267c
Downloader: hxxp://49.235.255[.]219:8080/Pruloh_Matsifkq[.]png
SHA-1: 0e7f076d59ab24ab04200415cb35037c619d0bae
SHA-256: 863e4557e550dd89e5ca0e43c57a3fc1889145c76ec9787e97f76e959fc8e1e1
Vhash: 015056655d155510f8z73hz2075zabz
Imphash: c8318053dac1b12c686403fde752954c




































