
New Cyber Attack Campaign Bombarding Organizations with Fake Emails and Phone Calls
The cyber threat landscape is always changing, with attackers using new methods to get into organizations and exploit their weaknesses. One campaign that has been in the news lately is the constant sending of fake emails and making phone calls to organizations. In this ongoing cyber attack campaign, showing indicators of groups such as Black Basta and FIN7, threat actors are using tricks to fool people within organizations into giving away important information or letting them in without permission.

An AI illustration of the fake email and call campaign related to Black Basta, FIN7
At its core, this campaign relies on manipulating how people think and trust. Attackers send a lot of fake emails to specific people, filling up their email inboxes and making them feel rushed and overwhelmed. These emails often look like they are from real sources, like co-workers or bosses, which makes it hard for recipients to tell if they are real or dangerous.
Along with the flood of emails, attackers also pretend to be someone else when they make phone calls. They might act like they are from the IT support team or another trusted person within the organization, tricking employees into sharing private information or doing things that hurt security. By using both email and phone calls, attackers have a better chance of succeeding and causing big problems.
It is really important for organizations to know about this cyber attack campaign and do things ahead of time to stay safe. By understanding what tricks attackers use, organizations can more easily find and stop possible dangers. This means teaching employees about the risks that come with fake emails and phone calls, having strong security measures in place, and knowing what to do if something bad happens. The main idea here is to always be watching out and keeping cybersecurity strong so these attacks do not work.
Understanding the Tactics Used
This cyber attack campaign utilizes two primary tactics, namely email overload and phone call impersonation.
Email Overload
The attackers inundate the targeted organizations with a deluge of spam emails, aiming to overwhelm their email systems and individuals’ inboxes.
- Specific techniques involve sending a high volume of seemingly legitimate emails that contain malicious attachments or links. For example, the emails may disguise themselves as important notifications, invoices, or requests for action, enticing recipients to interact with the malicious content.
- By exploiting trust and urgency in these emails, the attackers aim to deceive recipients into unwittingly facilitating unauthorized access to their organization’s systems.
Phone Call Impersonation
In addition to email overload, the campaign employs phone call impersonation as a tactic to exploit human interaction.
- Attackers impersonate trusted entities or authority figures over the phone, manipulating individuals into divulging sensitive information or performing actions that compromise organizational security. For instance, they might pose as IT support personnel or company executives and request login credentials or instruct employees to download and execute malicious files under the guise of system updates.
- This campaign capitalizes on social engineering tactics to establish unauthorized access and gather valuable intelligence from unsuspecting employees.
Impact on Organizations’ Security and Operations
The relentless barrage of spam emails and deceptive phone calls has significant implications for targeted organizations:
- Security Implications: The tactics create an environment ripe for exploitation, potentially leading to unauthorized access, data breaches, and compromise of critical systems.
- According tocyber security statistics, these attacks have been on the rise in recent years.
- Operational Disruption: The sheer volume of incoming emails and calls can disrupt normal operations, overwhelming communication channels and distracting personnel from legitimate tasks.
By understanding these tactics in detail, organizations can better prepare their cybersecurity defenses and equip their personnel with the knowledge needed to identify and thwart such deceptive strategies.
Visit the campaign’s page on the SOCRadar platform for more details (SOCRadar Campaigns)
Examining the Payloads and Techniques
One notable aspect of this campaign is the use of Cobalt Strike beacons. These beacons are versatile tools that allow attackers to establish control over compromised networks and carry out various malicious activities. With Cobalt Strike beacons, threat actors can:
- Gain remote access to systems
- Escalate their privileges
- Move laterally within the network
How the Attack is Carried Out & Communication with Command-and-Control Servers
The attackers use batch scripts to automate tasks on the targeted systems. These scripts are essential for actions like downloading more malware, changing system settings, and hiding their actions to avoid detection.
Additionally, they communicate with Command-and-Control (C2) servers to:
- Receive instructions
- Steal sensitive data
- Maintain control over the compromised environment
Use of a Reverse Shell
Using a reverse shell is a crucial tactic for attackers seeking unauthorized access. It allows them to bypass traditional network security measures and directly control compromised systems through command-line access. This covert method enables threat actors to:
- Run any commands they want
- Increase their privileges
- Gather information without raising suspicion
By understanding these payloads and techniques thoroughly, organizations can improve their ability to detect threats and strengthen their defenses against similar cyber attacks. It is essential for cybersecurity professionals to stay updated on the changing strategies used by threat actors in order to effectively manage risks and safeguard digital assets.
Possible Actors Behind the Campaign: Black Basta and FIN7
The ongoing cyber attack campaign targeting organizations through fake emails and phone calls has raised questions about the possible actors behind these malicious activities.
One avenue of exploration is the examination of indicators associated with the Black Basta ransomware. This ransomware has been known for its double-extortion model, encrypting systems and exfiltrating data for leverage. The campaign under scrutiny shares similarities with the Black Basta attack patterns, prompting researchers to investigate any potential connections.
Based on the analysis of attack patterns and similarities to known campaigns, researchers have also identified potential ties between the ongoing campaign and both Black Basta ransomware indicators and FIN7.
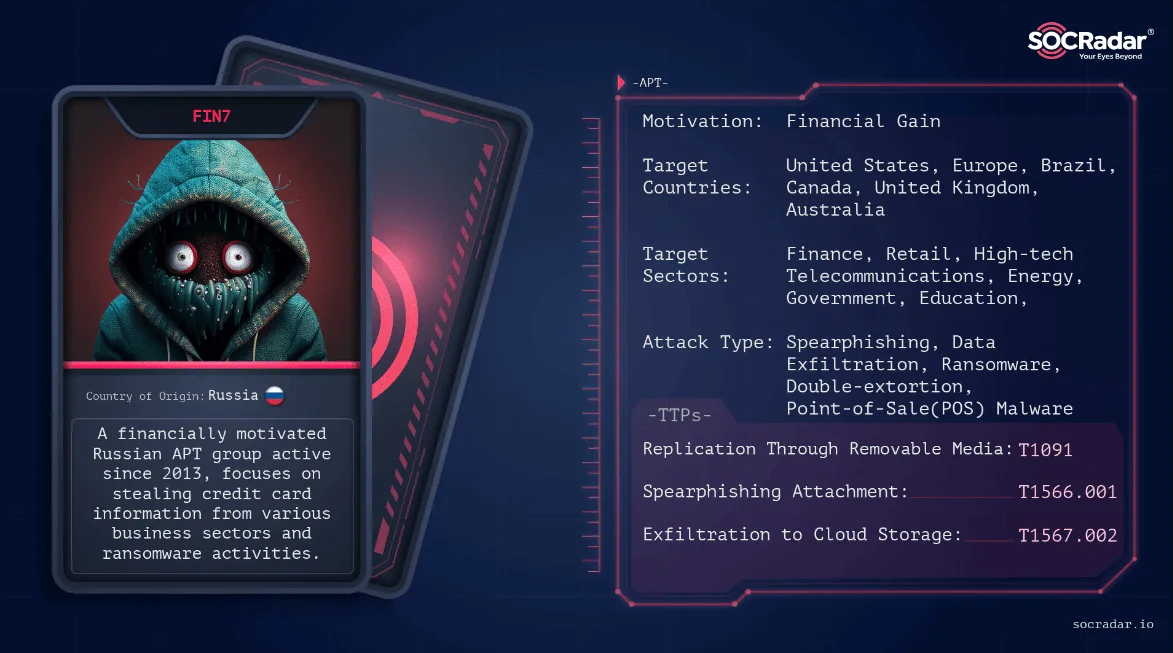
Threat actor card of FIN7
By understanding the possible actors behind this campaign, organizations can gain insights into the motivations and tactics employed by these threat actors. This knowledge will allow them to enhance their cybersecurity measures and better protect themselves against similar attacks in the future.
Please note that these connections are being investigated and attribution may require further evidence.
The SOCRadar platform is essential for detecting and dealing with such cyber threat campaigns. Visit the SOCRadar Labs Campaign page for more information and to stay updated on the latest attack trends.
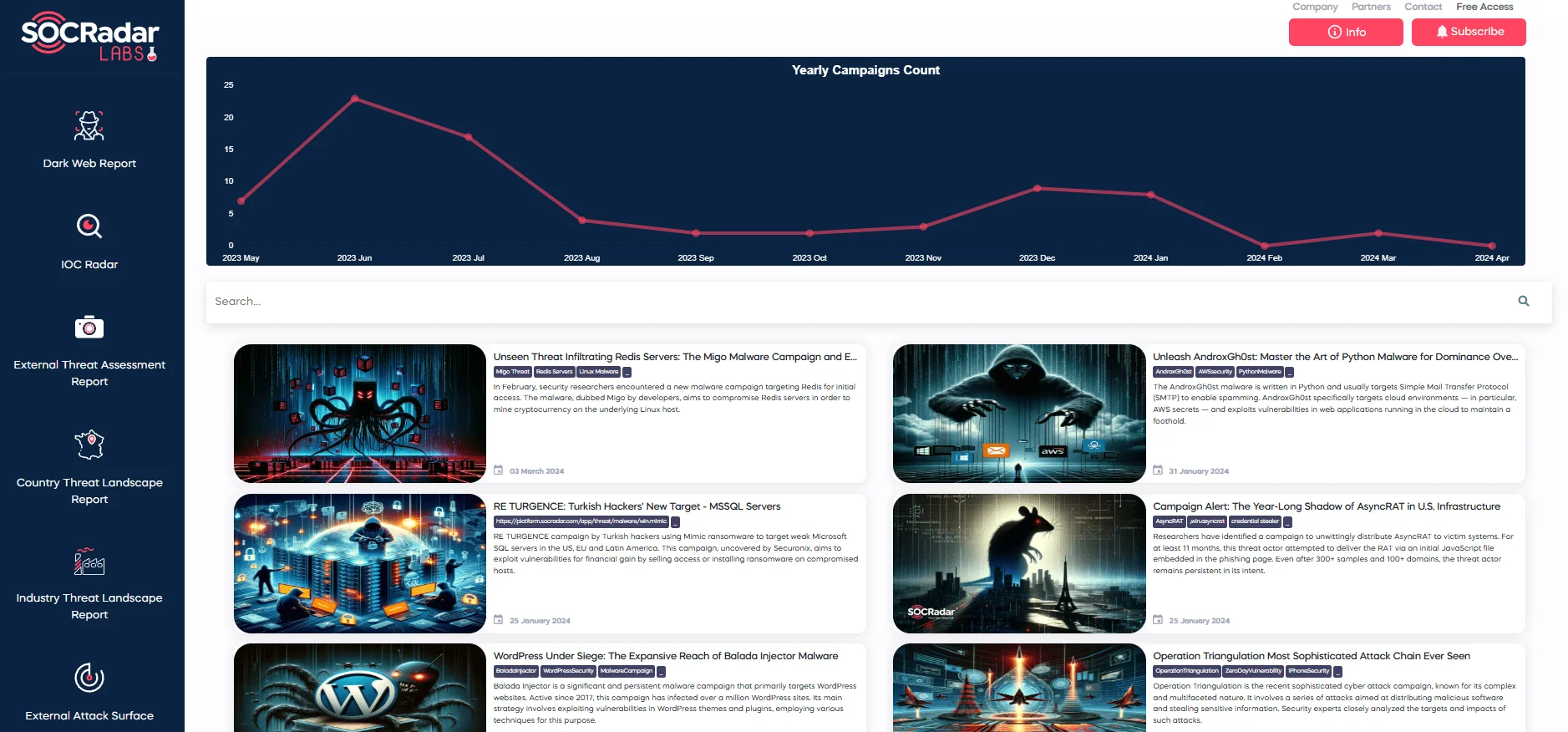
Campaigns page, available at SOCRadar LABS

































