
Phishing Template Targets U.S. Candidates; RobbinHood Tool and KFC Data Exposed
The SOCRadar Dark Web Team continues its diligent monitoring of the hacker landscape; several significant cyber threats have been identified over the past week, including the alleged leak of the RobbinHood ransomware toolset and unauthorized VPN access to Spanish universities. Additionally, sensitive customer data from KFC Mexico is being sold, alongside government logs from over 50 countries. A new phishing template targeting U.S. presidential candidates has also surfaced, raising serious concerns about identity theft and fraud.
Receive a Free Dark Web Report for Your Organization:
New RobbinHood Ransomware Tool Share is Detected
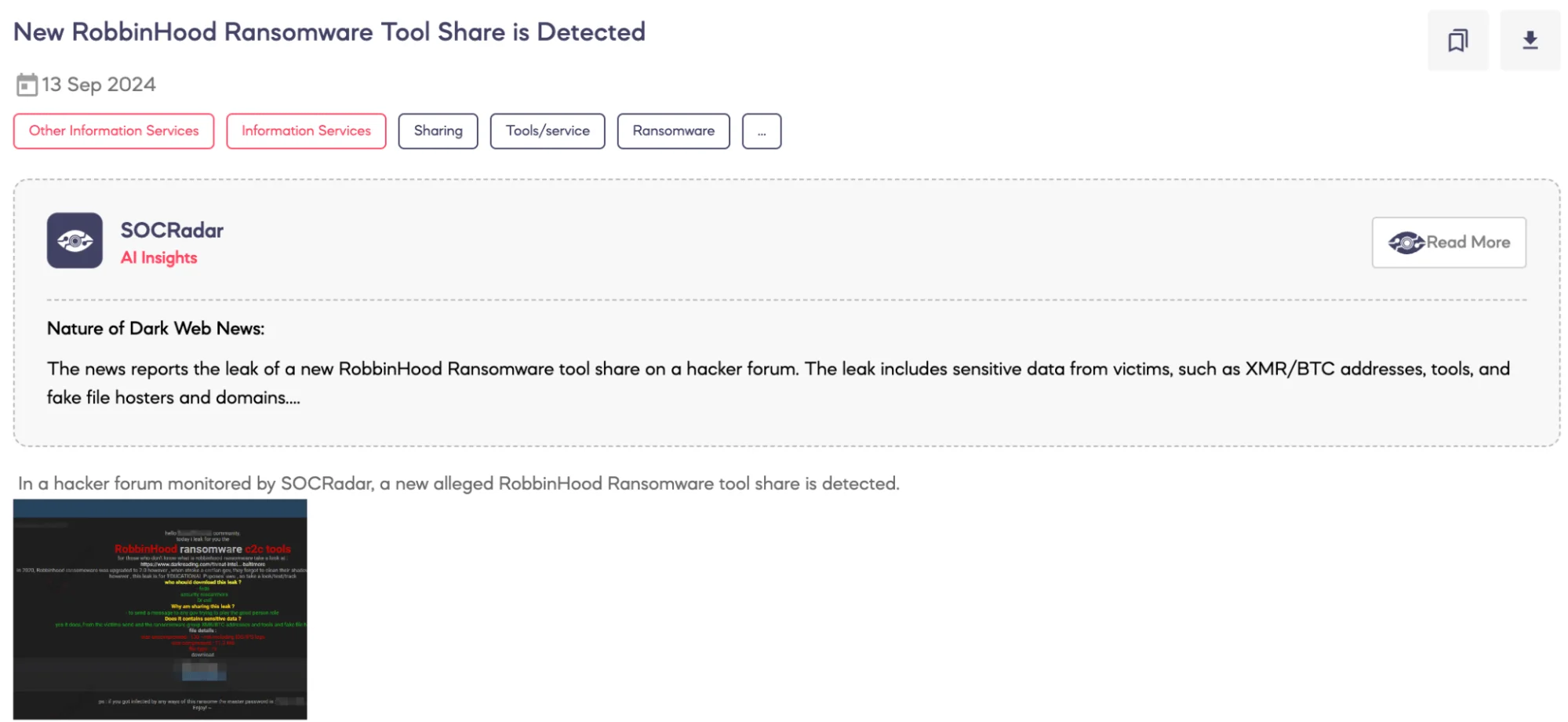
SOCRadar Dark Web Team detected a post on a hacker forum sharing an alleged RobbinHood ransomware toolset. The threat actor claims to have leaked the Command and Control (C2C) tools used by the RobbinHood ransomware group, which they state is intended for “educational purposes.”
According to the threat actor’s claims, RobbinHood ransomware was upgraded to version 2.0 in 2020. However, they allegedly failed to remove shadow files during an attack on a government entity.
The file is available in a compressed 7z format, with a total size of 11.3 MB when compressed and approximately 130 MB uncompressed. The leak also includes IDS/IPS logs. The threat actor emphasizes that security researchers, law enforcement, and “Dr. Evil” should find value in this leak, suggesting it contains critical insights for those investigating ransomware.
Additionally, the post provides a “master password” in case any users inadvertently become infected by the ransomware.
The Alleged Unauthorized VPN Accesses Sale is Detected for Spanish Universities
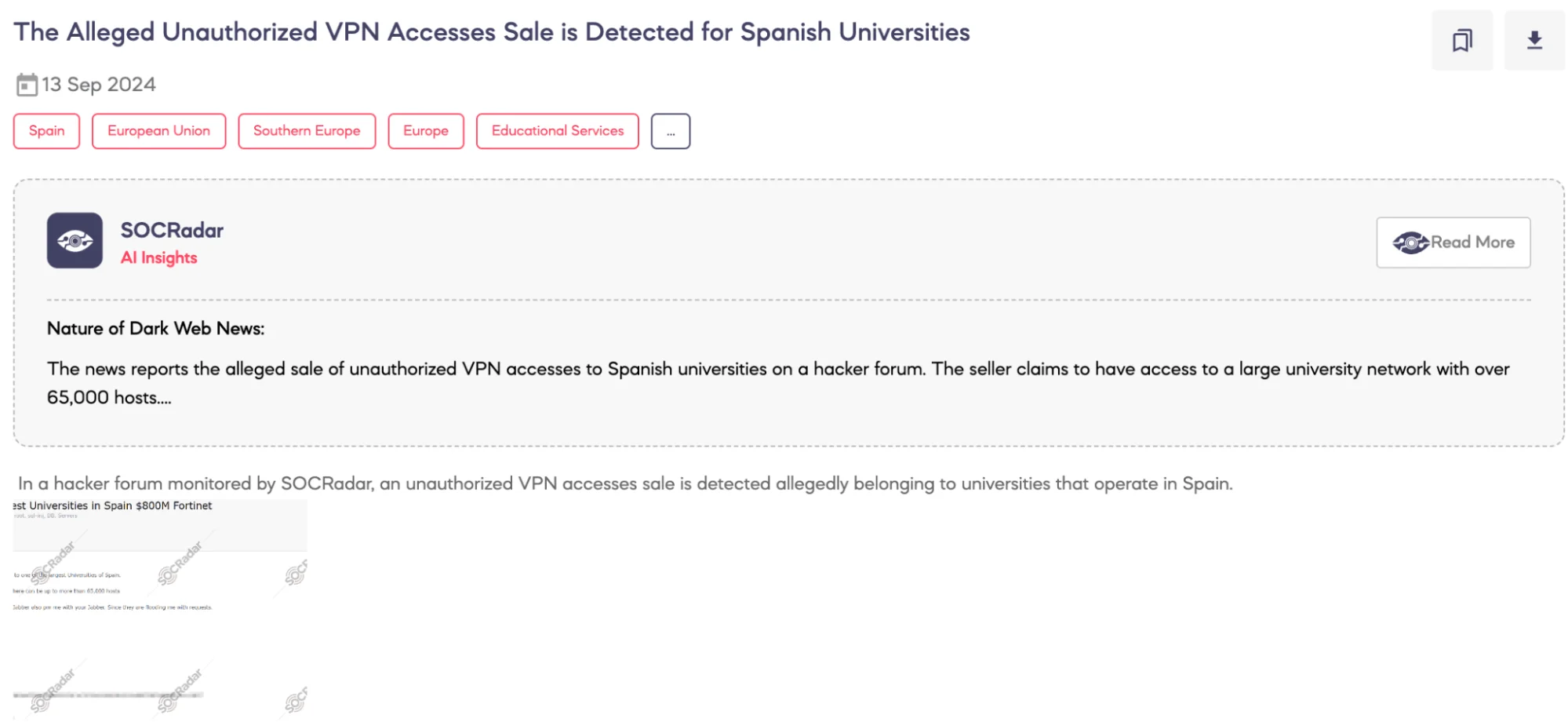
SOCRadar Dark Web Team detected a post on a hacker forum advertising the alleged sale of unauthorized VPN access to a large university in Spain. The threat actor claims that the access is via Fortinet VPN and involves a network that could include up to 65,000 hosts.
According to the threat actor’s claims, the targeted university is one of the largest in Spain, operating with a revenue of approximately $800 million. The access being sold is for a user-level account, and the asking price is $1,000. Escrow services are available for the transaction.
Database of KFC Mexico is Allegedly on Sale
SOCRadar Dark Web Team detected a post on a hacker forum where the alleged database of KFC Mexico has been offered for sale. The threat actor claims to have obtained the delivery order data from the fast-food chain, exposing a significant amount of customer information.
According to the threat actor’s claims, the database contains 349,751 records from customers in Mexico, with detailed information such as names, addresses, zip codes, phone numbers, emails, and additional data like customer notes, mobile device types, and even geo-coordinates. The data also includes business codes, merchant IDs, and information regarding communication preferences, such as whether the customer allows sending SMS or email notifications.
The threat actor offers a sample of the data and invites interested buyers to contact them via Telegram for further details.
Logs of Many Governments are Allegedly on Sale
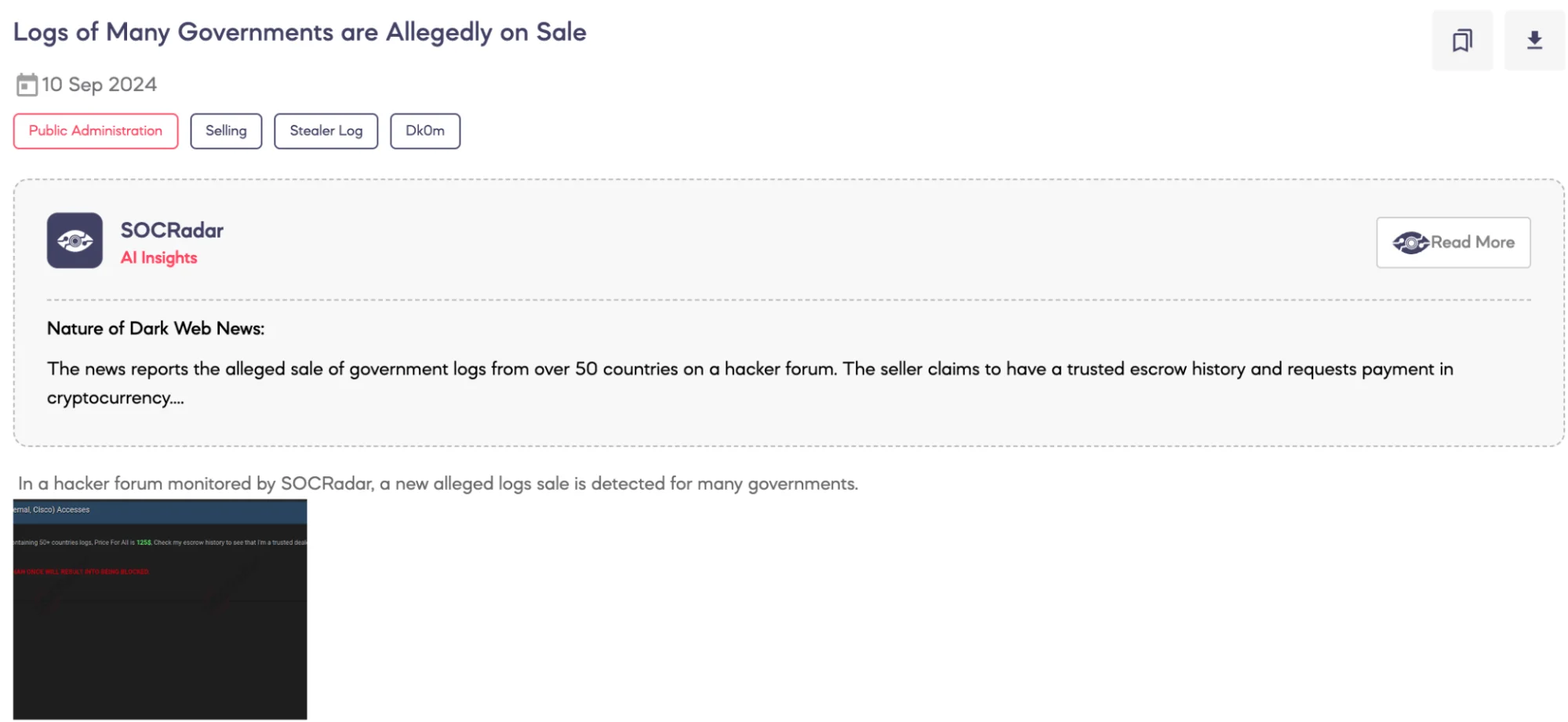
SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of alleged government logs from over 50 countries. The threat actor claims to possess over 10 million logs from various government entities, offering the entire dataset for just $125. The logs are allegedly available for purchase via cryptocurrency, and the threat actor invites interested parties to contact them through Telegram for further details.
New Phishing Template is on Sale
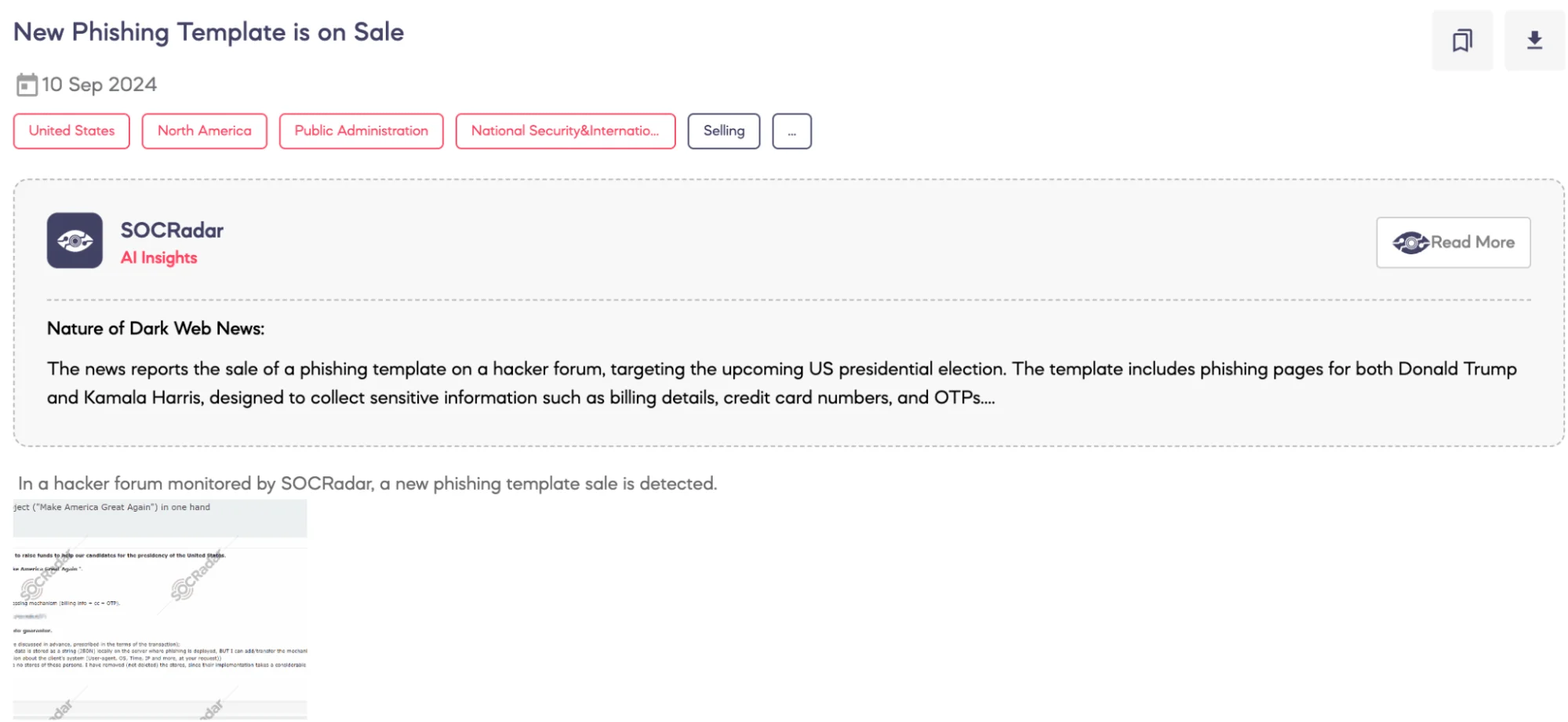
SOCRadar Dark Web Team detected a post on a hacker forum offering a new phishing template based on U.S. presidential candidates. The threat actor claims to be selling a turnkey phishing project that includes landing pages for two prominent figures: Donald Trump and Kamala Harris.
According to the threat actor’s claims, the phishing templates are fully equipped to collect sensitive information, such as billing details, credit card information, and One-Time Passwords (OTPs). The transaction for this phishing kit is to be handled through a guarantor or an automated guarantor system, ensuring security for both parties.
The threat actor offers customization options, stating that edits can be made based on the buyer’s preferences, which must be discussed and agreed upon before the transaction. While the collected data is currently stored locally on the phishing server as a string in JSON format, the seller is willing to modify the system to save the data to Telegram for easier access if desired. Additional features, such as collecting user system information (e.g., User-agent, OS, IP address), can be added upon request.
Lastly, the threat actor notes that stores for the candidates are not included by default but can be added to the phishing projects for an additional fee.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































