
What are Botnets: ‘Digital Zombie Herds’
The development of internet technologies has opened the door to a new area where malicious people can make some of their bad wishes come true. Since the second half of the 20th century, threat actors have been trying to find new ways to accomplish their goals, and they have succeeded many times. In today’s blog post we will try to explain such a concept, “botnets“.
One of the ways threat actors have found and used many times to carry out various tasks is called botnets: the abbreviation for robot network. Botnets consist of numerous enslaved computers awaiting commands from the master, the threat actor.
Enslaved computers are sometimes called zombies or bots. It performs various malicious tasks such as stealing personal information or sending spam emails to the victim’s connections on any command from the master.
Botnets Don’t Have to be “Bad Guys”
Even though botnets are mostly used by threat actors, they do not necessarily have to be malicious. In Blockchain technology, a blockchain is technically a non-malicious botnet where the users volunteer and add their system to the chain of servers. The user’s system, called a node, is used to carry out blockchain transactions; in return, certain rewards are granted to the user.
According to statistics, there are botnets with more than millions of enslaved computers. For example, a popular botnet named Conficker had over 10 million infected devices. Some of these botnets are rented out by cybercriminals for a variety of purposes.
Having millions of zombies in their armies does not keep cybercriminals away from carrying out attacks with devastating consequences. Some example attacks are DDoS attacks, phishing attacks with spam email campaigns, and InfoStealer attacks to collect information.
Additional use cases for botnets include generating fake website traffic for financial advertising earnings, and web crawling and mass crypto mining to find exposed RDP servers or IoT devices. That’s why we’ve come across many vendors selling botnet-related services in underground markets. Botnets are good business for bad actors with financial gain.
Threat actors may choose to sell the stolen data collected from the InfoStealer attacks on the Dark Web marketplaces which may allow less tech-savvy actors to perform less sophisticated attacks.
How Did My Laptop Become a Zombie?
For a botnet to be created, the threat actor first needs to establish an effective infection vector. One cannot create a herd without enough zombies. Common infection vectors of viruses that turn a system into a slave are phishing, malicious advertising, and malicious emails or SMS.
After enough systems are infected, the threat actor, also called the bot herder, gives orders through the C2 (Command and Control) servers, activating the botnet. An activated botnet can carry out automated tasks like info stealing or crypto mining and active tasks like DDoS or Brute Force attacks ordered by the threat actor.
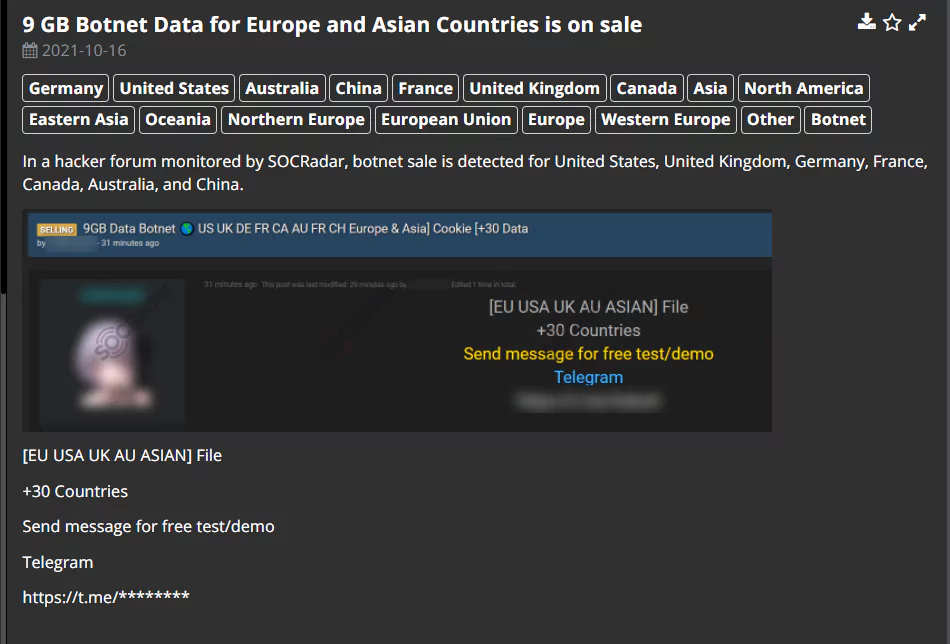
One of the best practices to help companies deal with botnet threats is data feeds. SOCRadar’s ThreatFusion crawls through the relevant sources on the web to discover malicious IPs, URLs, and hashes used by botnet command and control servers.
Example Notorious Botnets
Mirai
Only targeting Linux devices, the Mirai malware was first discovered in 2016. Devices in the Mirai botnet are known to be trying to access IoT devices with brute force attacks, and since 2016, the botnet is believed to be responsible for several DDoS attacks. An example DDoS attack perpetrated by the Mirai botnet is on krebsonsecurity.com, which had 620 Gbit attack volume.
MyKings
Also known as Smominru or DarkCloud, MyKings botnet is one of the most known botnets among cybercriminals. After five years of its debut, the botnet is still active and making huge amounts of money through crypto mining. Analysts at Kaspersky state that MyKings botnet is actively infecting around 4700 devices per day, and the total number of infected devices is above 90.000.
FreakOut
One of the newer botnets, The FreakOut botnet came into the scene in late 2020. Researchers at CheckPoint say that the malware behind FreakOut mainly targets devices with TerraMaster Operating System (TOS), Zend PHP framework, and Liferay Portal. Threat actors behind FreakOut primarily use CVE exploitations to infect a device.
Why is my Laptop Slow?
There are several indicators of whether your device is infected by botnet malware and is a part of a botnet. Some of these indicators are:
- Sudden or general slowness and lag while using the internet
- Unknown ads or pop-ups while surfing on the internet
- Unstable computer performance
- Unknown processes in the Task Manager
- Abnormalities in the CPU or RAM usage
- Unknown changes in your device
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































