
Enhancing IoT Security with Cyber Threat Intelligence (CTI)
The Internet of Things (IoT) represents a significant technological advancement that is widely utilized in various aspects of our lives, including social, commercial, and economic domains. IoT enables the identification, location, and access of diverse objects through cost-effective sensors. It promises substantial improvements in human quality of life by enhancing productivity and comfort across numerous applications, ranging from education to smart cities and multiple industries. However, while IoT offers numerous benefits, it also poses significant challenges, particularly concerning privacy and security. Traditional IoT security measures are often inadequate, leading to increased vulnerability to cyber-attacks and dark web threats, which negatively impact smart applications within the IoT framework.
This article assesses the specific threats and risks associated with industrial IoT devices and discusses solutions that incorporate security strategies augmented by Cyber Threat Intelligence (CTI).
What is IoT? Why is It Important?
The Internet of Things (IoT) refers to a network of interconnected or ‘smart’ devices and systems. These devices are equipped with sensors that collect, connect, and exchange data through software and other technological systems. IoT devices and systems can be monitored and remotely controlled via the Internet.
Examples of IoT devices and systems include smart meters, thermostats, lamps, alarm systems, smoke detectors, door locks, and cameras. Sensors and RFID (Radio-Frequency Identification) tags connected to a port or base station enable remote management over the Internet.
Driven by innovations from the Industry 4.0 revolution, businesses are increasingly using interconnected devices and systems for various purposes, such as securing facilities, optimizing energy consumption, streamlining production and logistics, enhancing customer service, and maintaining machinery or vehicles.
An important cornerstone for smart devices was laid out by the Biden-Harris Administration on July 18, 2023. It announced a cybersecurity certification and labeling program to help make it easier to select smart devices that are less vulnerable to cyberattacks. The proposed “U.S. Cyber Trust Mark” program aims to raise the bar for cybersecurity in common devices, including smart refrigerators, smart microwaves, smart televisions, smart climate control systems, smart fitness trackers and more.
What Are IoT Future Trends?
Worldwide, IoT devices are expected to increase to over 29 billion by 2030. These devices are utilized across diverse industries and consumer markets. In 2020, the consumer segment accounted for approximately 60 percent of all IoT-connected devices, a proportion expected to remain stable over the next decade.
Major industries currently employing more than 100 million connected IoT devices include electricity, gas, steam, and air conditioning supply, water supply and waste management, retail and wholesale, transportation and warehousing, and public administration. By 2030, the number of IoT devices across all industry sectors is anticipated to surpass 8 billion, with over 1 billion IoT devices dedicated to autonomous vehicles, IT infrastructure, asset tracking and monitoring, and smart grids.
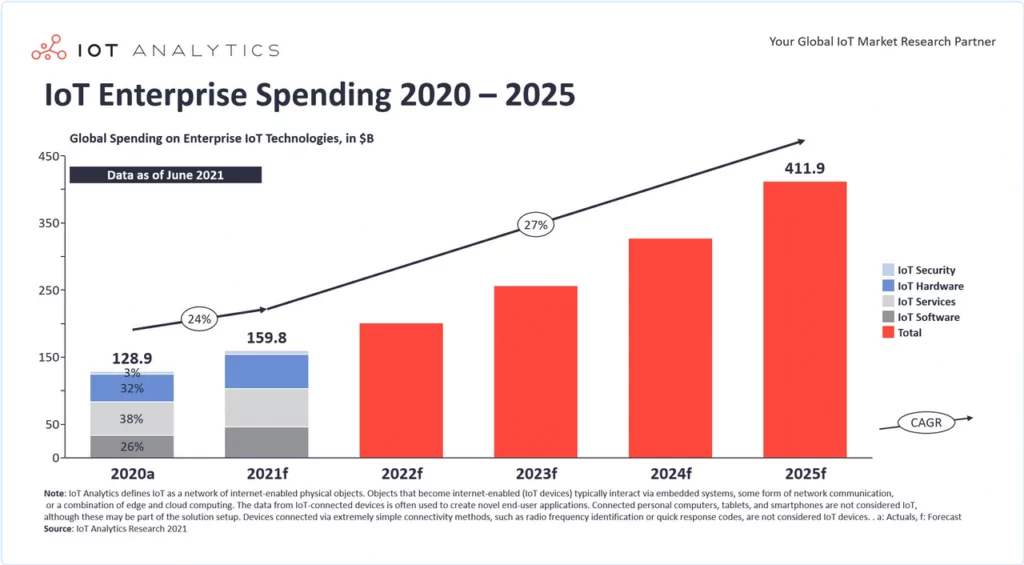
The Industrial IoT market is projected to reach a value of USD 276 billion in 2023 and USD 525.20 billion by 2028, growing at a CAGR (Compound Annual Growth Rate) of 13.73% from 2023 to 2028. This growth signifies a considerable increase in global revenue. In addition, another research predicts that IoT enterprise spending will exceed 400 billion dollars in 2025.
Why is IoT Device Security Crucial for Business Organizations?
The adoption of the Internet of Things (IoT) and Operational Technology (OT) devices has surged in recent years. While the increasing number of networked devices deployed on enterprise networks enhances the efficiency and visibility of an organization’s operations, it simultaneously introduces significant security risks. These risks expand an organization’s attack surface and potentially facilitate unauthorized access to sensitive data and critical systems.
IoT devices often lack robust security features by default, and long-lived OT devices are typically not designed with security as a priority, presenting risks when connected to the network. As organizations increasingly integrate these devices into their networks, it is crucial to balance their benefits with the associated risks to data confidentiality, integrity, and availability.
Each device deployed on a corporate network enlarges the organization’s digital attack surface due to potential coding flaws, access management issues, and security vulnerabilities. Addressing IoT security is vital to mitigate the risks these devices pose to the organization and to secure potential weak points.
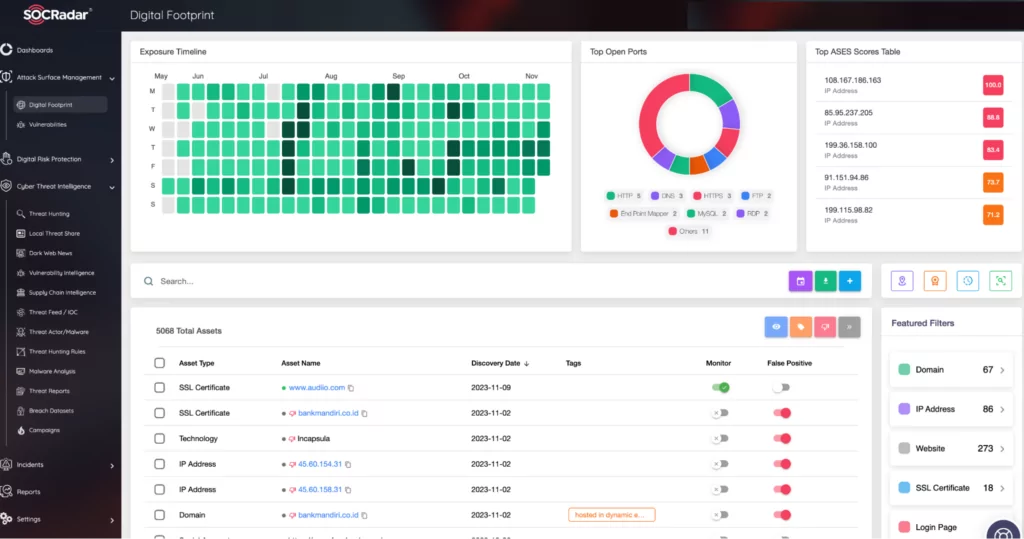
The digital attack surface should be well-defined and managed through Attack Surface Management (ASM) services. These services are essential for discovering digital assets within the expanding IoT ecosystem, identifying potential vulnerabilities, and assessing and mitigating cybersecurity risks. They provide a unified view of an organization’s cyber assets, enhancing the visibility of the expanding attack surface. For example, SOCRadar’s ASM allows for immediate exploration of public shadow IT assets to identify and address potential vulnerabilities that threat actors could exploit, while also enabling timely patch management and the mitigation of various security misconfigurations.
Which Type of Attacks Target IoT Devices?
As the number of IoT devices increases, so do their security vulnerabilities and the likelihood of exploitation by threat actors. IoT devices are particularly susceptible to network attacks, such as data theft, phishing, identity spoofing, and Distributed Denial of Service (DDoS) attacks. They can also lead to other cybersecurity incidents, including ransomware attacks and serious data breaches. To mitigate these threats, businesses need to be vigilant about potential cyber-attacks.
Here are some of the most common types of cyber-attacks targeting IoT devices:
1- Botnets and DDoS Attacks
IoT devices can be compromised to become part of a botnet, as seen with the Mirai botnet attacks. These devices, once controlled remotely, can be disabled, or can transfer private or sensitive corporate data, which can then be leveraged by threat actors in underground markets.
A DDoS attack, often utilized by hacktivist groups, overwhelms a targeted website’s infrastructure with excessive internet traffic, disrupting normal network activity. Although DDoS attacks typically do not aim to leak data, they can damage a business’s brand reputation and relationship with its customers.
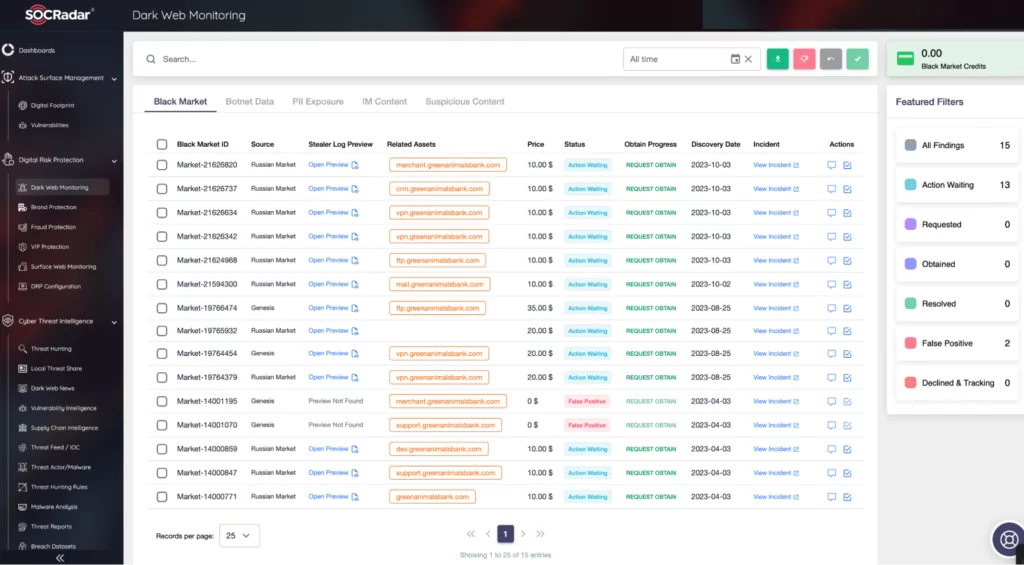
Dark Web Monitoring services, such as those provided under SOCRadar Digital Risk Protection, play a critical role. They continuously scan the dark web to uncover personal, sensitive, and trade secret information compromised by threat actors. Additionally, these services detect enslaved devices within botnets, many of which contain insecure IoT devices, and provide timely alerts.
2- Ransomware Attacks
The control of power grids, manufacturing operations, and other large-scale infrastructure by IoT devices makes them increasingly attractive targets for hackers seeking to make a public impact. The proliferation of Ransomware-as-a-Service (RaaS) platforms allows attackers to use decentralized tools to inflict damage more easily. Developing a mitigation plan for these attacks is crucial for companies operating in the IoT space.
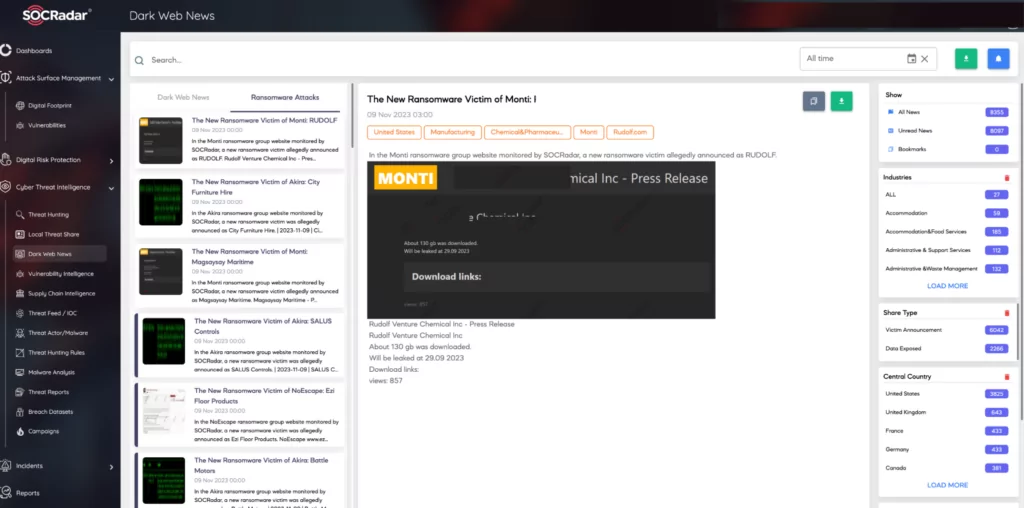
Cybersecurity attacks that impact our daily lives underscore the need to enhance IoT and Operational Technology (OT) security. For instance, in May 2021, a ransomware attack on Colonial Pipeline forced the company to shut down a major fuel pipeline on the East Coast, resulting in a ransom payment of approximately US$4.4 million to regain control of its infrastructure. This attack exploited a vulnerability in critical infrastructure, often running on complex, legacy systems that may not receive timely updates, highlighting the vulnerability of such infrastructure to cyberattacks. While technical investigations on the point of entry of this attack are ongoing, discussions on IoT integration of OT systems have heated up and opinions are shared that this will slow down.
The SOCRadar Dark Web News module separately tracks ransomware attacks and provides instant updates. This service enables insights into threat actor trends, helping protect against ransomware attacks, with filtering options for different countries and sectors.
3- Password Attacks
Hackers often try to access IoT devices by trying a large number of passwords, hoping to guess correctly. Often using brute force and a more specific type of dictionary attack, or a hybrid attack using both, cyber attackers use common password lists by systematically checking and trying all possible passwords and password phrases until they find the right one by generating a large number of guesses through software called password cracking tools.
The success of the password attacks is partly due to the fact that IoT devices have default settings with simple passwords. Default credentials are often factory presets embedded in devices and applications. Often these defaults are also shared between similar devices and may be well known to threat actors. Devices, systems and accounts with default settings are susceptible to dictionary, brute force and many other types of attacks. If an organization has a large number of IoT devices on endpoints that all share the same, unchanged defaults, such endpoints are likely to be the weakest link and easily compromised. Once attackers gain access to IoT devices through a password attack, then they can install malware or steal critical business data.
4- Eavesdropping
Threat actors seeking sensitive data might exploit weak links in IoT devices to infiltrate networks. Eavesdropping typically involves intercepting digital or analog voice communications or data sniffing. Through these methods, attackers can capture personal and corporate data, such as credit card information and intellectual property.
The goal of eavesdropping attacks is usually to steal confidential and valuable data by snooping on unsecured or unencrypted traffic. Hackers can exploit unpatched vulnerabilities in IoT devices and use them to access and monitor the targeted network. They can also install detection software or network monitoring tools.
For attackers, the potential gain from eavesdropping attacks can be significant. Everything from credit card information to personally identifiable information (PII), customer or employee passwords, and intellectual property can be compromised.
With the rise of IoT, there are more devices on business networks than ever before, increasing the risk. To minimize eavesdropping risks, organizations should implement network segmentation, dividing the network into segments and limiting access to critical users.
5- Firmware Attacks
Firmware attacks on IoT devices have become a growing concern in recent years. These attacks exploit vulnerabilities in firmware – the low-level software that controls the device’s hardware – to gain access to sensitive data or remotely control the device. Firmware attacks are particularly dangerous because they can be difficult to detect and can allow attackers to gain access to a device for long periods of time.
Typical of this type of attack is the Stuxnet worm, first discovered in 2010, an advanced malware designed to target industrial control systems, such as those used in nuclear power plants and other critical infrastructure. The worm spread via infected USB drives and exploited a vulnerability in the firmware of Siemens Programmable Logic Controllers (PLCs). The worm was able to modify the firmware of PLCs and manipulate their operation, causing potentially catastrophic damage. The Stuxnet worm was believed to have been developed by the US and Israel as part of a cyber warfare campaign against Iran’s nuclear program.
In addition to being difficult to detect, firmware attacks pose a significant risk by allowing long-term unauthorized access to IoT devices. The consequences of such attacks can range from device failure to data theft and physical damage. It is also possible to ensure the security and integrity of connected IoT devices by taking proactive steps backed by Cyber Threat Intelligence (CTI) beyond keeping firmware up to date, using strong passwords, and monitoring suspicious activity on the network.
What is the Role of CTI in IoT Security? How Can SOCRadar Help?
Cyber Threat Intelligence (CTI) is a key component of the modern proactive cybersecurity approach that helps organizations stay ahead of potential threats by collecting, processing and analyzing data from the open and dark web to better understand a potential cyber attacker’s intent, possible targets and attack methods.
A recent study by IEEE proposes a CTI platform for Internet of Things (IoT) devices that uses machine learning to predict potential threats propagating to smart devices using a Naïve Bayes supervised machine learning (ML) classifier.
SOCRadar Threat Intelligence supports the widest range of industrial devices and protocols and is continuously developed by an industry-leading research team.
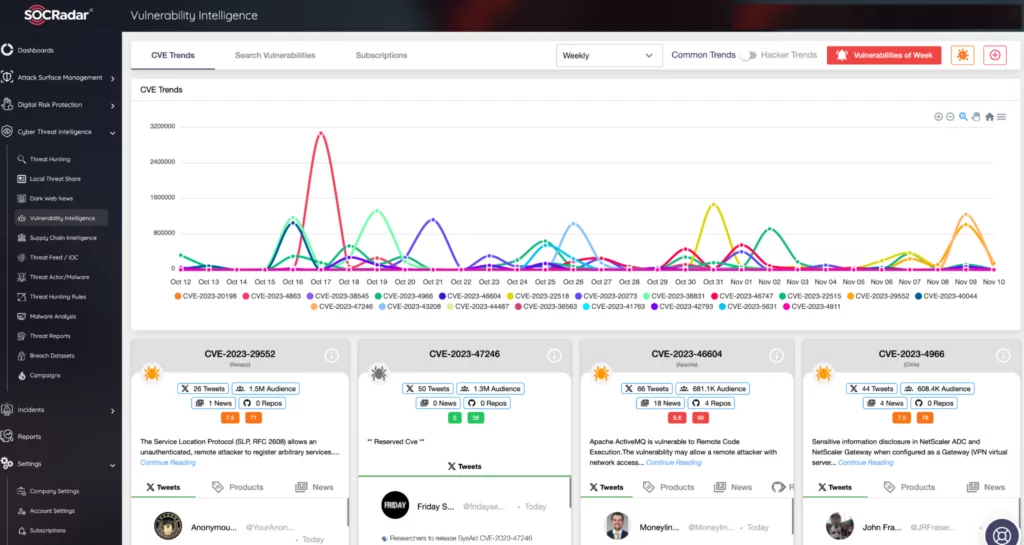
With the SOCRadar Vulnerability Intelligence module, you can gain insights into which vulnerabilities are being exploited by threat actors. It provides contextual and actionable intelligence about known and zero-day vulnerability data specific to potentially vulnerable OT and IoT technologies to accelerate risk assessment and knowledge validation processes.
In the underground world, it is impossible to keep up with the massive amount of threat data that emerges every day. Curating this data from trusted sources and presenting it in a customized way is vital for security teams who are lost between real threats and misleading information.
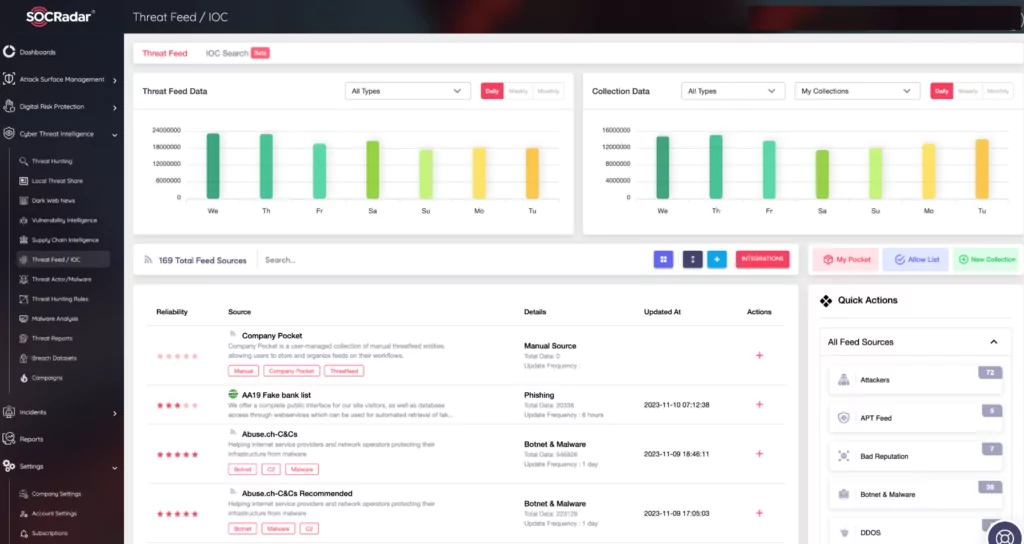
SOCRadar’s Threat Feed and IoC Management module assists cybersecurity teams in their cyber threat research by providing detailed data supported by user-friendly dashboards.
Cybersecurity professionals can customize these streams, review the latest threat information and Indicators of Compromise (IoCs) for malware specific to IoT devices, and integrate them into corporate systems. It can be used as a threat stream that can be transferred to third-party security solutions, such as firewalls and orchestration solutions, with integration via the TAXII protocol.
Conclusion
The adoption of IoT (Internet of Things) and OT (Operational Technology) is surging as organizations across various industries continue their digital transformation efforts. However, cybercriminals are advancing their development, deployment, and exploitation techniques, utilizing AI to launch faster and more sophisticated attacks. As discussed in this article, a broad spectrum of cyberattacks, particularly DDoS (Distributed Denial of Service) and ransomware attacks, pose significant threats to this ecosystem.
Cyberattacks on IoT ecosystems can lead to more unpredictable effects, as they can more readily result in physical consequences. This is particularly evident in the Industrial Internet of Things (IIoT) sector, where previous cyberattacks have demonstrated sequential repercussions. It is crucial to acknowledge that IoT security is a complex and ever-evolving field. Staying informed about the latest security trends and best practices is imperative.
Proactive IT professionals are already beginning to reevaluate their security strategies, incorporating threat intelligence into an integrated and automated security framework. This approach aims to mitigate common threats targeting IoT and OT devices while actively enhancing their security.



































