How to Build a Proactive Incident Response Plan?
Some standard cybersecurity measures are endpoint security tools, such as VPNs, proxies, antimalware, and employee cybersecurity awareness training. Despite all these precautions, sometimes employees can fall victim to social engineering attacks due to unawareness and ignorance. At this very point, the proactive incident response comes into play.
What is Proactive Incident Response?
This forms various consequences such as unauthorized access, mistrust among partners, data theft, economic loss of clients, and regulatory fines. At this point, having a proactive incident response plan would diminish the harmful effects of these consequences.
Incident response is an organization’s process of reacting and defense systems to IT threats such as security breaches, cyberattacks, and server downtimes. An incident response plan is designed so that the security team can make an outline, plan and improve strategies against cyberattacks.
The incident response steps consist of a framework for detecting and interfering with cyberattacks and threats. It describes the cyberattacks to be understandable, and it decides which tools, measures, and actions are necessary in case of coping with the cyberattacks.
Why Do Companies Build a Proactive Incident Response Plan?
Many essential reasons an organization needs a proactive incident response plan. One of the main reasons is to provide data protection. Data protection is vital to a company because the data includes a lot of sensitive private information such as customer and employee information or company plans. When malicious people steal this information, stolen data can be used to initiate ransomware attacks, social engineering attacks, and identify theft for clients and employees.
The other main reason is to protect organizations’ financial structures. A data breach or cybersecurity incident can risk an organization’s finances. The result of cyber attacks is not only limited to loss of income. Cyber attacks can also result in fines, criminal investigations, and out-of-service. Therefore, organizations should respond effectively to cyber incidents to experience financial and reputational damage.
The last main reason is to ensure reputational integrity and customers’ trust. Loss of reputation and customers is one of the possible consequences of cyber attacks. If companies fail to cope with a security breach and mismanage the process, their reputation and integrity will destroy. This situation leads to disrupting customer relationships with an organization and tainting reputation. Therefore, proactive incident response is essential to protect the company’s reputation and customers’ future.
How to Build a Proactive Incident Response Plan?
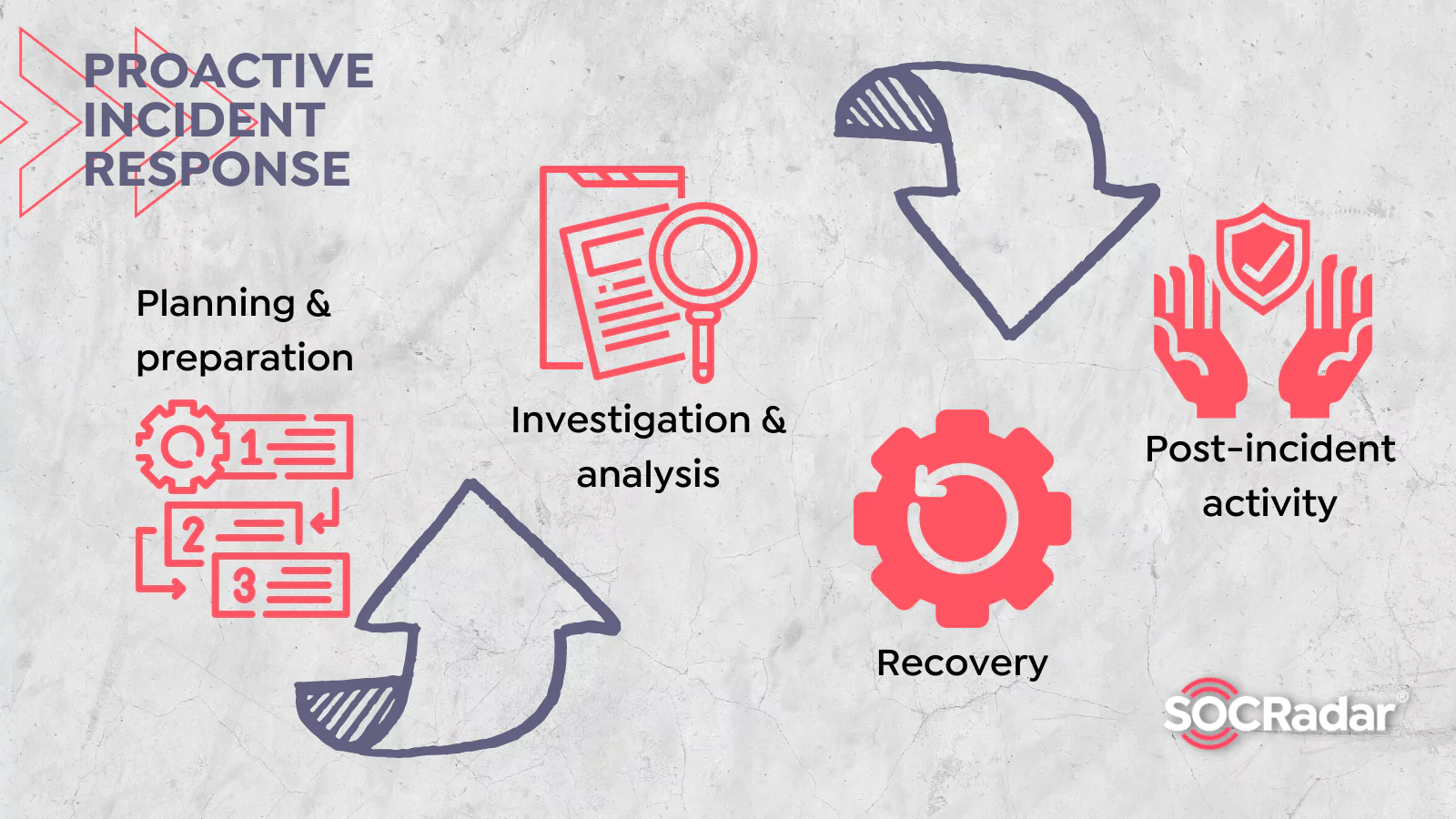
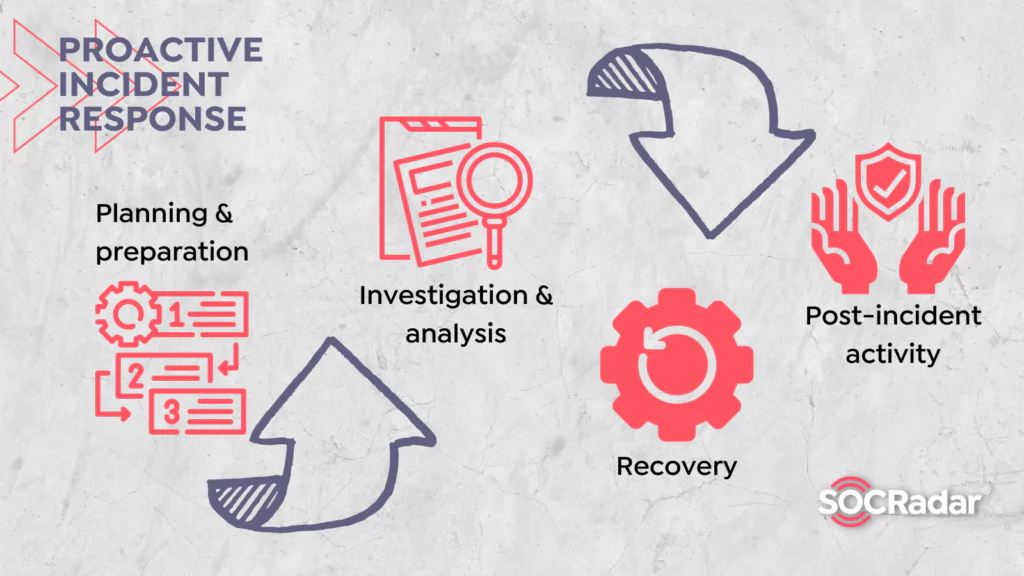
Incident response plans are created to help an organization sustain the damages that formed in cyber attacks. Many companies assume they are ready for cyber-attacks using a residential proxy, VPN, or antimalware software, but more logical and comprehensive approaches are needed. Therefore, it is crucial for a proactive incident response plan to include all the necessary steps. A proactive indecent response plan consists of the following essential elements:
Planning & Preparation:
Planning and preparedness are critical components of a proactive incident response strategy. An organization company needs to plan what endpoint security tools it needs. To ensure data security, it should be required to utilize various security technologies like VPNs, antimalware software, and password managers.
Organizations must also ensure data encryption is part of a proactive response plan. Additionally, the organization should develop channels for information security teams to communicate about any security issue. These communication channels need to be ready to function correctly during and after a security incident.
Identification & Investigation:
Employees must have a standardized channel of reporting security issues to guarantee that the security team is informed of any incidence within the organization quickly and effectively. To proactively identify cyber threats, the security teams should also have automated endpoint technologies that detect and gather real-time data about existing and potential threats.
To ensure ongoing threat identification and monitoring, the organization should run regular cyber threat intelligence programs and create thorough threat monitoring and detection systems. Additionally, firms must have routine cyber compromise assessment processes to find holes in their security system.
Analyzing Security Incidents:
Another crucial component of a proactive incident response plan is a detailed cyber incident investigation. The security team should perform a thorough examination of the incident to ascertain the degree of its influence to guarantee that there is little harm as a result of the cyber security incident. The security team’s study should emphasize on:
- Examining the systems and security networks to find the evidence of the incident the threat actor left behind
- Document the affected systems, networks, devices, and accounts and conduct a thorough study to identify the extent of the incident.
- Analyze the tools or binaries used by the malicious actor to carry out the attack.
- Such evaluations will help the organization choose the best course for repairing the harm and stopping further assaults.
Containment & Eradication
The security team manages the event using their intelligence and analysis. The team assures preventing the organization from more harm while minimizing risky behaviors. The security team also shuts down all the infected systems in a coordinated manner to contain these damages until the threat is reduced. In addition, the security personnel should meticulously update the login information for every account and clean up and rebuild every operating system within the company.
The security team starts working on preventing communication from those domains as soon as it has successfully identified the domain and IP addresses of the malicious actors. The security team also patches the security framework and eliminates current dangers.
Recovery
The organization returns the business to its standard forms throughout the recovery phase. The security team concentrates on creating risk mitigation and remediation plans. These tactics are based on confirmed instances, guaranteeing the company is safeguarded against additional security incidents.
Post Incident Activity
The team examines the incident and the incident response. They gather all the takeaways and record all the pertinent information about the incident. The gathered information is also used to decide on the near-term risk monitoring procedures. The team also collects evidence that would be useful to pass along to law enforcement. The phase attempts to reduce the likelihood of such incidents and create a more robust incident response plan.
In conclusion, a proactive incident response plan goes beyond preparing to respond to a security issue, given the ongoing evolution of the cyber threat landscape. The proactive program ensures the firm is prepared to respond to cyber incidents effectively and fully recover from them without suffering irreparable harm.