
Windows SmartScreen Vulnerability Exploited in DarkGate Malware Attacks, Patch CVE-2024-21412 Now
[Update] July 25, 2024: “Information Stealer Campaign Exploits the Windows SmartScreen Vulnerability (CVE-2024-21412)”
In January 2024, a new DarkGate malware campaign was discovered, which used a Windows Defender SmartScreen zero-day vulnerability to evade security measures and deploy fake installers.
The vulnerability in question is CVE-2024-21412, which recently received a patch during Microsoft’s February 2024 Patch Tuesday.
How Do Attackers Exploit the Windows Defender SmartScreen Vulnerability, CVE-2024-21412?
SmartScreen is an important Windows Defender security feature that warns users when they try to run suspicious, potentially malicious, downloaded files.
The CVE-2024-21412 (CVSS 8.1) vulnerability is classified as a Security Feature Bypass. It enables attackers to bypass Windows Defender SmartScreen’s security warnings with specially crafted files, allowing them to covertly infiltrate their victims and carry out further malicious acts.
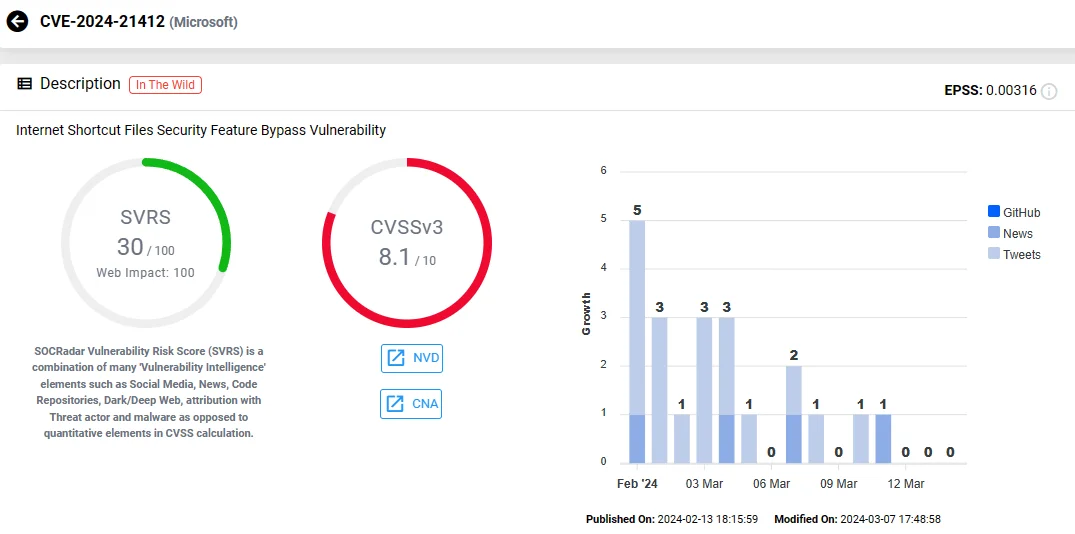
Vulnerability card of CVE-2024-21412 (SOCRadar Vulnerability Intelligence)
Attackers can take advantage of this vulnerability by creating a Windows internet shortcut (.URL) file that links to another shortcut file hosted on a remote SMB share. This action results in the automatic execution of the file located at the final destination.
Notably, CVE-2024-21412 is a patch bypass for another SmartScreen vulnerability, CVE-2023-36025 (CVSS: 8.8), which was initially patched by Microsoft during November 2023 Patch Tuesday.
Threat Actors Targeting CVE-2024-21412 and Details of DarkGate Malware
After Microsoft addressed CVE-2024-21412 in February 2024 Patch Tuesday, researchers revealed that Water Hydra (a.k.a. DarkCasino) had previously exploited it as a zero-day in attacks directed at foreign exchange traders. The exploitation of the vulnerability resulted in the deployment of the DarkMe Remote Access Trojan (RAT) on victims’ systems.
Now, DarkGate malware operators are also leveraging CVE-2024-21412 with the objective of infiltrating their targets while simultaneously disabling security warnings.
The DarkGate malware appeared in July 2023 as a successor to QakBot, shortly after PikaBot, and both were used in campaigns following QakBot’s takedown. You can find a timeline of these events, including the emergence of DarkGate, in a previous SOCRadar blog post detailing the events and operations of QakBot.
For further information on DarkGate visit our blog post: DarkGate Malware, Exploring Threats and Countermeasures
Explore the details and latest updates on the operation through our Cyber Threat Intelligence module’s Threat Actor/Malware page:
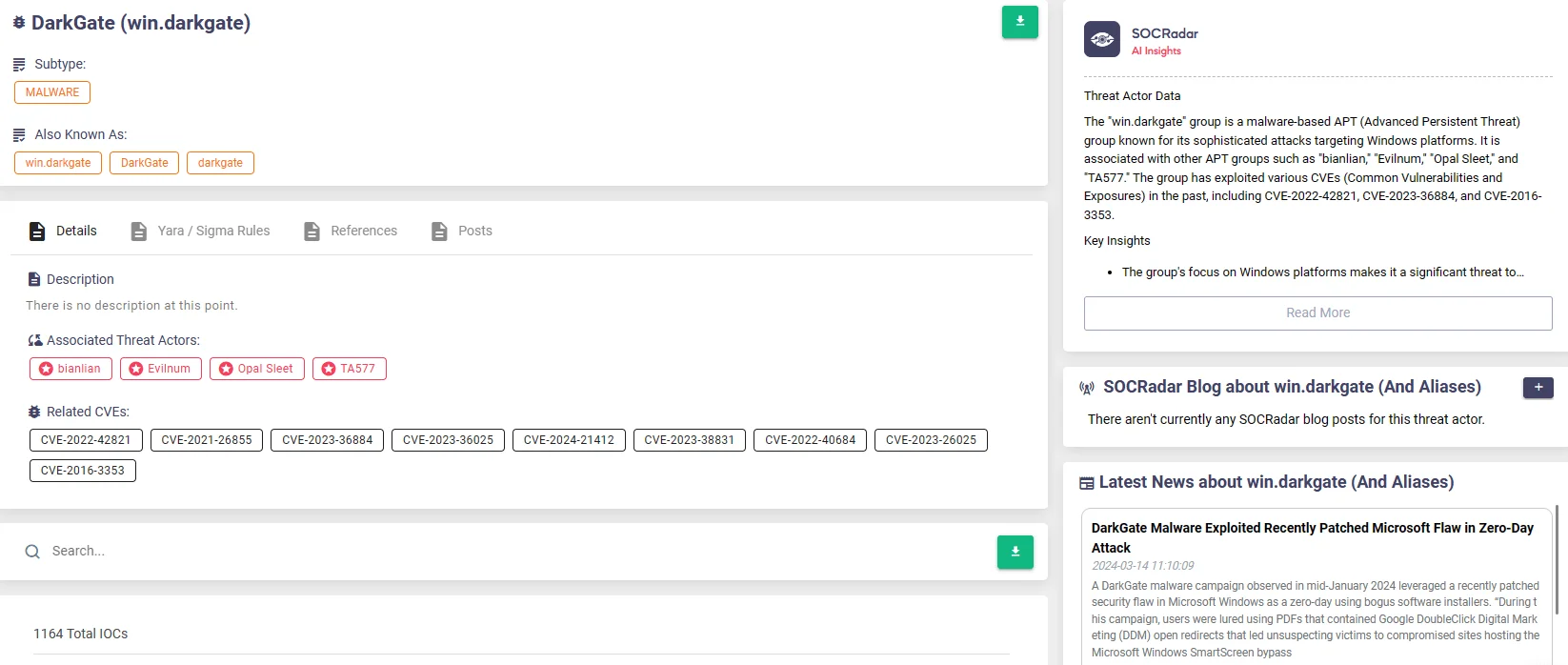
DarkGate Malware, SOCRadar Threat Actors/Malware page
The Attack Chain of DarkGate Malware
Operators initiate the attack by sending a phishing email containing a PDF attachment with links that leverage open redirects from Google DDM services, enabling them to bypass email security checks.
If attackers are successful in persuading the victim to click the link, the victims are directed to a compromised web server hosting an internet shortcut file (.URL). This file then links to a second shortcut file hosted on an attacker-controlled WebDAV server.
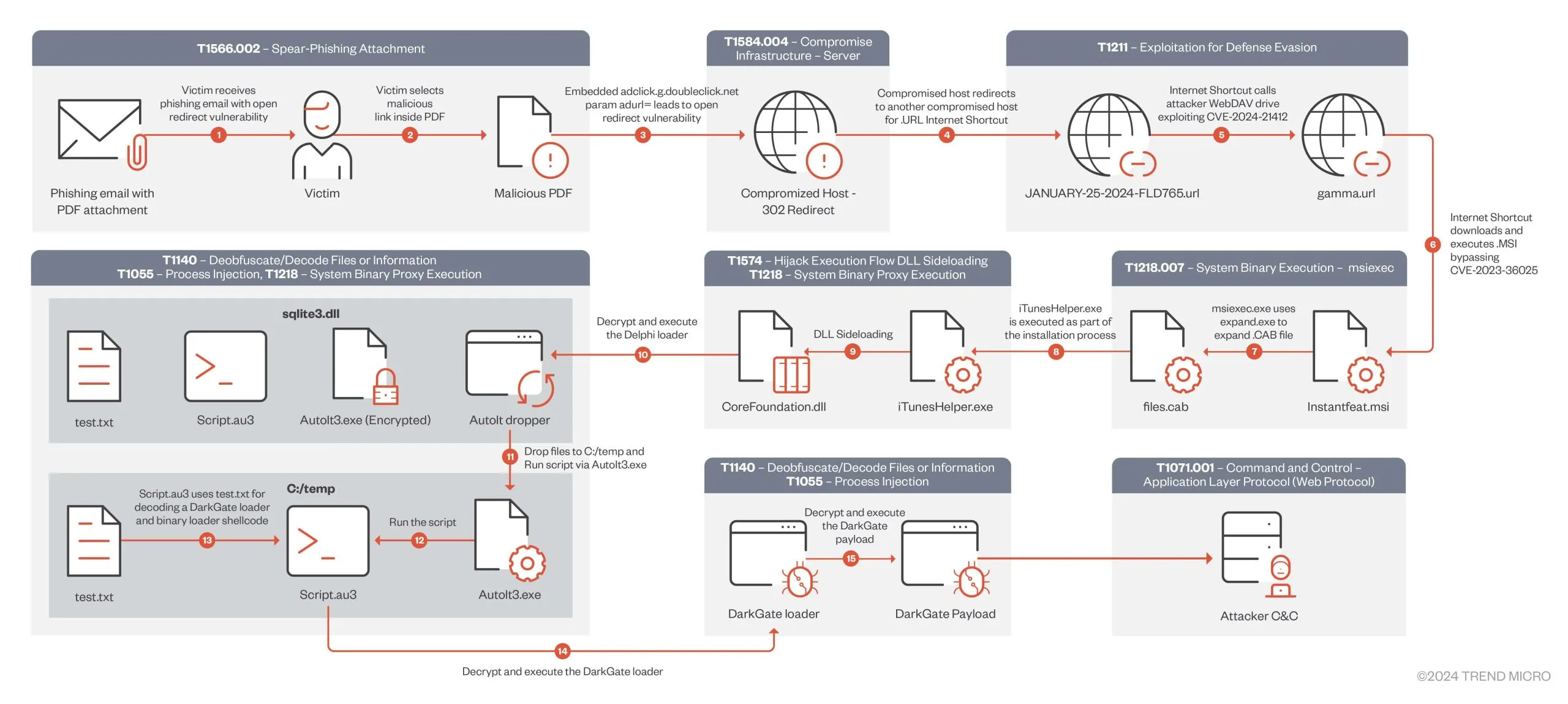
DarkGate Attack Chain (TrendMicro)
Exploiting the CVE-2024-21412 vulnerability, a Windows shortcut triggers the execution of a malicious MSI file, often disguised as legitimate software like NVIDIA, Apple iTunes, or Notion. Upon installation, a DLL sideloading flaw decrypts and launches the DarkGate malware, enabling data theft, additional payload deployment, keylogging, and real-time remote access for attackers.
Additionally, researchers have identified that this campaign utilizes DarkGate 6.1.7, which incorporates XOR-encrypted configuration, updated Command and Control (C2) values, and new configuration options to enhance attacks, enabling attackers to establish persistence and evade test environments more effectively.
Information Stealer Campaign Exploits the Windows SmartScreen Vulnerability (CVE-2024-21412)
Fortinet recently detailed a stealer campaign that distributed multiple files that exploited the CVE-2024-21412 zero-day to deliver malicious payloads.
According to the company’s analysis, several threat actors aside from Water Hydra, like Lumma Stealer, and Meduza Stealer have exploited the vulnerability over the last year.
In the stealer campaign, researchers discovered that the threat actors use different injectors to avoid detection and use different PDF files to target specific regions, such as North America, Spain, and Thailand.
How Do Attackers Exploit CVE-2024-21412?
Attackers lure victims into clicking a crafted link to a URL file, designed to download an LNK file.
This LNK file downloads an executable containing an HTA script. Once executed, the script decodes and decrypts PowerShell code to retrieve final URLs, decoy PDF files, and a malicious shell code injector.
These files aim to inject the final stealer into legitimate processes, initiating malicious activities and sending the stolen data back to a Command and Control (C2) server.
Here’s a summary of the attack chain:
- Initial Access
Attackers create a malicious link to a remote server to find a URL file. This file employs the “forfiles” command to invoke PowerShell and execute “mshta” to fetch an execution file from “hxxps://21centuryart.com.”
These LNK files download executables containing an HTA script that minimizes the window and hides the taskbar to execute further malicious code.
- Shell Code Injector
Two types of injectors were identified in the campaign.
The first uses an image file to obtain shell code, which downloads a JPG file from “hxxps://i.imghippo[.]com/files/0hVAM1719847927[.]png” and decodes it using the Windows API “GdipBitmapGetPixel” to execute the shell code.
The shell code accesses APIs from a CRC32 hash, creates folders, and drops files in the “%TEMP%” directory. The second injector decrypts its code and uses Windows API functions to inject the shell code.
- The Use of Stealers
The attack employs Meduza Stealer version 2.9 and an ACR stealer loaded from HijackLoader. The ACR stealer hides its C2 on the Steam community website using a Dead Drop Resolver (DDR) technique.
By decoding the C2 from Steam, the stealer maintains communication with its server.
The ACR Stealer targets local text files, browsers, crypto wallets, messengers, FTP clients, email clients, VPN services, password managers, numerous Chrome extensions, and other applications.
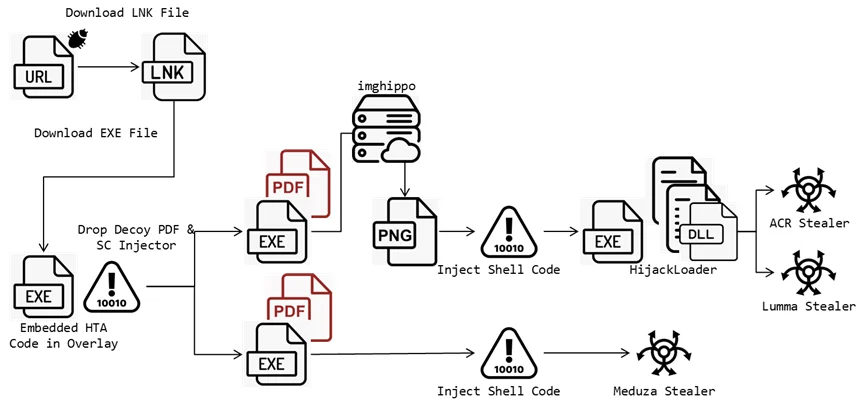
The full attack chain used in the campaign (Fortinet)
To see the full list of targets and Indicators of Compromise (IOCs) related to the campaign, visit the official research blog.
Harness SOCRadar’s Capabilities to Stay Proactive Against Exploitation
Stay proactive in mitigating the risk of malware attacks and vulnerability exploitation. Monitor your digital assets and stay informed about the evolving vulnerability landscape to stay one step ahead of emerging threats.
SOCRadar’s Vulnerability Intelligence offers comprehensive details on identified vulnerabilities, including the latest updates, available exploits, and vulnerability lifecycles. Moreover, the Attack Surface Management module sends timely alerts for any security issues, including the emergence of vulnerabilities across your assets, facilitating a better patch management strategy.
CVE and exploit trends, SOCRadar’s Vulnerability Intelligence
Indicators of Compromise (IoCs) for the DarkGate Campaign Targeting SmartScreen
An extensive list of Indicators of Compromise (IoCs) related to the DarkGate campaign exploiting the Windows Defender SmartScreen vulnerability, CVE-2024-21412, is available here.




































