Over 400K Buckets and 10.4B Files Are Public Due to Cloud Misconfigurations
In today’s cloud-centric era, the migration of digital assets to cloud storage has become widespread, driven by the demand for high availability and performance. However, this transition has not been without its challenges.
One significant security concern that emerged was the misconfiguration of cloud buckets. Cloud buckets store critical organizational assets, including confidential data, sensitive databases, and source codes. In line with the principle of shared responsibility, cloud providers maintain the health of these cloud files within their network, while the sole authority to configure access rights rests with the cloud users.
Often due to human error, cloud buckets become publicly accessible. Verizon’s 2022 Data Breach Investigations Report revealed that human errors played a role in 13% of data breaches, with cloud storage misconfigurations as a top contributor.
Using the open source programs/platform, anyone can scan millions of public buckets at once using certain keywords. Typically, buckets adhere to a common naming convention, with a user-specific portion in the URL, making them susceptible to massive detection.
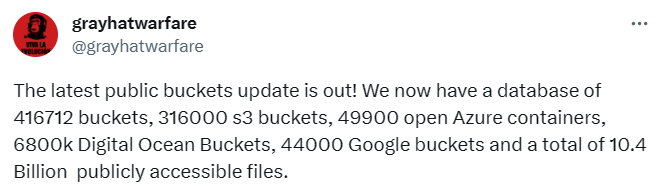
Cybercriminals frequently seek unauthorized access to such buckets, gathering information from a variety of sources to accomplish their goal. One such platform that can be utilized to gather information on buckets, GrayhatWarfare, has recently announced that its public buckets database has been updated.
The availability of such an extensive collection of data in one place, open to look through, may attract the interest of threat actors, potentially turning it into a focal point for malicious activities.
What Is the Risk of Open Search for Public Buckets?
While the platform itself cannot be labeled as a threat and actually serves to increase awareness about the public buckets problem, it does provide an opportunity for anyone to search for publicly available buckets and apply filters. Therefore, it is undeniable that threat actors are inclined to exploit such a resource.
The top 20 keywords in files identified by the platform are listed below:
|
# |
File |
Count |
|
1 |
nyc |
6041607 |
|
2 |
208 |
1622759 |
|
3 |
nba |
1561075 |
|
4 |
on |
1552635 |
|
5 |
ice |
1481593 |
|
6 |
blood |
1353315 |
|
7 |
Panasonic |
955446 |
|
8 |
abc |
916150 |
|
9 |
australia |
452230 |
|
10 |
consumer |
140809 |
|
11 |
id |
100601 |
|
12 |
vote |
85212 |
|
13 |
plaid |
79628 |
|
14 |
Iso |
73097 |
|
15 |
CA |
56802 |
|
16 |
CSA |
43133 |
|
17 |
monet |
35093 |
|
18 |
cloudfront |
28024 |
|
19 |
gov |
27479 |
|
20 |
cos |
26505 |
What exacerbates the situation is that these leaks are accessible on a single platform, albeit for a fee. The platform offers over 10 billion files that users can search based on file extensions and content.
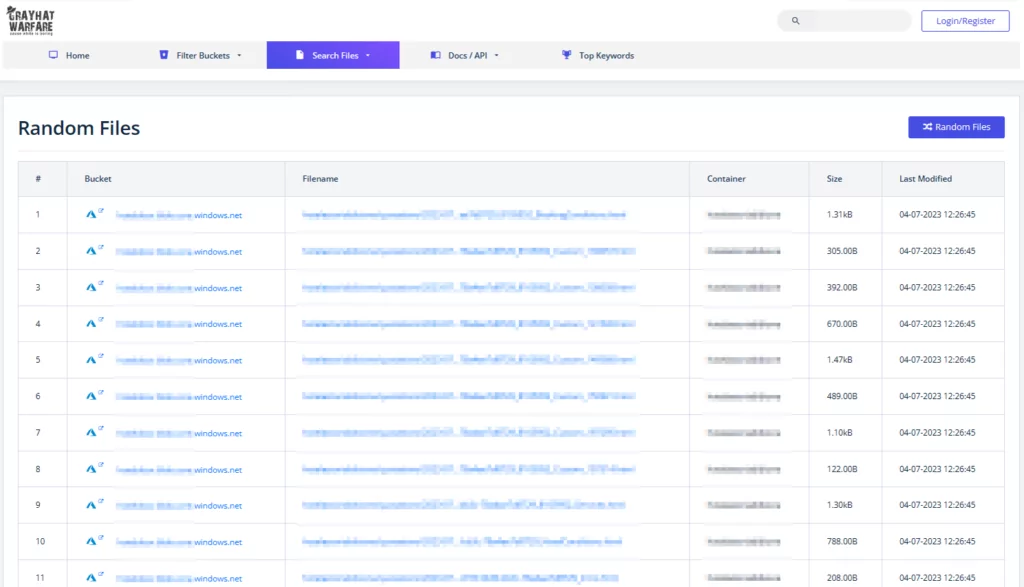
Although most features on the platform require a membership, basic searches are available for free. One of the free features also allows users to view information about random files. Refreshing the list returns 50 new files, from another container name.
Conclusion
Just as initial access brokerage has become a pivotal launching pad for ransomware groups, platforms that centralize public buckets for searches with filters can become go-to resources for threat actors.
As cloud adoption continues to grow within organizations, coupled with the persistence of human errors that inadvertently expand the attack surface, we can anticipate more frequent disclosures of critical files due to misconfigurations.
A recent incident highlighted by Microsoft’s AI research team serves as a stark reminder of these risks. They accidentally exposed 38 terabytes of sensitive data while sharing an open-source training data bucket via GitHub. This exposure resulted from a misconfigured Azure Shared Access Signature (SAS) token during the URL generation process. This recent incident and previous cases like BlueBleed underscore the ever-present threat of data exposures due to public buckets, which can occur at any time and potentially compromise vast amounts of information.
Furthermore, the ability to search for specific file types adds an extra layer of risk. Previously, several crucial file types have been discovered in such bucket disclosures, including configuration files and backup disk images. Files of this nature pose significant risks, and when coupled with existing vulnerabilities, they could potentially facilitate further cyberattacks.
Monitor Cloud Environments with SOCRadar: Mitigate the Risk of Public Buckets
Our platform offers real-time monitoring capabilities, enabling organizations to promptly detect unusual activity and potential security threats within their cloud-based systems and applications.
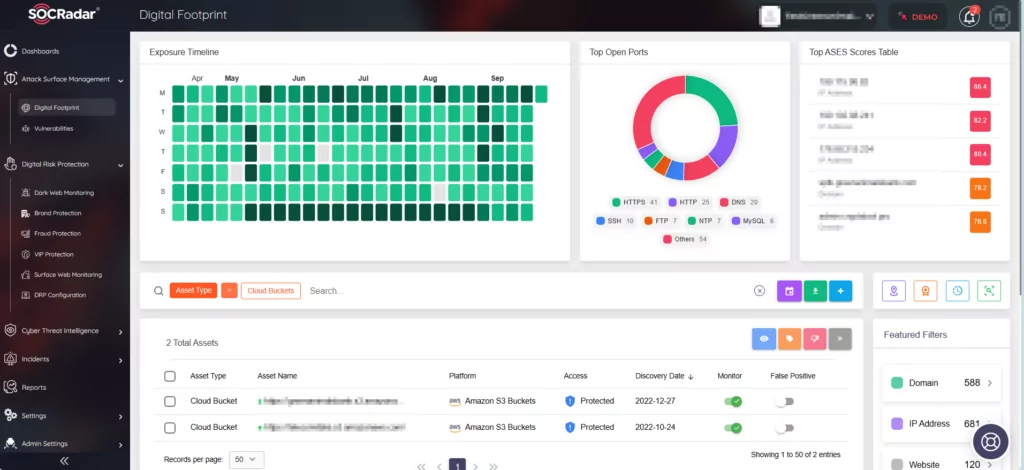
SOCRadar’s Cloud Security Module (CSM), a part of our External Attack Surface Management (EASM) service, is dedicated to safeguarding your data within cloud computing environments. It provides notifications whenever sensitive data is identified in any public cloud storage. Notably, this module played a crucial role in identifying the sources behind the BlueBleed breach.
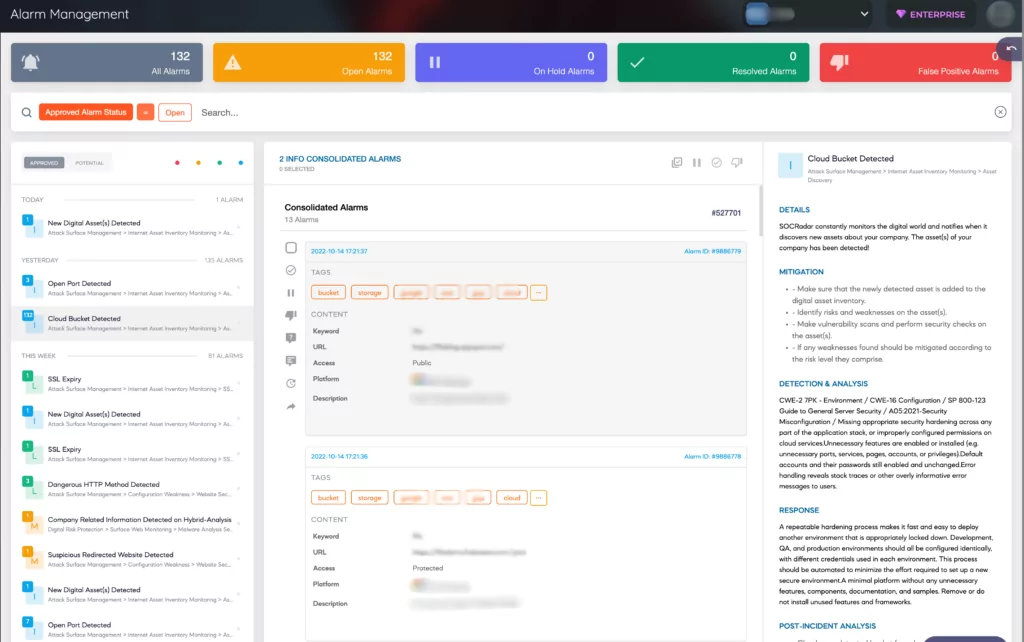
The module is designed to notify you when it discovers new cloud buckets associated with your organization and keeps you updated on their status, sending a “Cloud Bucket Status Change” alert if any issues arise.
For a more in-depth understanding of how to secure your cloud environment, read our blog post, Secure Your Cloud Environment: 5 Best Practices.

































