‘Nightmangle’ Telegram C2 Agent and New FUD Crypter with Windows Defender Bypass
[Update] October 5, 2023: See the subheading: “SPCRYPTER’s Latest Update: No More Trials.”
Hackers favor Telegram as a platform for a wide range of activities, such as communication, announcements, advertisements, and even recruitment. Recently, a red team enthusiast shared their latest development, revealing how threat actors can further exploit the platform. They introduced a new post-exploitation Command and Control (C2) Agent, built specifically for Telegram.
This agent, known as Nightmangle, quickly gained attention on its GitHub repository, accumulating 42 stars and some forks to other projects within just two days since its launch.
What Is the Idea Behind Nightmangle?
The underlying concept behind Nightmangle is to demonstrate how the Telegram API can be leveraged by threat actors for post-exploitation purposes. It was developed by “1N73LL1G3NC3,” and serves as a Proof-of-Concept (PoC).
Nightmangle highlights the versatility of Telegram as a C2 server for communication between attackers and their target clients in a covert and effective manner. Telegram’s suitability for this purpose is underpinned by several advantages; beyond its capability to execute commands, Telegram:
- Ensures reliable uptime, guaranteeing uninterrupted C2 connectivity, and supports multiple platforms, including desktop, mobile, and web, enabling attackers to operate seamlessly across platforms.
- Its traffic seamlessly blends with legitimate network traffic due to its use of HTTPS and TLS protocols. This design reduces the likelihood of detection by intrusion detection or prevention systems and minimizes the chances of being blocked by network security solutions.
- Its implementation of end-to-end encryption and the absence of direct IP connections contribute to enhanced privacy, effectively concealing the attacker’s IP address and location.
Nightmangle, like many other hacking tools or PoC projects, has the potential to pose a risk if it falls into the wrong hands or if it is used for malicious purposes. However, the severity of the risk for specific individuals is determined by how vulnerable their assets are. Therefore, it is critical to follow security best practices such as updating regularly to avoid security vulnerabilities, exercising caution with online contents and downloads to avoid being compromised in the first place.
Using the SOCRadar Attack Surface Management (ASM) module, you can actively monitor your digital footprint, stay vigilant about the state of your digital assets and any security vulnerabilities, and proactively address them.
Capabilities of Nightmangle
Nightmangle has a limitation in that it can only set one Telegram bot API per payload. Consequently, if an attacker wishes to infect another machine, they must construct a new payload with a different Telegram bot API.
This agent is written completely in Rust. Its GitHub page displays a set of commands:
- Help: Displays help information.
- ShowDir: Reveals the content of a directory.
- SendFile: Retrieves a specified file from the victim.
- Task: Executes a specified shell command.
- Imperun: Performs token duplication UAC bypass by using a token stolen from an elevated process, based on Impersonate-RS.
- Screenshot: Captures a screenshot.
- St3al3r: Steals saved credentials from several browsers, including Firefox, Edge, Chromium, Chrome, and Brave.
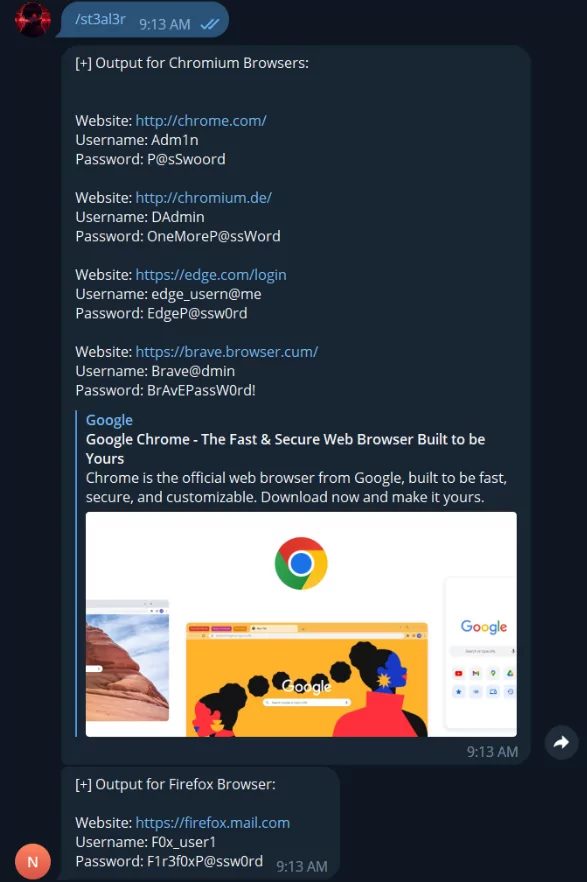
It is important to note that Nightmangle is not primarily designed to be evasive. Instead, its author states it is created to be highly modular, allowing the operator to incorporate custom features or modules that can help evade their target’s detection systems.
The agent employs the Coffee library, a custom implementation of the original Cobalt Strike’s beacon_inline_execute. This enables Nightmangle to support most of the features found in the Cobalt Strike compatibility layer.
For further details about the Nightmangle C2 agent, refer to its GitHub page.
Another Discovery: New FUD Crypter ‘SPCRYPTER’ Advertises on Telegram
A new Fully Undetectable (FUD) crypter, named SPCRYPTER, has surfaced on Telegram, and it operates on a subscription basis.
FUD crypters are advanced tools employed by cybercriminals, which make malicious code completely undetectable, enabling attackers to covertly infiltrate systems.

The Telegram channel for the crypter was established in April 2023, but it appears to have begun promoting its services in early August. Currently, the channel boasts nearly 500 subscribers, and the threat actor/s responsible for the crypter are actively enhancing and updating its capabilities.
Here are the latest features of the crypter:
- .NET/Native (x64) support
- UAC Bypass
- Anti Debug
- Anti VM
- Melt file (self delete)
- AMSI bypass
- ETW bypas
- Bypass WD (Windows Defender)
- Bypass AV (Antivirus)
- Bypass Chrome (Download Detection)
The threat actor/s are offering the crypter for $99 per month, which includes one build, and a lifetime subscription for $999, providing unlimited builds. Additionally, the seller assures a 24-hour trial period before payment.
For a comprehensive understanding of the potential impact of this cybersecurity threat, read our research, which offers a detailed analysis of various FUD markets operating within the deep web.
SPCRYPTER’s Latest Update: No More Trials
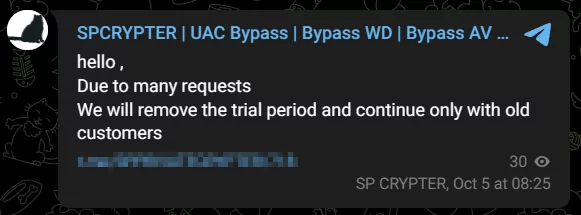
In its latest update, SPCRYPTER no longer provides users with a 24-hour trial period.
The individual/s behind the crypter claim this change is due to “many requests” and further note that they will continue with their “old customers.” This message suggests that there is an increased demand from threat actors, with new buyers showing interest in this malicious tool.
The tool’s latest update introduces high quality in both scantime and runtime capabilities, and its Telegram channel now has approximately 500 users. It is deeply concerning that such sophisticated tool ostensibly created for “educational purposes” has garnered this level of interest from potential threat actors in such a short period of time.
Track Emerging Dark Web Threats with SOCRadar
SOCRadar delves into the enigmatic world of the dark web, where security threats abound, and diligently filters and highlights the most crucial events, providing valuable insights.
With the Dark Web Monitoring module, SOCRadar promptly updates you on Telegram channel activities, discussions among hackers on dark web forums, and cybersecurity incidents targeting your digital assets.
Additionally, SOCRadar continuously scans the dark web for leaked data and promptly reports such occurrences through the Dark Web News module. Our goal is to detect leaked data and alert the potential victim before an incident escalates into a catastrophe.