
Microsoft’s July 2023 Patch Tuesday Fixes Five Zero-Days, Nine Critical Vulnerabilities
Microsoft has released the July 2023 Patch Tuesday update, which includes 130 security vulnerabilities and two advisories. While nine of the listed vulnerabilities are critical, there are five zero-day vulnerabilities actively exploited.
July’s Patch Tuesday addressed the following vulnerability types:
- 37 Remote Code Execution Vulnerabilities
- 33 Elevation of Privilege (EoP) Vulnerabilities
- 22 Denial-of-Service (DoS) Vulnerabilities
- 19 Information Disclosure Vulnerabilities
- 12 Security Feature Bypass Vulnerabilities
- 5 Spoofing Vulnerabilities
- 2 Cross-Site Scripting (XSS) Vulnerabilities
Five Zero-Day Vulnerabilities Actively Exploited
CVE-2023-32046 (CVSS Score: 7.8, High): It is a privilege elevation vulnerability in Windows MSHTML that allows an attacker to gain the rights of the user running the vulnerable application by opening a specially crafted file via email or malicious websites.
CVE-2023-32049 (CVSS Score: 8.8, High): Attackers exploited this Security Feature Bypass vulnerability in Windows SmartScreen to prevent the display of the Open File – Security Warning prompt when downloading and opening files from the Internet.
CVE-2023-36874 (CVSS Score: 7.8, High): The vulnerability in Windows Error Reporting Service allows attackers to gain admin privileges on a device. According to Microsoft, an attacker must have local access to the targeted machine and restricted privileges of default users for successful exploitation.
CVE-2023-35311 (CVSS Score: 8.8, High): The zero-day vulnerability exists in Microsoft Outlook and allows users to bypass the Microsoft Outlook Security Notice while working in the preview pane.
CVE-2023-36884 (CVSS Score: 8.3, High): This zero-day vulnerability allows remote code execution via the use of specially crafted Microsoft Office documents. Microsoft has reported that the CVE-2023-36884 vulnerability has been used in the wild. However, user interaction with the malicious file is required for successful exploitation.
Although a patch for CVE-2023-36884 is not yet available, Microsoft has stated that Microsoft Defender for Office users are not at risk. Those who use the appropriate Attack Surface Reduction Rule to prevent the creation of child processes are also safe from exploitation.
Microsoft Guide: CVE-2023-36884 Exploited by Storm-0978 (RomCom)
Microsoft has released mitigation guidance for the vulnerability, which also includes information about related exploitation activity.
To summarize, Microsoft has identified a phishing campaign carried out by Storm-0978 (DEV-0978, RomCom) threat actor. The group’s most recent campaign, which began in June 2023, involved the exploitation of CVE-2023-36884 to deliver a RomCom-like backdoor.
Storm-0978 is the creator and distributor of the RomCom backdoor. In addition, the actor employs the Underground ransomware, which is related to the Industrial Spy ransomware, first seen in May 2022. Researchers have linked the group to the Cuba ransomware operation because their ransom notes in Industrial Spy operations mistakenly included email addresses, links, and TOX chat IDs related to the group.
According to reports, the threat actor is based out of Russia and is well-known for carrying out ransomware and extortion attacks, and intelligence-gathering operations based on credential theft.
Storm-0978 infiltrates organizations by using trojanized versions of legitimate software to install RomCom; previous targets have mainly included Ukrainian government and military organizations, and organizations in Europe and North America that may be involved in Ukrainian affairs. They target telecommunications, finance, and various other industries.
To learn more about Storm-0978, and see the mitigation methods for CVE-2023-36884, visit Microsoft’s security guidance.
Critical Vulnerabilities in Microsoft’s July 2023 Patch Tuesday
The nine vulnerabilities labeled as critical in the July Patch Tuesday consist of RCEs in:
- Microsoft SharePoint (CVE-2023-33160 and CVE-2023-33157)
- Windows Layer-2 Bridge Network Driver (CVE-2023-35315)
- Microsoft Message Queuing (CVE-2023-32057)
- Windows PGM (CVE-2023-35297)
- Windows Routing and Remote Access Service (RRAS) (CVE-2023-35367, CVE-2023-35366, CVE-2023-35365)
Additionally, a Security Feature Bypass Vulnerability in Windows Remote Desktop, identified as CVE-2023-35352 is critical.
The most critical of these vulnerabilities are those in the Windows RRAS and Microsoft Message Queuing (MSMQ), each with a CVSS score of 9.8.
CVE-2023-35365, CVE-2023-35366, CVE-2023-35367: These RCE vulnerabilities exist in RRAS, a service in Windows that can be used as a VPN gateway or router. An attacker must send crafted packets to a vulnerable server in order to exploit it. RRAS is not installed or configured by default, and users who have not enabled the feature are unaffected by these vulnerabilities.
CVE-2023-32057: An unauthenticated attacker can exploit this vulnerability remotely by sending malicious packets to a vulnerable MSMQ server. For exploitation to be possible, the MSMQ service must be enabled.
Apply the Official Patches
We strongly advise you to apply the patches as soon as possible to protect your environment and improve your security posture. For more information on the vulnerabilities mentioned in this update, see Microsoft’s July 2023 Release Note.
Enhance Patch Management with SOCRadar
SOCRadar’s Vulnerability Intelligence provides additional security protection by detecting and tracking potential security risks such as vulnerabilities.
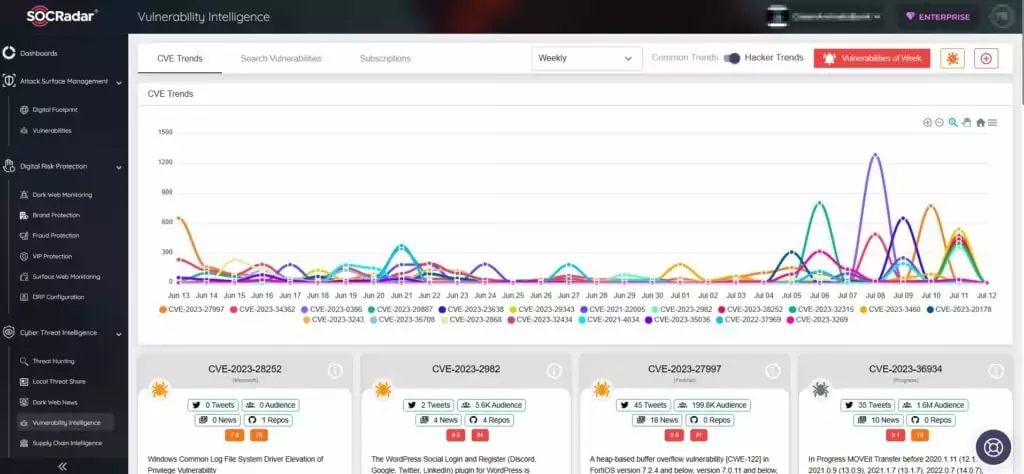
Furthermore, the SOCRadar XTI External Attack Surface Management (ASM) feature aids in the identification of your digital assets and alerts you to any emerging issues. The platform improves security measures and patch management by providing actionable insights.
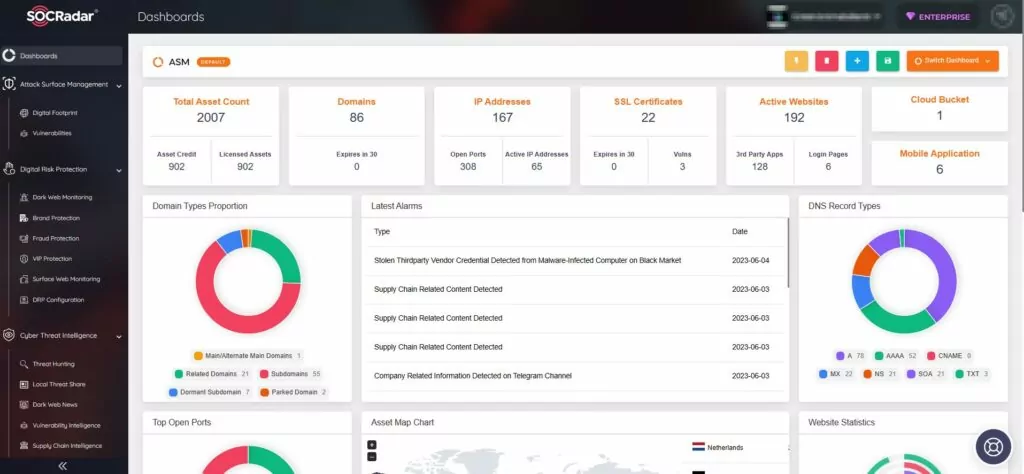
Sign up for a free edition of the SOCRadar platform to gain more knowledge and stay up to date on the latest vulnerabilities.



































