Vocalcom Ransomware Attack, Credit Card Sales, and Botnet Services
This week, we have some troubling news to share, like always. We’ve learned that half a million credit cards belonging to Brazilians are up for sale on the dark web. In addition, an American shop has been compromised with unauthorized admin access for sale, putting both the business and its customers at risk.
Our researchers also detected a new Android botnet APK crypt service that cybercriminals could use to evade detection and another victim of the Play ransomware: Vocalcom.
Here are some details about the issues.
Find out if your data has been exposed.
500K Credit Cards Belonging to Brazilians are on Sale
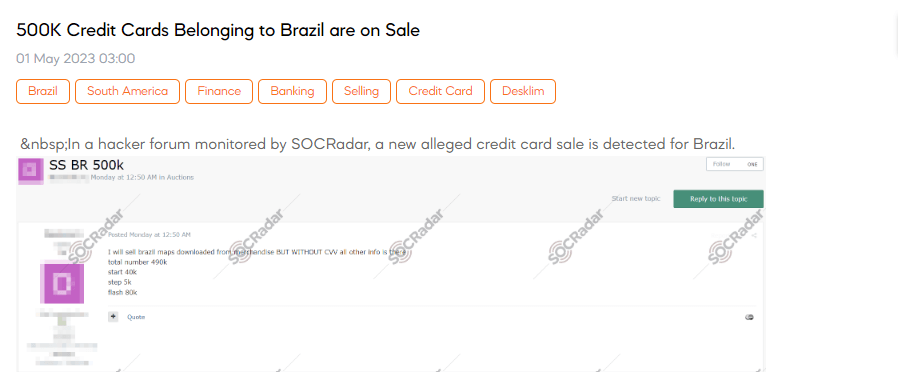
SOCRadar detected a post on a hacker forum dominated by Russian threat actors. The post advertised the sale of credit card information purportedly belonging to Brazilian citizens. The credit card data available for purchase reportedly does not contain the Card Verification Value (CVV) but includes all other essential details. The seller claims the total number of available credit card details is 490,000.
Unauthorized Admin Access Sale is Detected for an American Shop
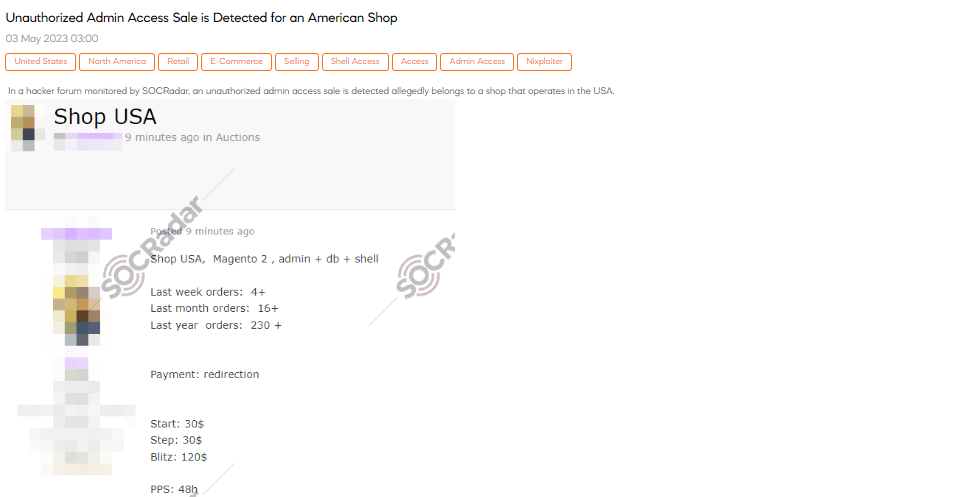
SOCRadar dark web analysts have detected a post in a hacker forum revealing the sale of unauthorized administrative access to a shop operating in the US. The compromised shop is based on the Magento platform and includes access to the admin panel, database, and shell. According to the post, the shop has processed at least four orders in the past week, sixteen orders in the last month, and a significant 230+ orders within the past year. The payment method involves redirection. The starting price for this illicit access is $30, with bidding increments of $30. Additionally, a blitz option is available for immediate purchase at $120.
New Android Botnet APK Crypt Services Detected
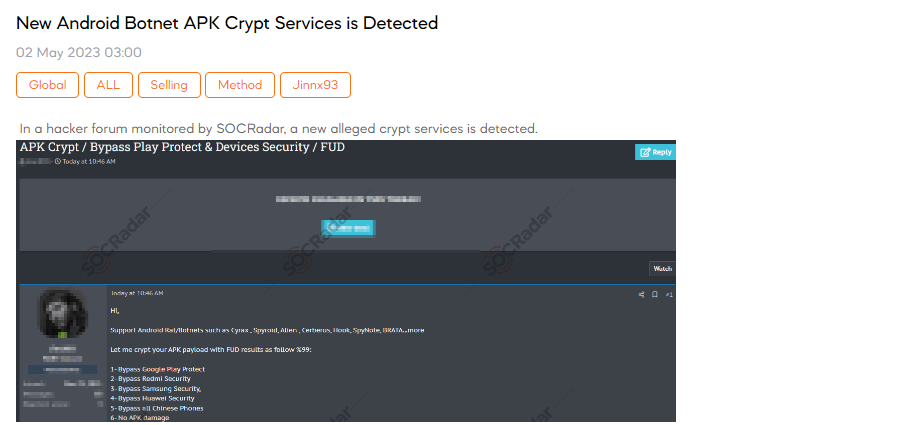
SOCRadar dark web team recently discovered a post on a hacker forum revealing the presence of a new alleged crypt service. This service claims its ability to support Android RAT/botnets such as Cyrax, Spyroid, Alien, Cerberus, Hook, SpyNote, BRATA, and more. The individual behind the service claims to crypt APK payloads with FUD (Fully Undetectable) results, offering a range of benefits. These include bypassing security measures such as Google Play Protect, Redmi Security, Samsung Security, Huawei Security, and even security on Chinese phones. Interested users are encouraged to make payments only after the file has been crypted and tested. Pricing options include $35 for one crypt, $80 for three crypts, and $135 for five crypts. In addition, the crypter is being sold to a limited number of users, with only three copies available. The seller also offers free monthly updates.
The New Play Ransomware Victim: Vocalcom
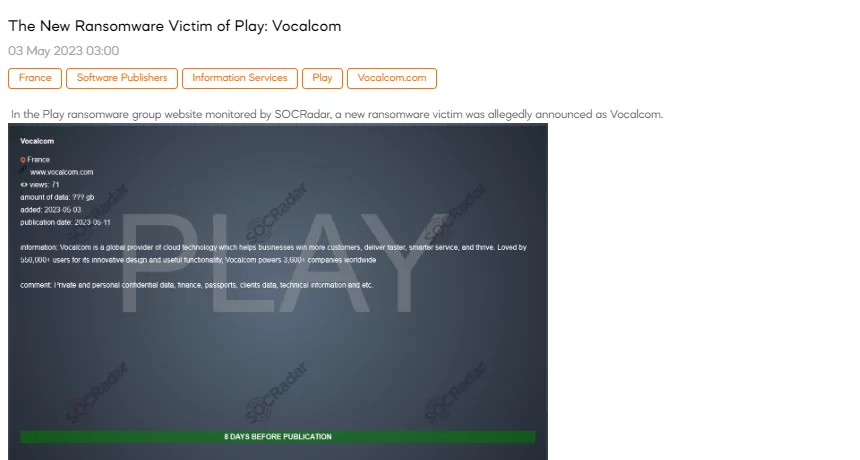
SOCRadar dark web researcher found a post that the Play ransomware group claimed responsibility for the cyberattack on Vocalcom. The company, a prominent provider of cloud-based contact center software and customer engagement solutions, has recently fallen prey to Play’s cyber attacks. According to the post, the threat actors claim to have accessed and compromised sensitive data, including private and confidential information, finance, passports, client data, and technical information.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.