
Ransomware Takes Its Route in a More Dangerous and Harmful Direction. What Do You Need to Know?
Ransomware is one of the biggest challenges and security problems on the internet and its costs are forecast to reach a record $20 Billion by 2021. It was predicted by security researchers that in 2021, a ransomware attack will take place every 11 seconds. Following statistics can give a better understanding of how ransomware attacks are getting more dangerous and harmful.
- 51% of businesses have been impacted by ransomware in the last year.
- 90 % of IT pros had clients that suffered ransomware attacks in the past year.
- 50% of IT professionals don’t believe that their organization is ready to defend against a ransomware attack.
- 85% of ransomware attacks target Windows systems.
What is ransomware?
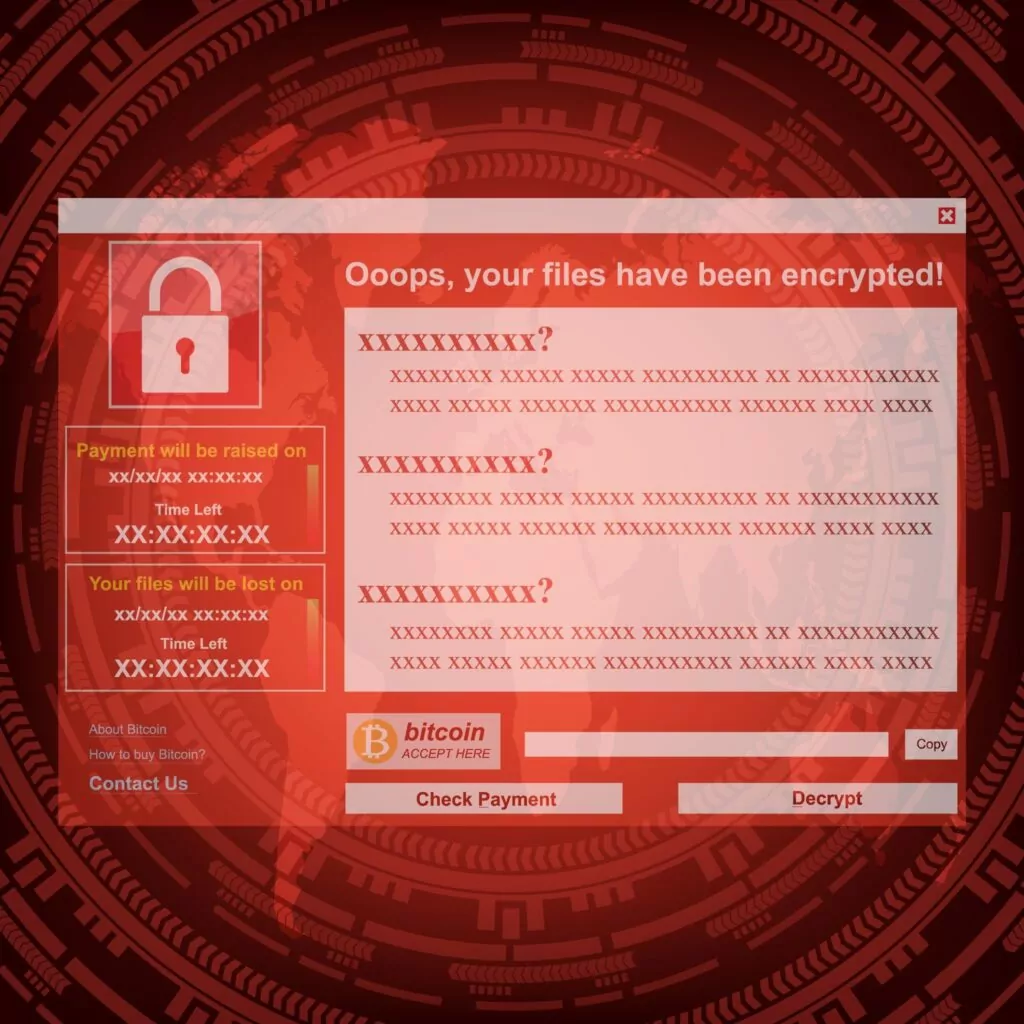
Ransomware is a kind of malware that encrypts files and documents from a single PC to a whole network including a server. Usually, victims have two options, paying ransoms to the adversaries by hoping that a decryption key works or restore their data from backups.
How did ransomware evolve?
Ransomware is a kind of malware that encrypts files and documents from a single PC to a whole network including a server. Usually, victims have two options, paying ransoms to the adversaries by hoping that a decryption key works or restore their data from backups.
Even though email phishing was the top attack vector behind ransomware, RDP is far and away from the most common initial attack vector nowadays as can be seen in the following figure.
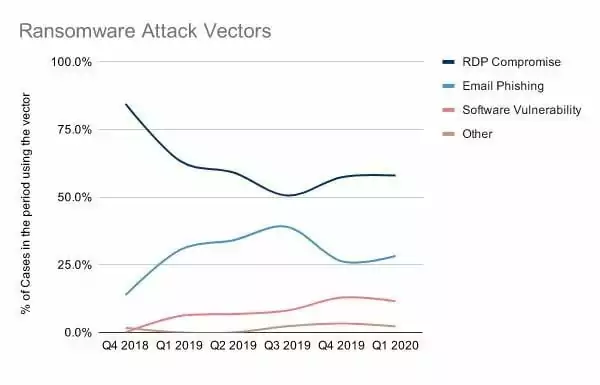
RDP is a formal process for remote system control to IT managers. However, any hackers who have connections to RDP endpoints will use networks to gain territory on an enterprise network and continue to expand their rights and access even further. Organizations can take a variety of actions to lock RDP endpoints, including the security of them with complex passwords and multifactor authentication.
Based on the recent report Remote Code Execution (RCE) vulnerabilities move to the top of the list for ransomware attacks.
Why is ransomware so successful?
What it requires is for a single user to slip and open a malicious email attachment or use a weak password for ransomware to access your network.
If companies would not send requests for ransom, hackers would stop using ransomware. However, companies require access to data to operate and they are ready to pay a ransom to get it done.
On the other hand, it is a very simple way to make money for cybercriminals. Why waste time and money designing complicated codes or creating false credit cards on the bank information if ransomware will lead to hundreds or even thousands of dollars in immediate payments from vast numbers of infected victims?
What are the top 5 ransomware attacks of 2020-2021?
- REvil Ransomware
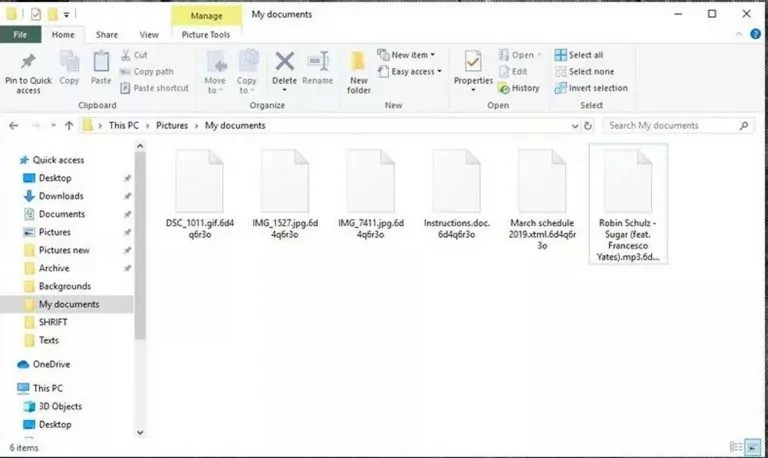
It was found that the Grubman Shire Meiselas & Sacks data leak was triggered by Revil Ransomware. Attackers compromised the data of famous clients and shared it on the dark web.
According to news, this Ransomware attack has been able to access personal information from Drake, Robert De Niro, Rod Stewart, Elton John, Mariah Carey, among several other actors. Screenshots have also leaked from the machine files of celebrities such as Madonna Tour, including Bruce Springsteen, Bette Midler, and Barbra Streisand files.
Source: https://www.keepnetlabs.com/top-11-ransomware-attacks-in-2020-2021/
- Sodinokibi Ransomware
In September 2019, it circulated across the Oracle Weblogic servers with a zero-day vulnerability. Later, though the flaw was corrected, malware installers with remote servers and other backdoor insecure vulnerabilities and resources to abuse this ransomware started to propagate.
Source: https://www.keepnetlabs.com/top-11-ransomware-attacks-in-2020-2021/
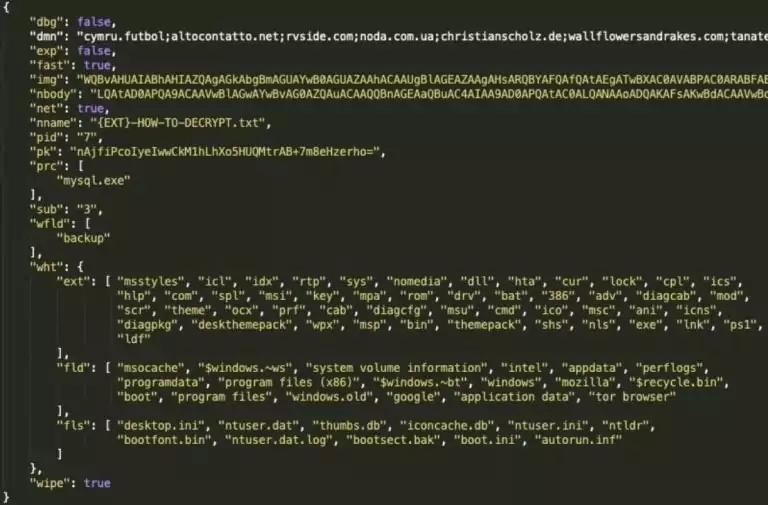
When activated on the target, Sodinokibi ransomware, due to its configurable structure, can process certain things that are mentioned below:
- Expanding one’s authorization by using CVE-2018-8453 weakness.
- Preventing resource conflict by ending blocked projects.
- Deleting files that are in the blocked list
- Encrypting mobile or web drivers that have not yet been taken to the whitelist.
- Transferring the system data to the attacker that belongs to the target.
- Nemty Ransomware
Unlike other ransomware, Nemty behaves like a ransomware service. It was published on the Russian pirated forum websites regularly when it first appeared. It operated from the summer of 2019 to the summer of 2020.
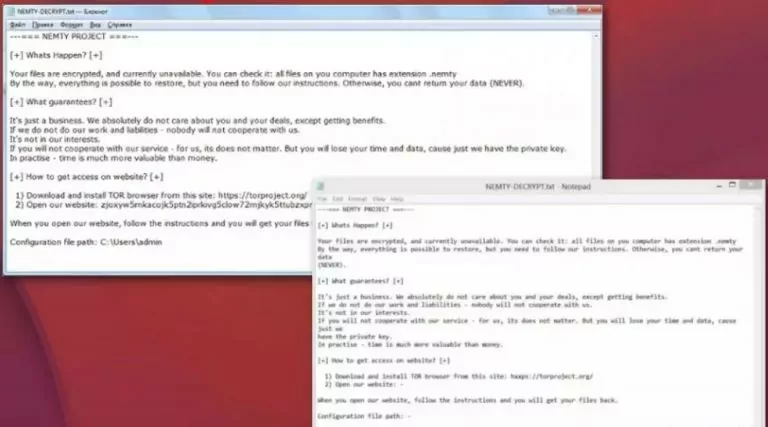
Source: https://www.keepnetlabs.com/top-11-ransomware-attacks-in-2020-2021/
During the period when RaaS (Ransomware as a service) served actively, its clients could use a portal allowing them to build a specific edition of Nemty Ransomware. These copies could subsequently be disseminated in a manner that clients favor.
- Nephilim Ransomware
When it first emerged, researchers found that the resource codes of Nephillim are somewhat like Nempty ransomware. The architecture was the same as the codes and not just the codes were identical. In case they do not pay the ransom requested, they menaced their victim with the publication of sensitive data.
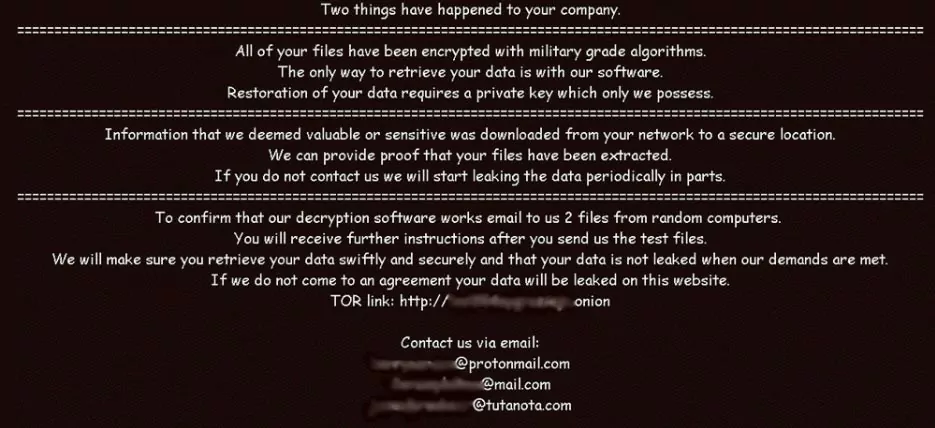
Source: https://www.keepnetlabs.com/top-11-ransomware-attacks-in-2020-2021/
The casualties of Nephilim were typically large corporations and organizations. In December to target governmental organizations, by using the vulnerability that they found in the devices of Citrix Gateway. In addition, the insecurity of a remote desktop network and VPN may be used to encrypt victim data.
The ransom note stresses that the data were encrypted by an algorithm at the military level and confidential data were violated. Nephilim attackers need two encrypted files from victims, decrypt them and return them to the victims to show their authority.
- NetWalker Ransomware
Also known as Mailto, Netwalker is one of the latest variations of ransomware. Governmental agencies, healthcare organisations, corporations, remote employees are targeted by NetWalker-using attackers.
Source: https://www.keepnetlabs.com/top-11-ransomware-attacks-in-2020-2021/
NetWalker uses the victim’s network to encrypt all computers in Windows. It uses a ransom note and filenames setup.
NetWalker follows two separate approaches.
A) Coronavirus phishing mails
B) executable networked files.
NetWalker is one of the most disruptive malware apps for 2020-2021.
Why should businesses worry about ransomware?
Simply put, ransomware can destroy your business. It will affect your profits if you are locked out of your own malware files for even a day. But because ransomware keeps at least one week or even months with most of its victims offline, the losses can be substantial. Systems go offline for too long not only because malware locks the system, but all the time it takes to clean the networks up and recover them.
How do you prevent a ransomware attack?
Following measures can help to prevent ransomware attacks ;
- Implement an awareness and training program. Because end users are targets, employees and individuals should be aware of the threat of ransomware and how it is delivered.
- Enable strong spam filters to prevent phishing emails from reaching the end-users and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
- Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
- Configure firewalls to block access to known malicious IP addresses.
- Patch operating systems, software, and firmware on devices. Consider using a centralized patch management system.
- Set anti-virus and anti-malware programs to conduct regular scans automatically.
- Manage the use of privileged accounts based on the principle of least privilege: no users should be assigned administrative access unless absolutely needed, and those with a need for administrator accounts should only use them when necessary.
- Configure access controls—including file, directory, and network share permissions with the least privilege in mind. If a user only needs to read specific files, the user should not have write access to those files, directories, or shares.
- Disable macro scripts from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
- Implement Software Restriction Policies (SRP) or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/decompression programs, including the AppData/LocalAppData folder.
- Consider disabling Remote Desktop Protocol (RDP) if it is not being used.
- Use application whitelisting, which only allows systems to execute programs known and permitted by a security policy.
- Execute operating system environments or specific programs in a virtualized environment.
- Categorize data based on organizational value and implement physical and logical separation of networks and data for different organizational units
Is there any useful tool to prevent ransomware attacks?
Threat actors are closely monitoring vulnerability trends as much as your public-facing services and technology to find the easy way in. To prevent them disrupt your business, get alerted whenever there’s a new critical vulnerability or exploit for the pre-defined product components and technologies associated with your auto-discovered digital footprint. See which vulnerabilities are being leveraged by threat actors. Get actionable insights and context on potentially vulnerable technologies to speed up the assessment and verification processes.
SOCRadar notifies and informs you immediately when;
- Critical ports are opened such as RDP port,
- There is a critical vulnerability for your attack surface,
- Any sensitive information or data available about your organization on the dark web.
SOCRadar vulnerability intelligence;
- Tailored for you: Select products and technologies you’d like to monitor.
- Twitter CVE trends: See the worldwide vulnerability trends by monitoring millions of tweets.
- Instant alerting: Rapid data collection, structuring, and analysis to notify on-time.
- Filter and search: : Find vulnerability information by filtering based on keyword, CVSS score, or report time.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.



































