
Top 10 Major Cyber Attacks Targeting E-Commerce Industry
The e-commerce industry has transformed global commerce, offering convenience and accessibility to millions of consumers worldwide. However, this digital evolution has also made it a prime target for cybercriminals. Beyond well-known threats like ransomware and data breaches, the sector faces sophisticated attacks including phishing, payment skimming, and fraud.

AI illustration of cyber attacks targeting e-commerce industry
These threats not only disrupt business operations but also erode consumer trust—an essential element for the success of any e-commerce platform. As the attack surface continues to expand with increasing reliance on digital tools, it is crucial for businesses to recognize these risks and implement robust security measures.
In this article, we examine the diverse and evolving threat landscape targeting e-commerce platforms, analyzing the methods used by cybercriminals, real-world incidents, and practical steps businesses can take to mitigate these risks.
Dark Web Statistics Highlighting Risks to the E-Commerce Industry
The e-commerce industry has become a prime target for cybercriminals, ranking fifth among industries for ransomware attacks, accounting for 6.77% of all such incidents globally. Threat actors on the dark web frequently exploit vulnerabilities in the sector, using forums to trade sensitive data, sell access, and launch cyberattacks.
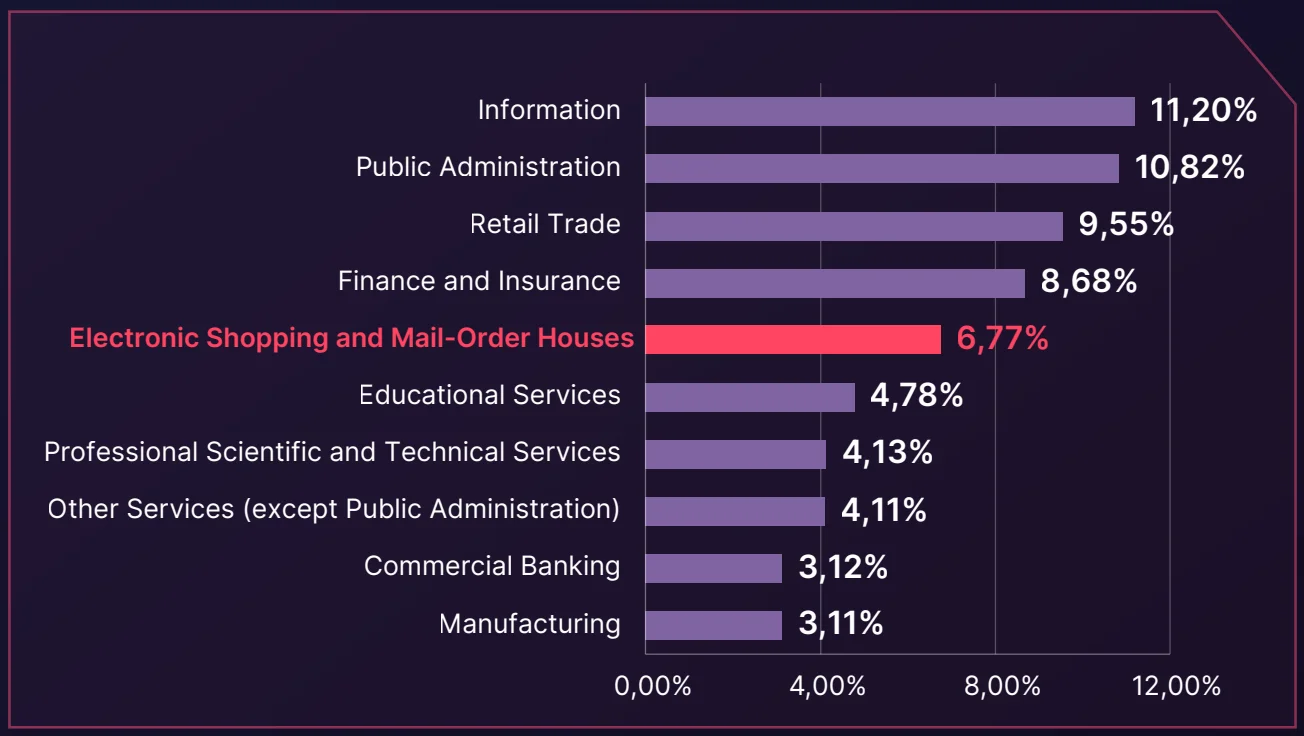
Distribution of dark web threats by industry
The U.S. leads as the most targeted country in the e-commerce sector, accounting for 17.16% of all dark web posts. Following closely are the UK at 7.20% and India at 5.11%, reflecting a global distribution of threats that primarily focus on regions with significant e-commerce activity.
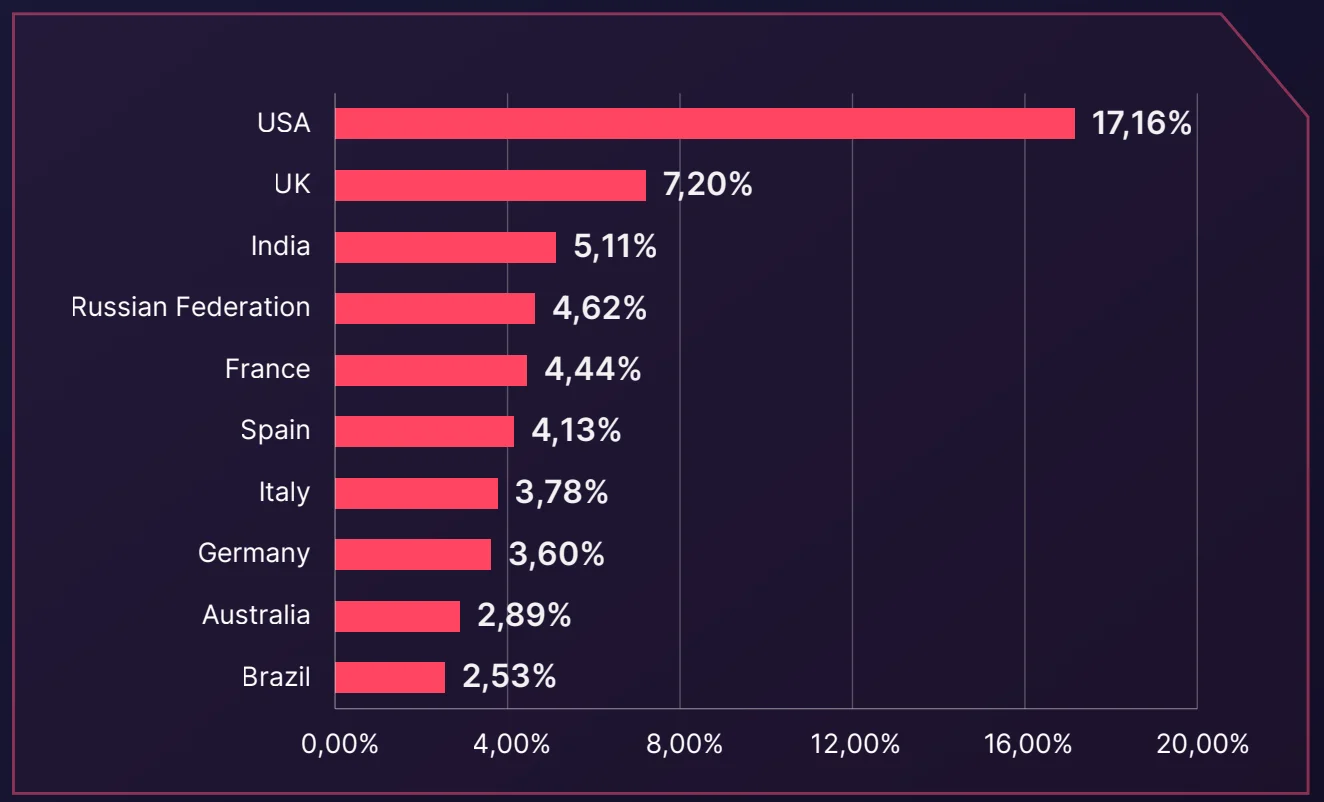
Distribution of dark web threats by primary target country
Threat actors engage in various illicit activities, with Access sales (46.82%) topping the list. This category includes unauthorized access to systems, databases, or accounts, enabling further exploitation.
- Data-related content follows at 41.22%, where sensitive customer data, including emails, addresses, and financial information, is often sold or shared.
- Website attacks, such as defacements and DDoS campaigns, make up 10.53% of the posts, aiming to disrupt services or damage reputations.
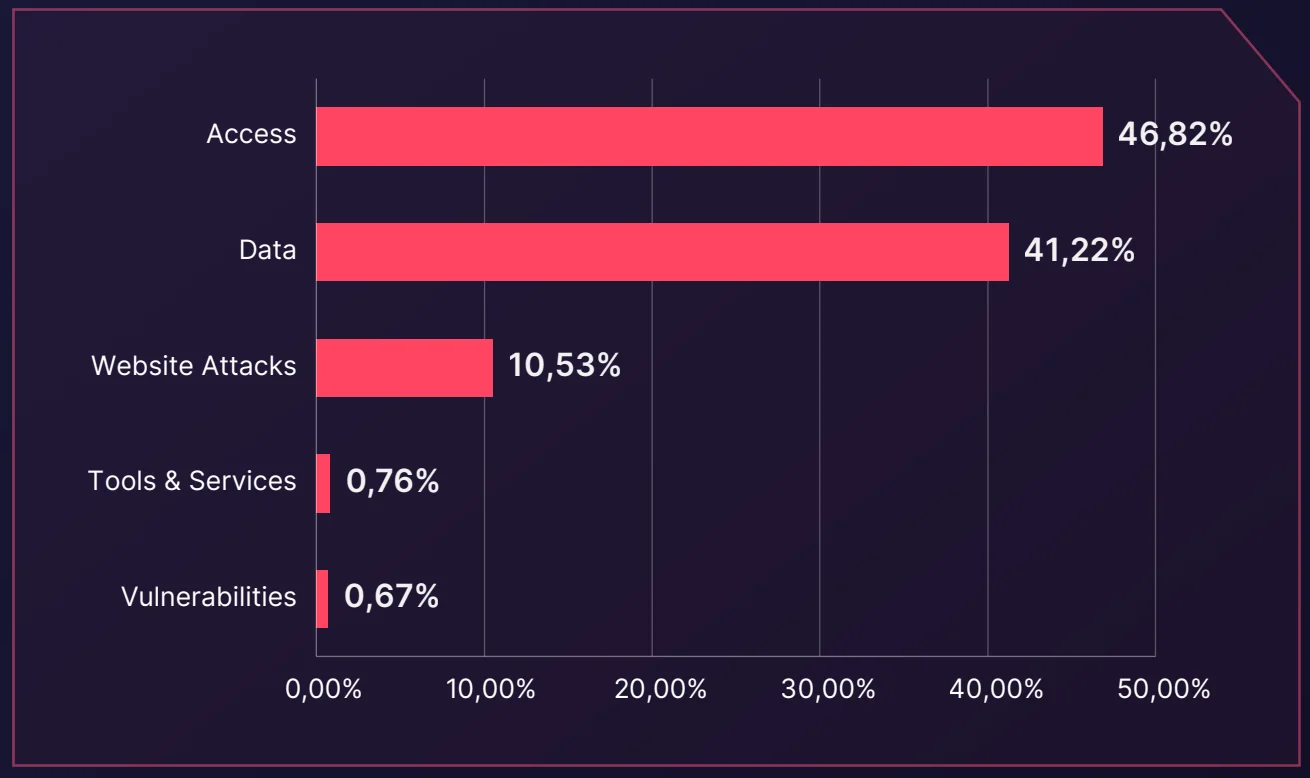
Distribution of dark web threats by threat type
SOCRadar’s Dark Web Monitoring Module plays a critical role in uncovering illicit activities threatening the e-commerce sector. From credential dumps to unauthorized access sales, SOCRadar provides actionable insights into emerging risks, helping businesses secure their sensitive assets. Recent findings include:
- Over 686,644 stolen email-password combinations,
- 29,925 compromised credit card details,
- Threat intelligence indicating a global impact, with hotspots in India, the U.S., and Brazil.
This data underscores the importance of integrating dark web threat intelligence into cybersecurity strategies to mitigate financial and reputational damage.
SOCRadar Dark Web Monitoring
Dark Web Activities Targeting the E-Commerce Industry
1. Millions of Taobao Users’ Personal Information Exposed
A significant data exposure has reportedly affected millions of users on Taobao, one of China’s leading e-commerce platforms owned by Alibaba. According to Cybernews, researchers discovered an unprotected Elasticsearch cluster containing 11.1 million records, including names, phone numbers, and home addresses. Each record is believed to correspond to a Taobao user.
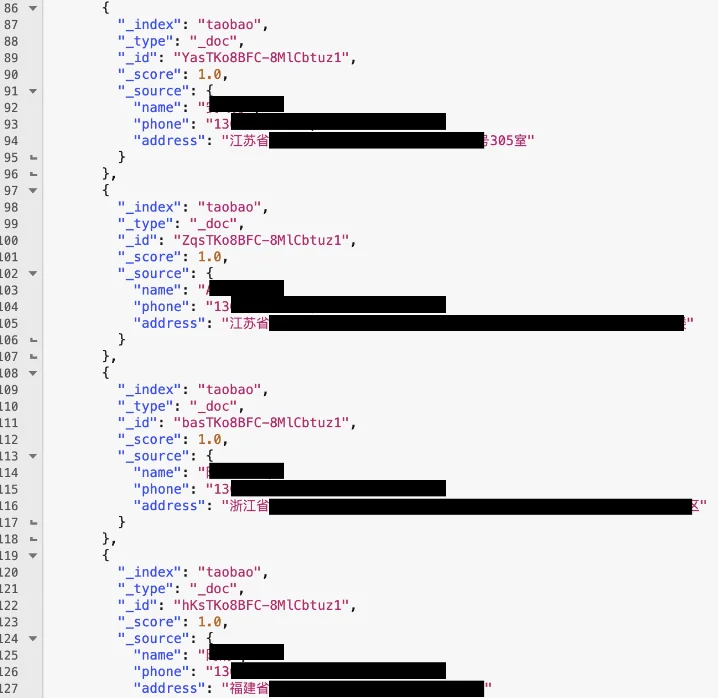
A sample of the exposed data (Cybernews)
While Taobao has denied any data leak, stating that their analysis of the sample data provided did not indicate a breach, Cybernews researchers warned about the potential risks. Exposed data of this nature can be exploited for identity theft, phishing campaigns, and other malicious activities, endangering the platform’s users.
This incident aligns with earlier security concerns for Taobao, such as the 2020 exposure of user data through unauthorized web scraping.
2. Ticketmaster Data Breach: Millions of Records and Event Tickets Exposed
The Ticketmaster data breach of 2024 stands out as a significant cyber incident involving multiple threat actors and escalating data leaks. The breach has exposed sensitive user information and ticket data, impacting millions of users and causing severe implications for Ticketmaster’s operations and reputation.
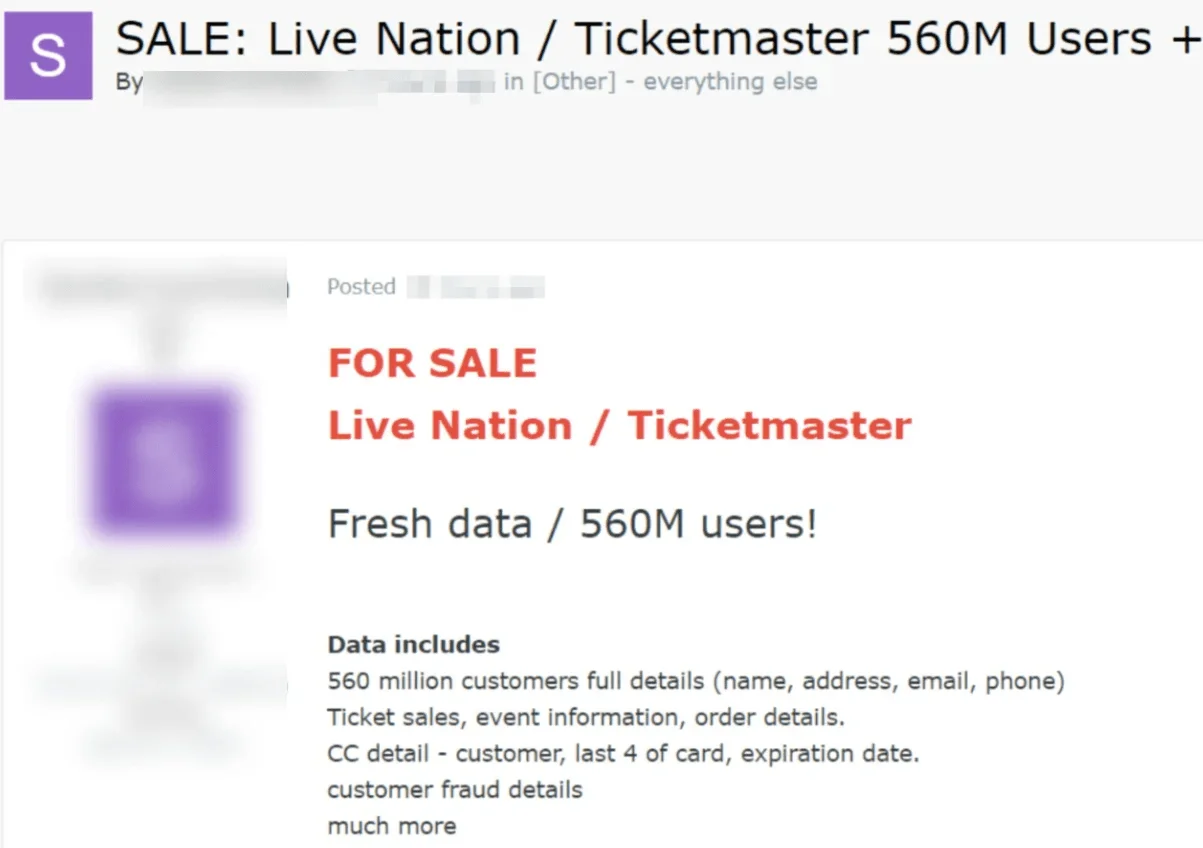
Ticketmaster data breach post by SpidermanData
On May 27, a threat actor named SpidermanData claimed access to Ticketmaster’s systems on a hacker forum, offering 560 million user and financial records for $500,000. The dataset allegedly included personal information such as names, email addresses, addresses, phone numbers, order details, event information, and partial credit card details.
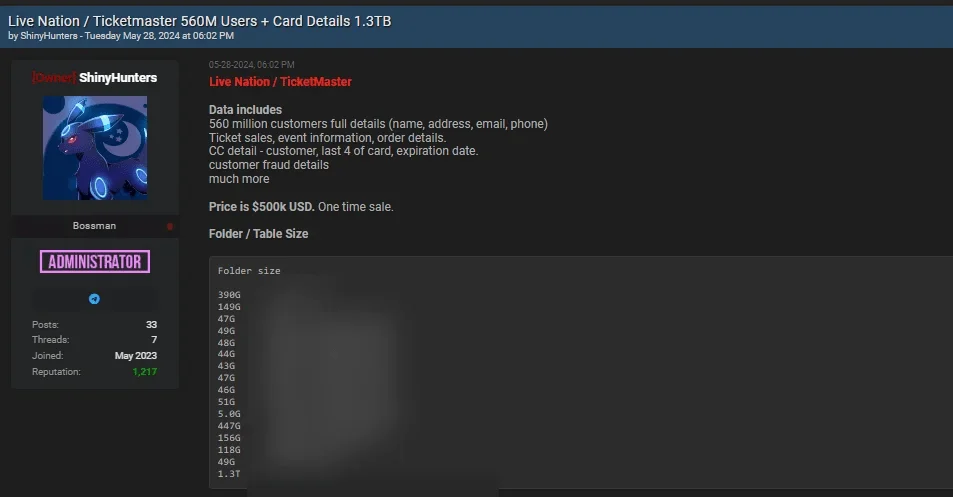
Mirrored Ticketmaster data breach post by ShinyHunters
A day later, the hacking group ShinyHunters mirrored SpidermanData’s post on another forum.
On May 31, Live Nation, Ticketmaster’s parent company, confirmed the breach in a filing, attributing it to unauthorized access to a third-party cloud database detected earlier in May.
The incident escalated further on June 20 when Sp1d3r, a rebranded version of SpidermanData, leaked a sample of 1 million Ticketmaster user records, citing the company’s failure to respond to extortion attempts. The leaked data included personal details such as names, emails, addresses, birth dates, and partial credit card information.
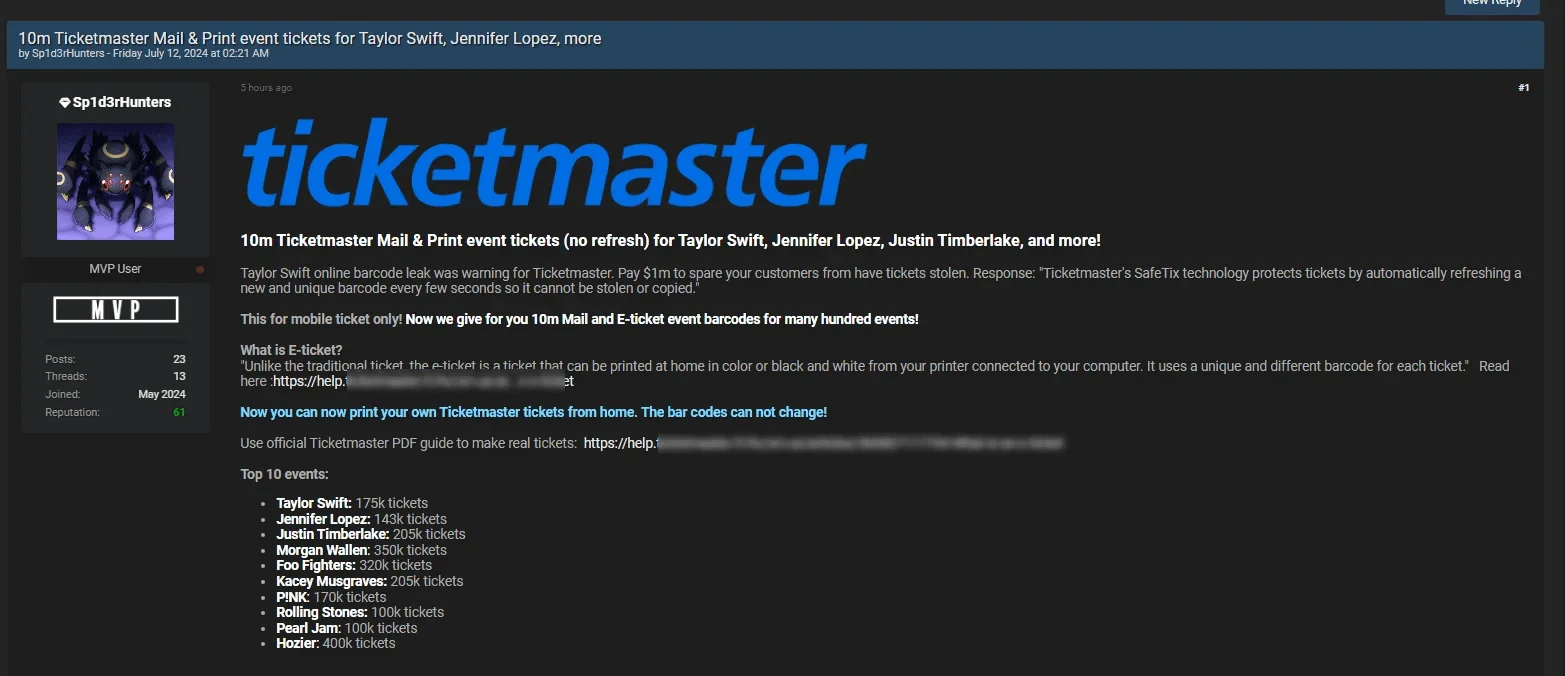
Ticketmaster event tickets leak post
In early July, ShinyHunters claimed possession of 193 million barcodes, including 440,000
Taylor Swift tickets, and demanded $8 million from Ticketmaster after initially settling for $1 million. On July 5, Sp1d3rHunters, an evolved alias of Sp1d3r, leaked 170,000 Taylor Swift event barcodes, threatening to release data for 30 million more events unless Ticketmaster paid $2 million.
Further leaks followed, including 30,000 TicketFast barcodes on July 8 and 10 million mail and print tickets on July 12, affecting high-profile events and artists.
SOCRadar’s Supply Chain Intelligence
By utilizing SOCRadar’s Supply Chain Intelligence, businesses can detect vulnerabilities in third-party integrations, preventing access to critical cloud environments like Snowflake and Azure.
3. Threat Actor Claims Temu Data Breach, Platform Denies Allegations
Temu, a rapidly expanding e-commerce platform known for its budget-friendly offerings, has become the center of controversy after a threat actor, using the alias ‘smokinthashit,’ claimed to have stolen a database containing 87 million records. The alleged data includes usernames, IDs, IP addresses, full names, dates of birth, gender, shipping addresses, phone numbers, and hashed passwords. The threat actor attempted to sell the purported data to other cybercriminals, publishing samples on underground forums.
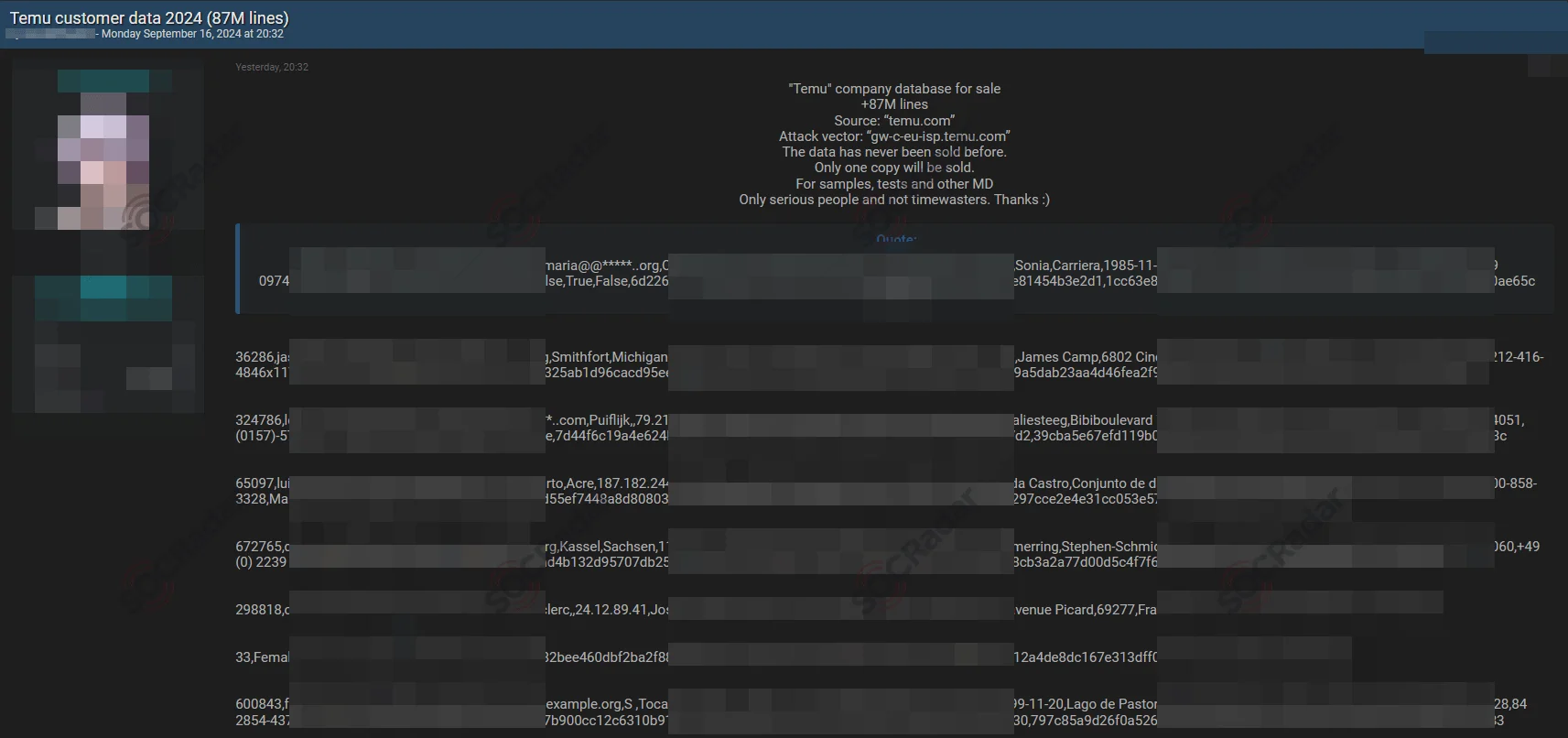
Alleged Temu data breach post
In response to the claims, Temu firmly denied any data breach. Speaking to BleepingComputer, the company stated, “Temu’s security team has conducted a comprehensive investigation into the alleged data breach and can confirm that the claims are categorically false; the data being circulated is not from our systems. Not a single line of data matches our transaction records.”
The platform emphasized its commitment to user security and privacy, describing the allegations as a deliberate attempt to damage its reputation. Temu also mentioned plans to pursue legal action against those responsible for spreading false information and attempting to profit from the claims.
The threat actor was banned from BreachForums for misrepresenting and attempting to sell data that was already publicly accessible.
4. Hot Topic Data Breach Exposes Over 54 Million Customer Records
Hot Topic, a popular retail brand known for its alternative fashion and pop culture merchandise, along with its affiliated brands Box Lunch and Torrid, has experienced a significant data breach. The breach compromised over 54 million customer accounts, exposing names, email addresses, physical addresses, phone numbers, purchase histories, and partially encrypted credit card details.
Cybersecurity firm Atlas Privacy confirmed that the database, approximately 730GB in size, contains weakly encrypted credit card data, which increases the risk of decryption. The compromised data spans from 2011 to October 19, 2024, suggesting potential lapses in data retention and security practices.

Threat actor claims to sell Hot Topic
The breach was first disclosed by a threat actor under the alias “Satanic” on BreachForums, who initially claimed to possess 350 million records and demanded $20,000. After failing to secure a buyer, the actor reduced the price to $4,000 and reposted the data on a Russian-speaking forum, sharing samples to validate the claim.
Investigators believe the breach originated from an information stealer malware infection. The malware compromised login credentials for a third-party data unification service used by Hot Topic, including access to cloud environments such as Snowflake, Azure, and Looker, highlighting vulnerabilities in third-party integrations.
5. PandaBuy Data Breach Exposes Over a Million Customer Records
Online shopping platform PandaBuy has fallen victim to a major data breach, reportedly compromising the personal information of over a million customers. Two threat actors, “Sanggiero” and “IntelBroker,” linked to the CyberNiggers group, exploited a vulnerability in the platform, exposing over 3 million records.
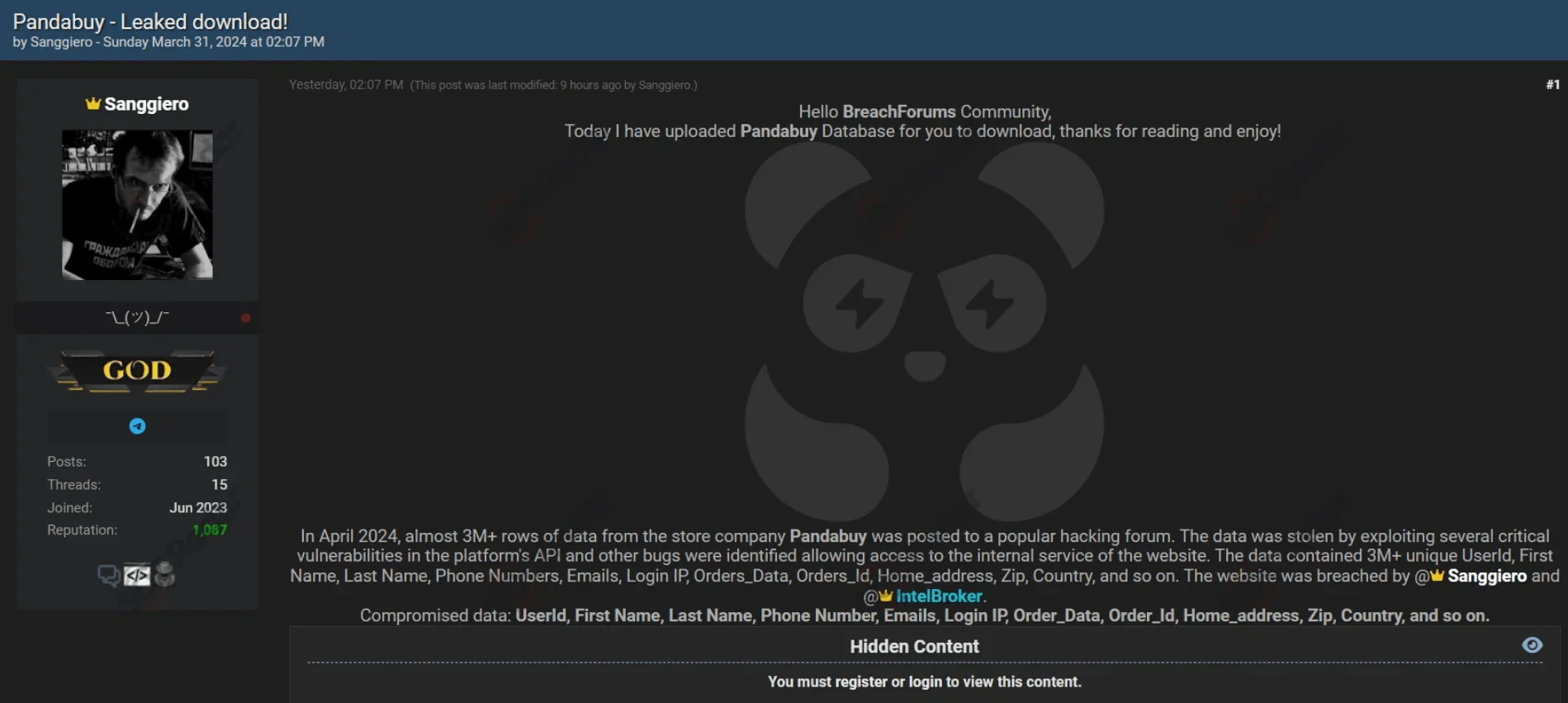
On March 31, Sanggiero claims to have breached PandaBuy
The leaked data includes names, usernames, emails, login IPs, order details, and addresses, posing significant risks for affected users. Have I Been Pwned (HIBP) verified that nearly 1.35 million valid accounts were impacted, underscoring the breach’s severity.
The threat actor Sanggiero initially leaked 1.3 million records but later claimed possession of PandaBuy’s entire database, consisting of 17 million records. In June 2024, this dataset was offered for sale on a hacker forum for $40,000. The stolen data is said to include employee credentials alongside customer information, raising further security concerns.
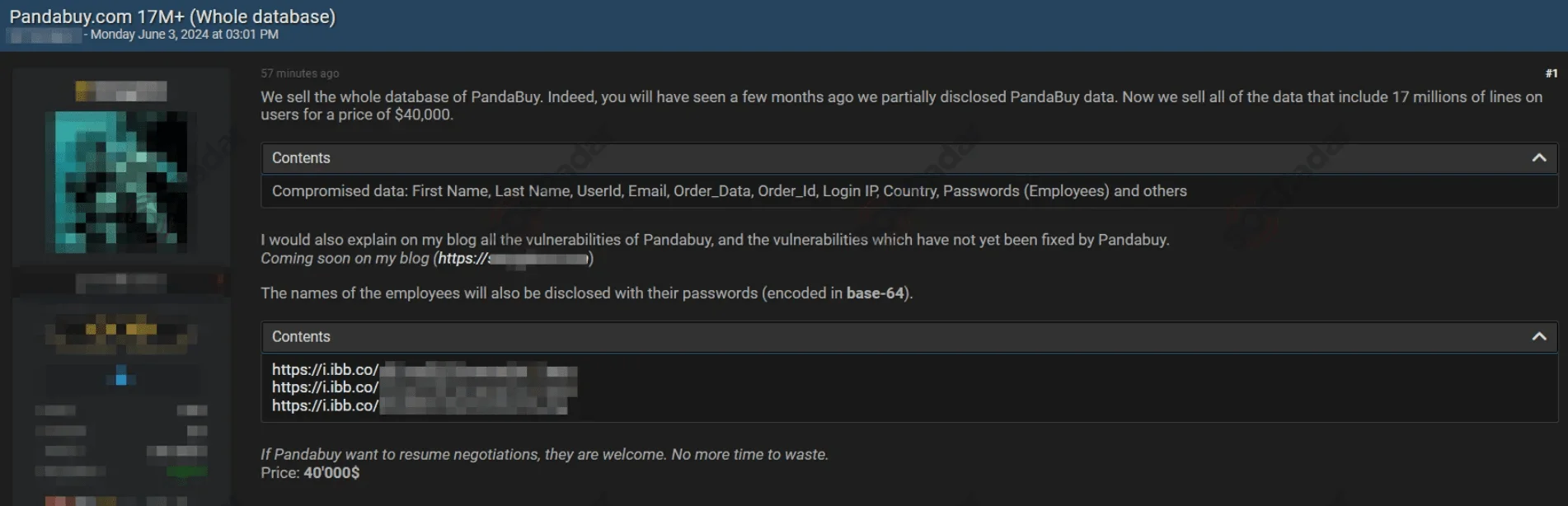
Second claims of Sanggiero
PandaBuy admitted to previously paying a ransom to prevent data leaks but now faces renewed extortion attempts from the same threat actor, who claims to hold the full database.
Sanggiero and IntelBroker have also been implicated in breaches targeting HSBC and Barclays earlier in 2024. These attacks compromised sensitive banking data, including transaction records and account details, suggesting a pattern of high-profile and large-scale breaches by the group.
6. Threat Actor Claims Jarir Bookstore Database Breach Impacting 26 Million Users
A threat actor has allegedly put up for sale a database belonging to Jarir Bookstore, a prominent Saudi Arabian retailer. The actor claims the breach affects 26 million users across multiple countries, including Kuwait, Qatar, Bahrain, and the UAE. The database is reportedly being offered for $10,000.

Threat actor claims to have breached Jarir Bookstore
According to the post, the stolen database contains:
- Personal information of millions of users.
- Specific records from Jarir Bookstore’s operations in Gulf Cooperation Council (GCC) countries.
The threat actor labeled Jarir Bookstore as “the largest social e-commerce in the Middle East” and included a sample dataset to substantiate their claim.
7. Neiman Marcus Data Breach Exposes Over 70 Million Records
The Neiman Marcus data breach linked to its Snowflake platform has exposed sensitive customer and employee information, raising serious cybersecurity concerns. The breach began on April 14, 2024, when attackers gained unauthorized access, compromising names, addresses, phone numbers, partial Social Security numbers, gift card details, and shopping records.
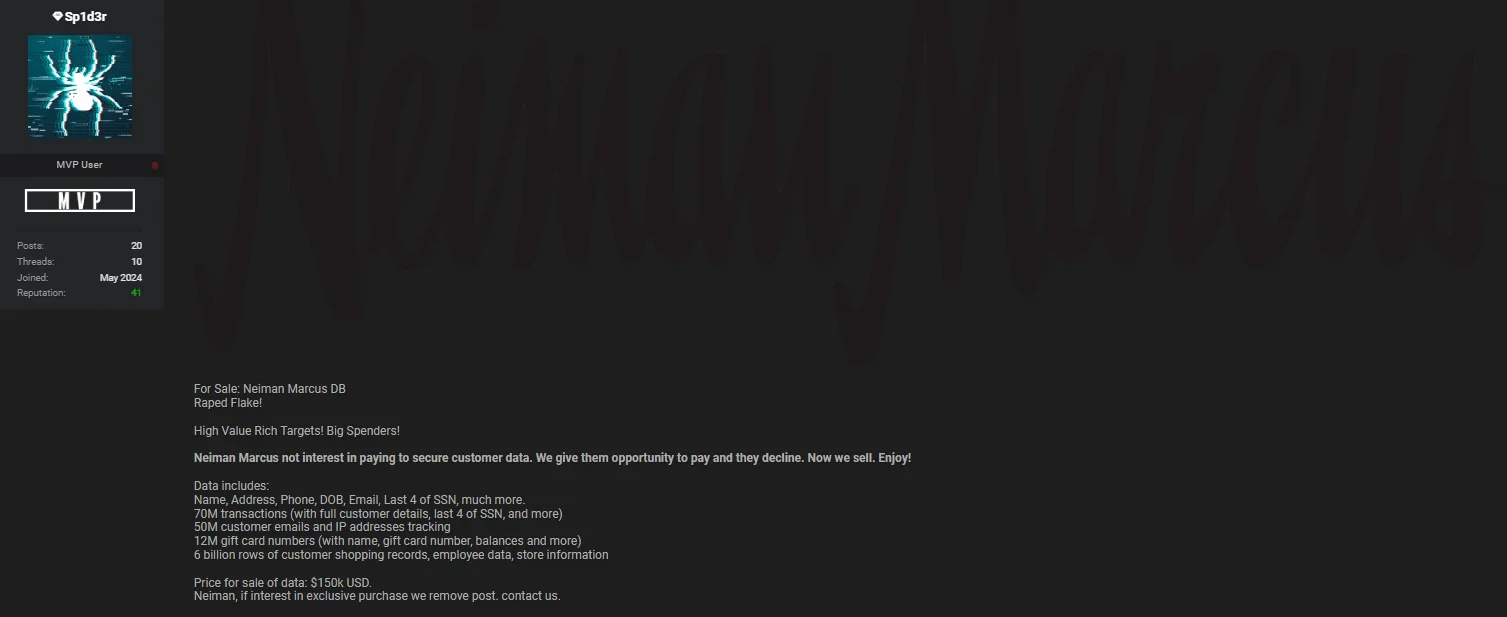
Neiman Marcus Group data breach post by Sp1d3r
The intrusion was detected on May 24, 2024, but by then, a significant amount of data had already been accessed.
On June 25, 2024, the threat actor Sp1d3r publicly claimed responsibility for the breach, posting on a hacker forum. Sp1d3r offered the stolen data for $150,000 and revealed that Neiman Marcus had declined to pay an earlier ransom. The dataset was described as including 70 million transaction records, 50 million customer emails, 6 billion rows of shopping records, and employee details.
That same day, Neiman Marcus confirmed the breach, attributing it to unauthorized access to its Snowflake account. The company reported that 65,000 customers were directly affected, although threat actor claims suggested a much broader impact.
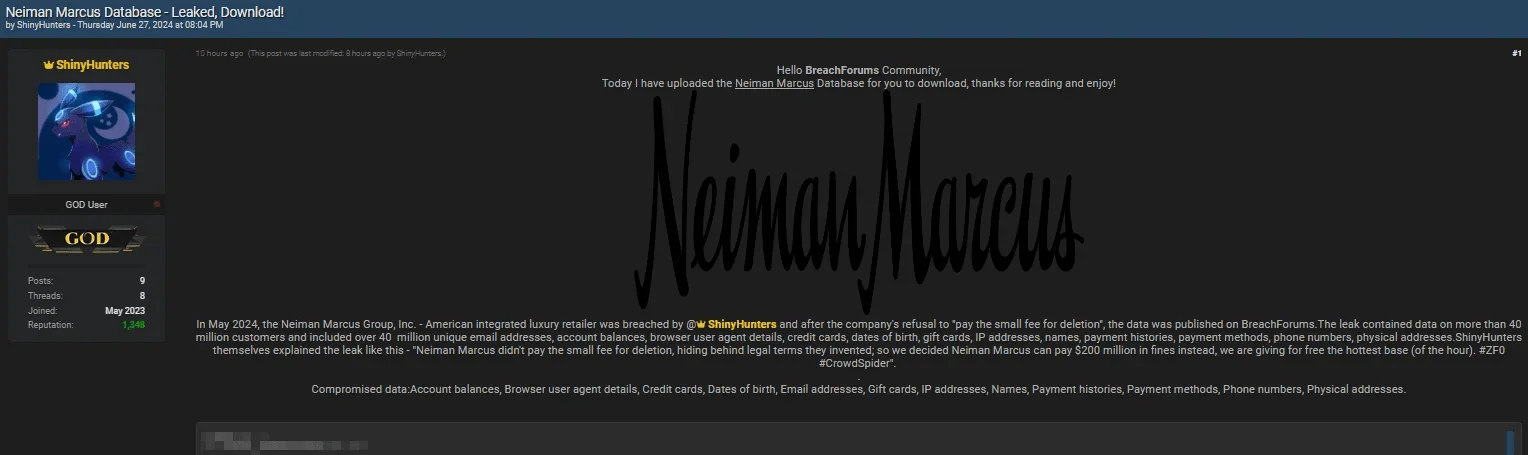
Neiman Marcus data leak post by ShinyHunters
On June 27, 2024, another threat actor, ShinyHunters, leaked a portion of the Neiman Marcus database for free. This leak included data for 40 million customers, such as email addresses, balances, and personal details. ShinyHunters accused Neiman Marcus of refusing to negotiate, further escalating the situation.
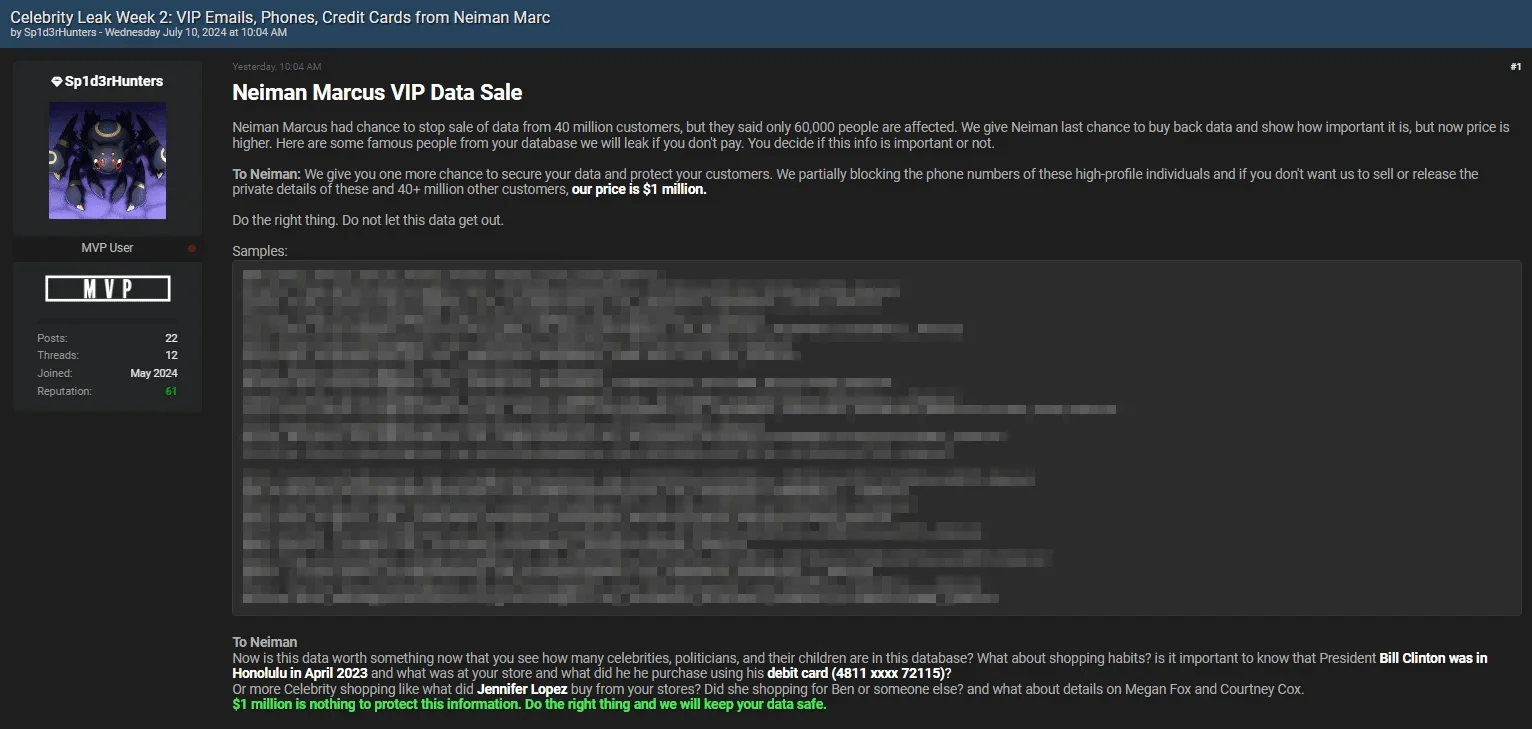
Neiman Marcus VIP data sale post by Sp1d3rHunters
By July 10, 2024, the threat actor, now using the updated alias Sp1d3rHunters, threatened to release VIP customer data as part of “Celebrity Leak Week 2.” The post claimed to feature high-profile names like Kylie Jenner, the Kardashians, and Elon Musk. The actor demanded $1 million to halt further leaks, adding urgency to the matter.
The Neiman Marcus breach underscores the vulnerabilities associated with cloud services and the critical need for robust cybersecurity measures to protect sensitive data.
8. Lookiero Data Breach Exposes Nearly 5 Million Customer Records
In August 2024, a data breach involving Lookiero, an online styling service, was disclosed on a popular hacking forum. The breach, which occurred on March 27, 2024, compromised nearly 5 million accounts and included sensitive information such as email addresses, names, phone numbers, and physical addresses.
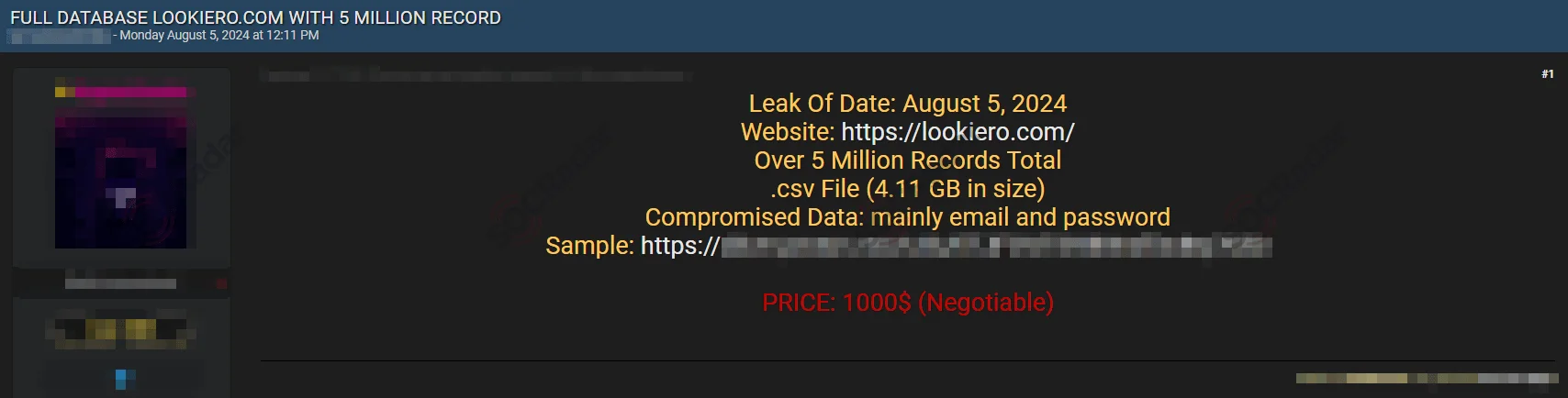
Threat actor claims to be selling Lookiero data
The threat actor initially posted the dataset for sale on August 5, 2024, but later released the records for free on August 20, 2024, significantly increasing the potential impact of the breach.
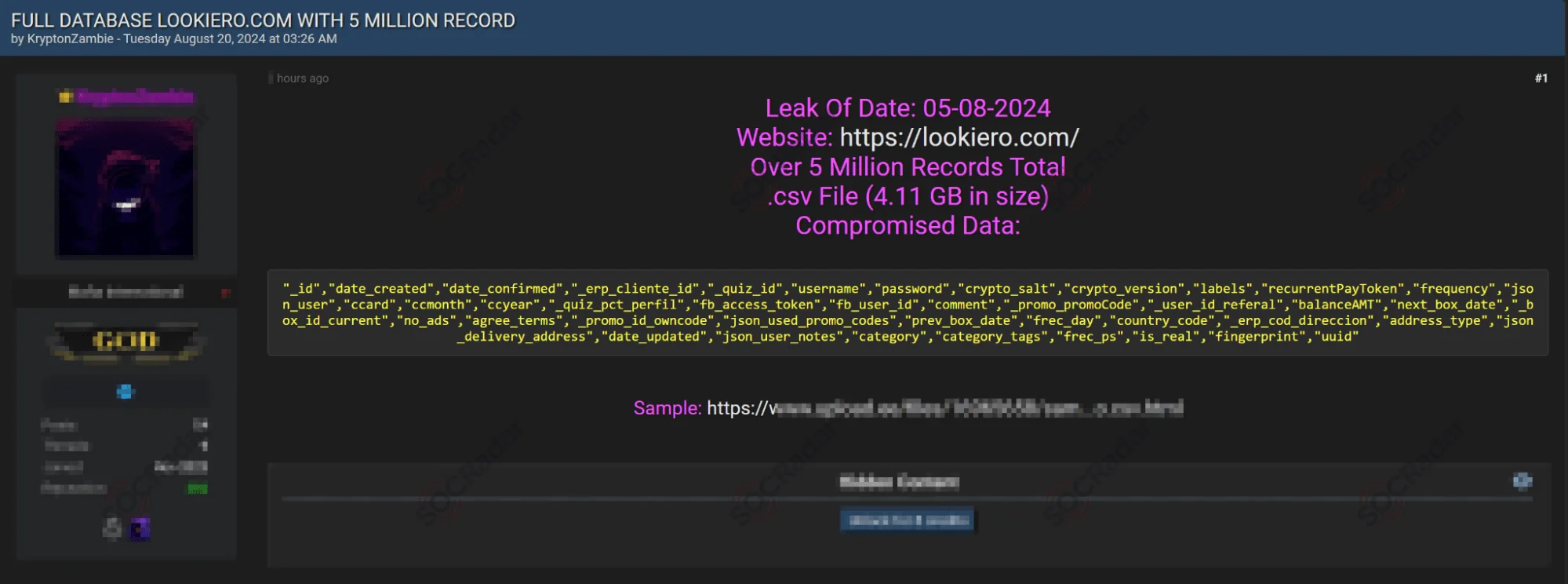
Lookiero data leak post
9. Threat Actor Claims Data Breach of Lulu Hypermarket, Impacting 2.8 Million Users
A threat actor has allegedly posted a sale listing for a database belonging to Lulu Hypermarket, a popular shopping brand in the Middle East. The breach, claimed to have occurred in July 2024, reportedly affects 2,796,835 users.
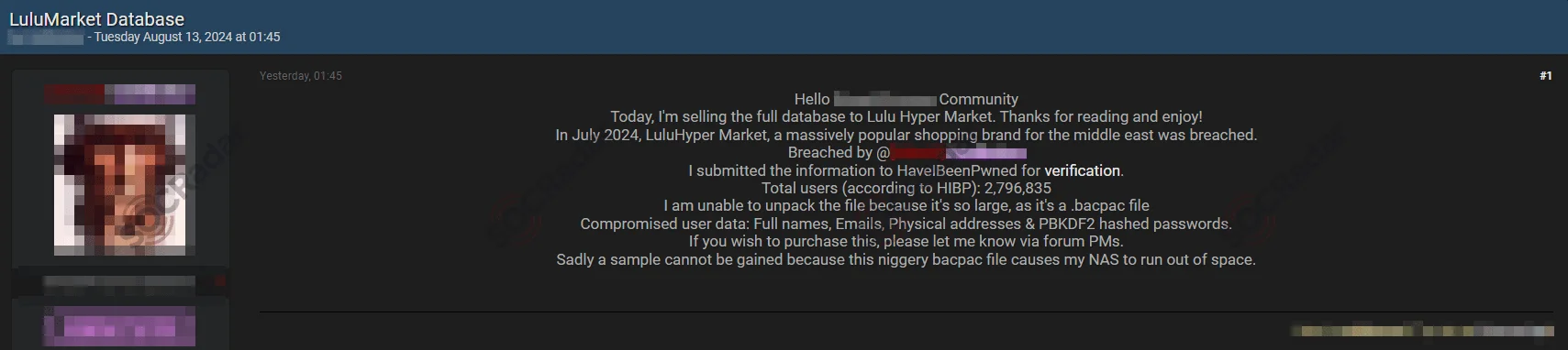
Lulu Hypermarket data sale post by IntelBroker
The compromised data allegedly includes:
- Full names
- Email addresses
- Physical addresses
- PBKDF2-hashed passwords
The threat actor, identified as IntelBroker, stated that the file format (.bacpac) is too large to unpack for further analysis, limiting the ability to provide samples. Despite this, the dataset has been submitted to HaveIBeenPwned for verification.
10. Threat Actor ‘888’ Claims Shopify Data Breach Linked to Third-Party App
On July 3, 2024, the threat actor known as ‘888’ shared a post on a popular hacker forum, claiming to sell stolen Shopify data. The post included data samples that allegedly feature:
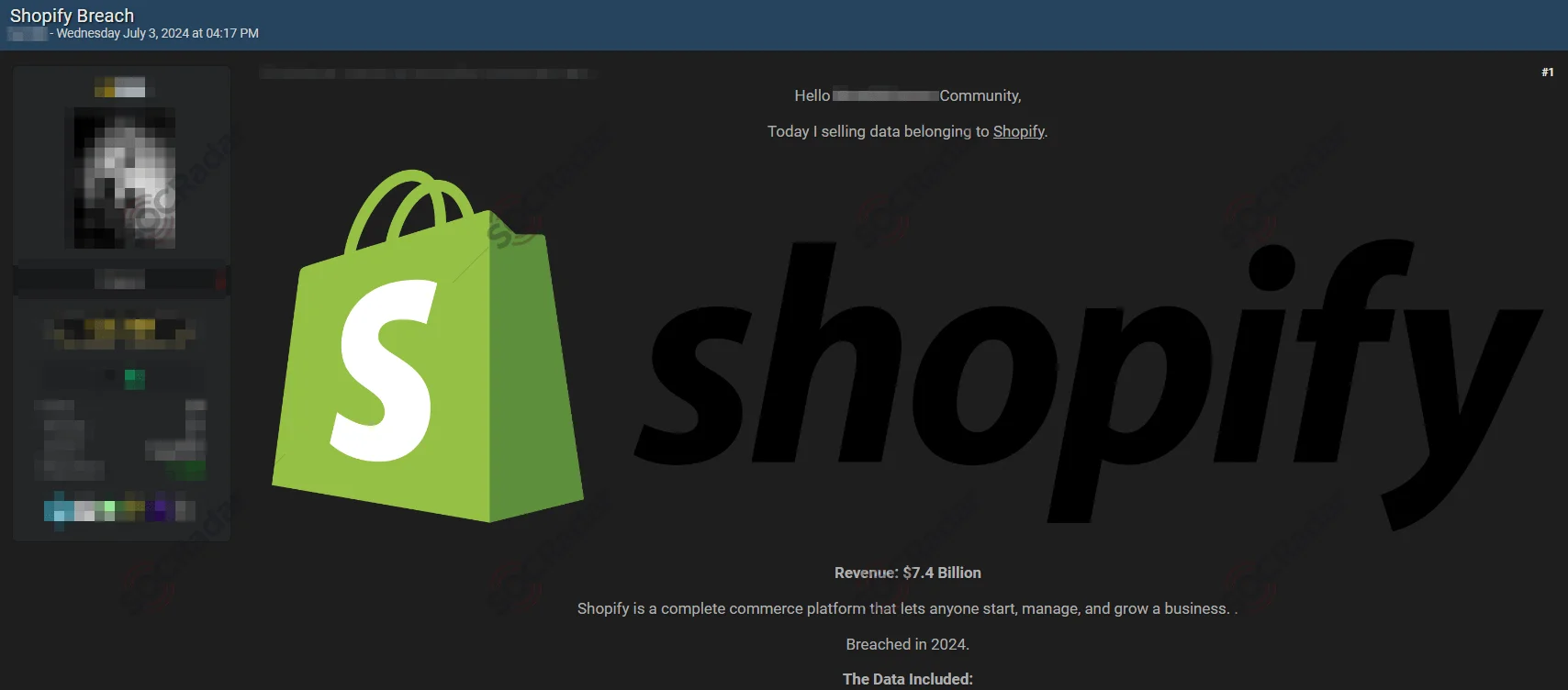
Shopify data sale post by 888
- Shopify ID
- First and last names
- Email and mobile numbers
- Order count and total spent
- Email and SMS subscription details with timestamps
The data was reportedly linked to a breach in 2024. However, Shopify later stated that the information likely originated from a third-party app and not its own platform.
The threat actor ‘888’ is associated with the CyberNiggers threat group, which has been linked to numerous high-profile breaches. In addition to the Shopify claims, ‘888’ has allegedly sold or leaked data tied to Credit Suisse, Shell, Heineken, Accenture India, and UNICEF, demonstrating a history of targeting major organizations.
Bonus: Beyond Data Breaches – The Multifaceted Threats on the Dark Web
When exploring the dark web’s impact on the e-commerce industry, it’s crucial to recognize that threats extend far beyond data breaches. The dark web serves as a marketplace not just for stolen credentials and customer records but also for tools, exploits, and recruitment aimed at enabling deeper and more insidious attacks. Below are examples of recent dark web activity that demonstrate how diverse and dynamic these threats can be:
1. Alleged 1-Day RCE Exploit Sale for Magento 2 (CVE-2024-34102)
A threat actor advertised the sale of a Remote Code Execution (RCE) exploit for Magento 2, a widely used e-commerce platform. The exploit claims to provide an automated process that requires only a target URL, resulting in a full SSH shell. Priced at $20,000 per copy, with only five copies available, this alleged vulnerability could grant attackers unfettered access to e-commerce websites, enabling data theft, defacement, or malware installation.
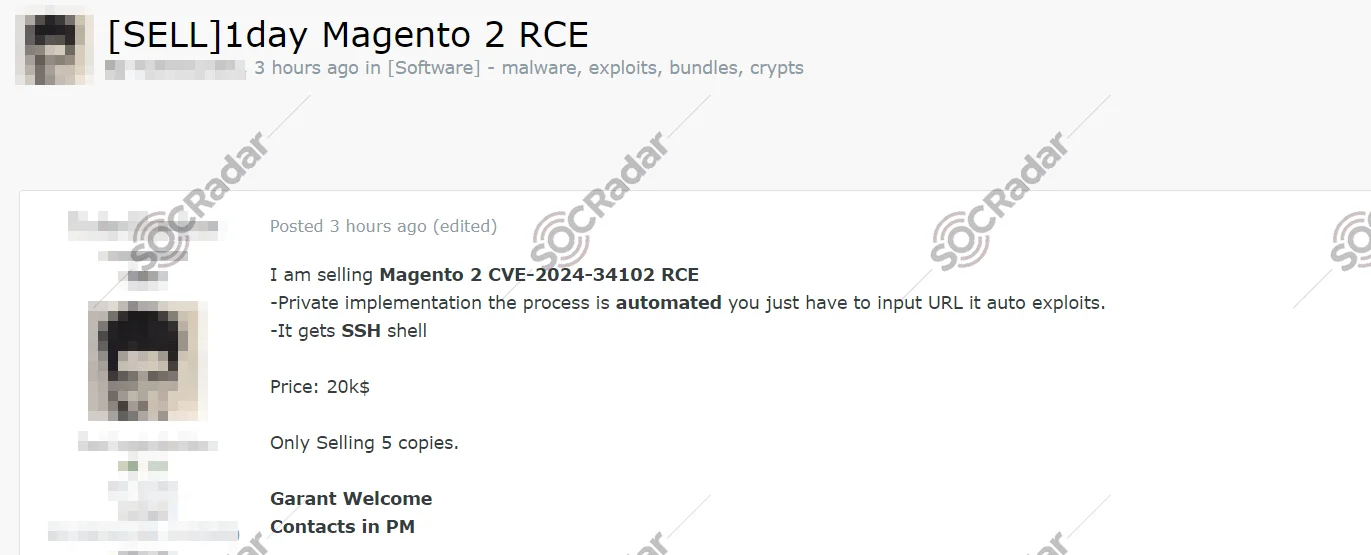
Threat actor claims to be selling exploit for Magento
Such exploits highlight the critical risks posed by unpatched vulnerabilities in platforms like Magento. For businesses, it underscores the importance of applying patches promptly and maintaining rigorous security monitoring. A single RCE exploit could compromise entire e-commerce operations, leading to devastating reputational and financial losses.
SOCRadar integrates seamlessly with patch management workflows, helping businesses remediate vulnerabilities quickly. By correlating vulnerability data with their digital assets, organizations can identify high-risk areas and address them proactively.
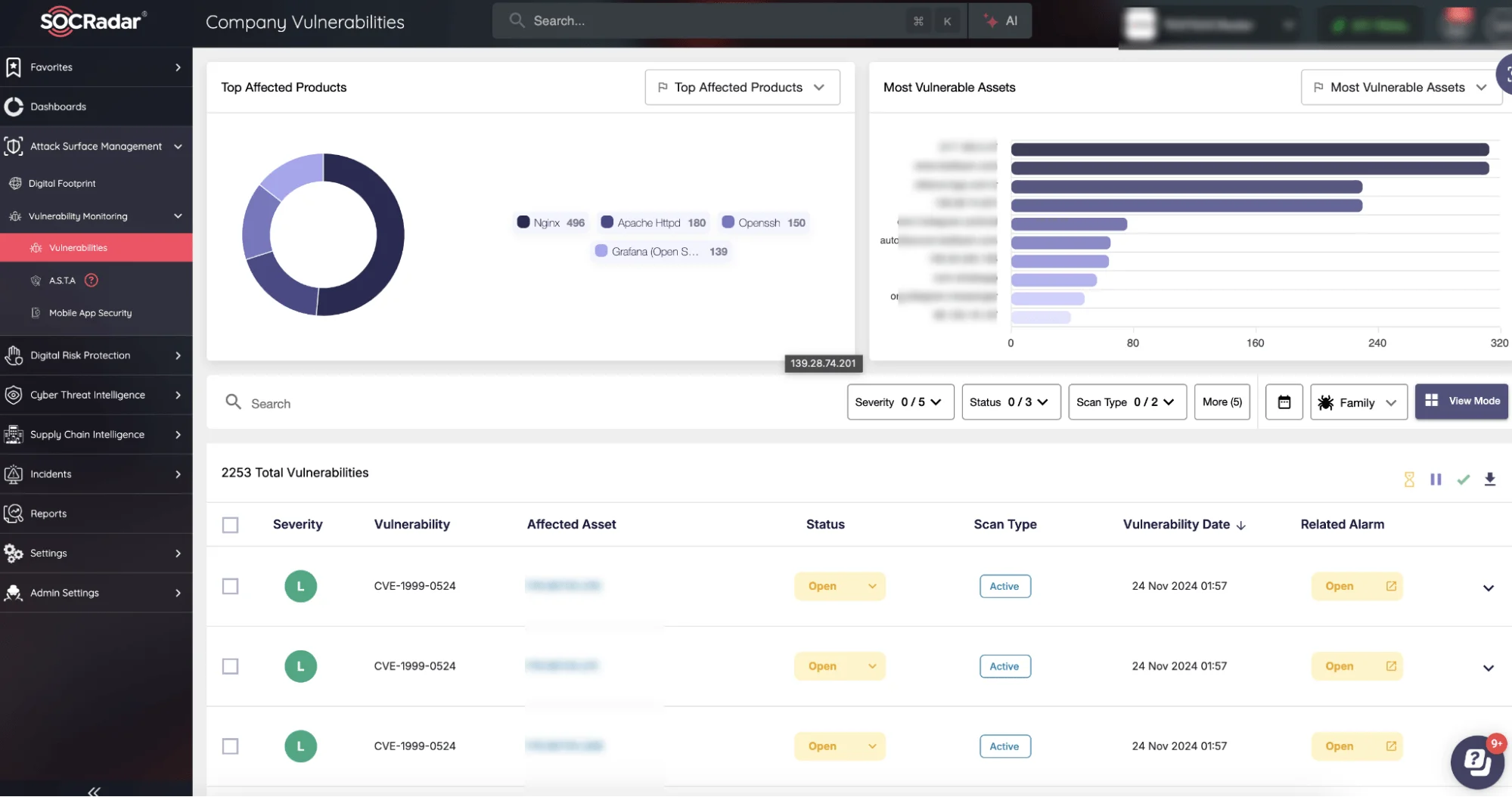
SOCRadar Company Vulnerabilities
2. Recruitment Post for Internal Cooperation
A recruitment post was detected from a threat actor seeking employees who can “influence payments” within their stores. The post invites potential collaborators to connect via Telegram for further discussions.
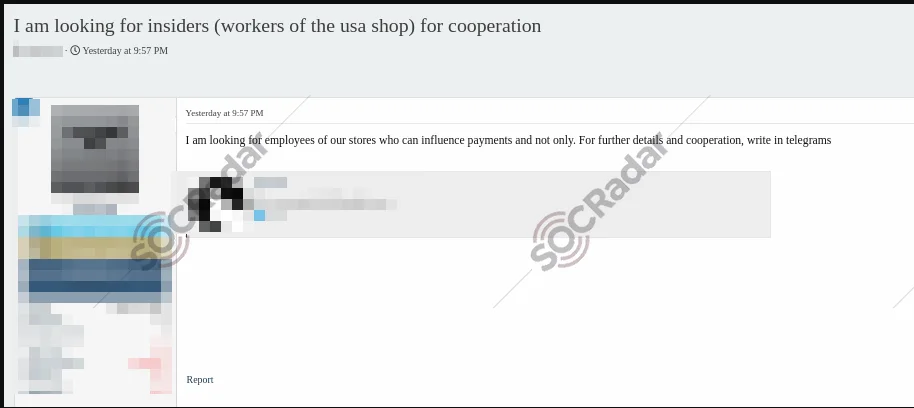
Threat actor’s recruitment post
This example reflects the growing trend of insider threats in e-commerce. By recruiting employees with access to payment systems or inventory, attackers can execute fraud schemes, siphon funds, or manipulate stock levels. For businesses, this highlights the need for robust insider threat detection programs, including monitoring unusual employee activity and enforcing strong access controls.
3. Alleged Amazon Gift Card Generator Tool Shared
A post surfaced on a dark web forum offering a tool claimed to generate random Amazon gift card codes. The tool allegedly filters duplicate codes and allows users to save valid codes for future use.
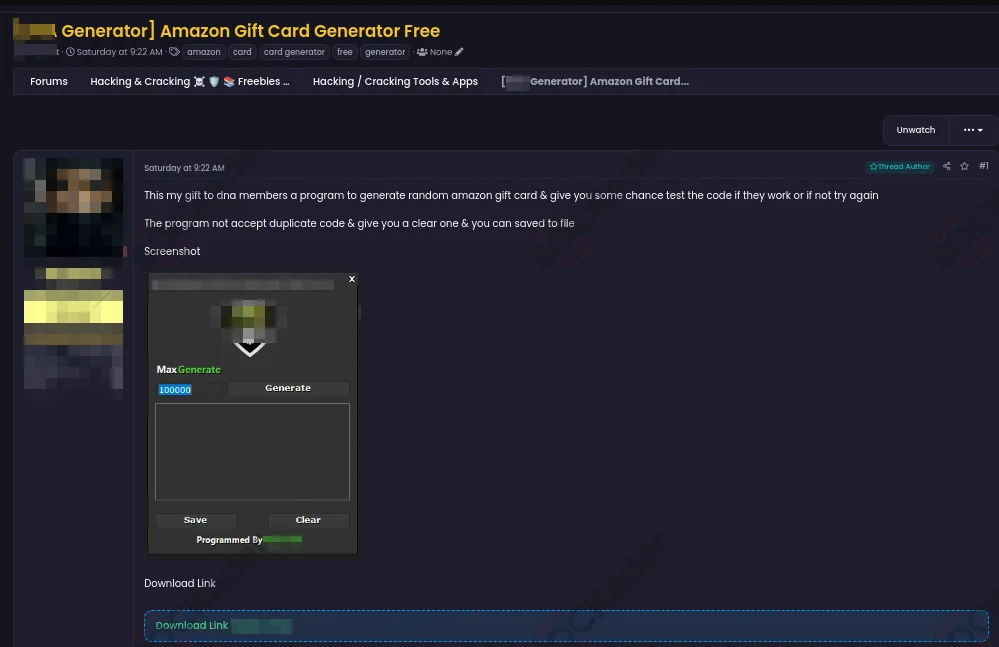
Alleged Amazon Gift Card Generator Tool
Though such tools are often scams or highly unreliable, their presence can cause significant damage to e-commerce brands. Even the perception of vulnerabilities in gift card systems can erode consumer trust. Businesses must implement advanced fraud detection systems to monitor and prevent the misuse of promotional assets like gift cards.
4. Phishing Page of Farfetch on Sale
A phishing page mimicking Farfetch, a luxury e-commerce platform, has been detected for sale on a dark web forum. The threat actor advertises a comprehensive package including the phishing site’s source code, dual Stripe payment systems (one legitimate and one phishing), and a cryptocurrency payment gateway for receiving stolen funds. Priced at $999, the package also comes with full support and accepts escrow payments.
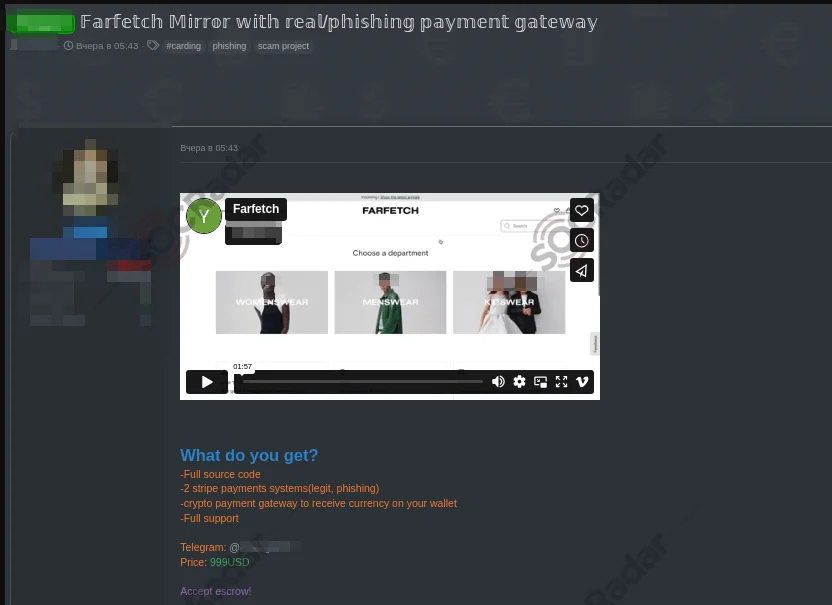
An advertisement on a dark web forum selling a phishing page for Farfetch, highlighting features like Stripe payment systems, a cryptocurrency gateway, and full support.
Such phishing kits are designed to deceive users into providing payment and personal details under the guise of legitimate transactions. For businesses, this underscores the importance of proactive phishing detection and customer education on recognizing fraudulent sites.
5. New CC Store Offering Worldwide Fullz and Dumps
A new credit card (CC) store has surfaced, offering a range of stolen data from regions worldwide, including complete personal details (Fullz) and payment card dumps with tracks 1 and 2. The store emphasizes a high validity rate of 98% and claims to provide fresh data with substantial balances daily. Additionally, it offers full identity information such as SSNs, driver’s licenses, and addresses for USA-based cards, with the threat actor seeking long-term, reliable buyers.
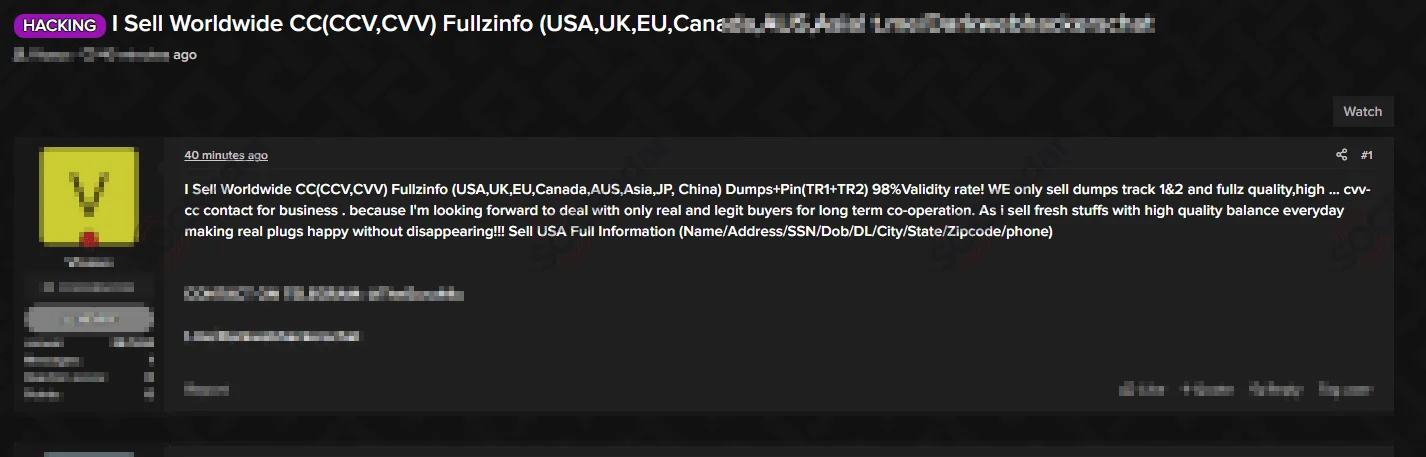
A post promoting a credit card store offering stolen data such as Fullz, card dumps, and personal information, with claims of high validity and fresh balances.
The sale of financial and personal data fuels fraud and identity theft on a massive scale, posing risks for consumers and businesses alike. Monitoring and shutting down such operations, while challenging, is essential to minimizing financial and reputational harm.
Conclusion
The e-commerce industry stands at the crossroads of innovation and vulnerability, with cyber threats evolving in complexity and scale. From phishing and ransomware to sophisticated dark web activities, attackers are targeting platforms with growing precision. Real-world breaches like those impacting Taobao, Ticketmaster, and Temu underscore the urgent need for robust security measures.
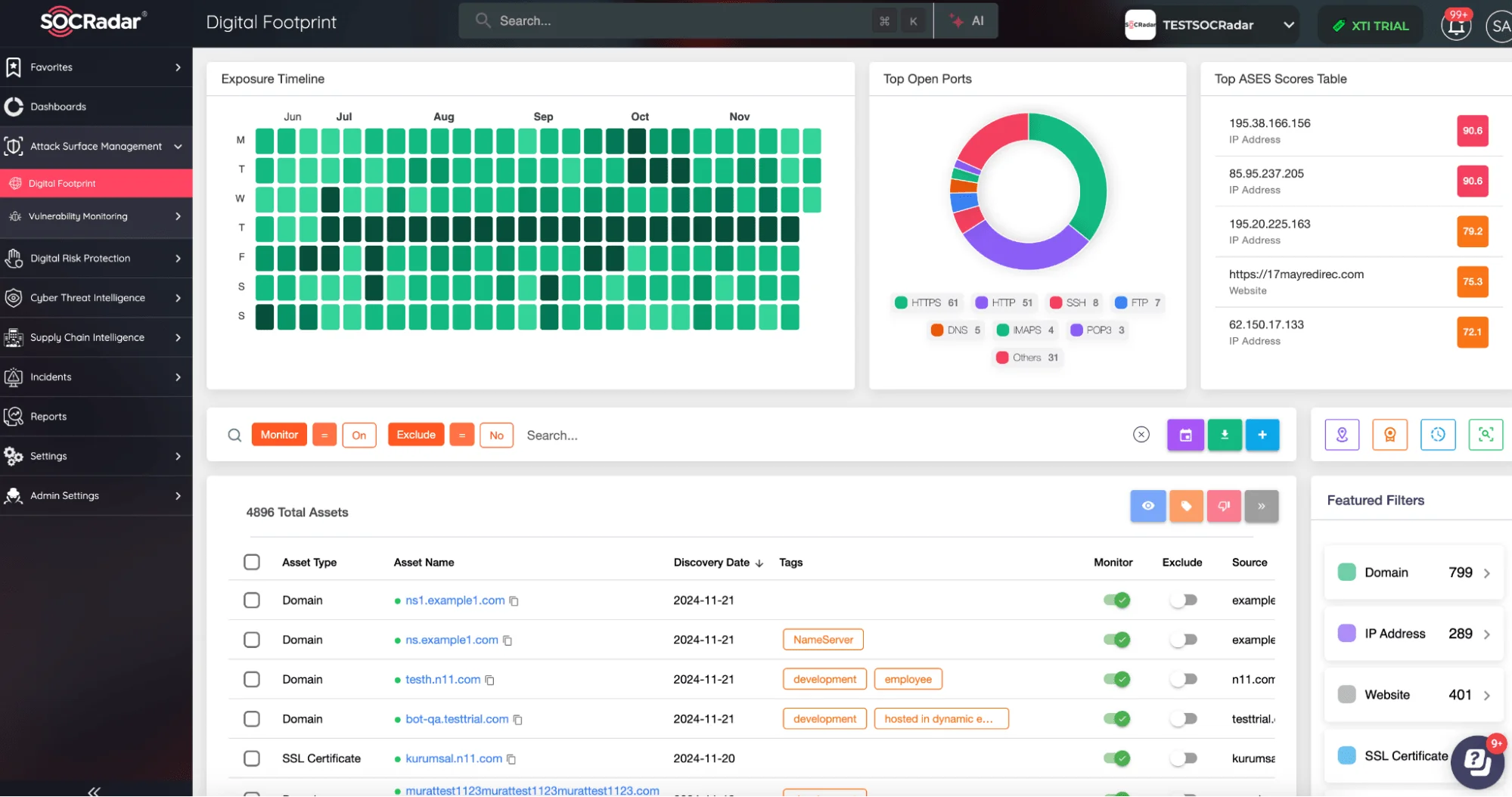
SOCRadar Attack Surface Management
To combat these challenges, integrating solutions like SOCRadar’s Attack Surface Management is crucial. By providing real-time insights into exposed assets and vulnerabilities, businesses can proactively secure their digital presence.
For a deeper exploration of these trends and actionable strategies, refer to our comprehensive report: “From Black Friday to Cyber Monday: 2024 E-Commerce Threat Landscape Report!”
Safeguarding sensitive data and maintaining consumer trust requires a vigilant and adaptive approach to cybersecurity—one that recognizes the dynamic risks inherent in the e-commerce landscape.






































