
Top 5 Tools for Phishing Domain Detection
Phishing attacks have victimized many users and companies for years, and it seems they will continue to do so. Many security measures have been taken against such attacks. However, the attackers develop new TTPs with the developing technology and carry out their attacks with the same effect, even in a way that will reach broader masses in a shorter time.
Although the best way to deal with this is to make employees aware of information security, unfortunately, this is often impossible.
In this case, the best action we can take is to detect the attack in advance, inform the target people about this malicious domain, and ensure that the domain is closed as soon as possible on the same day.
How to Detect Phishing Domains?
1. URLScan
urlscan.io is a service that allows you to scan and analyze URLs. URLScan records this activity by analyzing the URL it receives from users. As a result, URLScan has many suspicious domains in its pool, among which we can detect phishing domains using some dorks.
In the URLScan Search section, we can use the following dork to detect domains other than paypal.com that contain ‘paypal’
page.domain:(/paypal.*/ AND NOT paypal.com)
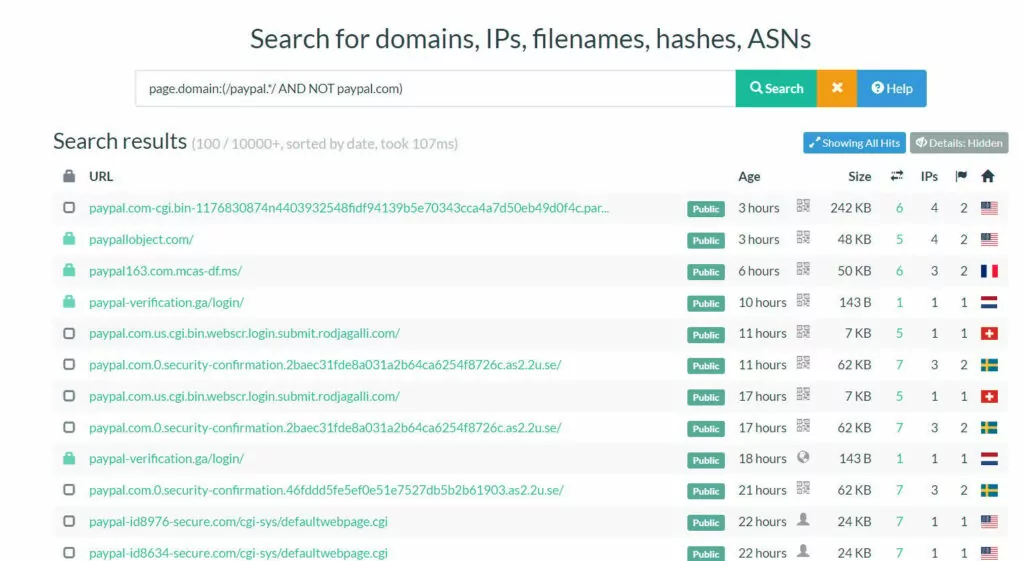
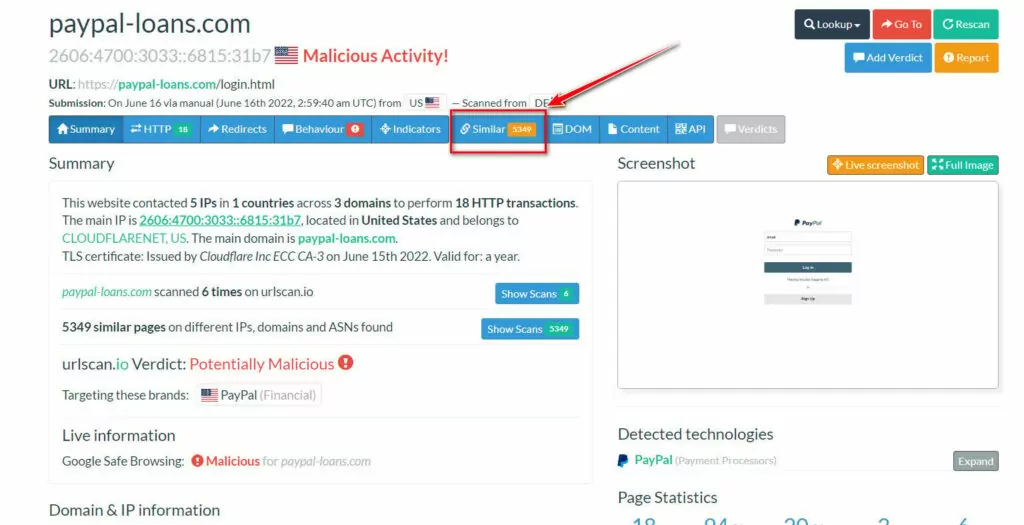
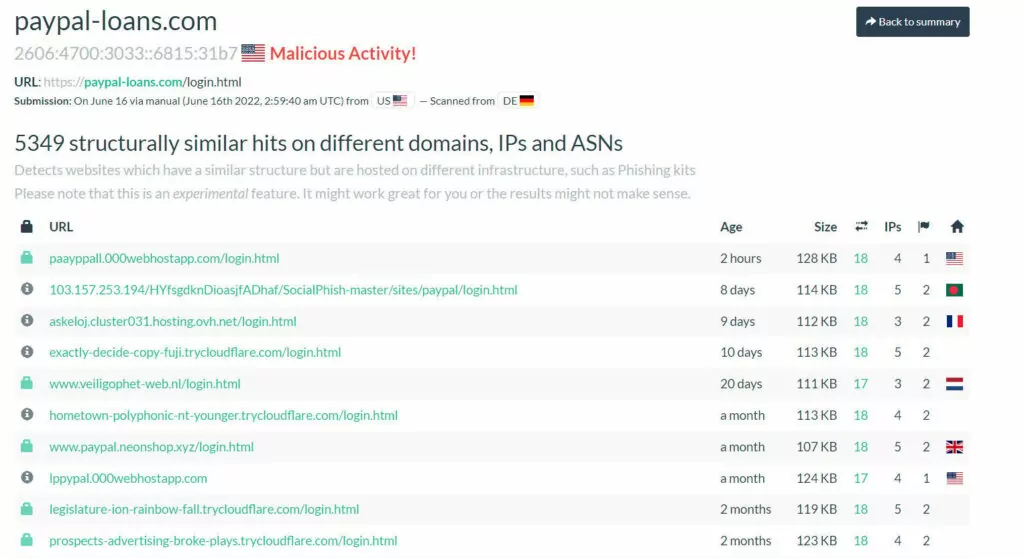
It is also possible to access many domains with the same or similar content via the phishing domain identified with the dork above. We can use the “similar” feature of URLscan for this.
2. Censys
Certificate Transparency (CT) is a project that collects the certificates issued and makes this data available to the public. By filtering Certificate Transparency logs, we can easily extract domains and search within those domains using keywords.
We can access certificate transparency logs from many different sources such as certdb, crt.sh. However, it is not easy or practical to make the kind of queries we want in most resources. The Censys mass scanner can be used to query the CT logs practically.
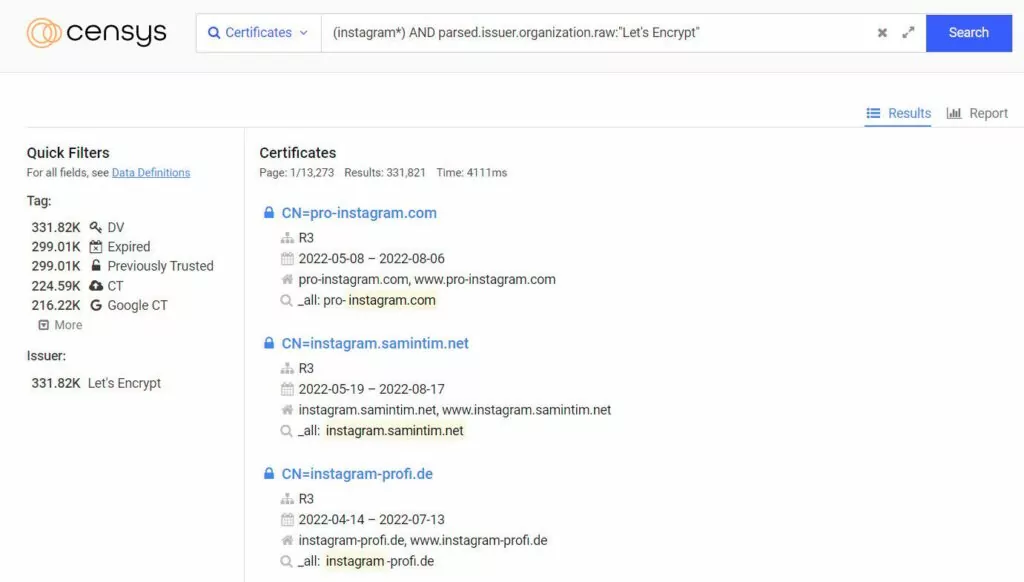
Nowadays, getting free SSL certificates from certificate authorities such as Let’s Encrypt is quite easy. This leads attackers to obtain an SSL certificate to make the attack more legitimate. As a result, when the victim visits the phishing site, the ‘Secure’ badge appears in the URL bar.
It is possible to detect these phishing sites with Censys. So how can we use it?
(instagram*) AND parsed.issuer.organization.raw:”Let’s Encrypt”
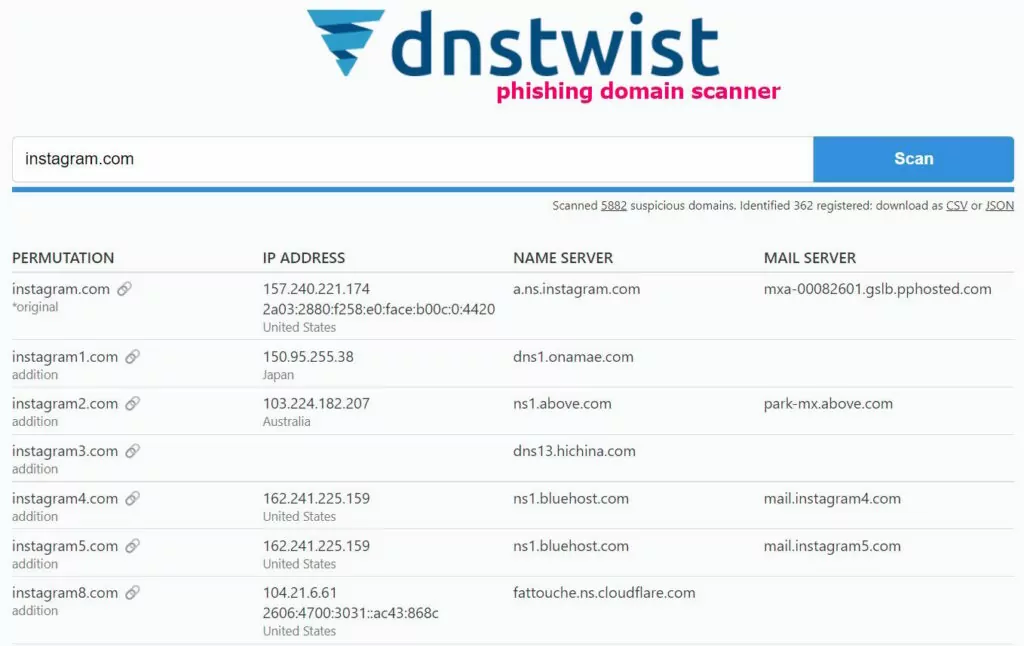
3. Dnstwist
Similar domain names are created by applying typosquatting, attack methods such as addition, bitsquatting, and homoglyph to the target domain. These are the most common situations in a phishing attack. We can use the dnstwist tool to detect such domains.
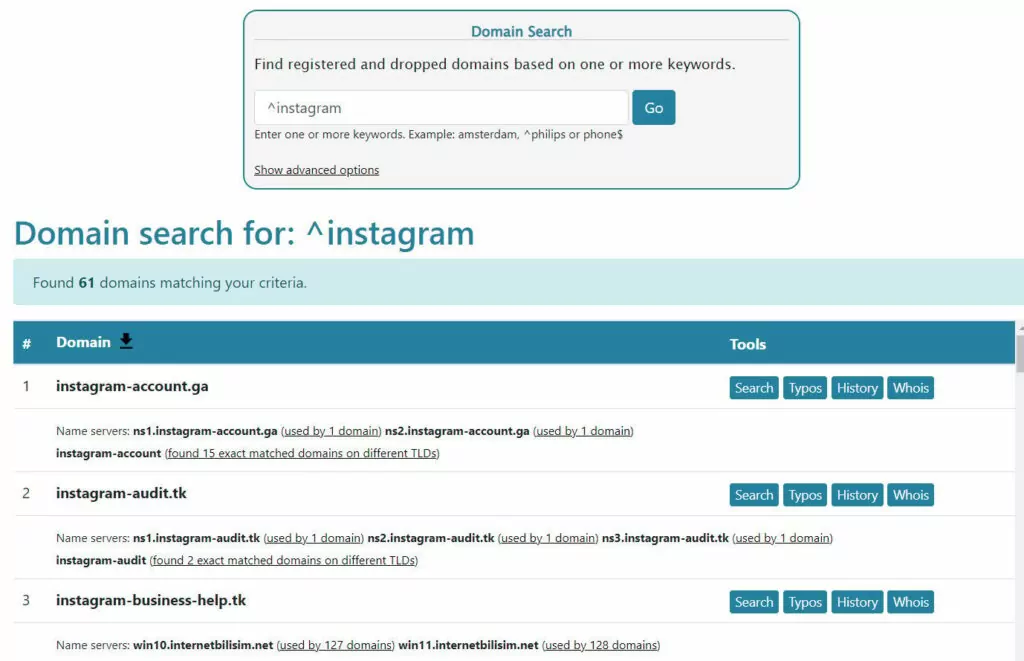
4. Dnslystic
Dnslystic hosts many of the newly registered domains in its database, making it very easy for us to detect phishing domains among them. It allows us to search all Top Level Domains, including gTLDs, nTLDs, and ccTLDs.
You can easily find phishing domains targeting your brand by using some dorks.
For example:
- ^instagram: List domains starting with “Instagram”
- instagram$: List domains ending with “Instagram”
- !news: Don’t list what contains “news”
5. openSquat
openSquat is an open-source intelligence (OSINT) tool to identify cyber threats to specific companies or organizations. It is a handy tool for collecting information on newly registered domains. Although there is a web version, using the code available on GitHub offers additional advantages. It allows daily, weekly, and monthly research to be done.
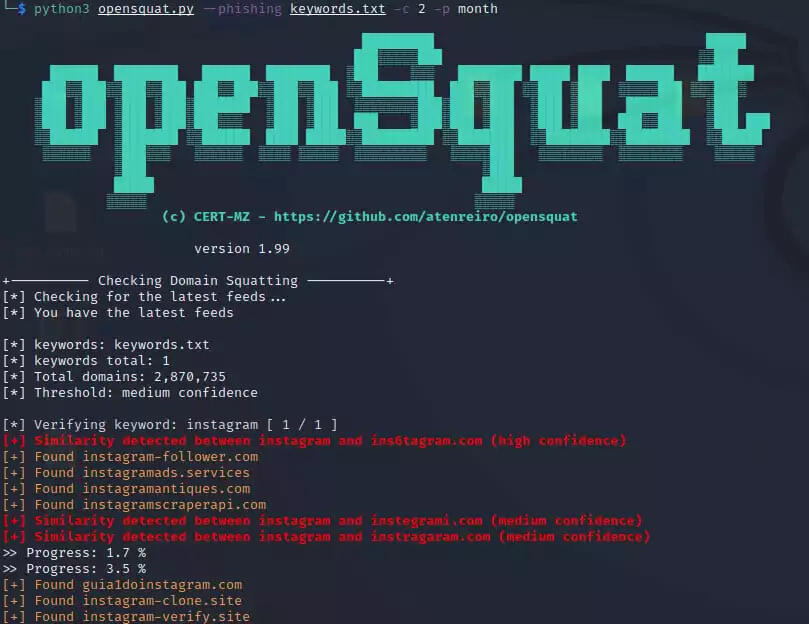
The parameters to be used when researching will give you a tradeoff. You can get more results by missing some domains as long as you want the affinity rate higher in the keywords you specify or by being more sensitive and choosing words far from your keyword. This will result in encountering more false positive domains.





































