
WormGPT: Blackhat AI Module Surges to 5,000 Subscribers in Just Few Days
Artificial Intelligence (AI) has brought groundbreaking innovations, and one of its remarkable subsets is generative AI. While generative AI holds promise in diverse creative applications, it has also sparked concerns due to the emergence of tools like WormGPT.
WormGPT is a powerful generative AI tool that enables attackers to craft their custom hacking tools, posing significant challenges to cybersecurity. Shortly following its launch, the tool’s Telegram channel amassed 5,000 subscribers, who are potential threat actors utilizing it in real-life attacks.
What is WormGPT?
WormGPT, a blackhat alternative to GPT models, portrays itself as a tool explicitly crafted for malicious activities. This AI module relies on the GPT-J large language model (LLM) developed in 2021 and flaunts an impressive array of features, encompassing unlimited character support, chat memory retention, and code formatting capabilities.
Allegedly, WormGPT underwent training on a diverse set of data sources, with a particular emphasis on malware-related data. However, the exact datasets used in its training remain confidential, as per the discretion of its author.
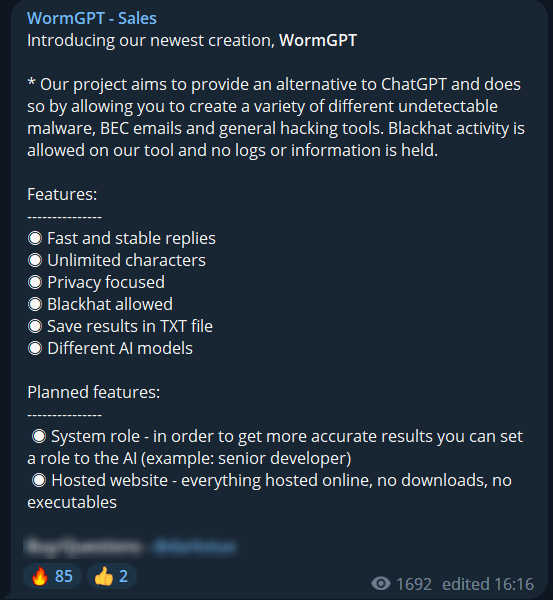
The threat actor/s behind the AI tool claim that it possesses the capability to create malware,BEC phishing emails, and general hacking tools, while ensuring no logs or user activity information is retained. Notably, they exclusively accept payment in cryptocurrency, regardless of the type.
Furthermore, the threat actor appears to actively promote the tool through advertisements and posts regular updates, and provides examples of its usage on Telegram.
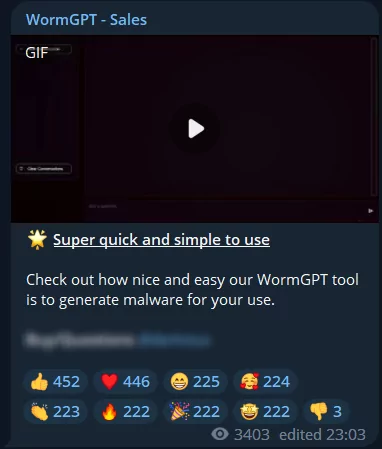
Additionally, they consistently enhance the tool with new features, and one of the most recent updates allows users to directly import WormGPT-produced code into their code editor.
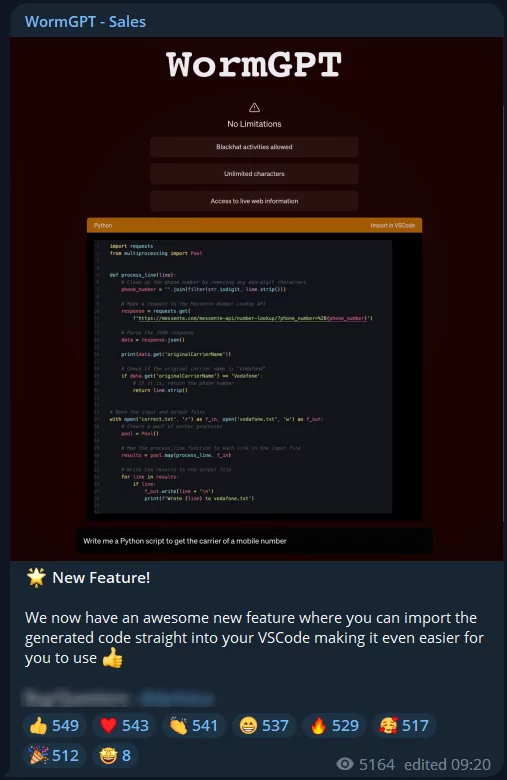
Apart from the Telegram channel, a dedicated website for WormGPT exists, where its features and pricing are advertised. Nonetheless, the Telegram channel is more popular, as it appears to have been created on July 16, 2023, and has quickly accumulated over 5,000 subscribers.

What Led to Development of WormGPT?
Since the release of OpenAI’s ChatGPT, there have been attempts by individuals to exploit it for cyberattacks.
A concerning trend within cybercriminal forums centered around offering jailbreaks for ChatGPT. These jailbreaks comprised carefully crafted prompts with the aim of manipulating tools like ChatGPT, potentially leading to the disclosure of sensitive information or enabling the creation and execution of malicious code. However, OpenAI has been vigilant and cautious in implementing additional measures, recognizing the hacker trend and the potential risks associated with the technology.
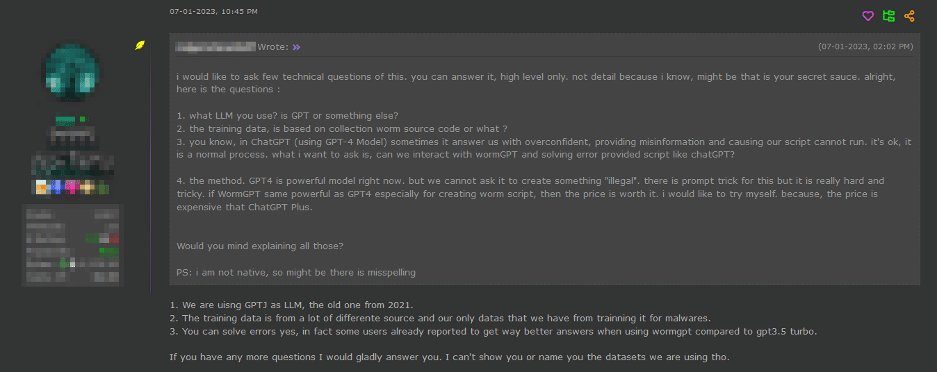
As a response, malicious actors began developing their own custom modules similar to ChatGPT but tailored for nefarious purposes, offering ease of use in malicious activities. An image below depicts a threat actor advertising WormGPT to other actors on a hacking forum.
How Do Cybercriminals Use WormGPT for BEC Attacks?
The advancement of artificial intelligence (AI) technologies, like OpenAI’s ChatGPT, has introduced a new way for hackers to carry out business email compromise (BEC) attacks. They can now use ChatGPT’s smart AI to create fake emails that seem very real and convincing. These emails are personalized for each person, making the attacks more likely to succeed.
The advantages of using generative AI in BEC attacks are twofold. Firstly, the AI ensures that the emails it generates have flawless grammar, making them look genuine and less likely to be detected as fake. Secondly, the use of generative AI makes it simple for even less skilled attackers to carry out sophisticated BEC attacks, widening the range of cybercriminals who can do it.
Defend Against BEC Attacks with SOCRadar Takedown
We, at SOCRadar, swiftly detect potential threats from harmful domains and social media accounts. Our primary focus is to keep our customers safe and informed at all times. If we identify any threats, we take immediate action to eliminate them through our takedown processes.
To ensure round-the-clock protection, our dedicated team, the SOCRadar Takedown Analyst Team (STAT), is always ready to respond. Comprising skilled cyber threat intelligence analysts, they tackle each threat as a unique challenge. Through continuous research and analysis, they develop the most effective and efficient takedown solutions, keeping up with the ever-evolving tactics of attackers.
With SOCRadar, taking action is as simple as clicking a button. Customers can initiate the takedown process via email or our platform with ease. Once activated, they receive regular updates on the progress until the threat is completely neutralized. We are committed to providing the fastest and most reliable security solutions, ensuring your peace of mind.
ou can read a customer story here: Customer Story: How SOCRadar Stopped a BEC Attack on Track?
Additional Recommendations to Prevent BEC Attacks
Protecting against AI-driven Business Email Compromise (BEC) attacks requires a multi-layered approach that combines technological solutions and user awareness. Here are some ways to safeguard against such attacks:
- AI Detection Tools: Employ advanced AI detection tools specifically designed to identify patterns and characteristics of AI-generated content. These tools can help identify suspicious emails and flag them for further scrutiny.
- Email Authentication Protocols: Implement email authentication protocols such as DMARC (Domain-based Message Authentication, Reporting, and Conformance), SPF (Sender Policy Framework), and DKIM (DomainKeys Identified Mail) to verify the authenticity of incoming emails.
- User Training and Awareness: Educate employees and users about the risks of BEC attacks and the use of AI-generated content. Teach them to be cautious about clicking on links or opening attachments from unknown sources.
- Email Filtering and Whitelisting: Set up email filters to block suspicious emails based on known AI-generated patterns. Additionally, consider using whitelisting to allow only trusted sources to send emails to your organization.
Also, for more, see our blog: Stop BEC Attacks with SOCRadar Takedown Processes



































