
Pipeline to Peril: Unpacking the ALPHV Attack on Trans-Northern
[Update] February 16, 2024: “US State Department’s Reward for Information on ALPHV/BlackCat Ransomware”
In the ever-evolving landscape of cybersecurity threats, the recent alleged cyber attack on Canada’s Trans-Northern Pipelines by the notorious ALPHV/BlackCat Ransomware group once again marked a concerning escalation in targeting critical infrastructure.
On February 13, 2024, ALPHV claimed responsibility for infiltrating the pipeline’s security systems and stealing a staggering 190GB of vital data and released alleged leak files.
The incident may not be isolated; it echoes the disruptive 2021 Colonial Pipeline attack in the United States, where a similar ransomware infiltration led to significant fuel shortages, economic turmoil, and widespread panic. Both incidents are reminders of essential services’ vulnerability to cybercriminal activities and the far-reaching consequences of such breaches.
The high possibility of the linkage of ALPHV to BlackMatter and DarkSide, groups responsible for the Colonial Pipeline attack, underscores a sophisticated and interconnected web of cyber threats that knows no borders.
Background and Context: Revenge
The cyber attack on Trans-Northern Pipelines by the ALPHV/BlackCat group is not an anomaly but a part of a disturbing trend that has seen vital services and infrastructure becoming prime targets for digital extortion schemes. While since the Ukraine-Russia war and Israel-Hamas conflict, targeting critical infrastructure is a rising trend, ALPHV has other reasons as well. Last year, many of ALPHV’s structures were seized by the FBI.

FBI’s seizure announcement of ALPHV domains
ALPHV took an aggressive stance, lifting limitations on ransomware deployment and motivating affiliates to conduct attacks without restraint. While groups operating under the Ransomware-as-a-Service (RaaS) model typically establish specific guidelines for their affiliates, including restrictions like avoiding attacks on certain sectors or government entities, ALPHV basically encouraged a more indiscriminate approach to targeting. The goal was revenge.
About the ALPHV
ALPHV, also known as BlackCat, is at the forefront of this new wave of cyber threats. It is a group known for its sophistication, technical prowess, and innovation. The lineage of ALPHV is traced back to notorious predecessors like BlackMatter and DarkSide, the latter being infamously associated with the 2021 Colonial Pipeline ransomware attack.
This lineage is not merely a historical footnote; it is indicative of the evolving nature of cybercriminal enterprises. They are learning entities, adapting and refining their methods with each campaign, making them increasingly difficult to predict and counteract.
As one of the most active Russian Ransomware groups, an operation was carried out against ALPHV last year, and the operational capacities of the threat actors were significantly reduced. Still, ALPHV, which has interesting extortion methods, continues to be one of the prominent groups in the ransomware landscape.
The Colonial Pipeline Precedent
Before moving on to the recent incident, we need to look at the Colonial Pipeline. Because, the Colonial Pipeline incident served as a critical case study of the vulnerabilities and potential impacts of ransomware attacks on critical infrastructure.
In May 2021, DarkSide infiltrated the Colonial Pipeline’s systems, forcing a shutdown of approximately 5,500 miles of pipeline. This action resulted in widespread fuel shortages across the Eastern United States, panic buying, and a significant spike in fuel prices.
Beyond the immediate disruption, the incident highlighted the fragility of critical infrastructure systems to cyber-attacks and raised questions about national security and economic stability in the digital age.
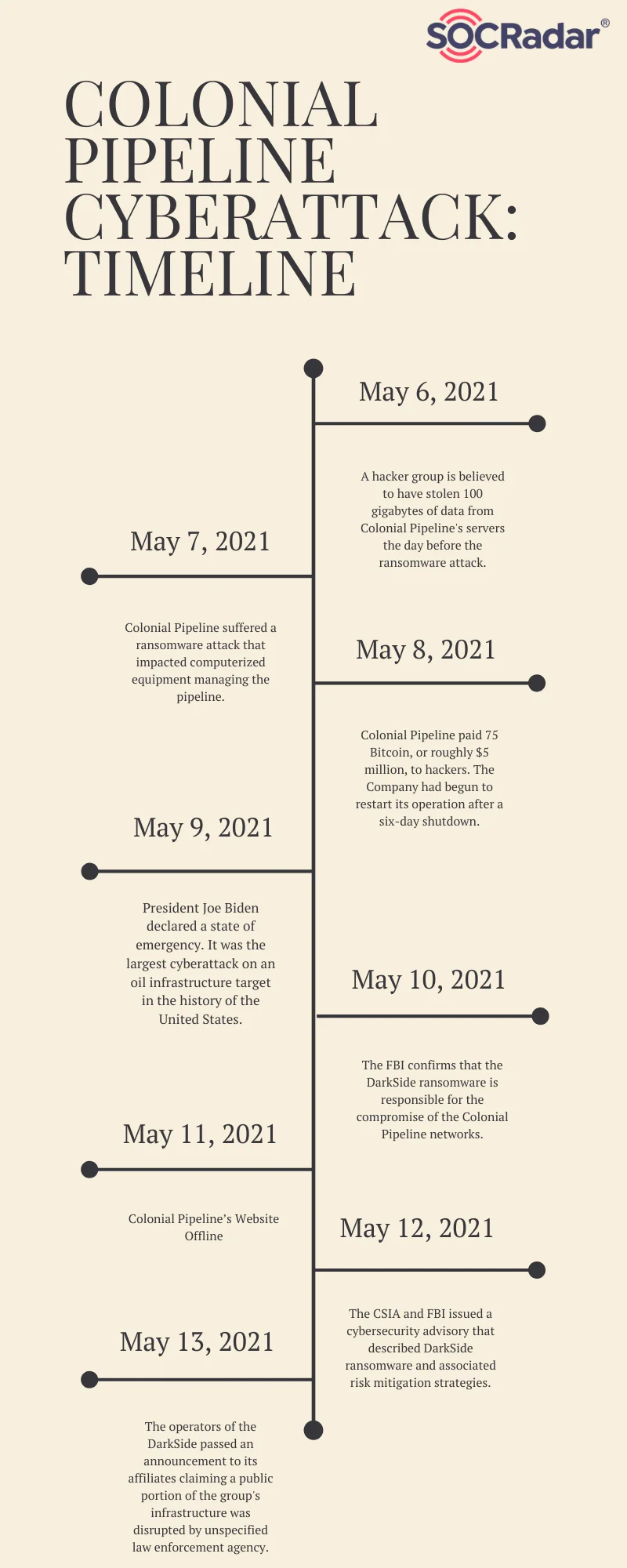
Timeline of the Colonial Pipeline incident
The Colonial Pipeline attack became a wake-up call, underscoring the urgent need for enhanced cybersecurity measures across all sectors of critical infrastructure. It illustrated not only the potential for immediate disruption and chaos but also the long-term implications on public trust and economic health.
In fact, this incident was so significant that it allegedly caused international tensions. After the attack, DarkSide was purged from the cyber world. However, The FBI declined to comment on whether the US government had played a hand in shutting down DarkSide’s website.
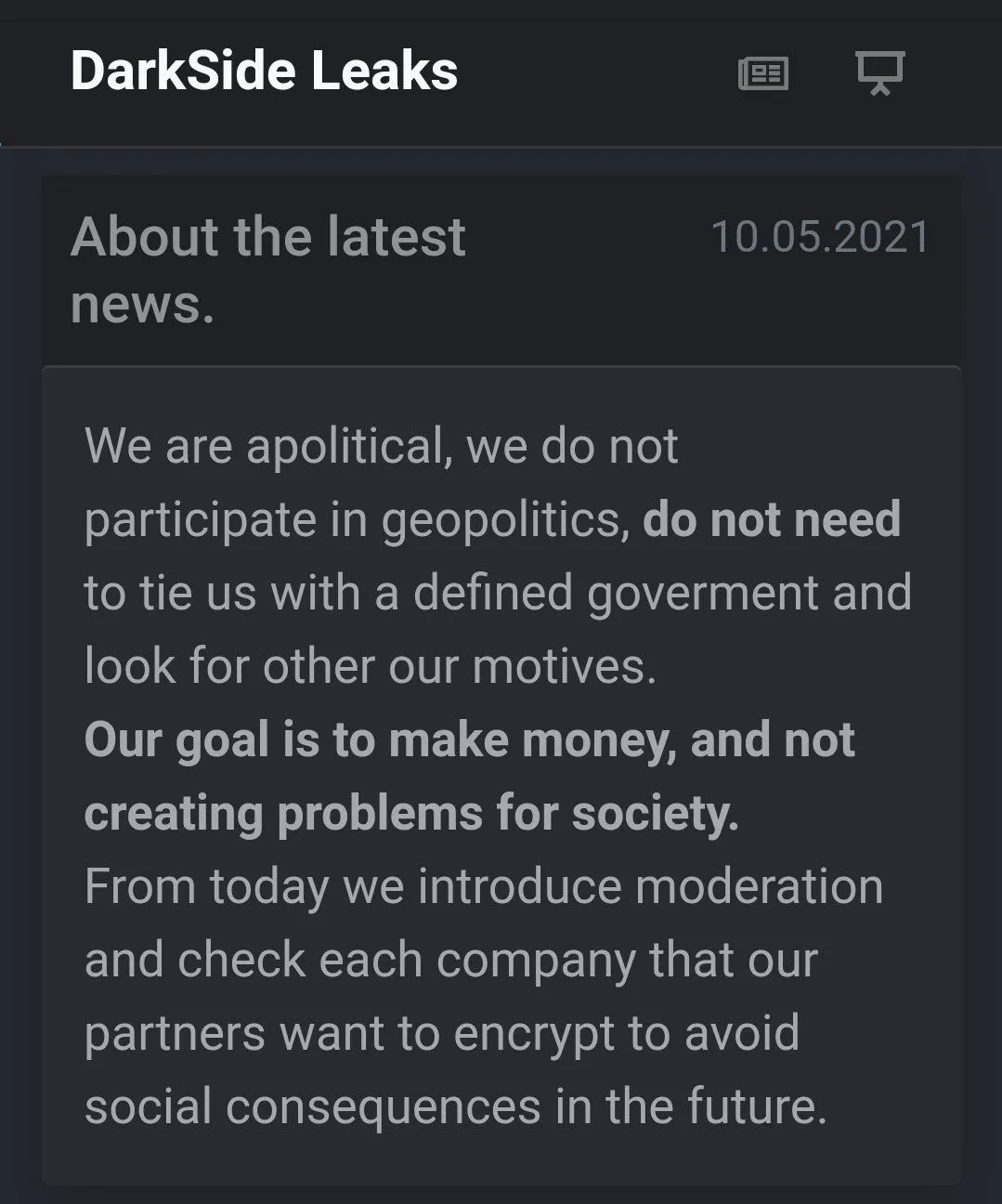
DarkSide’s announcement about alleged ties to any nation.
So, the attack on Trans-Northern Pipelines by ALPHV must be viewed within this broader context. It is a stark reminder that cybercriminals continue to target the essential services that underpin modern society.
Let’s see if the attack on Trans-Northern Pipelines will be a milestone on the path that will truly bring about the end of ALPHV.
Alleged Breach of Canada’s Trans-Northern Pipelines
ALPHV’s infiltration of Trans-Northern Pipelines’ security systems was a calculated assault on one of Canada’s key oil distributors. The oil and gas company, managing approximately 528 miles (850 kilometers) of pipeline across Ontario and Quebec, along with close to 200 miles (320 kilometers) of pipeline in Alberta.
The group claimed responsibility for stealing 190GB of vital data, a substantial breach that exposed sensitive operational, financial, and potentially personnel information. ALPHV’s modus operandi probably involves exploiting vulnerabilities in the pipeline’s cybersecurity defenses to gain unauthorized access and exfiltrate it to their servers.
190 GB of alleged leak files on ALPHV’s leak site
The ransomware group then added Trans-Northern Pipelines to its blackmail/leak site, and leaked the “all-important information.” Normally, unless their demands—typically a ransom payment in cryptocurrency—were met. This tactic of double extortion, threatening both data encryption and public release, is a hallmark of modern ransomware operations designed to maximize pressure on the victim organization to comply with the attackers’ demands.
However, the data currently appears to be available for download on the leak site. This, of course, strengthens the revenge thesis.
The group also claimed that it leaked 60 GB of data from another Canadian company.

Alleged leak of The Source, a Canadian electronics chain
A representative from Trans-Northern reached out to The Register to confirm that the company “encountered a cybersecurity breach in November 2023, affecting a select few of our internal computer systems,” and is currently investigating the recent claims made by the ransomware group.
They stated that the incident was swiftly managed with the assistance of third-party cybersecurity specialists, ensuring the ongoing safe operation of our pipeline systems, and they are cognizant of the dark web posts alleging possession of our company’s data and are actively looking into these assertions.
Therefore, the similarities between the Trans-Northern and Colonial Pipeline incidents are striking, not only in the nature of the attack but also in the potential for widespread disruption. Both incidents involved the targeting of critical pipeline infrastructure, the use of ransomware or extortion tactics to lock and steal data, and the looming threat of significant operational and economic disasters.
However, there are also differences worth noting. The Colonial Pipeline attack led to a proactive shutdown of the pipeline’s operations, fuel shortages, and public panic, highlighting the real-world consequences of such cyber attacks. In contrast, it seems like the immediate response of Trans-Northern Pipelines to the ALPHV attack has been to engage cybersecurity experts and law enforcement, aiming to contain a possible breach and maintain operations for now.
Possible Impact
If data leak claims are valid the cyber attack on Trans-Northern Pipelines could act as a catalyst for policy and regulatory change. Governments and regulatory bodies may see this as an impetus to introduce stricter cybersecurity standards and reporting requirements for critical infrastructure operators. There’s a growing recognition of the need for a unified approach to cybersecurity, one that includes public-private partnerships, shared intelligence, and coordinated response mechanisms.
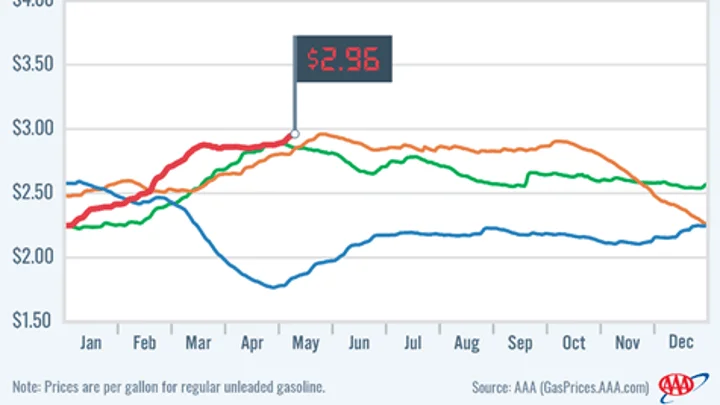
An impact that did not occur within this incident, the gas price jump around the Colonial Pipeline incident (AAA)
Moreover, this incident may prompt a reevaluation of international norms and laws regarding cyber activities and ransomware just like the Colonial Pipeline incident. With ransomware gangs often operating across borders, international cooperation becomes essential in tracking, prosecuting, and dismantling these networks. The global nature of cyber threats necessitates a concerted effort among nations to establish legal frameworks and collaborative initiatives aimed at curtailing the reach and impact of cybercriminals.
US State Department’s Reward for Information on ALPHV/BlackCat Ransomware
A bounty program was published right after this pipeline incident. On February 15, 2024, the US Department of State announced a reward of up to $15 million for information leading to the identification, location, or conviction of key figures within the ALPHV/BlackCat ransomware group. This includes up to $10 million for information on individuals holding leadership roles and up to $5 million for information leading to the arrest and/or conviction of anyone attempting or conspiring to participate in the group’s ransomware activities. This initiative highlights the global effort, including cooperation with law enforcement agencies from several countries, to combat the ransomware threat that has impacted over 1,000 entities worldwide. The announcement emphasizes the severity of ransomware attacks and the commitment to disrupting criminal activities threatening global security. For more details, visit the official announcement.
Conclusion
The attack serves as a potent reminder of the persistent and evolving threat that cybercriminals pose to critical infrastructure worldwide. This incident, set against the backdrop of ALPHV’s sophisticated operations and recent developments in their tactics, underscores the urgent need for a comprehensive, multi-layered approach to cybersecurity. The implications of such attacks extend far beyond the immediate disruption, posing significant risks to national security, economic stability, and public safety.
To mitigate these threats and enhance the resilience of critical infrastructure, it is imperative that organizations adopt advanced cybersecurity measures, leveraging the latest in threat detection and response technologies. Equally important is the cultivation of a cybersecurity-aware culture, where employees at all levels understand the risks and their role in safeguarding the organization’s digital assets. Incident response plans must be robust and regularly updated, ensuring swift action can be taken to minimize the impact of any breach.
Collaboration emerges as a critical theme in the fight against cyber threats. Public-private partnerships can facilitate the sharing of threat intelligence and best practices, enhancing the collective defense against cybercriminals. Additionally, international cooperation is crucial in addressing the cross-border nature of cybercrime, enabling the pursuit and prosecution of cybercriminals regardless of their location.
How Can SOCRadar Help?
The SOCRadar Cyber Threat Intelligence suite offers a variety of tools and functionalities designed to assist in the detection and prevention of ransomware attacks. Through the Threat Hunting feature, users can delve into billions of records to search for Indicators of Compromise (IoCs) and obtain relevant attribution data. In addition to manual searches during incident response activities, the integration of Threat Hunting data into your Security Orchestration, Automation, and Response (SOAR) systems is streamlined through a Restful API.
This integration enables the creation of custom feeds that can be incorporated into your security technologies, including Security Information and Event Management (SIEM) systems, Firewalls (FW), and Endpoint Detection and Response (EDR) platforms. These technologies are equipped to monitor, detect, and block traffic from identified malicious sources, thus enhancing your organization’s defense against ransomware threats. Learn more on How to Use SOCRadar Integrations.

SOCRadar Attack Surface Management includes a Ransomware Check functionality
Customers are empowered to seamlessly incorporate these data collections into their security setups, such as SIEM, FW, and EDR solutions, to guard against ransomware incursions stemming from newly identified malicious URLs.
At SOCRadar, we are committed to continually refining and expanding our platform to meet your security needs, safeguarding your enterprise against cybercriminals and their evolving strategies, tactics, and procedures. We invite you to explore our platform and leverage its capabilities at no cost within minutes. Your feedback, opinions, and direct communication are highly valued as we strive to fortify your digital defenses.




































