
Overview of TIBER-EU From Threat Intelligence Perspective
Financial institutions are crucial for the global economy. They hold trillions of dollars in assets and billions of customer records. As such, they are one of the prime targets for cyberattacks.
According to Statista, in 2022, there were 1,829 reported cyber incidents in the financial industry worldwide. This is a decrease from the previous year (down from 2,527). However, it is still significant because finance and insurance had the second highest share of cyber attacks among the leading industries worldwide, with nearly 19 (18.9) percent of the total cyber attacks.The financial industry was also the most targeted by basic web application attacks worldwide, with 173 incidents between November 2021 and October 2022.
According to the IBM Cost of Data Breach Report 2023, financial organizations are on the second list of the most expensive data breaches.
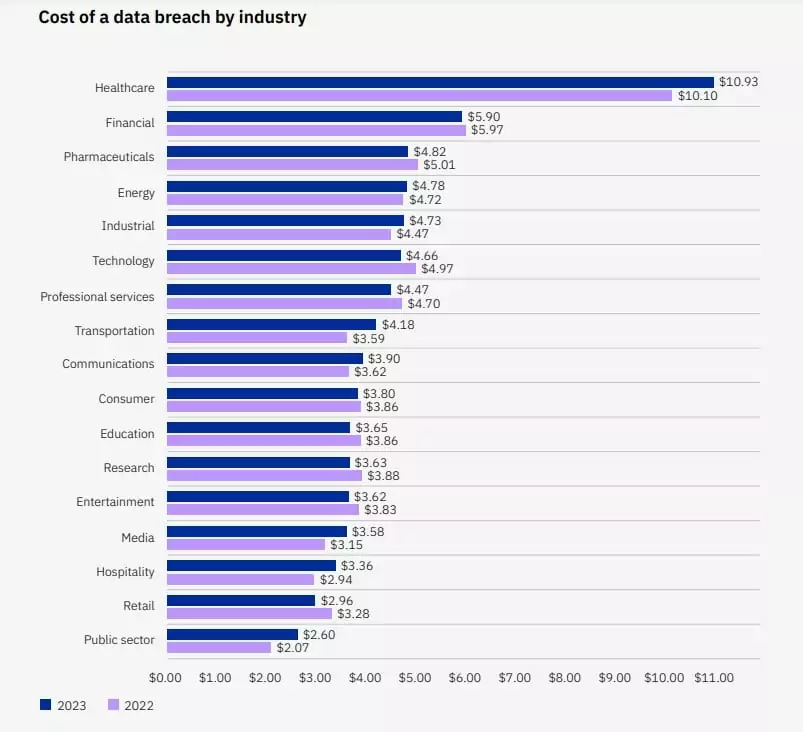
Financial institutions, classified as critical infrastructure, are part of an interconnected industry that made them at least partially dependent on other members of the chain for their own cyber resilience.
So, financial institutions must have robust cybersecurity protocols and be prepared to respond quickly and effectively to cyberattacks in place to maintain a secure ecosystem all over the industry.
A European framework for ethical red-teaming based on threat intelligence is called TIBER-EU. TIBER-EU is designed to help financial institutions enhance their cyber resilience through realistic cyberattack simulations.
What is TIBER-EU?
The Threat Intelligence-based Ethical Red Teaming, known as TIBER-EU, is a framework that delivers a “controlled intelligence-led red team test of entities’ critical systems.” TIBER-EU guides real-world attackers’ tactics, techniques, and procedures are distilled into controlled cyberattack simulations. These simulations are meticulously designed to mirror an assault on an entity’s critical functions, spanning people, processes, and technologies.
The TIBER-EU was developed by the EU national central banks and the European Central Bank (ECB) and published in March 2018. The framework’s objective is to test and improve financial institutions’ resilience against sophisticated cyber-attacks by helping to understand their protection, detection, and response capabilities to cyberattacks in real-life scenarios.
Countries including the Netherlands, Belgium, Denmark, Finland, Germany, Iceland, Ireland, Italy, Luxembourg, Norway, Portugal, Romania, Spain, and Sweden have adopted the TIBER-EU framework.
Fundamentals of TIBER-EU
- Core Objectives:
TIBER-EU, therefore, has the following core objectives:
- Enhance the cyber resilience of entities of the financial sector;
- Harmonize and standardize the way entities perform intelligence-led red team tests across the EU and also allow each jurisdiction some flexibility to adapt the framework according to its specificities;
- Guide authorities on how they might establish, implement, and manage this kind of testing at a national or European level;
- Support cross-border, cross-jurisdictional intelligence-led red team testing for multinational entities;
- Enable supervisory and/or oversight equivalence discussions where authorities seek to rely on each other’s assessments carried out using TIBER-EU, thereby reducing the regulatory burden on entities and fostering mutual recognition of tests across the EU;
- Create the protocol for cross-authority/cross-border collaboration, result sharing, and analysis.
- Main Stakeholders:
According to their roles and responsibilities within the TIBER-EU framework, the main participants in a TIBER-EU test can be classified into five different teams;
- TIBER Cyber Team: The TIBER cyber team is responsible for managing the test and ensuring it meets the requirements of the TIBER-EU framework as the authority representative.
- White Team: The white team is a small team that knows a test is happening within the entity that is the subject of the test. The white team coordinates all test activity in collaboration with the TIBER cyber team.
- Blue Team: The blue team covers all staff at the entity, not part of the white team. The blue team should be completely excluded from preparing and conducting the TIBER-EU test for prevention, detection, and response capabilities are being assessed without foreknowledge.
- Threat intelligence provider: The threat intelligence provider is one of the two key stakeholders that have a role in test implementation. A threat intelligence provider is a company that gathers intelligence on possible threats and conducts reconnaissance on the entity.
- Red-team provider: The red-team provider is the company that plans and executes a TIBER-EU test of the target systems and services. The red-team providers carry out the simulated attack to attempt to compromise the entity’s critical functions.
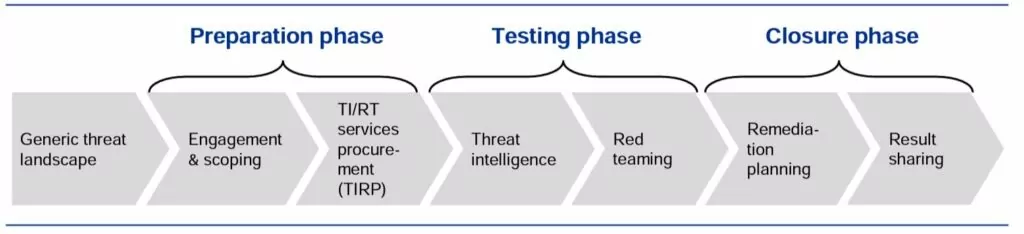
- TIBER-EU Process:
The TIBER-EU process is divided into three phases: preparation, testing, and closure. However, before the preparation test, the generic threat landscape phase can be optional. This step involves a generic assessment of the national financial sector threat landscape, including outlining the entity’s role and identifying current threat actors for the industry and their methods. The results of the generic threat landscape phase can be used to inform the preparation phase and the development of attack scenarios.
Preparation phase:
- The team Test Manager (TTM) from the TIBER cyber team contacts the participating entity
- The entity identifies its critical systems and assets.
- The entity hires a threat intelligence provider and a red team.
- Intelligence report and the entity’s critical systems and assets.
- The scope of the testing phase is established.
Testing phase:
- The threat intelligence provider provides the entity with information about the latest cyber threats.
- The red team develops attack scenarios based on the threat intelligence report and the entity’s critical systems and assets.
- The red team conducts simulated cyberattacks against the entity’s critical systems and assets.
- The entity’s blue team defends against the attacks.
- The red team keeps TTM and the white team up to date.
- The white team can stop the test whenever it deems necessary.
- The red team collects and saves evidence of the attacks in the red team test report.
Closure phase:
- Include remediation planning and result-sharing
- The red team provides the entity with a report that includes the findings and evidence from the testing phase.
- The entity reviews the report and develops a remediation plan to address any identified weaknesses or vulnerabilities.
- All parties provide feedback on each other and the overall process.
The Position of Threat Intelligence in TIBER-EU
The function of the TIBER-EU framework is to check for financial institutions’ defense capabilities over a test tailored to the organization based on real-life scenarios. In this context, threat intelligence provides the ‘intelligence’ that will enable the creation of accurate test scenarios by viewing the organization’s attack surface, defining the threats it faces, and identifying potential threat actors and their TTPs.
A threat intelligence provider should be required to fulfill crucial requirements in the TIBER-EU framework. Some of them are:
- be competent to explain the methodology
- have experienced technical experts and support staff
- having a qualified manager
- have several years of experience
- have mature ethical standards
- must have a multidisciplinary team with a wide range of skills, including OSINT, HUMINT, and geopolitical knowledge.
The threat intelligence provider needs to develop a strategic understanding of ‘what’ makes the financial organization interesting, ‘why’, for ‘which’ threat actors, and ‘how’ that interest can be translated into action.
In this regard, The TI provider should determine the organization’s digital footprint as a part of gathering threat intelligence. The first step for this is to define the attack surface. Thus, all digital assets of the organization can be seen from the perspective of threat actors.
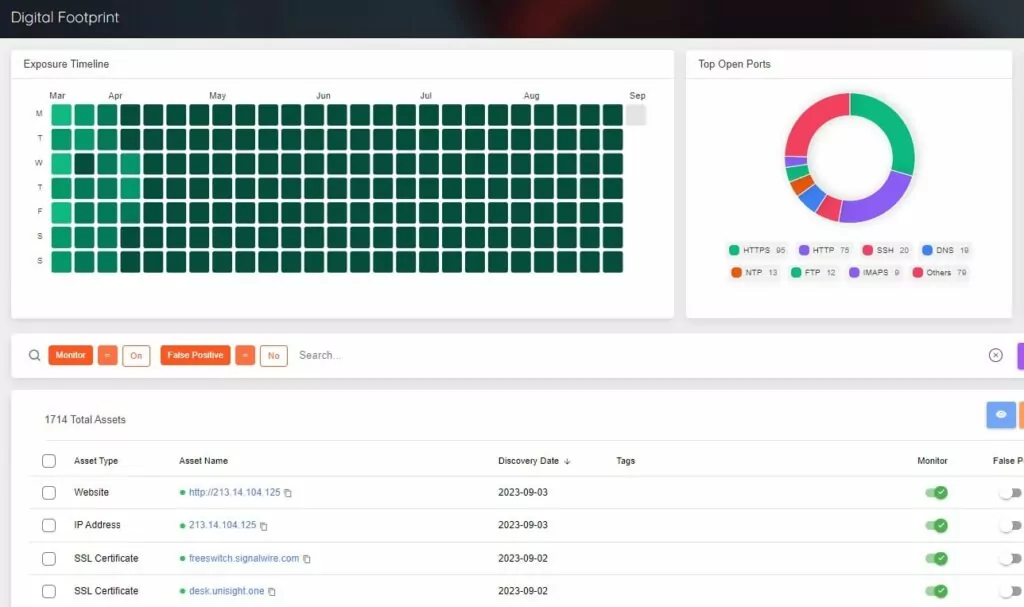
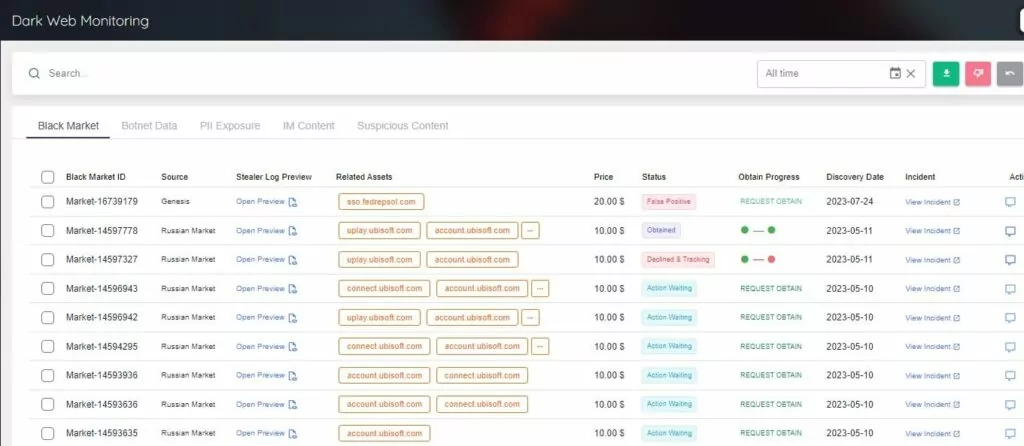
The next step is acquiring intelligence specific to the organization, such as sensitive information about the organization and its customers, employees’ data on social media, impersonating domains, or V.I.P. personnel’s data in breach data sets.
Additionally,
- third-party providers and their security posture,
- common security vulnerabilities in the financial sector and the vulnerabilities of the organization
- The threat actors targeting the financial industry and likely to target the institution, the malware and vulnerabilities they use, and their TTPs within the framework of MITER ATT&CK should be provided by the threat intelligence provider.
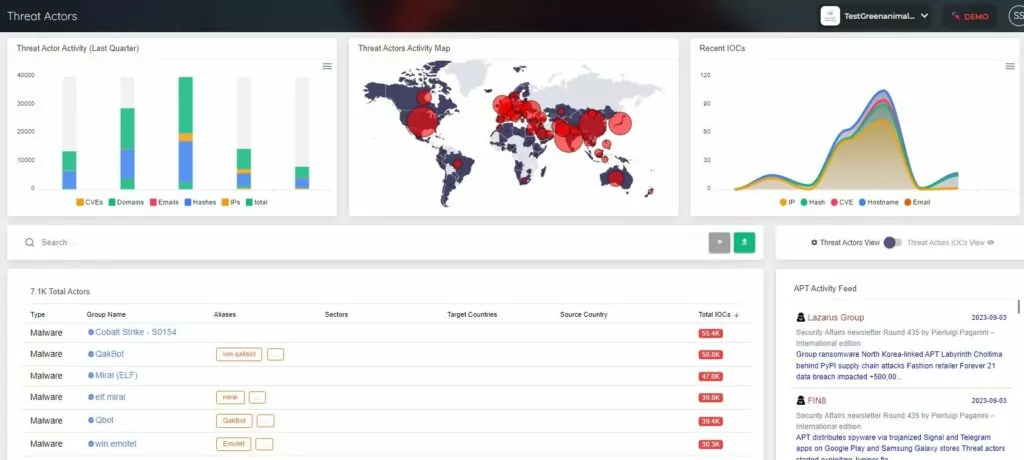
Monitoring the dark web along with the surface web is crucial to gathering all of this intelligence.
Conclusion
TIBER-EU is a valuable framework for financial institutions looking to improve their cyber resilience. TIBER-EU can help financial institutions identify and mitigate security vulnerabilities by simulating real-world cyberattacks. So, financial institutions can establish a road map to protect themselves from cyberattacks and mitigate the damage these attacks can cause.
Although TIBER-EU is not mandatory, it emerges as a proactive and insightful tool that stands ready to empower financial institutions in their quest for cyber maturity, and it is highly recommended for financial institutions in the European Union. By January 2023, more than 100 TIBER tests had been conducted under the TIBER-EU framework, underscoring its relevance and value in today’s dynamic threat environment.
By participating in TIBER-EU, financial institutions can demonstrate to regulators, their customers, and partners that they take cybersecurity seriously. The TIBER-EU framework, while improving cyber resilience, helps to enhance customer confidence, strengthen the financial industry’s collective cybersecurity posture.



































