
VMware ESXi Hypervisor Vulnerability (CVE-2024-37085) Exploited by Ransomware Groups, Microsoft Warns
[Update] July 31, 2024: “CISA Adds VMware ESXi Hypervisor Vulnerability (CVE-2024-37085) to KEV Catalog”
Microsoft recently brought attention to the active exploitation of CVE-2024-37085, a critical vulnerability in Broadcom’s VMware ESXi hypervisors.
The CVE-2024-37085 vulnerability, stemming from Active Directory integration, allows ransomware groups to execute zero-day attacks and gain full administrative control over domain-joined ESXi hypervisors.
ESXi provides direct access to underlying server resources and hosts vital virtual machines essential for network operations. Thereby, with administrative access achieved via exploitation of the vulnerability, attackers can lead to extensive damage on the network.
What Is CVE-2024-37085?
CVE-2024-37085 (CVSS: 6.8, Medium) is an authentication bypass vulnerability that enables attackers to exploit Active Directory integration in VMware ESXi hypervisors, eventually leading to privilege escalation.
By creating a ‘ESX Admins’ group in Active Directory, attackers can automatically grant a new user full administrative privileges on the ESXi hypervisor.
The ESX Admins group is not built-in and does not exist by default in Active Directory; however, when joined to a domain, ESXi hypervisors do not check for the group’s existence, treating any members of such a group as having full administrative rights, even if it was created by an attacker.
Overall, the CVE-2024-37085 vulnerability, if exploited, allows attackers to completely control the hypervisor and the virtual machines it hosts.
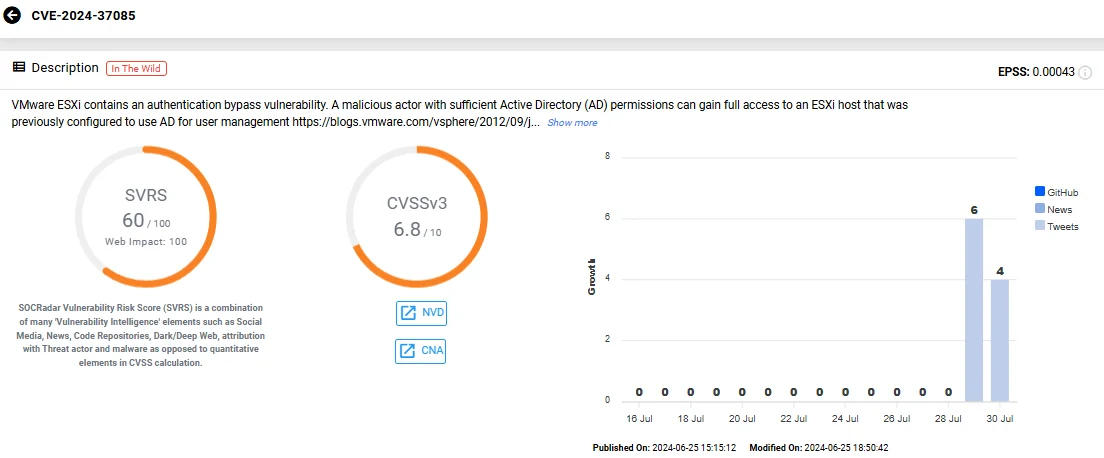
Vulnerability card of CVE-2024-37085 (SOCRadar Vulnerability Intelligence)
Microsoft security researchers identified three specific methods that can be used to exploit this vulnerability.
The first method involves creating the ESX Admins group and adding it to the domain with a new user, granting admin access. The second method entails renaming any domain group to ESX Admins and adding a user or utilizing an existing member for administrative privileges. The final method could leverage that assigning admin privileges to other groups does not remove them from the ESX Admins group, allowing attackers to maintain unauthorized access.
SOCRadar’s Vulnerability Intelligence monitors CVE and exploitation trends in real time, providing you with an extensive database and advanced analytics for tracking updates, identifying exploits, and gaining actionable insights for proactive vulnerability management.
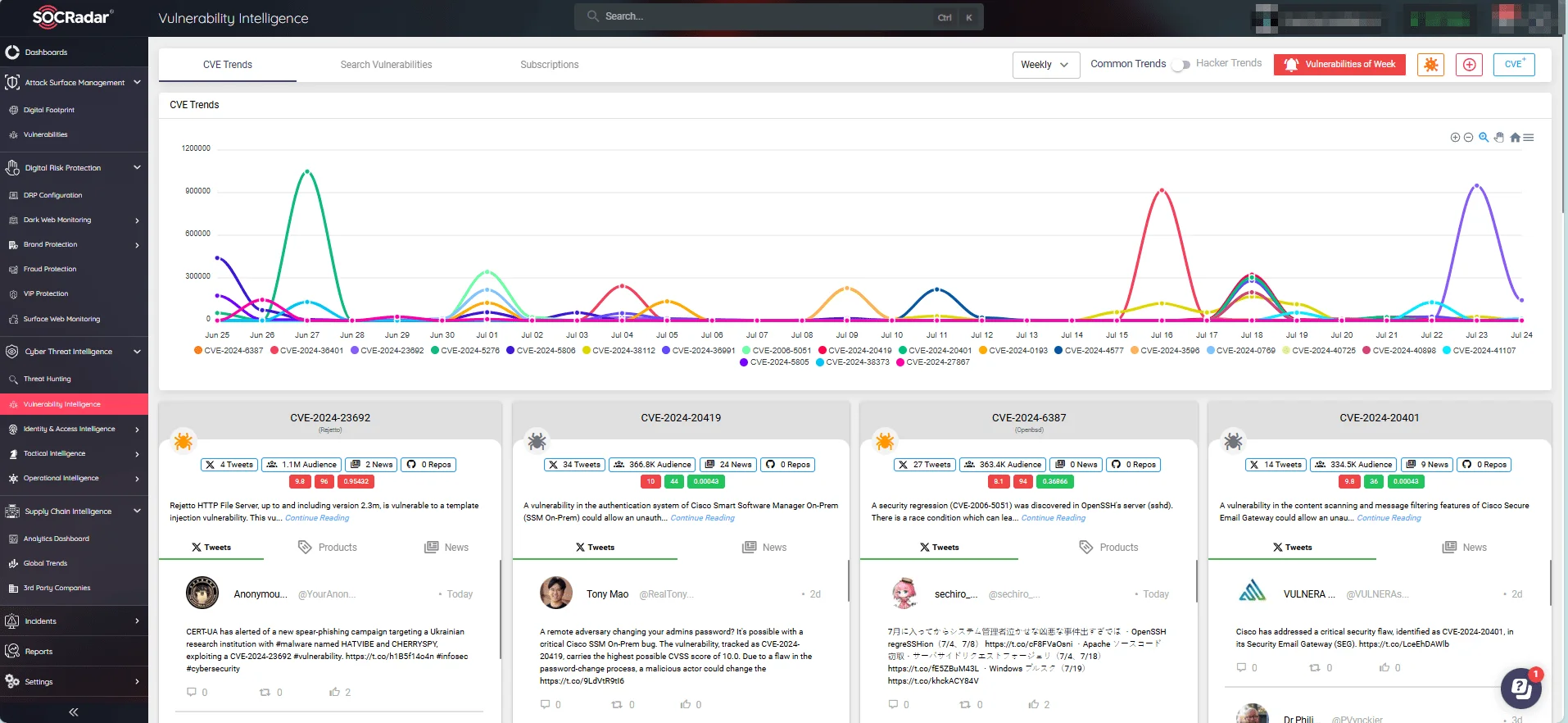
Keep up with emerging CVEs and hacker trends, and access extensive information on vulnerabilities with SOCRadar’s Vulnerability Intelligence module
ESXi Hypervisors Targeted with Ransomware
Microsoft has observed a rise in ransomware attacks targeting ESXi hypervisors over the past year. The tech giant states that these hypervisors are appealing targets due to limited visibility and protection from many security products.
Encrypting an ESXi hypervisor file system allows attackers to execute mass encryption with a single action, impacting all hosted virtual machines. This method provides more time and opportunities for attackers to move laterally and steal credentials within the network.
Ransomware groups such as Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest have been identified to support or sell ESXi encryptors like Akira, Black Basta, Babuk, Lockbit, and Kuiper.
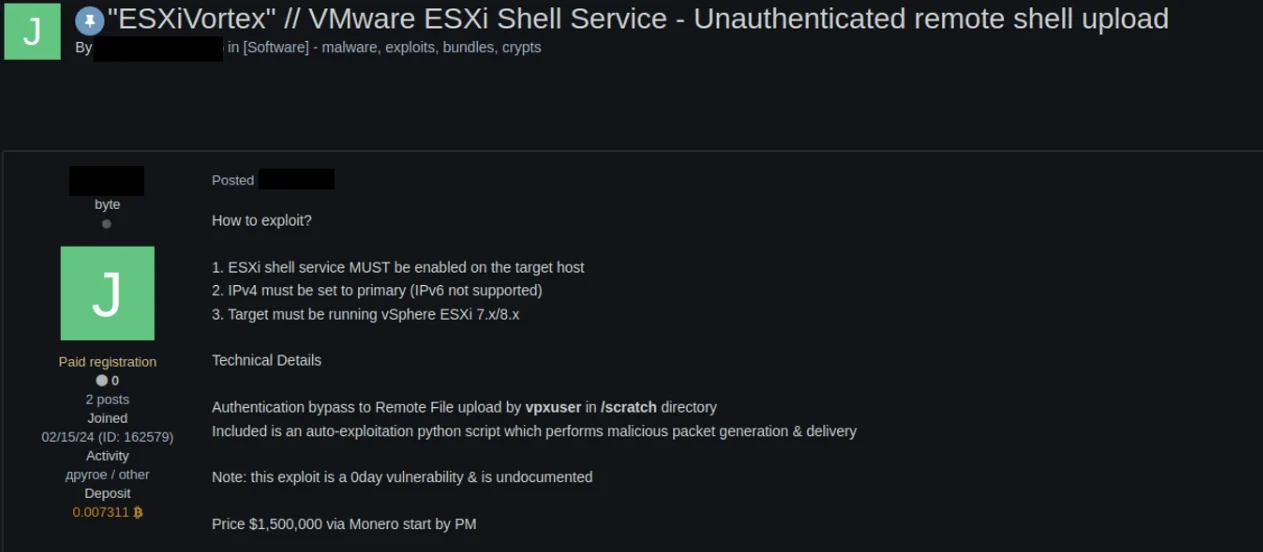
Sale post for an unauthenticated ESXi shell on a dark web forum (Microsoft)
Microsoft stated that in early 2024, a North American engineering firm was targeted by a Black Basta ransomware attack from Storm-0506, which exploited CVE-2024-37085 for privilege escalation.
Initial access was gained through a Qakbot infection, followed by exploiting a Windows CLFS vulnerability (CVE-2023-28252) for privilege escalation. Using tools like Cobalt Strike and Pypykatz, they stole domain administrator credentials and moved laterally to domain controllers, where they installed persistence mechanisms and attempted to brute-force RDP connections.
The attackers created the “ESX Admins” group, added a new user, and encrypted the ESXi file system, disrupting hosted virtual machines. They also used PsExec to encrypt devices not on the ESXi hypervisor.
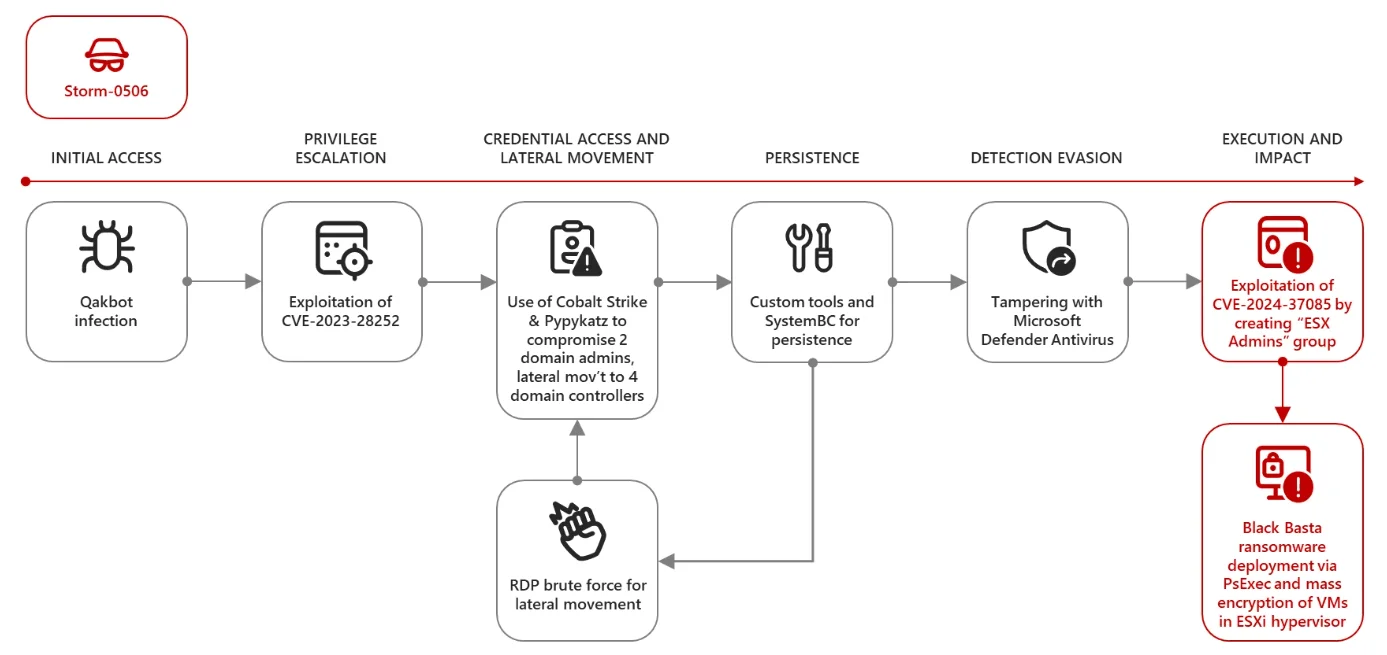
The attack chain (Microsoft)
CISA Adds VMware ESXi Hypervisor Vulnerability (CVE-2024-37085) to KEV Catalog
On July 30, 2024, CISA included CVE-2024-37085 in its Known Exploited Vulnerabilities (KEV) Catalog.
CISA emphasizes that such vulnerabilities are frequent targets for threat actors and pose serious risks to federal enterprises; thus, federal agencies are mandated to patch this vulnerability by August 20, 2024.
In this regard, it is strongly recommended to implement mitigations as advised by the vendor or discontinue the product’s use.
The Potential Attack Surface of VMware ESXi Servers
According to a ZoomEye search, there are over 434,000 VMware ESXi servers exposed, highlighting a significant potential attack surface.
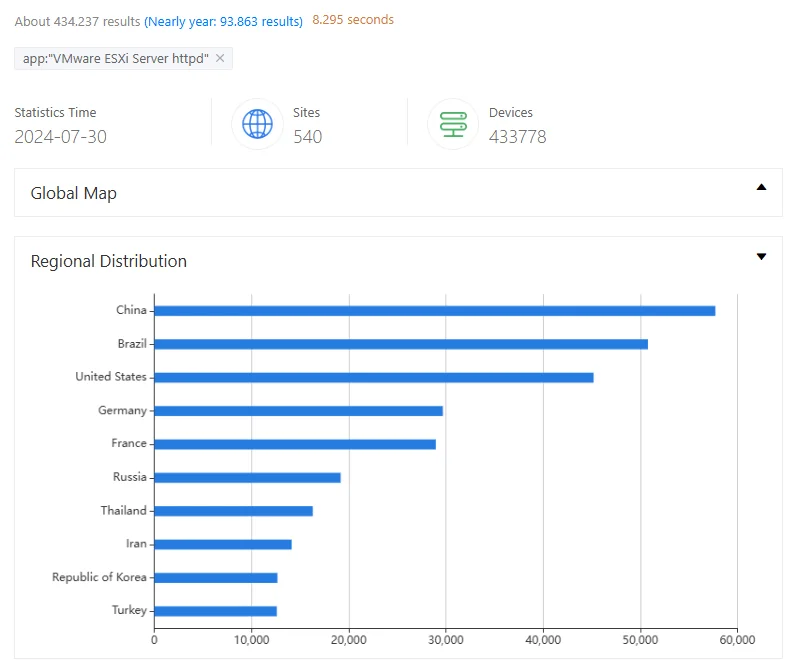
ZoomEye search results for exposed VMware ESXi Server instances
According to Rapid7 researchers, ransomware groups have long been interested in exploiting ESXi hypervisors. Nevertheless, since ESXi servers shouldn’t be left open to the public, it is unlikely that CVE-2024-37085 will be used as an initial access vector. In order to take advantage of this vulnerability, attackers would need previous access to the target system.
Patch CVE-2024-37085
With the release of ESXi 8.0 U3, Broadcom fixed CVE-2024-37085 and two additional vulnerabilities, CVE-2024-37086 and CVE-2024-37087. For detailed information and to access the update, visit the official Broadcom advisory.
Are There Any Workarounds?
If updating is not immediately feasible, you can implement the following workarounds to mitigate the issue:
- Change the ESXi advanced option Config.HostAgent.plugins.hostsvc.esxAdminsGroupAutoAdd from true to false.
- Adjust the Config.HostAgent.plugins.vimsvc.authValidateInterval from 1440 to 90.
- Set Config.HostAgent.plugins.hostsvc.esxAdminsGroup from “ESX Admins” to “”.
With these mitigation methods, Broadcom also notes that the “ESX Admins” group will be added to the host with admin privileges once the host is added to Active Directory. It is recommended to change these settings after joining the domain.
For more details on workarounds, refer to the CVE-2024-37085 workaround article.
Monitor your digital footprint and obtain useful intelligence to stay ahead of threat actors by utilizing the Attack Surface Management (ASM) module of the SOCRadar XTI platform.
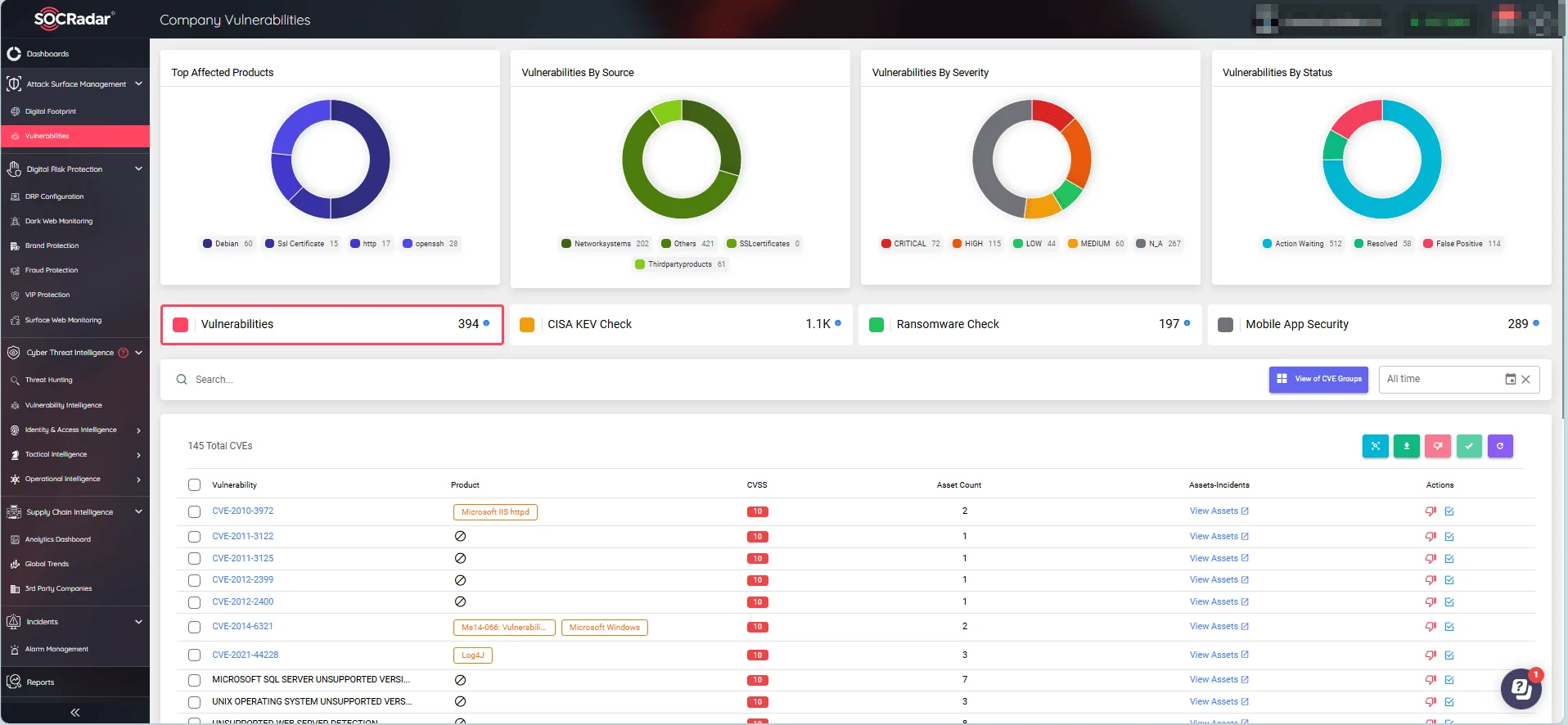
Monitor digital assets and security flaws with SOCRadar’s Attack Surface Management (ASM) module
Additionally, the platform offers alerts for new security vulnerabilities within your company, enabling more efficient patch management and a more effective security posture.


































