Top 5 Free Attack Surface Management Tools
Attack surface management is the continual identification, monitoring, assessment, prioritizing, and remediation of attack vectors within an organization’s IT infrastructure.
What is Attack Surface Management?
While similar in nature to asset discovery or asset management, frequently seen in IT hygiene solutions, the primary distinction in attack surface management is that it addresses threat detection and vulnerability management from the attacker’s viewpoint. Consequently, the company is compelled to identify and assess the risk posed by recognized assets and unknown and rogue components.
Cybersecurity companies continue to develop new tools and features to help organizations manage their attack surface. Let’s look at these most well-known Attack Surface Management Tools on the market that adapt to threat actors’ advanced techniques and tactics.
A quick note: Keep in mind that all of these tools have “free” versions, but they all have their “limitations.” Contact vendors to take advantage of all the features and get advanced protection.
Top 5 Free Attack Surface Management Tools
1- Rapid7 InsightVM
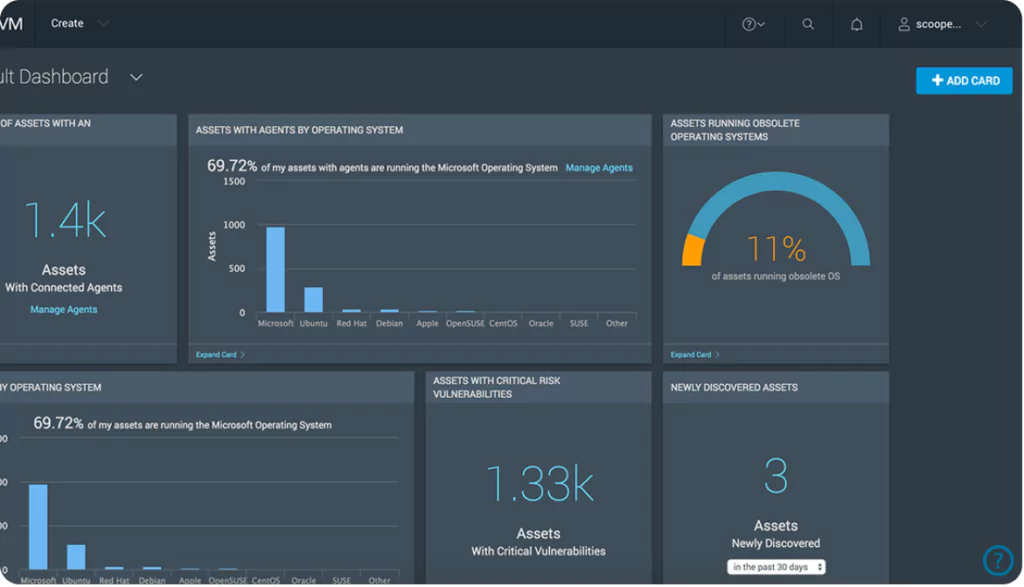
With its prospective features and extensive analytics capabilities, InsightVM tops the list. Launched in 2015, the Rapid7 Insight platform contains an exploit KB (knowledge base), vulnerability research, internet-wide scanning data, global attacker activity patterns, real-time reporting, and exposure analytics.
It provides a highly scalable, accessible, and efficient method for collecting vulnerability data and transforming it into actionable insights.
Rapid7 InsightVM resembles vulnerability management rather than a monitor for attack surface. In addition to virtual and cloud stacks, network devices and endpoints are scanned. This cloud-based application is capable of scanning distant locations for external endpoints.
It contains Project Sonar, which gathers data loss event alerts and other security-related data from several firms to expand its capabilities. This information may be used to establish a third-party risk evaluation for a vulnerability scanner.
2- SOCRadar AttackMapper
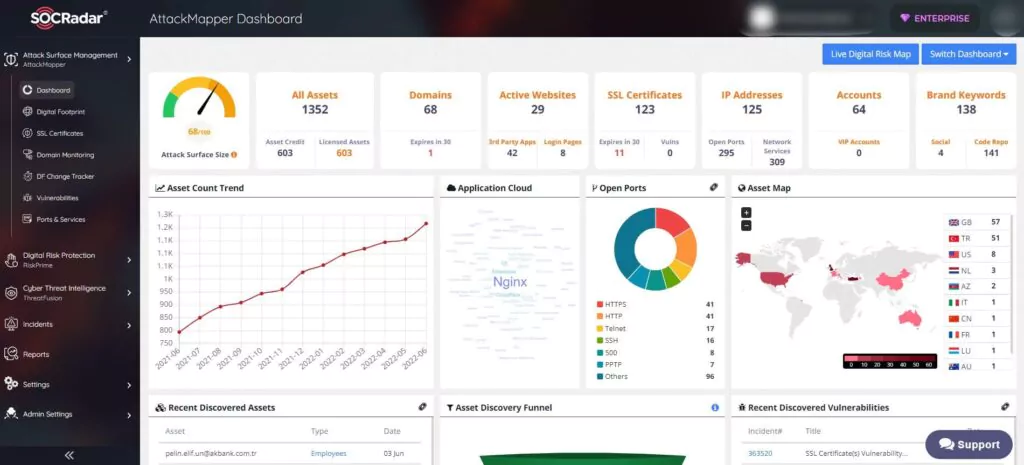
AttackMapper provides greater visibility and context on the severity of unknown external-facing digital assets with automation. AttackMapper gives security teams direct insight into all internet-facing technical assets in operation, as well as assets ascribed to IP, DNS, Domain, and cryptographic infrastructure, using the powerful internet-wide monitoring algorithms of SOCRadar.
3- CyCognito Attack Surface Management
CyCognito is a SaaS platform for the management of external attack surfaces. It automates and executes offensive strategies to test and protect businesses. The SaaS application has five phases of operation: Mapping Business-Asset Relationships, Defining Business Context, Automated Security Testing, Prioritizing Risks, and Accelerating Remediation.

It maps your external attack surface using natural language processing, machine learning, and graph data models. This displays the links between your company assets and cloud environments, joint ventures, and acquired organizations. Using iterative analysis, it automatically identifies and assigns attack surface assets.
Automated security testing will discover vulnerabilities and show all endpoints regularly used by hackers to target your IT resources.
The solution provides complete insight into your extended IT stack and identifies the top 10 security flaws that account for 90% of your threats. After prioritizing risks, it offers practical advice and leverages information to aid your IT personnel. It also provides workflow connectors with common IT technologies, like CMDBs, SIEMs, ITSM, and other tools.
4- Bugcrowd Asset Inventory
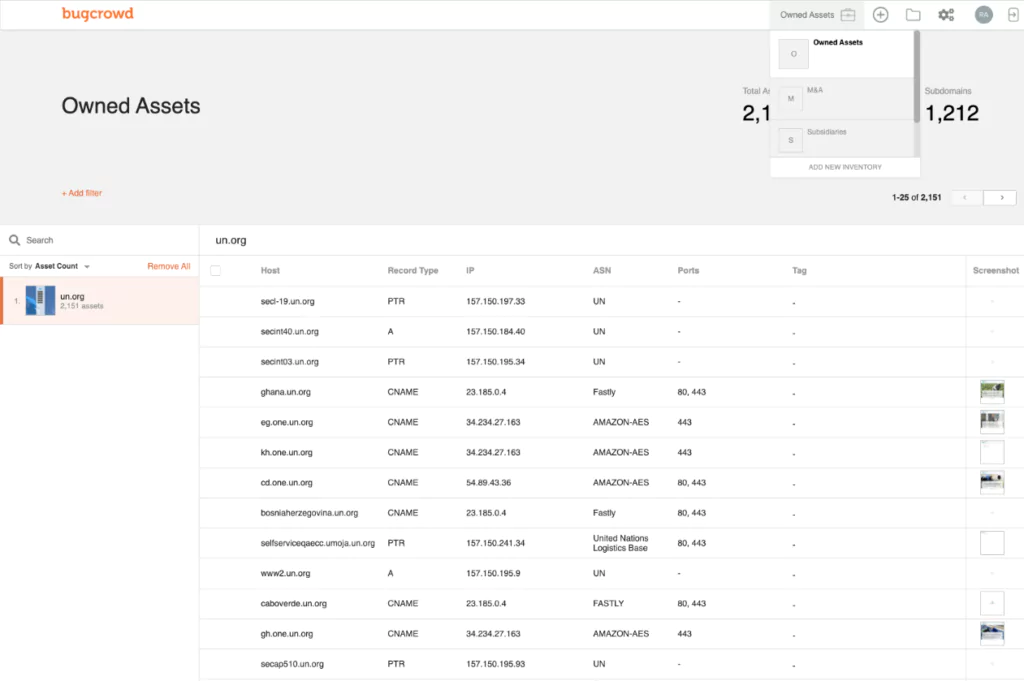
This is a program built by white-hat hackers. As a pen-testing system, it crawls across connected software packages to find the client’s software and services. This system links explicitly to all APIs and microservices that provide plug-in services for Web page functionality.
A third of all assaults, according to Bugcrowd, enter a firm via software and services that the IT staff is unaware of. You cannot secure systems that you are unaware of using. The system then monitors the newly-identified assets and notifies the customer if it finds any security threats.
Customers that want a customized service may commission human-based system searches. This is an actual penetration test since Bugcrowd places a bounty on your company’s systems and encourages the world’s top white hat hackers to break in, rewarding the first hacker for doing so. The name of this service is Asset Risk.
5- ImmuniWeb Discovery
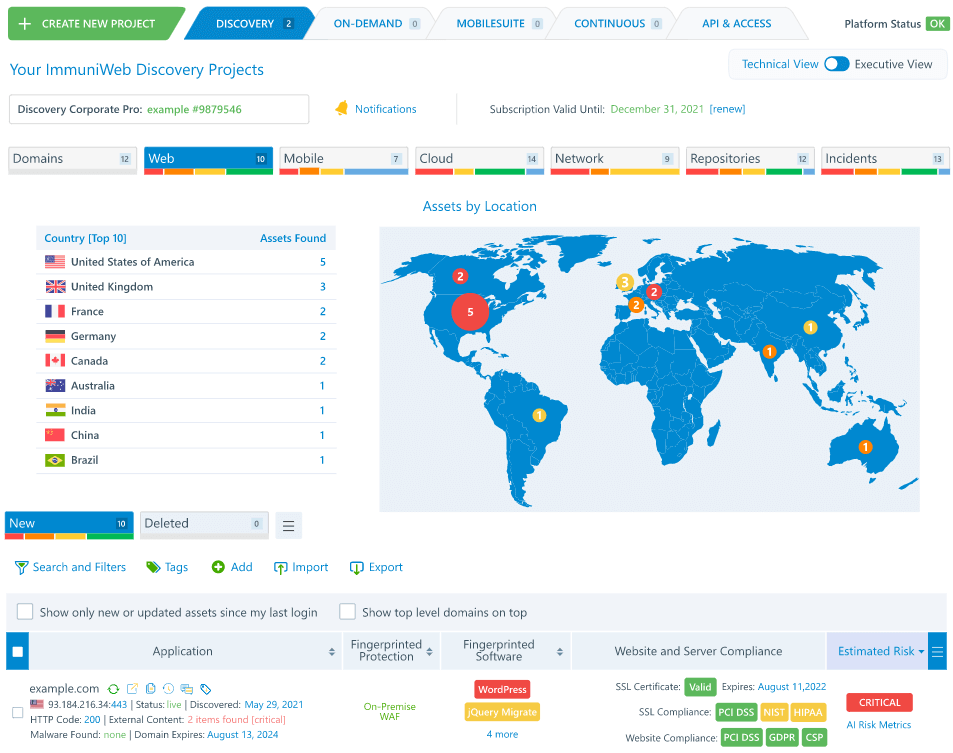
ImmuniWeb Discovery comprises many security services, including a vulnerability scanner and an attack surface monitor. This solution identifies all software assets on-premises and in the cloud. It may use APIs to locate the hosts of the code. It also offers a solution for managing vendor risk by monitoring any leaks or security incidents they suffer.