
SOCRadar’s Free IOC Search & Enrichment Service is Now Available
IOCs are a vital component of the threat hunting process, essential to detect and isolate advanced cyber threats. As a critical operational component of proactive security, identifying IOCs is functional to prevent possible intrusions and a procedure requiring repetitive tasks.
While exploring cyber intrusions, one of SOC teams‘ main challenges is checking various sources to get information about the IOCs. Several IOC forms, including IPs, URLs, hash values, malicious domains, etc., can be found in various OSINT feeds.
Time matters more, especially when defenders are competing against newly emerged threats.
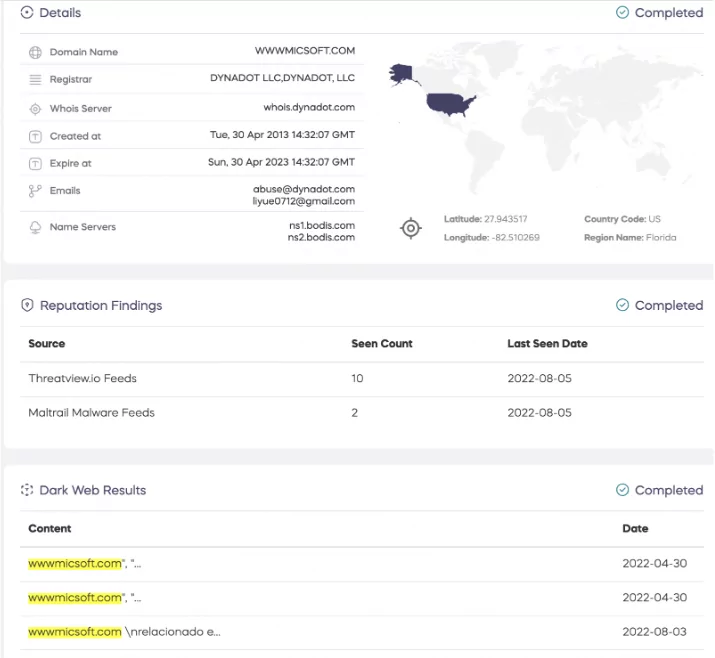
This is why SOCRadar releases IOC Radar, a new feature that helps SOC teams collect details of IOCs more effectively and rapidly. Instead of searching several threat intelligence sources, security experts can search IOCs in a single centralized platform.
IOC Radar can cover the open-source intelligence platforms, deep/dark web, GitHub repositories, and Telegram channels. Information from these sources will also be presented if any information is detected regarding the searched IOC.
After a few updates, IOC Radar will be more useful in getting meaningful outputs indicating the relations between threat actors and IOCs, such as the IPs used by certain threat actors. SOCRadar users will also do bulk searches with IOC Radar. Even searches for dozens of IPs can be found on one screen.
Threat intelligence certainly does not contribute to cyber defense when it is not actionable. IOC Radar enables SOC teams for effective IOC enrichment to correlate IOCs with your digital assets and known malicious indicators for more comprehensive intelligence




































