
What is Password Analyzer?
A password strength checker is an online application that assesses the security of a user’s password in real-time by analyzing its grammar and highlighting possible vulnerabilities.
The program verifies the usage of certain sequences of characters, such as proximity keys “asdf” and “qazwsx,” and very frequent weak passwords such as “123456” and “password1.” Other essential aspects evaluated are:
- The mix of alphanumeric and special characters.
- The number of characters.
- The originality of the password.
Risks of Weak Passwords
Weak passwords might enable hackers to access your account. They might utilize compromised email and social media accounts as spam bots. They can steal sensitive information, which may result in identity theft.
Short and simple passwords are susceptible to “brute force” assaults, which try every conceivable combination of characters until they find the right one. Typically, they begin by attempting combinations of lowercase letters. Personal information (birth year, favorite sports team) makes passwords simpler for hackers to guess.
What is the Strongest Password?
In settings involving frequent users, objectives, and accounts, a password should be at least 12 characters, preferably 16 or more. If the password is too short, hackers will easily guess it.
The greater the number of characters utilized, the less likely it is to be readily hacked. The minimum length suggested for privileged accounts, services, and administrators is 25 characters.
A strong password must at least adhere to the following guidelines:
- Length. Strong passwords consist of at least 12 to 16 characters (the longer, the better);
- Uniqueness. Avoid sharing passwords across many internet accounts.
- Discontinuity. It should not include numbers or characters in succession.
- Impersonal. Leave out personal information (birthplace or date, address, names of children/pets).
- Complexity. Create a combination of numbers, special characters, and letters that is difficult to predict (both uppercase and lowercase).
- No repetitions. Strong passwords exclude the term “password” and avoid letter and number repetition.
How Can You Remember All of Your Complex Passwords?

All your passwords should be different so that if one is leaked to a hacker, threat actors can’t use it across all your accounts. It would be best if you regularly changed passwords. Companies might not inform users of data breaches, and leaked passwords might not be used for long periods by hackers.
Memorizing your newest passwords can be difficult, so we recommend using a password manager. A password manager stores all your accounts’ passwords into a single app or browser extension and can input them automatically when you log in. You only need to remember a single master password to access them. Additional benefits of utilizing a password manager include:
- Multi-device synchronization.
- Integrated strong password generator.
- Convenient integration of autofill across platforms.
- Data is saved, managed, and exchanged securely.
- The ease of signing in, altering, and changing passwords.
How to Check if a Password is Leaked/Compromised?
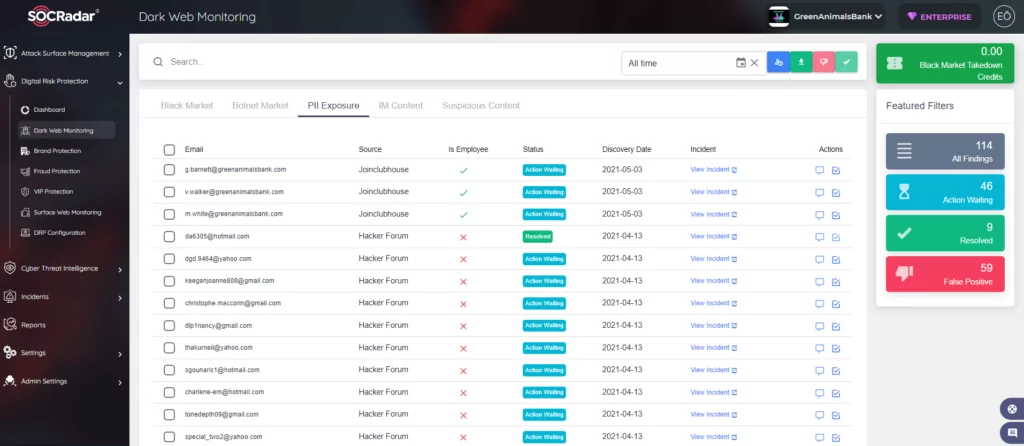
SOCRadar analyzes the surface, deep & dark web for personally identifiable information (PII), including the most recent hacked account passwords and credit card data pertinent to your business. This data is extracted from a broad range of Internet sources (surface and deep/dark web) to safeguard your firm against identity theft and fraud.
The historical accuracy and expanding robustness of SOCRadar’s database enable analysts to cut through the noise, focusing SOC analyst time and attention on important security occurrences.



































