
From the Trenches: Top 10 Cybersecurity Lessons Learned in 2024 H1
The first half of the year has been marked by sophisticated attacks, with ransomware incidents reaching alarming new heights and critical infrastructure coming under siege. Global patching crises crippled businesses and the increasing weaponization of AI in cyberattacks posed growing threats. Organizations are now facing greater challenges than ever in securing their digital ecosystems.
In this blog, we’ll explore the top 10 lessons learned from the frontline of cybersecurity in 2024 H1. These insights not only highlight emerging threats but also offer actionable strategies to strengthen defenses against the ever-changing tactics of cybercriminals. Let’s examine what went wrong, what worked, and how to better prepare for what’s ahead.
1. Ransomware’s Relentless Reign in 2024
Ransomware continued to dominate the cybersecurity landscape in the first half of 2024, affecting industries across the globe. LockBit 3.0, BlackCat (ALPHV), and other notable groups launched devastating attacks on sectors such as healthcare, manufacturing, and critical infrastructure. These attackers evolved their strategies, employing double extortion tactics, where they not only encrypted victims’ data but also threatened to leak sensitive information if the ransom was not paid.
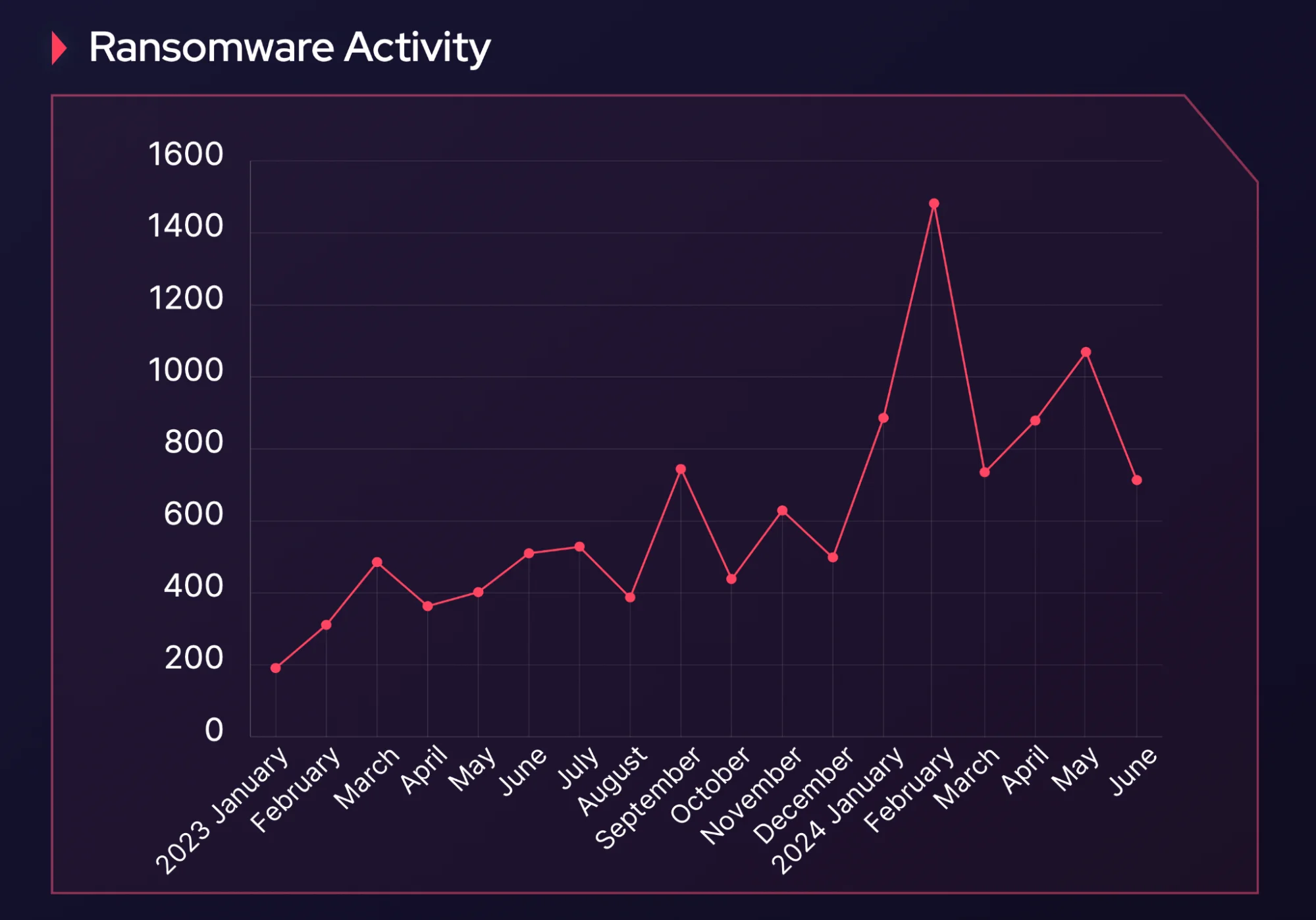
The trend in ransomware activity started from the previous year
SOCRadar’s data shows a peak in ransomware-related activity in February 2024, with 1,482 posts on ransomware operations. Activity remained high through May, reflecting a rise in incidents targeting the U.S. and Europe. Interestingly, there was a decline in June, with posts dropping to 713, possibly indicating a shift in ransomware groups’ focus or a recalibration of their strategies.
Organizations must remain vigilant. The growing sophistication and impact of ransomware attacks make it critical to implement multi-layered security strategies, including endpoint protection, robust encryption, isolated backups, and comprehensive incident response plans. Proactive measures like continuous monitoring and employee training can further reduce the risk of falling victim to these attacks.
2. Patch Management Failures and the Importance of Rigorous Testing
Patch management is essential for maintaining secure and operational systems. However, failures in proper patch testing can lead to significant disruptions. A prime example is the CrowdStrike incident in July 2024, where a simple software update caused global chaos, leading to system failures and Blue Screen of Death errors across millions of Windows devices in sectors such as healthcare and finance.

For more details on the incident, check out “CrowdStrike Update Causing Blue Screen of Death and Microsoft 365/Azure Outage.”
To mitigate the risks associated with patch management, organizations should implement key practices:
- Staged Rollouts: Deploy updates incrementally to catch and fix potential issues before full-scale implementation.
- Backup and Recovery: Ensure backups are in place prior to patch deployment to mitigate any failure risks.
- Testing and Quality Assurance: Conduct thorough testing in controlled environments to identify conflicts or vulnerabilities early.
SOCRadar’s Attack Surface Management (ASM) provides continuous monitoring of an organization’s digital assets, identifying vulnerabilities before they become critical issues. Integrating ASM into your patch management strategy helps prioritize vulnerabilities and streamline the patching process to minimize operational disruptions.
3. Dark Web Still Thrives as a Hotbed for Cybercrime in 2024
The dark web remains a key facilitator of cybercrime in 2024, providing a marketplace for illegal activities ranging from Ransomware-as-a-Service (RaaS) to the trade of stolen credentials and malware kits. This underground ecosystem continues to expand, with an increasing number of threat actors leveraging dark web platforms to exchange hacking tools, personal data, and vulnerabilities.
The dark web has become more accessible, allowing even lower-skilled attackers to acquire sophisticated tools that can wreak havoc on businesses of all sizes. The vast reach of these dark web operations, especially for ransomware and data breaches, makes proactive monitoring essential for businesses looking to stay ahead of these threats.
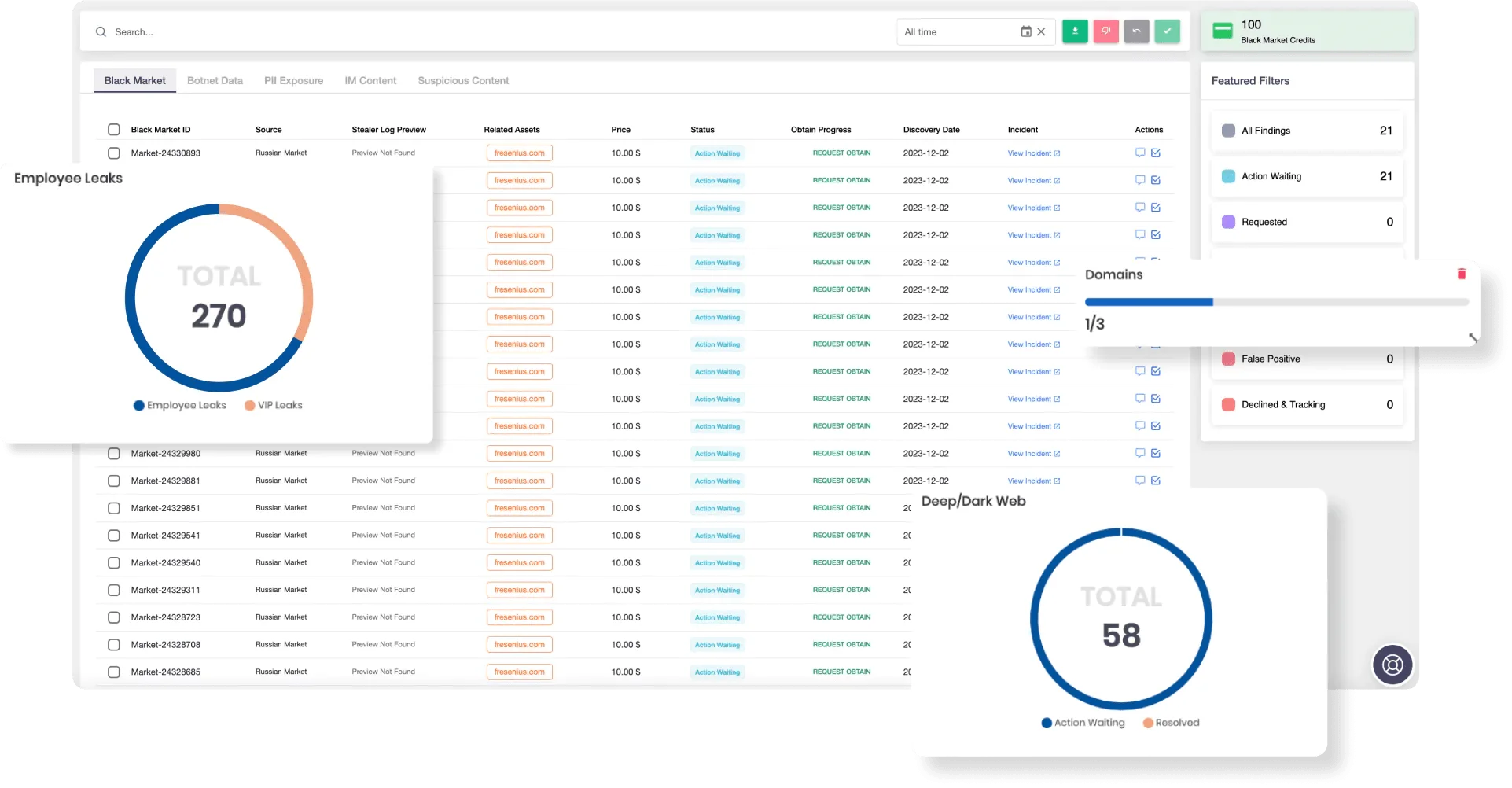
SOCRadar Dark Web Monitoring
To combat these rising threats, SOCRadar Advanced Dark Web Monitoring provides invaluable insights into this hidden world. The platform continuously tracks 4,659 Telegram channels, 340 Discord servers, and 231 hacker forums, along with numerous TOR sites and paste sites. By doing so, SOCRadar gathers critical data from sources often out of reach for most security teams(Mid-Year Report (1)).
Key findings from SOCRadar’s monitoring of the dark web in 2024 include:
- 10B+ breached databases detected.
- 5B+ leaked accounts.
- 75M+ Telegram posts monitored.
- 8K+ combolists shared by threat actors.
- 10B+ stealer log content, revealing sensitive data exfiltrated from compromised systems.
This vast network of monitored channels allows SOCRadar to provide early warnings of emerging cyber threats, stolen credentials, and ongoing cybercriminal activity. By identifying these indicators in real-time, organizations can take proactive measures to protect their assets, mitigate risks, and strengthen their defenses before they become the next target.
4. Strengthening Vendor Security in a Threatened Ecosystem
As supply chain attacks continue to escalate, cybercriminals are refining their strategies, shifting their focus towards third-party vendors to infiltrate larger networks. This tactic allows attackers to bypass direct security measures by exploiting weaker points in the supply chain, leading to extensive disruptions across industries. One of the most alarming incidents in 2024 was the Snowflake breach, where compromised credentials of a vendor were used to access the data of Snowflake’s high-profile clients, including Santander Bank and Ticketmaster.

For more information about the Snowflake breach, visit our blog
This breach wasn’t just about compromised data—it highlighted how deep the impact of supply chain vulnerabilities can go. Even more concerning was the aftermath: stolen customer data linked to the breach surfaced on dark web forums, where hackers openly advertised sales of sensitive information. Threat actors like ShinyHunters posted stolen data on hacker forums such as BreachForums, claiming to have valuable information related to the breach. These dark web sales demonstrated how easily supply chain weaknesses can be exploited and monetized
To combat the rising threat of supply chain attacks, SOCRadar’s Supply Chain Intelligence module offers a comprehensive solution to protect organizations from these vulnerabilities. The platform monitors over 50 million companies for cyber risks, delivering data-driven insights and dynamic scoring that help businesses prioritize which vendors pose the highest risk.
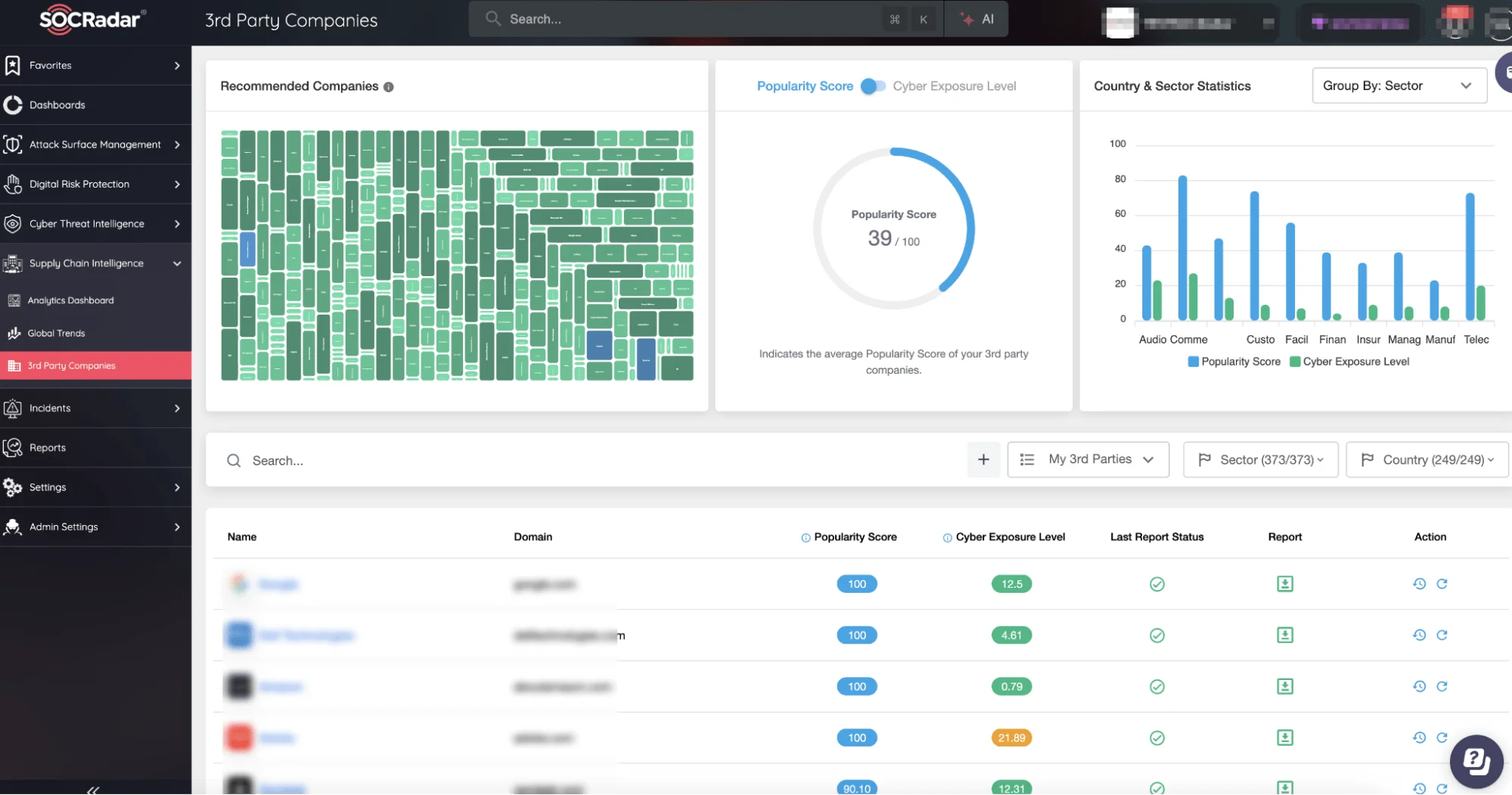
SOCRadar Supply Chain Intelligence
In addition, SOCRadar’s Dark Web Monitoring works in tandem with Supply Chain Intelligence to provide a holistic view of vendor-related risks. By scanning hacker forums, Telegram channels, and Discord servers, SOCRadar detects any stolen data or discussions related to your third-party suppliers. This early warning system ensures that businesses can respond quickly to security incidents and avoid the devastating consequences of a supply chain breach.
5. AI-Driven Cyber Attacks and the Rise of Automated Cybercrime
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing cyberattacks, leading to more effective and automated threats. In 2024, AI-enhanced phishing campaigns and adaptive malware have become significant challenges. Attackers are using generative AI, like ChatGPT, to craft convincing phishing emails, contributing to a 4,151% increase in malicious emails since late 2022. AI-driven malware can now adapt to defenses in real-time, making it harder to detect.
Cybercrime-as-a-Service (CaaS) is also on the rise, with services like Phishing-as-a-Service (PhaaS) offering pre-packaged phishing kits, making sophisticated attacks accessible to less skilled cybercriminals.
While attackers leverage AI, organizations can use AI-powered defenses to detect phishing attempts and malware, employing anomaly detection and real-time monitoring to stay ahead of evolving threats.
SOCRadar offers several advanced features to help organizations combat the growing threat of AI-driven cyberattacks, including phishing and malware:
SOCRadar Dark Web Monitoring
- Dark Web Monitoring: SOCRadar continuously tracks dark web forums and marketplaces for threats such as Phishing-as-a-Service (PhaaS) kits, helping organizations detect and mitigate potential attacks before they occur.
- Real-Time Threat Intelligence: Using AI-powered tools, SOCRadar provides real-time analysis of suspicious activities, such as phishing emails or malware distribution patterns, allowing organizations to respond quickly and effectively.
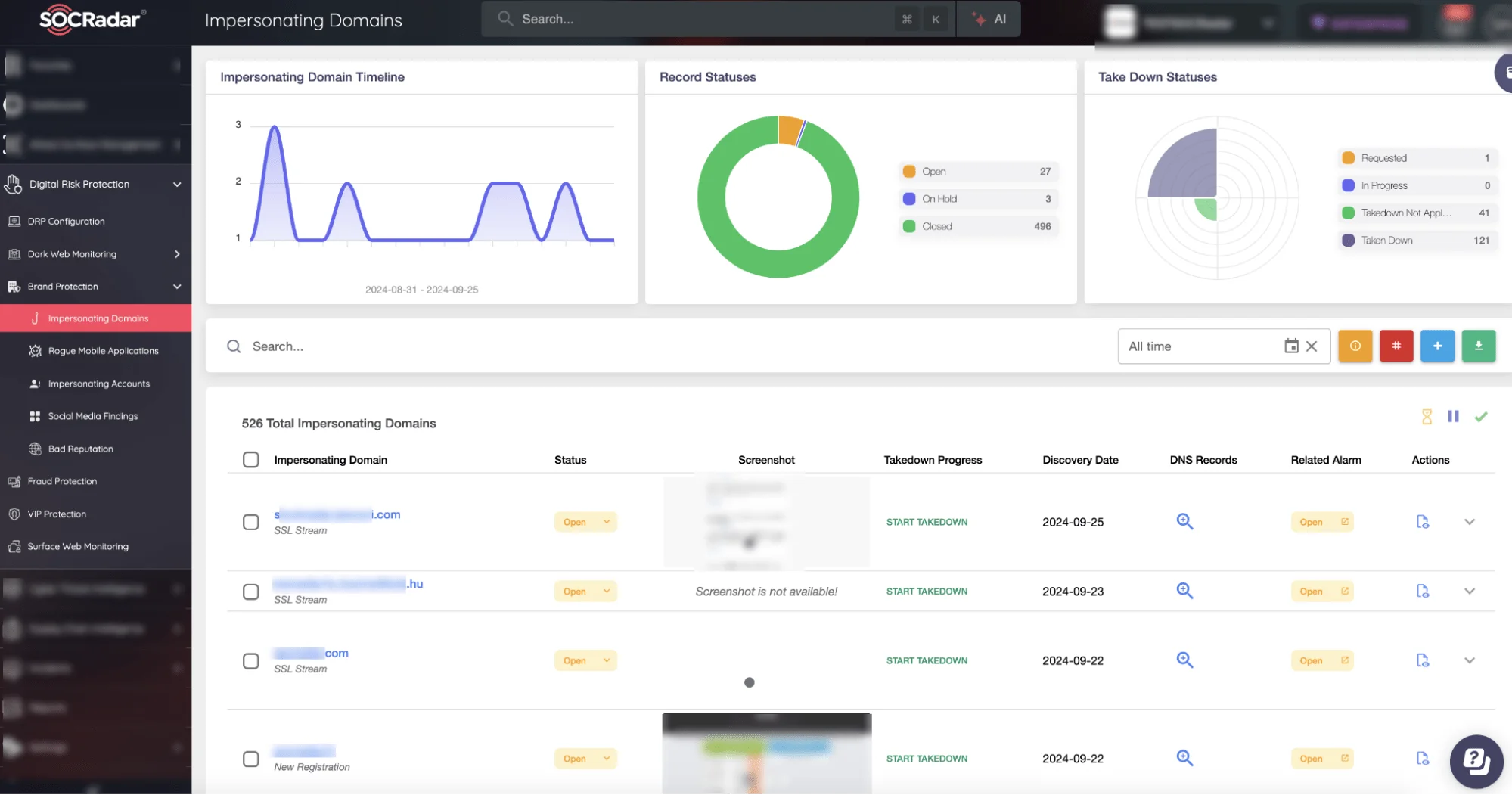
SOCRadar Brand Protection module
- Brand Protection: SOCRadar identifies phishing campaigns that target your organization by monitoring for impersonation attempts, suspicious domain registrations, and leaked credentials, enabling quick remediation.
- Anomaly Detection and AI-Driven Defense: With its AI capabilities, SOCRadar can detect unusual patterns and suspicious behaviors across networks, helping organizations prevent sophisticated AI-enhanced phishing attacks and adaptive malware before they cause significant harm.
By leveraging these tools, SOCRadar empowers organizations to stay ahead of evolving threats in the AI-driven cyber landscape.
6. Phishing in 2024 as the Most Prevalent Initial Attack Vector
Phishing remains one of the most prevalent and dangerous attack vectors in 2024, as cybercriminals continuously refine their tactics to exploit human vulnerabilities and weak security measures. The rise of phishing is reflected in various statistics that show a significant uptick in malicious activity. For instance, 30% of small businesses rank phishing as their biggest cybersecurity threat, highlighting its impact across industries and company sizes. Additionally, 94% of organizations have reported experiencing email security incidents, underscoring the widespread nature of this attack method.
In 2024, phishing has seen a dramatic 856% increase in malicious email threats, further demonstrating the growing sophistication and scale of these attacks. Cybercriminals often rely on phishing to launch Account Takeover (ATO) attacks, with 79% of ATO incidents beginning with a phishing email. This makes phishing a critical starting point for larger security breaches, where attackers steal credentials and gain unauthorized access to sensitive systems
To combat phishing, organizations must adopt proactive defenses, including AI-powered threat detection and employee training. These measures help identify phishing attempts early and prevent employees from falling victim to social engineering tactics. As phishing continues to evolve, staying ahead of these threats is crucial for maintaining a strong security posture in 2024.
7. Zero-Day Exploits and Navigating the Risks in 2024
Zero-day vulnerabilities remain one of the most dangerous cybersecurity threats in 2024, even as efforts to detect and mitigate these flaws improve. Attackers continue to exploit unknown vulnerabilities rapidly, taking advantage of the window before patches can be deployed. Despite some improvements in zero-day detection, vulnerabilities are still being exploited at alarming rates. In fact, 75% of vulnerabilities are exploited within 19 days of their disclosure, while 25% are exploited within the first 25 days, emphasizing how quickly attackers can move to take advantage of security gaps.
The speed at which vulnerabilities are weaponized poses a serious challenge for organizations, particularly when it comes to zero-day exploits. Because zero-day vulnerabilities are unknown until they are exploited, there is no immediate fix, giving attackers a critical opportunity to strike before defenses are reinforced.
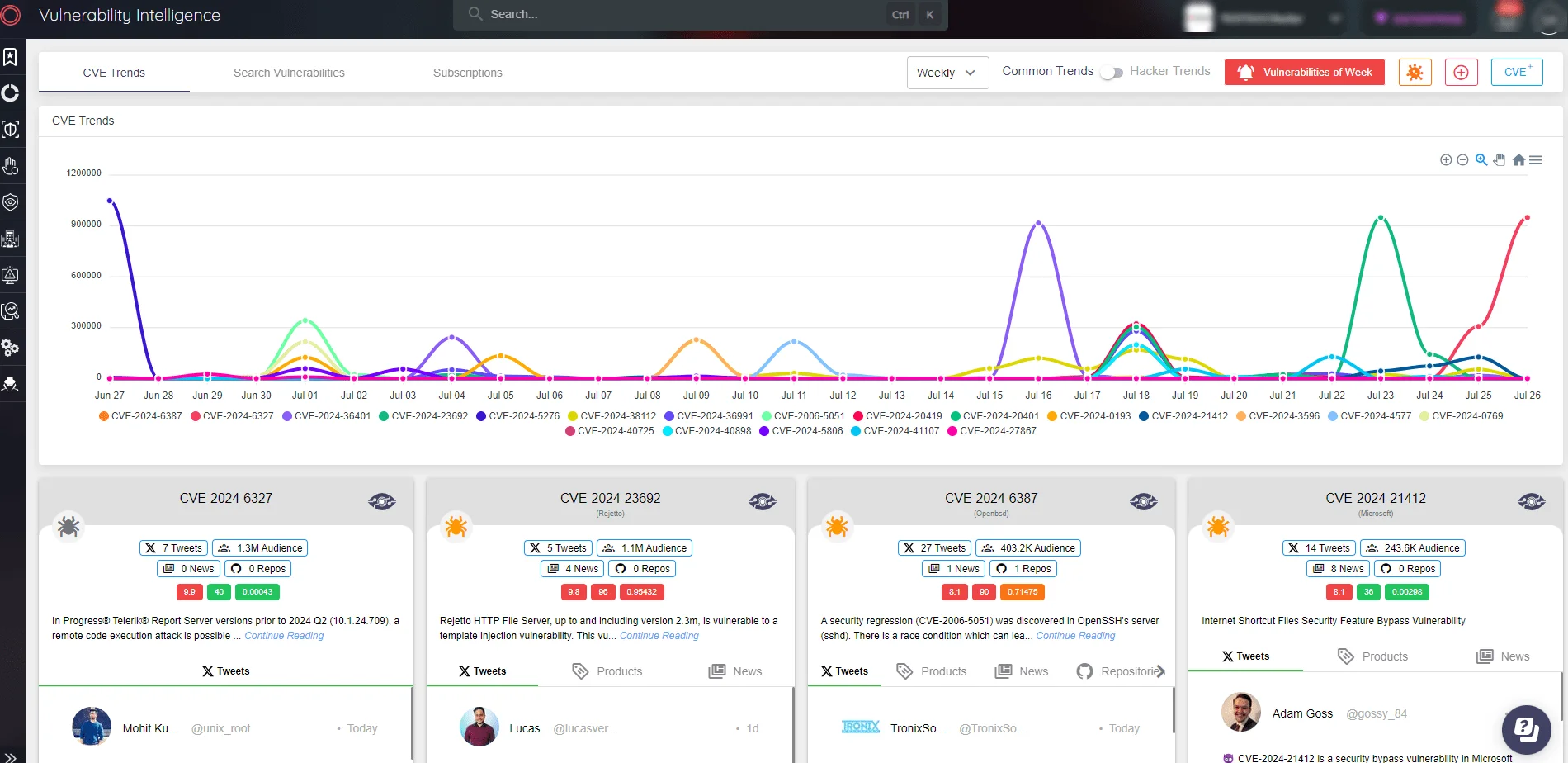
SOCRadar Vulnerability Intelligence
SOCRadar’s Vulnerability Intelligence provides real-time, advanced alerts for newly discovered vulnerabilities, enabling organizations to respond quickly and effectively. By continuously monitoring for critical vulnerabilities, SOCRadar helps protect digital assets and minimize exposure to potential exploits.
With insights into actively exploited vulnerabilities, SOCRadar delivers actionable information, helping security teams prioritize patching and mitigation efforts. The platform also offers customizable monitoring tailored to your specific technology stack, ensuring alerts are relevant to your organization’s needs.
Instant alerts and rapid assessments give you the edge to respond swiftly to emerging threats, preventing breaches before they occur.
8. Cloud Services Under Siege
With the continued rise of cloud adoption, cloud security has become one of the most critical areas for organizations to safeguard in 2024. As businesses increasingly migrate their operations, data, and infrastructure to the cloud, attackers are also evolving to target cloud environments more effectively. The complexity of cloud security challenges is driven by factors such as multi-cloud environments, shared responsibility models, and the widespread use of third-party cloud services.

An illustration of cloud security, generated by OpenAI’s DALL-E
One of the primary risks in cloud security is misconfigurations. Cloud environments often come with complex configurations, and small missteps can expose sensitive data to the public. In 2024, misconfigurations continue to be a leading cause of cloud breaches, with attackers scanning for poorly secured databases, misconfigured storage buckets, and unsecured APIs.
Another emerging threat is the rise in cloud-based ransomware and credential harvesting attacks. Attackers are increasingly targeting cloud credentials, which can provide them with access to entire cloud infrastructures. Once inside, they can deploy ransomware or extract valuable data from cloud storage environments. According to the IBM’s Cost of Data Breach Report 2024, cost of a cloud-related data breach exceeding $5.17 million.
As cloud infrastructures become more complex, visibility and control over these environments are vital. Companies need to implement robust encryption, Identity and Access Management (IAM) protocols, and continuous monitoring to safeguard their cloud resources. Proactive threat detection tools and Cloud Security Posture Management (CSPM) are also essential to detect vulnerabilities and misconfigurations before they are exploited.
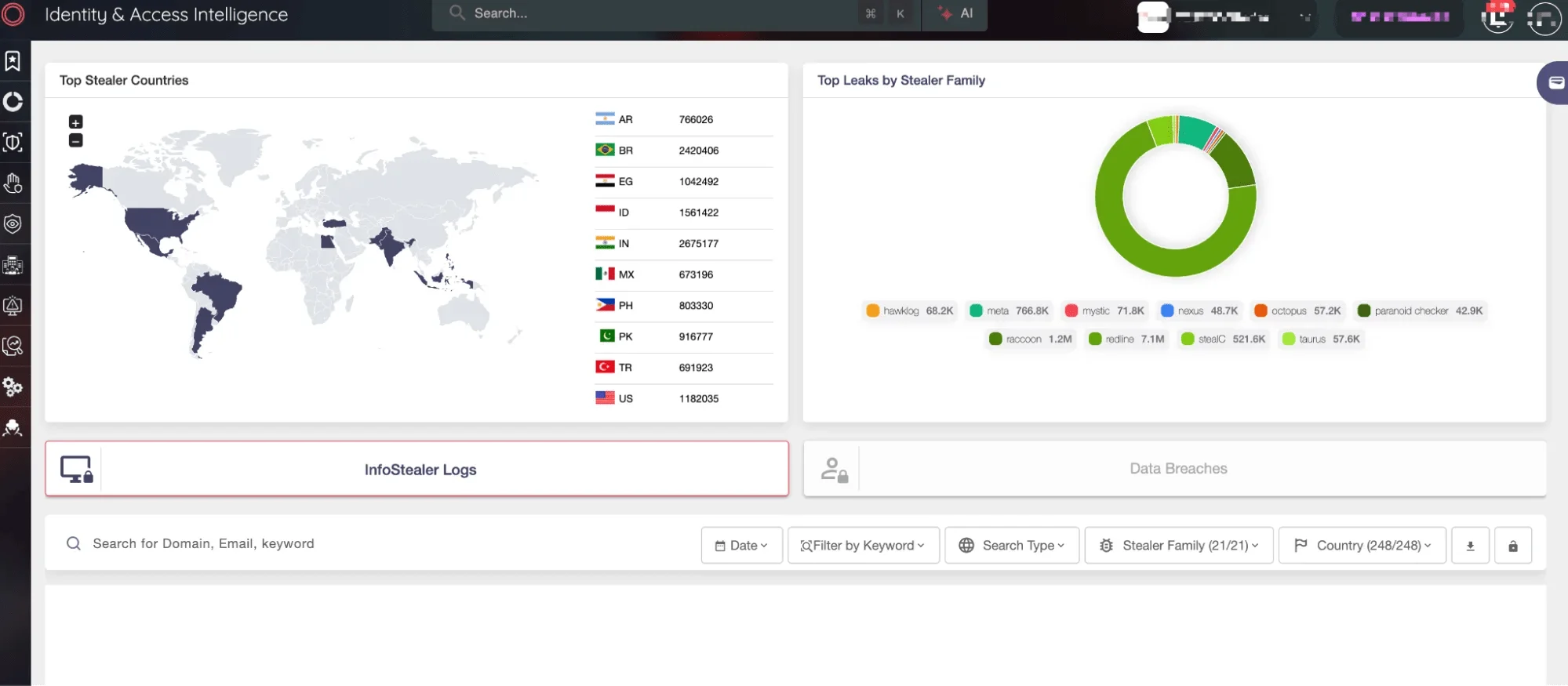
SOCRadar’s Identity & Access Intelligence
SOCRadar’s Attack Surface Management (ASM) greatly supports cloud security by offering organizations real-time visibility and control over their cloud environments. Cloud infrastructure is often complex and prone to security risks like misconfigurations and shadow IT, which can leave critical data exposed. SOCRadar’s ASM helps by continuously monitoring and identifying cloud assets, ensuring no services or resources are left unchecked.
By providing automated alerts for potential vulnerabilities and misconfigurations, SOCRadar enables teams to quickly address security gaps, such as open storage buckets or weak access controls, before attackers can exploit them. This real-time alerting system ensures that any misconfigurations or vulnerabilities in cloud environments are promptly corrected, reducing the risk of breaches.
9. DDoS Attacks and the Rising Hacktivist Threat in 2024
In 2024, Distributed Denial-of-Service (DDoS) attacks have become a central tactic for hacktivist groups looking to disrupt critical infrastructure during politically charged events. A notable example occurred in March 2024, where a coordinated DDoS attack disrupted over 300 French government websites and impacted 177,000 IP addresses, coinciding with preparations for the Paris Olympics and the European parliamentary elections. These attacks aimed to undermine public services and draw attention to political causes.
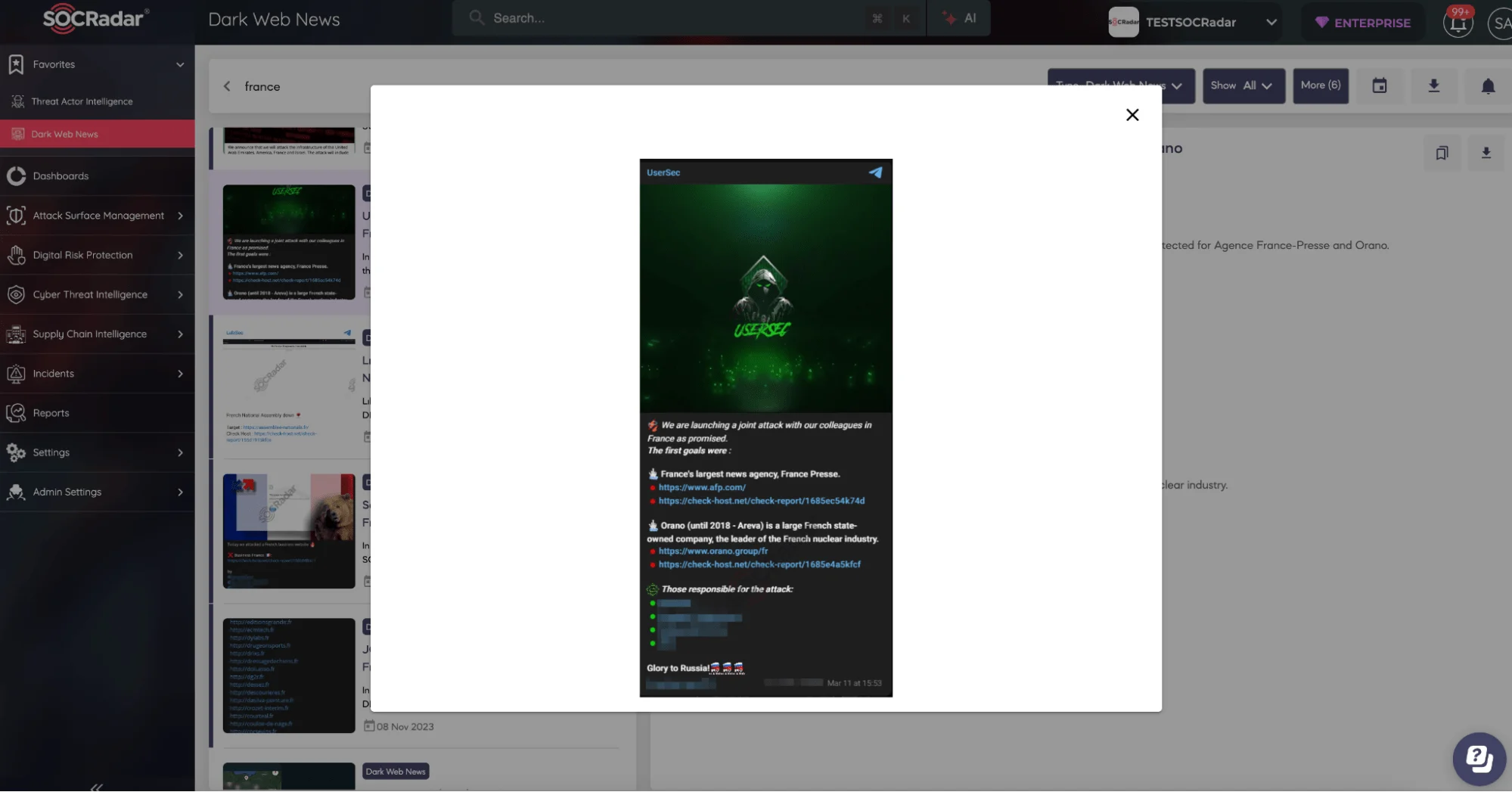
The pro-Russian threat group’s Telegram post claims to have targeted France with a DDoS attack. (SOCRadar Dark Web News)
Hacktivist groups are increasingly using DDoS attacks to target government institutions, aligning their actions with global political tensions. These attacks are designed to cause maximum disruption, especially during high-profile events, leaving governments and organizations vulnerable to severe service outages.
To counter these evolving threats, SOCRadar’s Threat Actor Intelligence provides organizations with real-time monitoring of threat actors. With advanced tracking capabilities, SOCRadar allows security teams to stay ahead of potential DDoS campaigns by offering insights into hacktivist operations and tactics. Through a dynamic dashboard, organizations can monitor threat actor movements, Tactics, Techniques, and Procedures (TTPs), and track regional activity patterns in real-time.
By leveraging SOCRadar’s Threat Actor Intelligence, organizations gain a comprehensive view of the cyber landscape, helping them anticipate and mitigate DDoS threats before they cause significant damage.
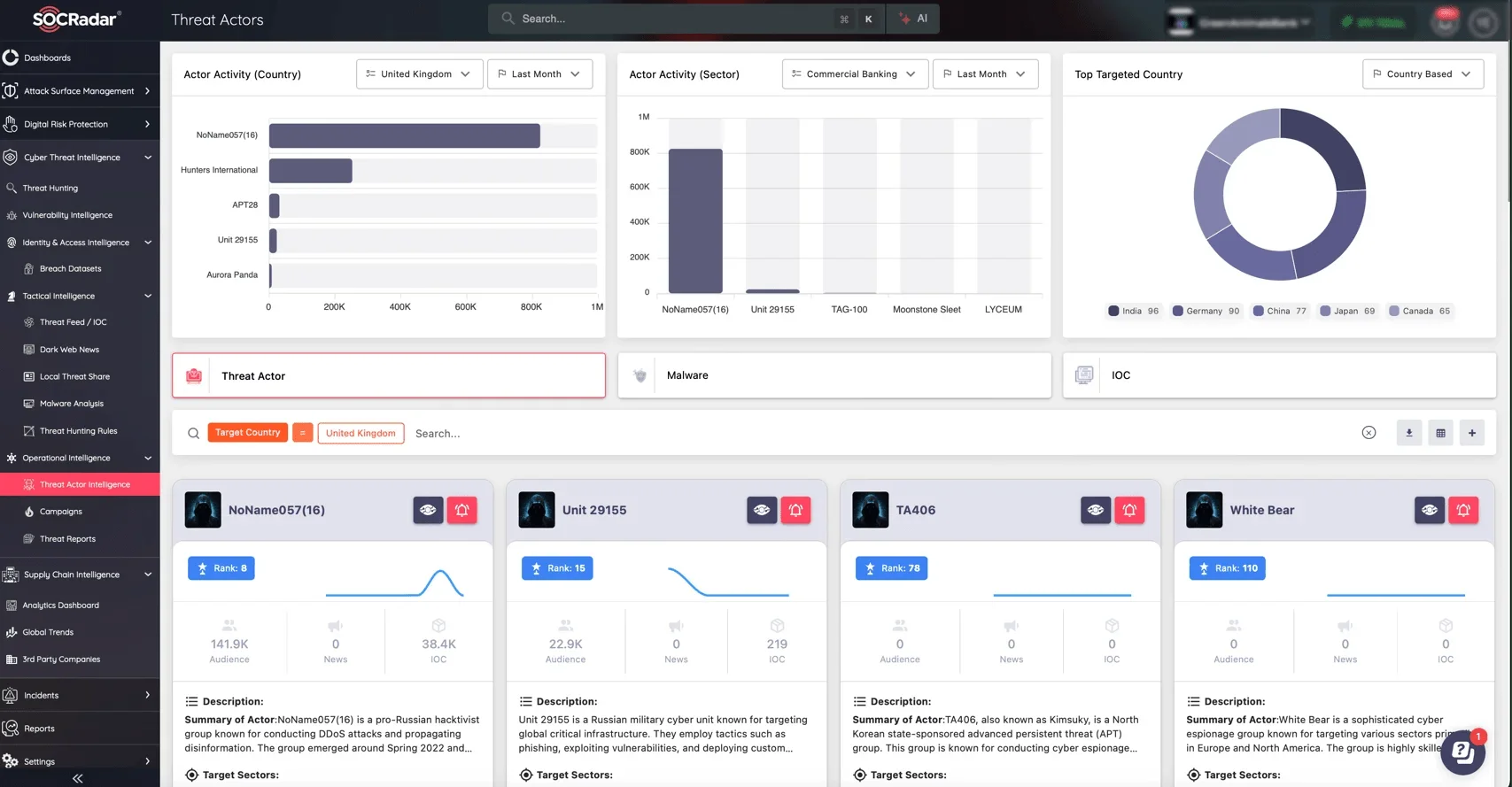
SOCRadar Threat Actor Intelligence
Enhance your organization’s defense against Denial-of-Service (DoS) threats with SOCRadar Labs’ DoS Resilience module. DoS Resilience allows you to test your domain’s or subnet’s ability to resist DoS attacks.
SOCRadar DoS Resilience
10. Targeted Attacks on IoT Devices and New Vulnerabilities in the Expanding Digital Landscape
As the number of Internet of Things (IoT) devices continues to rise, so too do the security risks associated with them. In 2024, the proliferation of connected devices has opened up new attack vectors for cybercriminals. IoT devices, which often lack robust security measures, are now being targeted by threat actors to gain access to broader networks, making them key entry points in cyberattacks.
Cybercriminals are exploiting weaknesses in IoT devices, such as default credentials, outdated firmware, and poor encryption practices. Once compromised, these devices can serve as gateways to more critical systems, enabling attackers to access sensitive data, disrupt services, or even launch larger-scale Distributed Denial of Service (DDoS) attacks. As IoT devices become integral to smart cities, manufacturing systems, and healthcare infrastructure, the impact of these vulnerabilities becomes even more severe.

The Internet of Things (IoT)
The targeted attacks on IoT devices can lead to significant consequences, including operational disruptions, financial loss, and even physical harm, particularly in sectors where IoT devices control critical infrastructure. As the threat landscape evolves, there is an urgent need for improved security protocols for IoT devices, such as device authentication, firmware updates, and network segmentation, to minimize the risk of exploitation.
SOCRadar’s Attack Surface Management (ASM) helps secure IoT environments by providing comprehensive visibility into all connected devices and their potential vulnerabilities. It continuously monitors your IoT infrastructure to detect exposed devices, weak configurations, and other risks that could be exploited by attackers.
With real-time alerts, SOCRadar’s ASM ensures you can address issues such as misconfigurations or open ports quickly, preventing cybercriminals from leveraging these gaps to infiltrate broader networks. By identifying and mitigating IoT-related threats proactively, SOCRadar enhances the overall security posture of organizations, ensuring connected devices don’t become an entry point for larger attacks.
Conclusion: Lessons for a Resilient Future
The first half of 2024 has been a wake-up call for businesses and cybersecurity professionals alike. From the relentless rise of ransomware to the growing sophistication of AI-driven attacks, it’s clear that the threat landscape is becoming more challenging with each passing day. However, amid these evolving dangers, one thing remains constant: the ability to adapt and learn from past incidents is the key to building a more resilient defense.
By implementing proactive security measures, such as multi-layered defenses, continuous monitoring, and robust incident response plans, organizations can stay ahead of emerging threats. The lessons learned in the trenches of 2024’s cybersecurity battlefield should serve as a blueprint for future preparedness. As we move forward, staying vigilant, continuously improving, and embracing innovation will be essential in safeguarding against the ever-changing tactics of cybercriminals.
The battle is far from over, but with the right strategies in place, businesses can not only survive but thrive in this volatile environment. Stay prepared, stay secure, and let these lessons guide your cybersecurity journey into the next half of 2024 and beyond.



































