
SOCRadar Singapore Threat Landscape Report: Excessive Increase in Cyberattack Attempts
The cyber security agenda is shaken every day with brand-new threats and methods developed by malicious actors. We see the effects of the developments in these attack techniques in countries where capital accumulation is intense, such as Singapore.
With the SOCRadar Threat Landscape Reports we issue regularly, we provide a regional, national and sectoral view of cyber incidents and various dark web threats. Thus, we help security leaders to see the future more clearly and help companies make investment decisions.
Download the SOCRadar Singapore Threat Landscape Report here.
54 Threat Actors Target Singapore Companies
Deep & dark web investigations by the SOCRadar CTIA team revealed the malicious activity of threat actors against Singapore businesses. Over the past year, we have detected a significant increase in customer data sales associated with attacks.
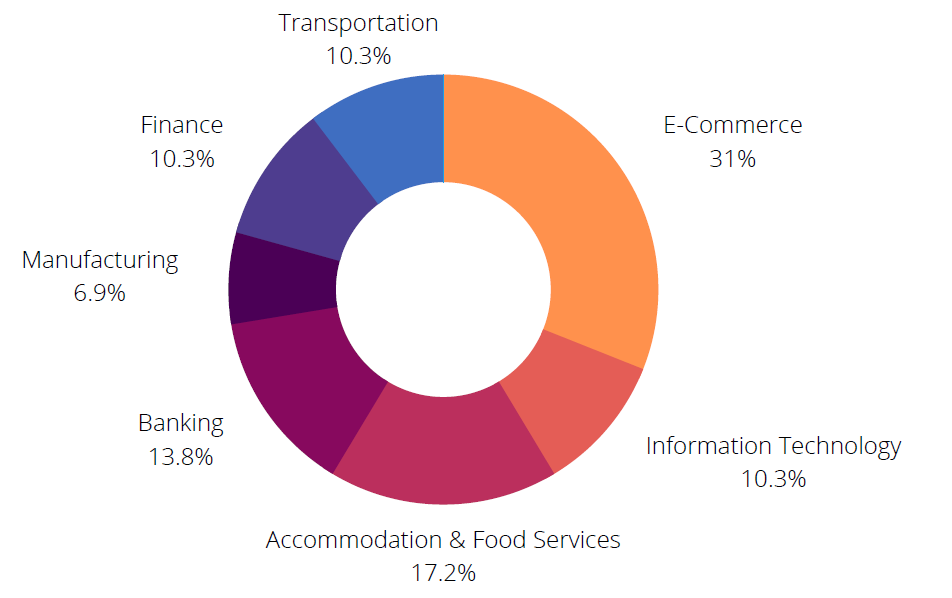
SOCRadar found that 70 dark web posts targeting Singapore belong to fifty-four threat actors. According to the intelligence data we obtained from SOCRadar DarkMirror, most posts concern the E-commerce and Accommodation & Food Services sectors.
Manufacturing Industry #1 Among Victims of Ransomware
We witnessed extensive damage caused by ransomware attacks in 2021. Ransomware caused financial damage to organizations by causing the loss of important data, and sometimes even public services were disrupted due to threat actors blocking access to the system.
Ransomware attacks have become a major threat in Singapore as well as around the world. Notorious ransomware gangs have announced 79 new victims associated with Singapore. 75% of the victims are from the manufacturing, information technology, and construction industries. The most active ransomware gangs were Conti, LockBit 2.0, and AlpVM BlackCat.
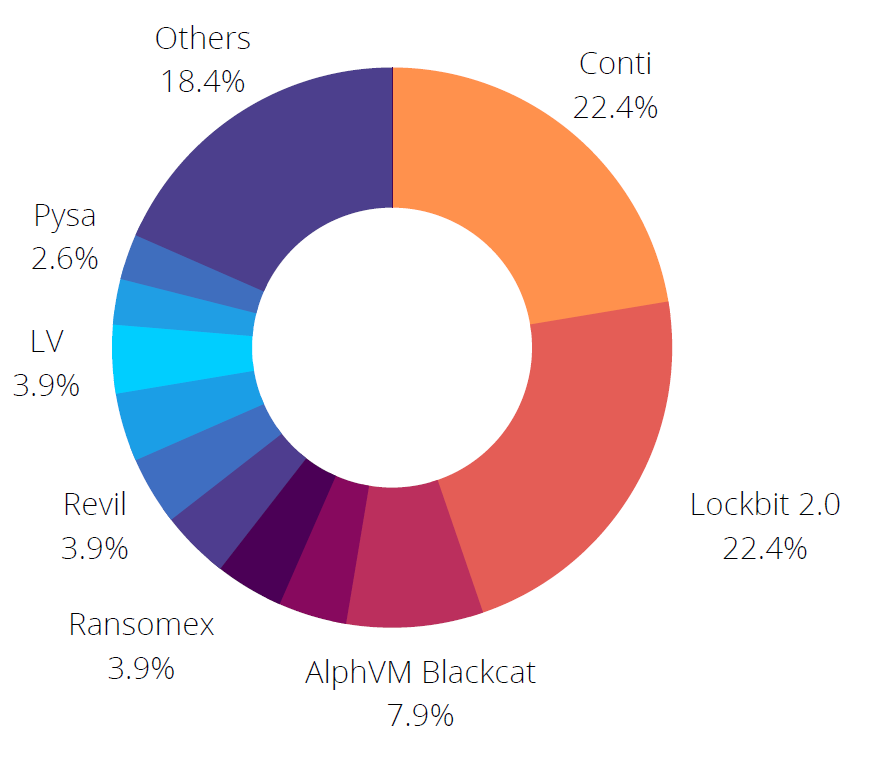
According to SOCRadar analysts’ investigations of ransomware attacks, more than 40% of victim organizations refused to pay the ransom, and threat actors leaked their data.
The Most Active Four APT Groups are State-Sponsored
State-sponsored APT groups can carry out large-scale cyberattacks to pursue their hidden agendas. SOCRadar analysts found that these groups, which target many state- or non-government organizations in Singapore, are mostly linked to China and Vietnam.
Looking closely at the activities of APT groups, the CTIA team thinks that the first three of the 14 APT groups active in Singapore are associated with the Chinese government and the fourth with Vietnam.
Some of the APT groups most targeted Singapore are:
- APT41 (Double Dragon): Known for its Chinese government-sponsored cyber espionage activities and independent attacks with financial motivations.
- APT30 (Naikon): It managed to steal sensitive data from many critical systems with the backdoor called “RainyDay,” opened to carry out cyber espionage activities on military forces in APAC countries. Apart from Singapore, it is known to be active in countries such as Indonesia, Thailand, and Malaysia.
- APT32 (OceanLotus): Vietnam-backed group attacks foreign companies investing in different sectors and Vietnamese human rights organizations and activists. The group’s interests fully coincide with those of the government.
Click here to get more insights and deep dive into our findings.




































