
What Is Shadow SaaS and How It Increases Vulnerability to SaaS Attacks
The concept of Shadow SaaS – where employees use unauthorized Software-as-a-Service (SaaS) applications – represents a significant shift in how data is accessed and managed across corporate environments. This trend, driven by the rapid adoption of convenient but unsanctioned applications, stretches the boundaries of traditional IT oversight.

An AI illustration for “Shadow SaaS,” by DALL-E
As employees register for SaaS applications, often just to explore a free trial, they inadvertently expose corporate data to a variety of risks. This widespread use of unauthorized apps creates a fertile ground for identity-related attacks, where vast amounts of sensitive information become vulnerable within this sprawling digital ecosystem.
What is Shadow SaaS?
Shadow SaaS refers to the use of Software-as-a-Service (SaaS) applications by employees without the explicit approval or oversight of their organization’s IT department.
This phenomenon is increasingly common in modern workplaces, where the rapid pace of technological change and the growing demand for flexible, efficient work solutions drive employees to seek out and use cloud-based tools that meet their immediate needs. Often, these tools offer simplicity and functionality that sanctioned corporate software may lack, leading to their quiet integration into daily business operations.
The Security Risks of Shadow SaaS
Shadow SaaS exposes organizations to multiple security vulnerabilities since these systems operate beyond regulated IT environments, risking sensitive data and opening pathways for cyber-attacks.
The widespread use and inherent vulnerabilities of cloud-based SaaS applications attract attackers seeking persistent access to corporate data, challenging incident response teams that may lack cloud-specific expertise. To combat this, organizations necessitate a deep understanding of unique app vulnerabilities and integration of this knowledge into security strategies.
Why Is Shadow SaaS ‘More Exposed’ to SaaS Attacks?
Applications that can be considered “Shadow SaaS,” due to their unofficial usage, are particularly vulnerable to SaaS-specific attacks as they often circumvent standard organizational cybersecurity measures.
For instance, credential stuffing can exploit weak or reused passwords on platforms adopted independently by employees. Unmonitored by IT, these login attempts can remain undetected until significant damage has occurred.
Similarly, phishing attacks are more effective against Shadow SaaS due to inadequate corporate filtering and inconsistent security policy enforcement, such as multi-factor authentication, leaving employees more susceptible to deception.
Compliance Issues
Shadow SaaS also poses severe challenges in compliance, as these applications often bypass standard regulatory checks.
For example, an employee using a non-compliant file-sharing app could inadvertently expose personal data. Additionally, decentralized management of these apps complicates data integrity and secure access, reducing the ability to conduct thorough security audits and complicating compliance, potentially resulting in serious legal and financial consequences.
To mitigate these risks, IT departments must improve visibility across their software landscape and implement flexible, strong policies that do not compromise security.
SOCRadar’s Attack Surface Management (ASM) module provides continuous monitoring of digital assets and components, identifying vulnerabilities within your environment. It helps manage exposure by alerting organizations to suspicious activities, thereby securing against potential cyberattacks and their consequences.
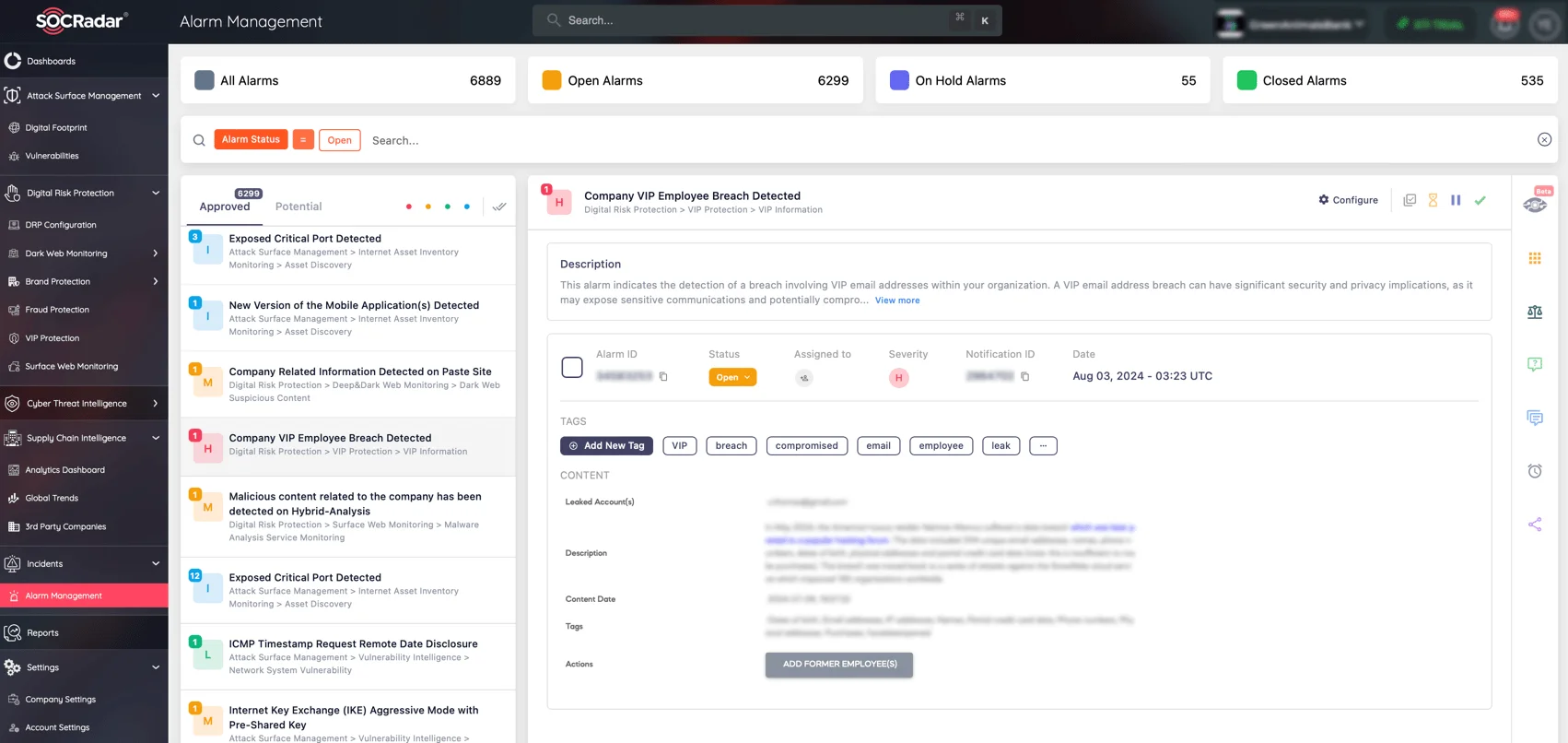
Alarm: VIP Employee Breach Detected (SOCRadar Alarm Management)
Why Employees Turn to Shadow SaaS
Employees typically turn to Shadow SaaS for several compelling reasons. Firstly, the agility and ease of access associated with these applications can significantly increase productivity and collaboration.
Employees might find that unsanctioned tools better facilitate real-time collaboration with colleagues or offer more user-friendly interfaces than the officially approved options. The rapid user-driven adoption of SaaS applications, largely unsanctioned by IT departments, has amplified the threat landscape, and increased the risk of identity attacks.
According to a 2024 report by Push, only one in five SaaS apps are officially sanctioned, leaving the majority unchecked and vulnerable to exploitation. The ease of account creation and maintenance, aimed at user convenience and reducing support costs, often compromises security, highlighting a need for security-centric procurement processes.

In the SaaS Attacks report for 2024, it was mentioned that only 1 in 5 SaaS apps are officially sanctioned by the business.
Secondly, the process to gain approval for new tools through official IT channels can be slow and cumbersome. In fast-paced work environments, employees may feel they don’t have the time to wait for approval and thus proceed without it to maintain their productivity.
Lastly, there may be a gap in the tools provided by the organization and the specific needs or preferences of the employees. When existing tools do not fully address their tasks, employees might seek out Shadow SaaS solutions that offer the exact features or capabilities they need, even if this means bypassing IT policies.
Overview of Key SaaS Attack Techniques
With the adoption of Shadow SaaS, organizations become more susceptible to specific SaaS attack techniques.
The SaaS attacks report we mentioned also discusses the challenges of securing identities across an expansive array of apps, each with its unique settings and vulnerabilities. There is a SaaS attack matrix provided, which serves as a critical tool in understanding and defending against these identity-based attacks.
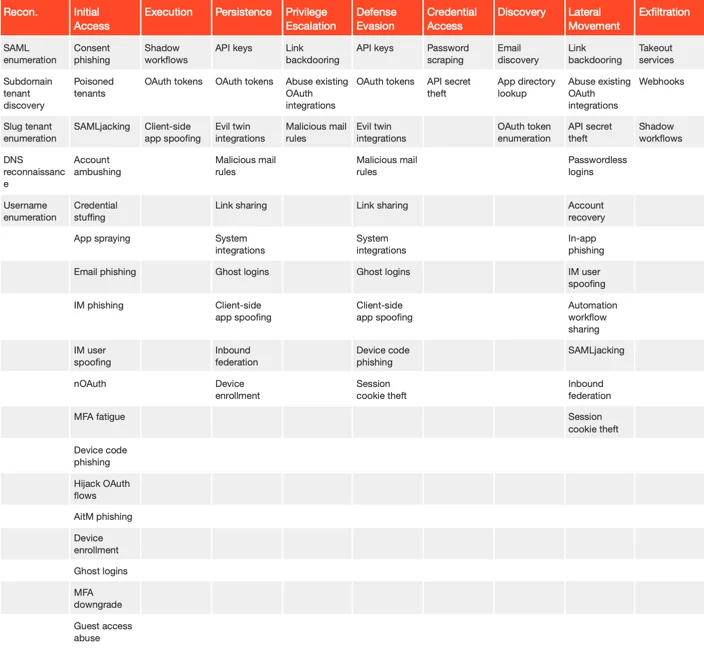
SaaS attacks matrix (SaaS Attacks Report 2024)
In this section, we explore some of the most notable techniques, particularly focusing on those categorized under Initial Access, and highlight others that play a crucial role across different stages of a SaaS attack lifecycle.
Initial Access Techniques
- Ghost Logins: This technique exploits the capability of SaaS platforms to handle multiple concurrent logins. Attackers use different authentication methods to maintain access without detection, often bypassing Multi-Factor Authentication (MFA) systems that are not uniformly enforced across all access points.
This vulnerability is especially concerning for Shadow SaaS, as these platforms often lack rigorous security protocols enforced by your organization.
For instance, an employee might use an unsanctioned project management tool with weaker security standards, enabling attackers to maintain access through dormant sessions or old credentials that were never properly secured or revoked.
- Consent Phishing: Often seen with SaaS applications that use OAuth for permissions, consent phishing tricks users into granting malicious apps permissions under the guise of legitimate requests. This method cleverly bypasses the need to directly compromise credentials by abusing the OAuth consent frameworks.
- SAMLjacking: This sophisticated attack involves manipulating SAML (Security Assertion Markup Language) responses to redirect users to attacker-controlled domains during the authentication process. It’s particularly effective in environments where SAML is used for Single Sign-On (SSO) across multiple applications.
- MFA Downgrade: MFA downgrade attacks involve tricking the system into bypassing multi-factor authentication, often by exploiting fallback mechanisms in the authentication process. Employees using Shadow SaaS solutions may set up MFA independently without aligning with the stronger, corporate-standard authentication methods.
Attackers can exploit this by initiating a recovery or update process that only requires knowledge-based answers or SMS-based authentication, which are easier to intercept or guess than app-based MFA codes.
- Adversary-in-the-Middle (AiTM) Phishing: This newer variant of phishing uses dedicated tooling to act as a web proxy between the victim and a legitimate login portal, making it easier to defeat MFA protection. Because the attacker can observe and manipulate the traffic, they can capture the MFA tokens or responses and gain access to the session.
Employees using Shadow SaaS are particularly vulnerable because they might not benefit from corporate network protections such as secure web gateways or advanced threat detection systems that can identify and block suspicious connections.
An example is an employee using an unauthorized SaaS tool for customer relationship management, which could be compromised to intercept customer data and login credentials.
There are also BitM attacks (Browser-in-the-Middle), which are a variation of AitM, where the attacker manipulates the user’s browser itself. This could involve tricking a user into installing a malicious browser extension that mimics legitimate functionality. Shadow SaaS applications, accessed without IT oversight, provide a fertile ground for such exploits.
For example, an employee could download a browser extension thinking it will integrate their unsanctioned SaaS tool with other systems, not knowing it’s designed to capture all their input data.
- Credential Stuffing: A more common but highly effective method, credential stuffing involves automated attempts to log in using stolen or leaked credentials. SaaS applications, which often lack robust account lockout policies, are prime targets for this type of attack.
SOCRadar’s Dark Web Monitoring alerts organizations to potential threats by tracking mentions of their assets on the dark web, crucial for preempting identity-based attacks stemming from data breaches.
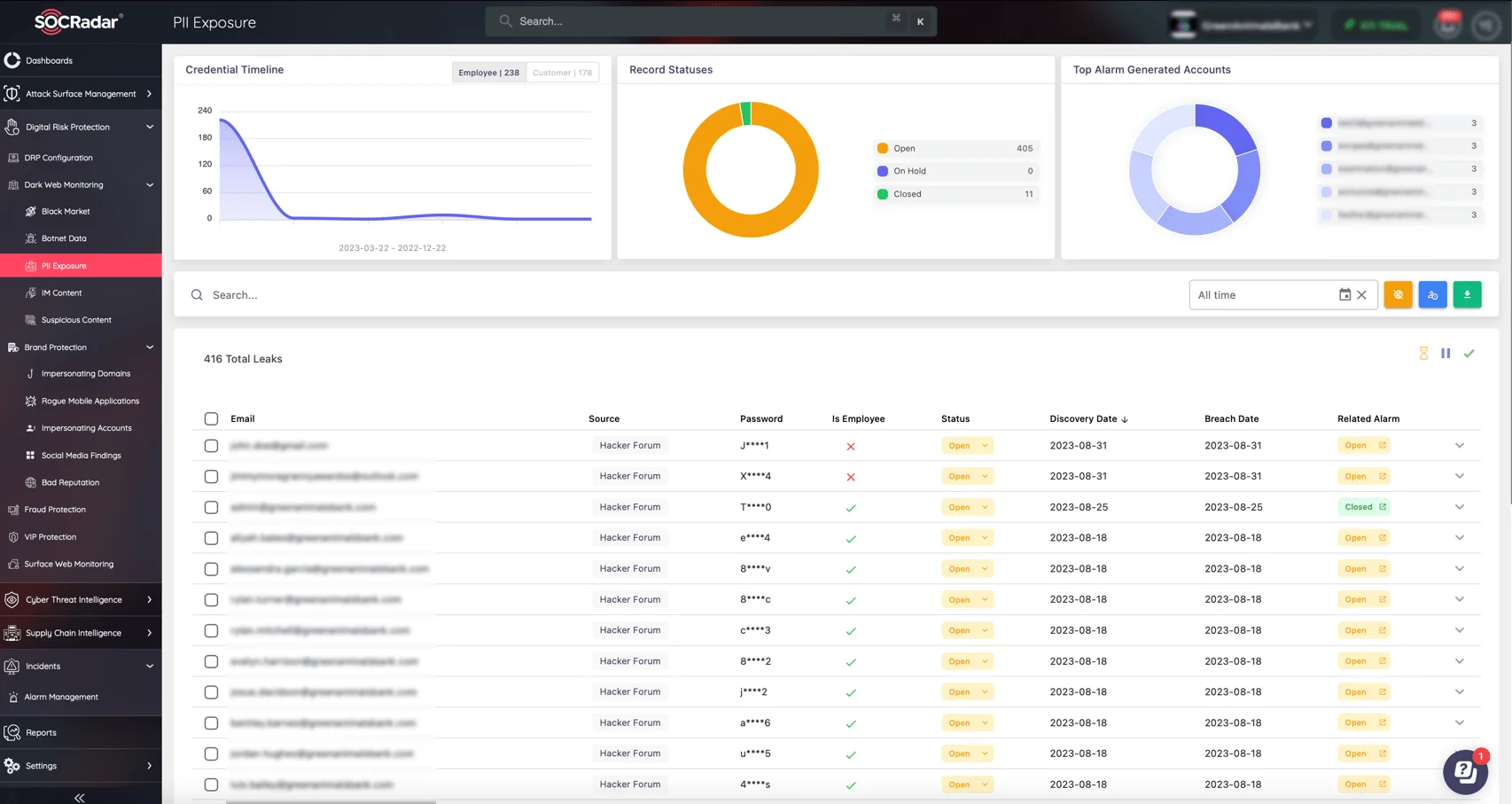
Monitor PII Exposure via SOCRadar’s Dark Web Monitoring
Other Notable Techniques Across the Matrix
- API Key Theft: Found under the Execution and Credential Access categories, this technique involves the unauthorized extraction of API keys, which can provide attackers with extensive access to SaaS platforms and data, often bypassing regular user authentication mechanisms.
- Client-side App Spoofing: Listed under Execution and Defense Evasion, this method involves creating malicious versions of legitimate applications or injecting malicious code into legitimate apps. This allows attackers to evade detection while executing malicious activities within the compromised environment.
- Device Code Phishing: Similar to consent phishing, this involves tricking users into authorizing a device that the attacker controls. It’s particularly deceptive because it mimics legitimate authentication workflows, thereby gaining credentials or tokens without raising alarms.
- In-app Phishing: Under Lateral Movement, this technique uses the compromised application itself to launch further phishing attacks against other users within the organization. It is particularly dangerous because it appears to come from a trusted source within the same application environment.
- Shadow Workflows: Highlighted in Execution and Exfiltration, this involves creating unauthorized automation workflows within SaaS applications that execute malicious actions or exfiltrate data seamlessly. Because they leverage legitimate functionality, they are hard to detect and can be very persistent.
These attack techniques highlight the need for organizations to extend their cybersecurity frameworks to cover all software and services in use, not just those formally recognized and managed by IT. Proper education on the risks associated with Shadow SaaS, combined with robust monitoring and response strategies, can mitigate these threats and safeguard organizational assets.
Best Practices to Counter SaaS Attacks
To effectively manage the risks associated with both sanctioned and Shadow SaaS, organizations need to implement robust security measures and policies.
Here are several best practices that can help secure the SaaS ecosystem:
Visibility and Asset Management: Achieving comprehensive visibility over all SaaS applications used across an organization is critical. IT departments should deploy tools to detect and catalog all SaaS products, whether officially approved or not. Techniques might include network monitoring that identifies SaaS traffic patterns and integrating with identity providers that record every authentication event.
SOCRadar’s Brand Protection module monitors for impersonations and brand abuse across various platforms, crucial for identifying and mitigating risks from impersonator apps that could target users with your organization’s name, enhancing overall security against identity-based threats.
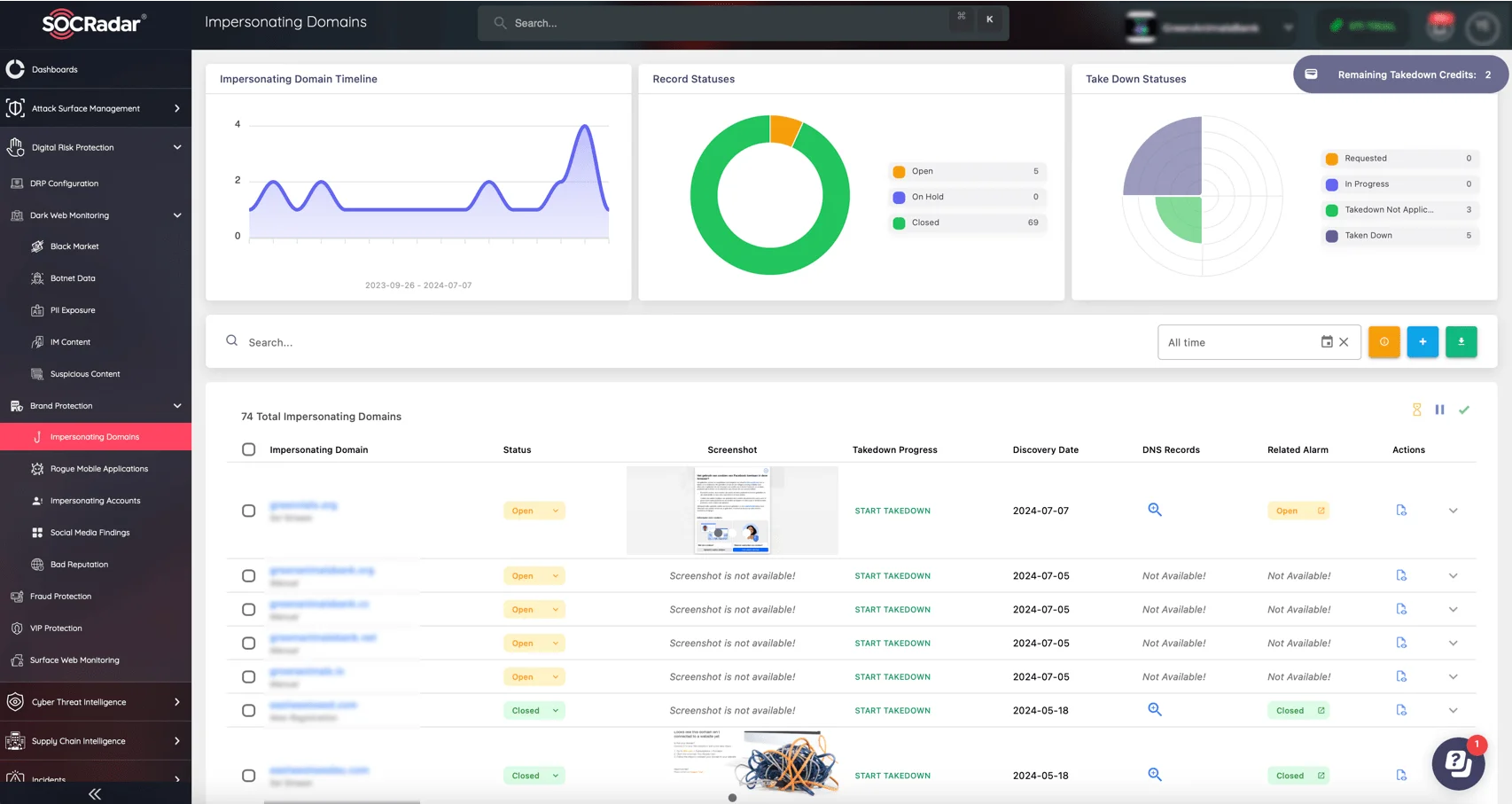
Impersonating domains, SOCRadar’s Brand Protection module
Access and Identity Management: Strong identity and access management (IAM) policies are essential. This entails enforcing Multi-Factor Authentication (MFA) across all SaaS applications, implementing least privilege access, and regularly updating access permissions. For Shadow SaaS, creating a straightforward process for employees to request and receive approval for new tools can reduce the tendency to circumvent IT protocols.
Organizations must recognize the severity of identity attacks and adapt accordingly by:
- Developing an identity threat model to pinpoint potential weaknesses.
- Analyzing security telemetry to identify defensive gaps.
- Instituting both proactive and reactive security controls centered on identity management.
SOCRadar’s Identity & Access Intelligence module can significantly enhance visibility by providing detailed insights into compromised credentials and risky access patterns, crucial for identifying and mitigating unauthorized access early.
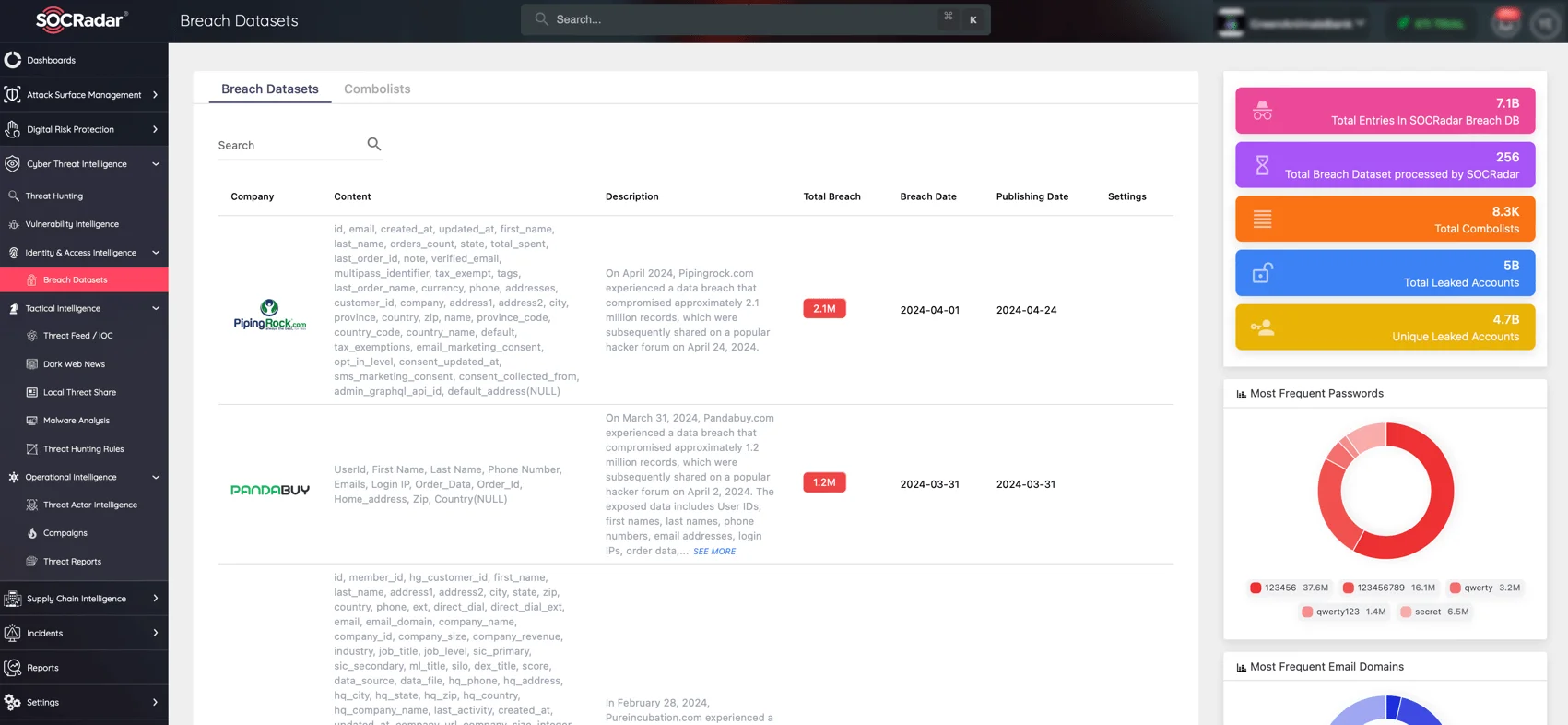
Breach Datasets on SOCRadar’s Identity & Access Intelligence module
Employee Training: Conducting regular training and awareness programs can substantially mitigate the risks linked to Shadow SaaS. Training should inform employees about the security dangers of unauthorized software and the correct procedures for technology adoption. Cybersecurity training should also cover specific SaaS attack scenarios to enhance threat recognition and response capabilities.
Incident Response and Anomaly Detection: It’s important to tailor incident response strategies to the unique challenges of SaaS platforms, integrating them into regular security monitoring frameworks and employing AI-driven anomaly detection to identify unusual patterns of access or potential data breaches. Rapid response plans are crucial for quickly addressing security incidents involving Shadow SaaS.
Secure Offboarding Procedures: Offboarding must include removing access to all SaaS applications to prevent ex-employees from retaining access to corporate data. Automating deprovisioning processes can ensure a thorough and timely revocation of access.
Legal and Compliance Measures: Legal frameworks should be updated to reflect the realities of Shadow SaaS by conducting regular audits and ensuring that all SaaS applications meet applicable regulatory standards, such as GDPR, HIPAA, or SOC 2. Legal teams should draft terms of use that discourage the adoption of unsanctioned applications and clarify their legal consequences.
Conclusion
Shadow SaaS, while appearing to be enhancing productivity and flexibility, introduces significant security vulnerabilities that can expose organizations to sophisticated SaaS attacks. By understanding the risks and implementing strategic defenses – from comprehensive visibility and robust access management to employee education and strong incident response – organizations can mitigate these threats. Embracing these best practices not only secures Shadow SaaS applications but also fortifies the overall cybersecurity posture, ensuring that innovation does not compromise security.




































