
Top 10 Breach and Attack Simulation (BAS) Software in 2024
In the cyber world, attackers are constantly seeking out new vulnerabilities and weaknesses to exploit. From phishing campaigns to advanced malware, cybercriminals use sophisticated tactics to infiltrate networks, often bypassing traditional security measures. As the threats become more complex, understanding your security weaknesses from an attacker’s perspective is critical. After all, without visibility into how and where a breach might occur, organizations are left in the dark, exposing themselves to potentially devastating consequences.
To effectively counter these dangers, businesses need to simulate real-world attack scenarios, testing their defenses against the tactics and methods used by cybercriminals – Breach and Attack Simulation (BAS) tools provide this capability. They allow organizations to evaluate their security posture by safely emulating different types of cyberattacks, from phishing schemes to lateral movement across networks.

Best Breach and Attack Simulation Software to test your defenses in 2024 (Illustrated by DALL-E)
In other words, instead of waiting for a cyberattack to happen, BAS platforms enable businesses to stay one step ahead, constantly testing their defenses and refining their security strategies. Some great BAS tools provide continuous, automated testing of security infrastructures, ensuring that defenses are always up to date and resilient against the latest attack techniques.
In this blog post, we’ll explore some of the best Breach and Attack Simulation software for 2024 and highlight how each can help fortify your cybersecurity defenses.
What is the Purpose of a Breach and Attack Simulation (BAS) Software?
Breach and Attack Simulation (BAS) tools are vital for organizations looking to stay ahead of potential cyber threats by testing their security defenses in a controlled environment.
These platforms emulate real-world attack scenarios, allowing security teams to simulate tactics used by cybercriminals without the risk of actual damage. By doing so, BAS tools help identify vulnerabilities in an organization’s network, systems, and applications, offering insights into where security measures might fail under attack.
The primary users of BAS platforms are security teams, CISOs, and incident response units within organizations.
Common Use Cases of BAS Platforms
BAS platforms are vital for evaluating the strength of security protocols, offering an essential layer for both risk management and regulatory adherence. They enable organizations to simulate cyberattacks, preparing them for real-world threats and refining their defensive measures.
Some key applications of BAS tools are listed below.
- Simulating attack paths, which helps identify vulnerabilities before attackers do. By recreating potential cyberattacks, BAS tools allow organizations to observe how a threat might move through their system. For example, a simulation might reveal a weak point in a network configuration that could allow lateral movement if not addressed.
- Validating security controls to ensure defenses function as intended. BAS platforms test firewalls, antivirus software, and other protective measures to verify they are properly set up. An organization may use BAS to assess whether their endpoint protection can block ransomware at different stages of an attack.
- Continuous monitoring for adapting security strategies to new risks. BAS tools provide ongoing assessments to help security teams keep pace with emerging threats. For instance, a company might use these tools to regularly test for vulnerabilities related to newly discovered exploits.
- Meeting regulatory compliance by regular security tests. BAS solutions ensure that an organization’s security measures align with industry standards and legal requirements. For example, a financial institution might employ BAS to verify that its security controls meet the standards of the PCI DSS (Payment Card Industry Data Security Standard).
These platforms are particularly useful for organizations looking to strengthen their cybersecurity approach, offering clear insights that help businesses stay ahead of potential risks and adjust their defenses accordingly.
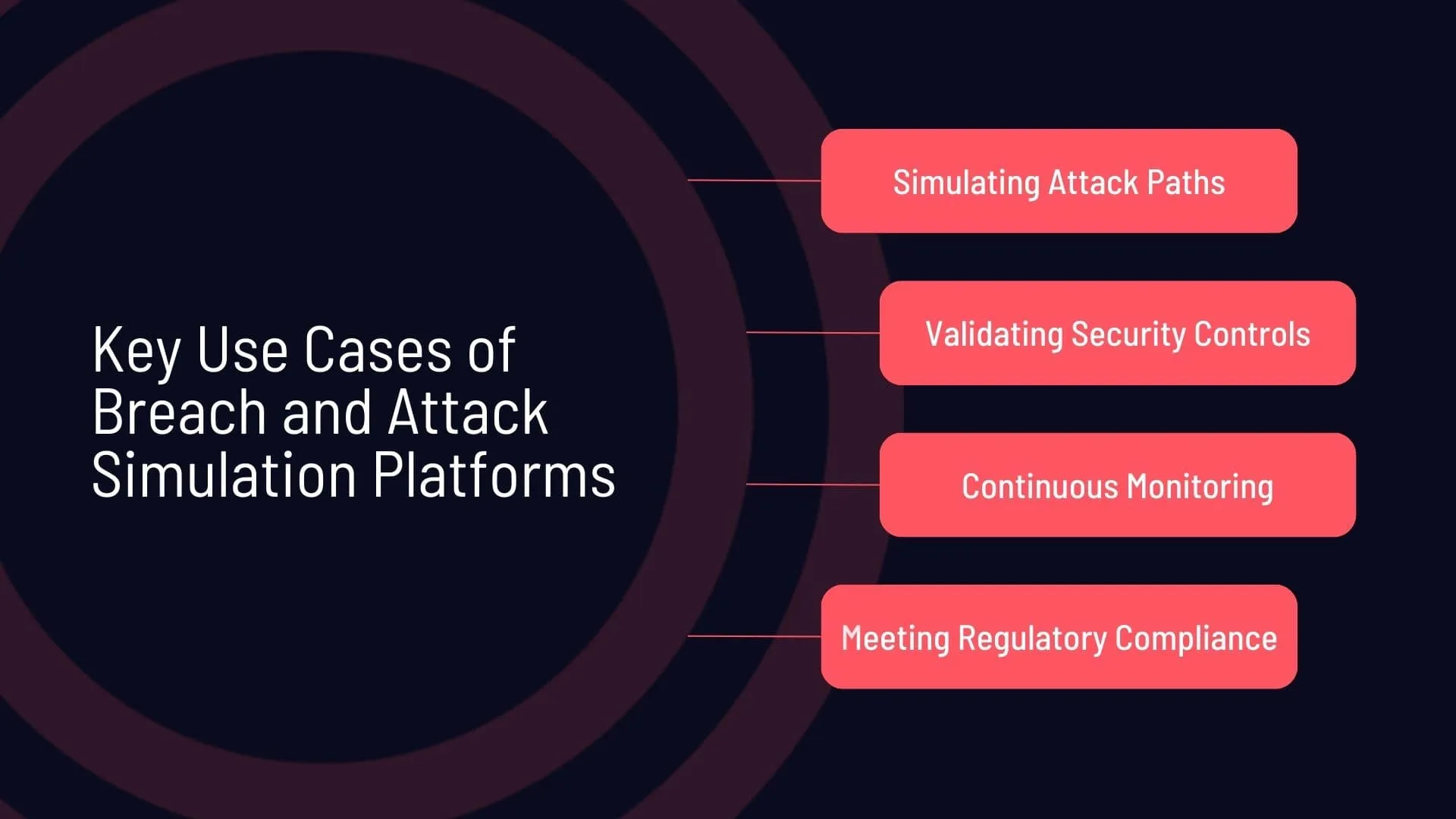
Key use cases of Breach and Attack Simulation platforms
Read on to explore our curated top 10 list showcasing some of the best BAS platforms, and their capabilities. The list is not in any specific rank order but is derived from trusted sources such as G2 and Gartner, as well as user reviews on social platforms.
1. Pentera
Pentera, previously known as Pcysys, is a prominent provider of Breach and Attack Simulation (BAS) solutions that automate security validation. It enables organizations to continuously test their defenses against real-world cyber threats, ensuring they stay resilient in an evolving security landscape.
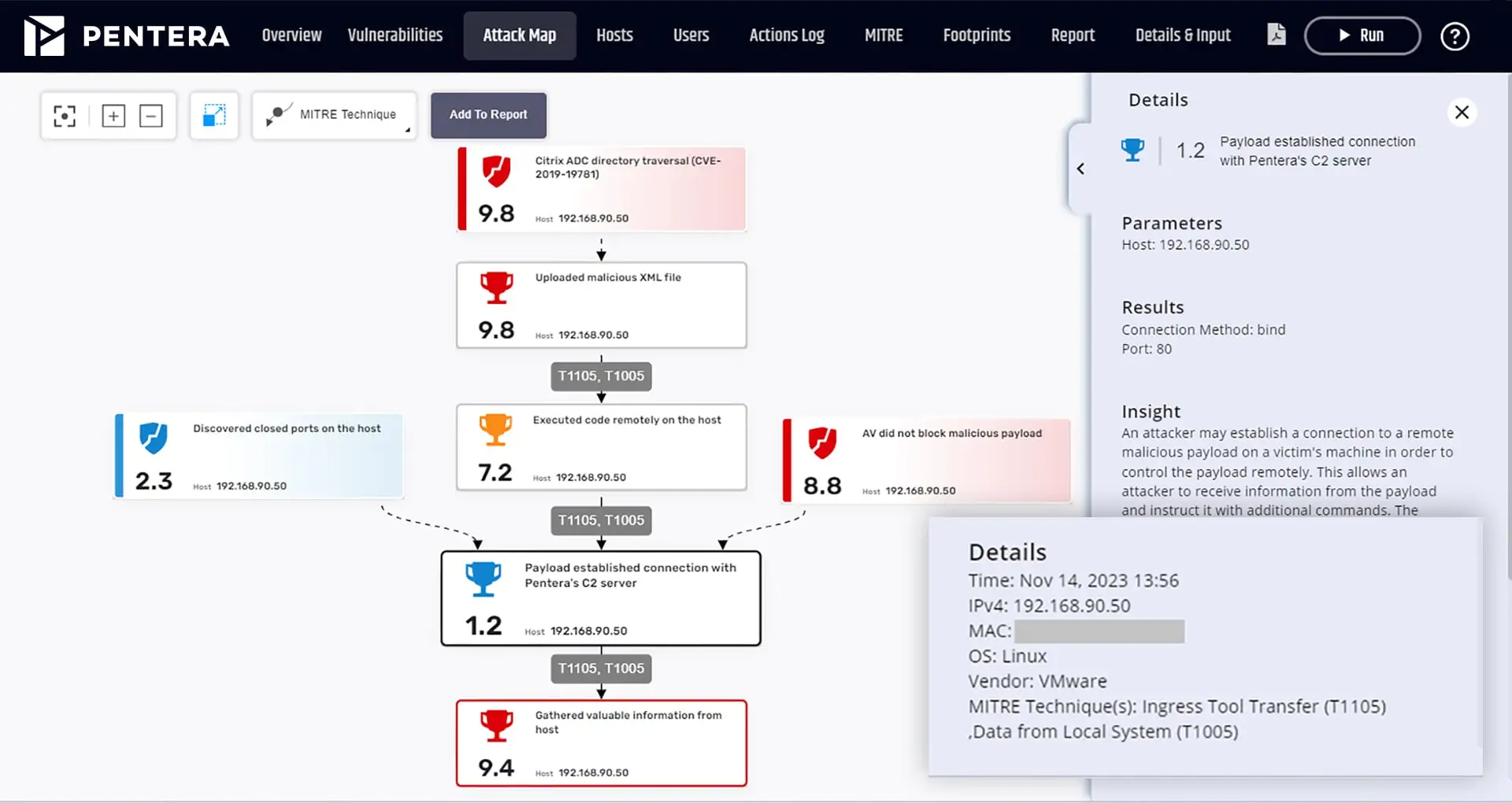
Pentera is an automated security validation platform that simulates real-world cyberattacks to assess and improve an organization’s defenses.
Key Features:
- Pentera automates the validation of security controls and configurations, providing broader coverage than traditional penetration testing, which typically addresses only a fraction of IT assets.
- It operates without requiring agents or pre-installation, simplifying deployment and reducing operational overhead.
- The platform emulates real-world attacker Tactics, Techniques, and Procedures (TTPs), mapping an organization’s attack surface and simulating internal and external threats. This approach helps identify potential exploits before they can be used in actual attacks.
- With continuous testing capabilities, Pentera ensures defenses are always adapting to emerging vulnerabilities.
- In addition, the platform generates a prioritized remediation roadmap, helping security teams focus their resources on addressing the most critical risks.
Pentera’s proactive approach to security validation makes it an essential tool for organizations looking to strengthen their cybersecurity posture.
2. AttackIQ
AttackIQ is a comprehensive Breach and Attack Simulation (BAS) platform designed to help organizations continuously test and strengthen their security posture through automated validation of security controls.
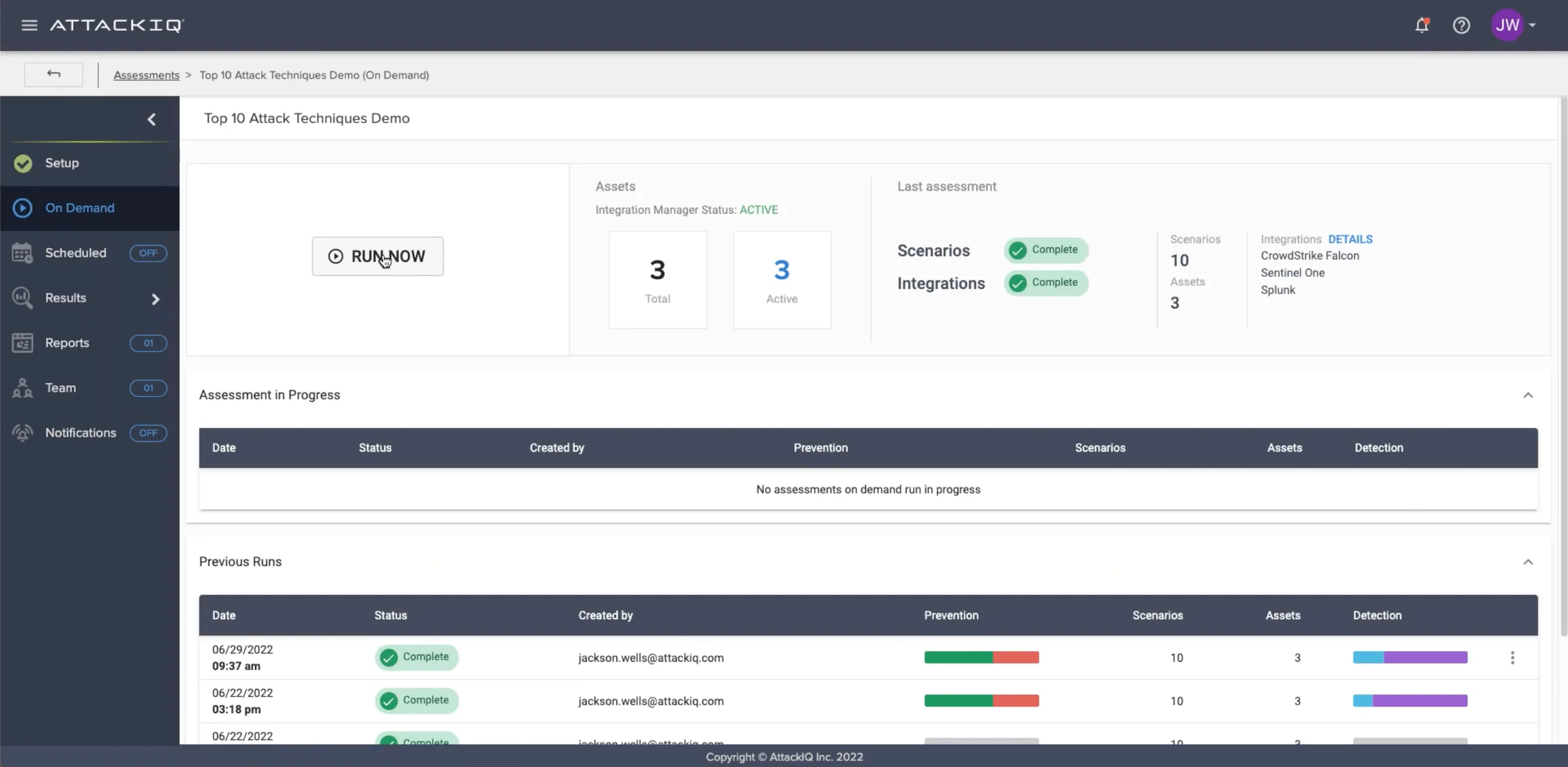
AttackIQ enables continuous security validation through real-world attack simulations, improving overall cybersecurity readiness.
Key Features:
- AttackIQ allows organizations to simulate real-world cyberattacks and evaluate their defenses, leveraging the MITRE ATT&CK framework to identify vulnerabilities and weaknesses.
- AttackIQ’s Mission Control feature centralizes and streamlines BAS operations for organizations with distributed teams, making it easier to orchestrate tests across multiple departments and locations.
- AttackIQ’s ability to test machine learning (ML) and artificial intelligence (AI) components in security systems offers advanced insights into how these technologies handle critical assets.
- AttackIQ supports both on-premises and cloud deployments, offering agentless testing to simplify the validation of security controls with minimal installation overhead.
- The platform provides intuitive dashboards with performance scores to help security teams measure and track security improvements over time.
AttackIQ’s BAS platform is built to enhance cybersecurity efficiency, helping organizations proactively address potential security gaps before they become serious threats.
3. Cymulate
Among Breach and Attack Simulation (BAS) platforms, Cymulate also stands out as a popular and preferred one, aimed to help organizations validate their cybersecurity controls by safely simulating real-world cyberattacks.
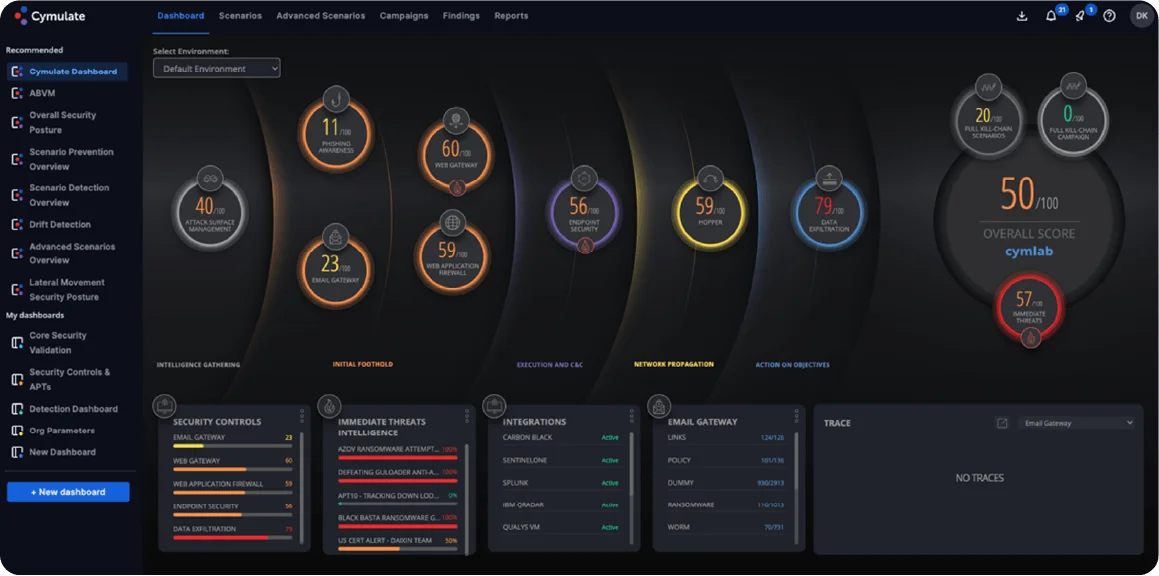
Cymulate is a BAS tool that provides attack simulations that test internal and external defenses.
Key Features:
- Cymulate enables organizations to assess their security posture against evolving threats by conducting automated simulations of various attack scenarios, including malware delivery and phishing attempts.
- The platform tests the entire attack kill chain, utilizing thousands of simulated cyberattacks, from common to emerging threats, to identify weak points in security controls.
- Cymulate’s cloud-based system requires minimal setup, deploying quickly with a single lightweight agent to streamline integration and testing.
- The simulations are powered by the latest threat intelligence and aligned with the MITRE ATT&CK framework, ensuring up-to-date testing of defenses like email gateways, web application firewalls, and endpoints.
- After simulations, Cymulate generates detailed reports with actionable insights and remediation guidance, helping organizations benchmark their security posture against industry standards.
Cymulate is a powerful BAS tool for organizations aiming to strengthen their defenses through continuous testing and proactive improvement.
4. Picus
Picus Security provides Breach and Attack Simulation (BAS) solutions that enable organizations to continuously assess and validate their defenses against real-world cyber threats.
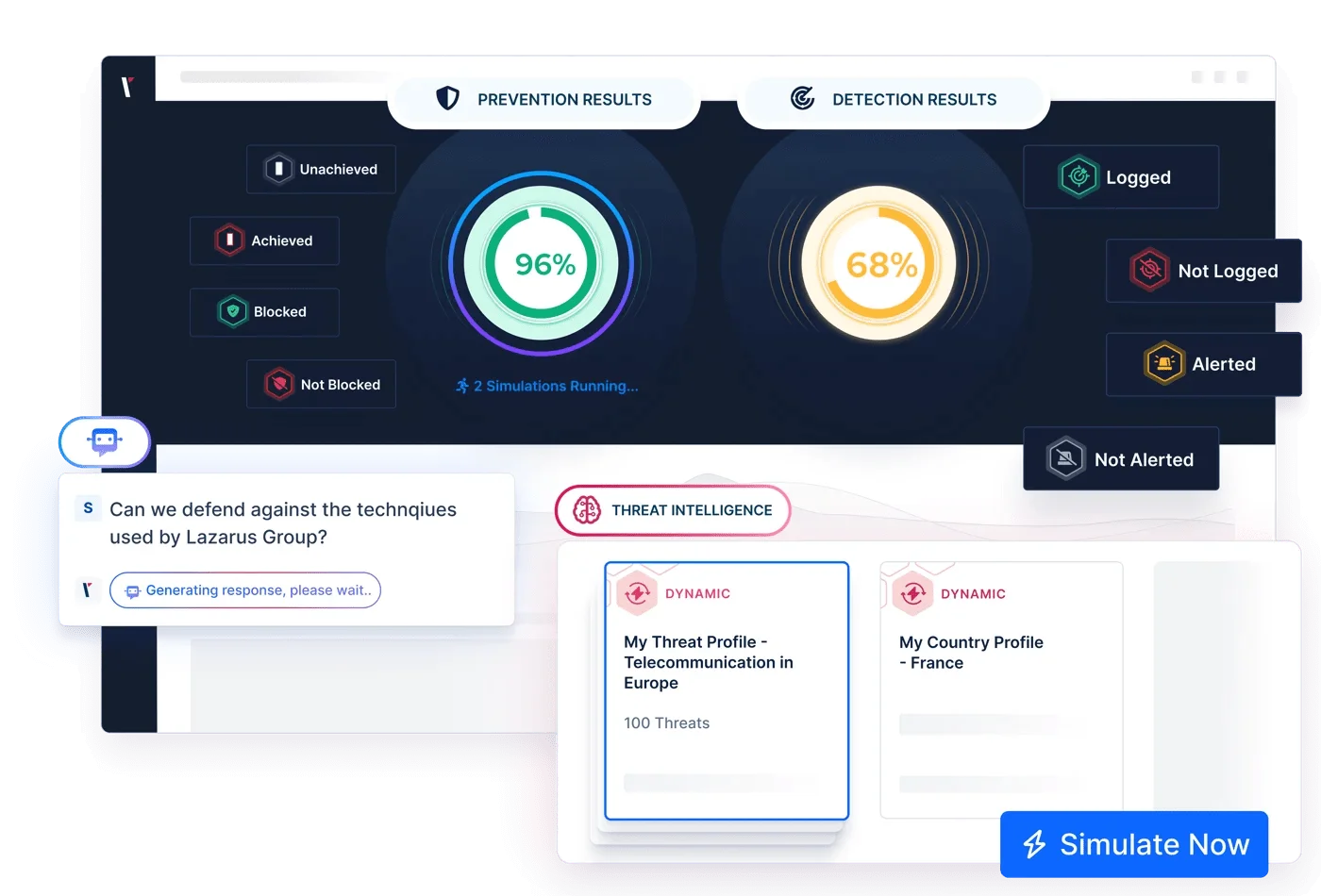
Picus Security can be a valuable BAS solution with its real-time threat simulation capabilities.
Key Features:
- Picus allows organizations to actively test their security measures, detecting vulnerabilities and weaknesses in real time as they appear.
- Picus supports automated simulations, enabling ongoing security assessments with minimal manual involvement and no disruption to production systems.
- The platform integrates with various SIEMs and security products, enhancing the validation of existing defense mechanisms.
- Upon completing simulations, Picus provides detailed reports with insights on security performance, discovered vulnerabilities, and recommendations for remediation, helping organizations prioritize their security efforts effectively.
- The platform features an extensive, regularly updated threat library, simulating both pre-compromise attacks like phishing and vulnerability exploitation, as well as post-compromise activities such as lateral movement and data exfiltration.
With its capabilities, Picus is a well-established player in the BAS market, supporting organizations in improving their cybersecurity resilience through continuous validation and testing.
Build Predictive Defense Beyond Simulation with Threat Actor Intelligence
Nevertheless, staying ahead of threat actors requires more than just simulation. While BAS tools can help simulate real world tactics, continuous monitoring of cybercriminal activities is essential for predictive defense.
SOCRadar’s Threat Actor Intelligence module complements simulation efforts by providing real-time insights into the behaviors, tactics, and emerging campaigns of threat actors.
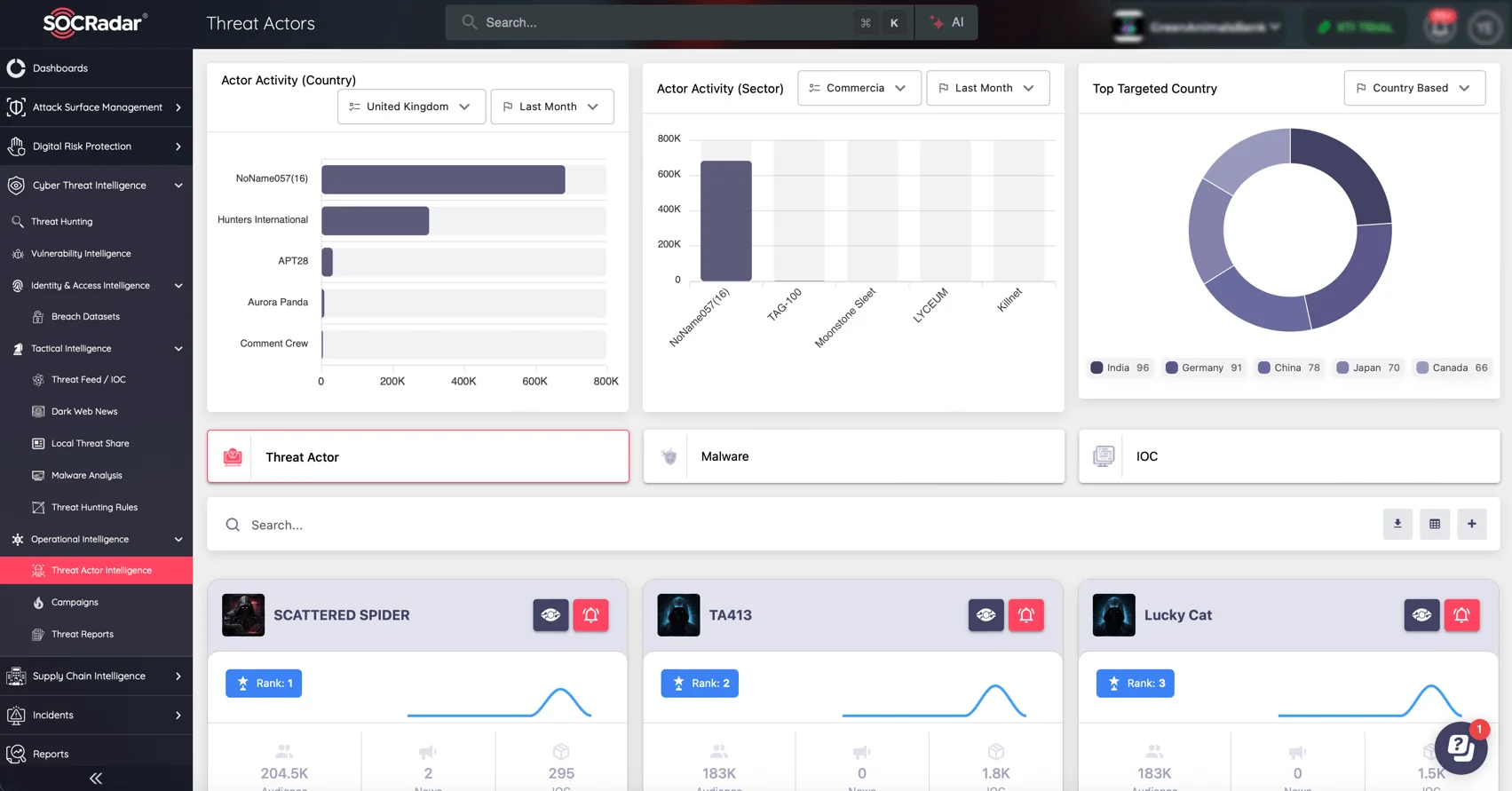
SOCRadar’s Threat Actor Intelligence module provides real-time insights into cybercriminal activities, enabling organizations to monitor emerging threats and anticipate adversaries’ tactics.
This intelligence allows organizations to not only address current vulnerabilities but also anticipate the next move of adversaries, enabling them to fine-tune their defenses based on real-world data and evolving threats.
5. RidgeBot
RidgeBot automates penetration testing and vulnerability management, allowing organizations to simulate attacks and assess their security posture with minimal manual effort.
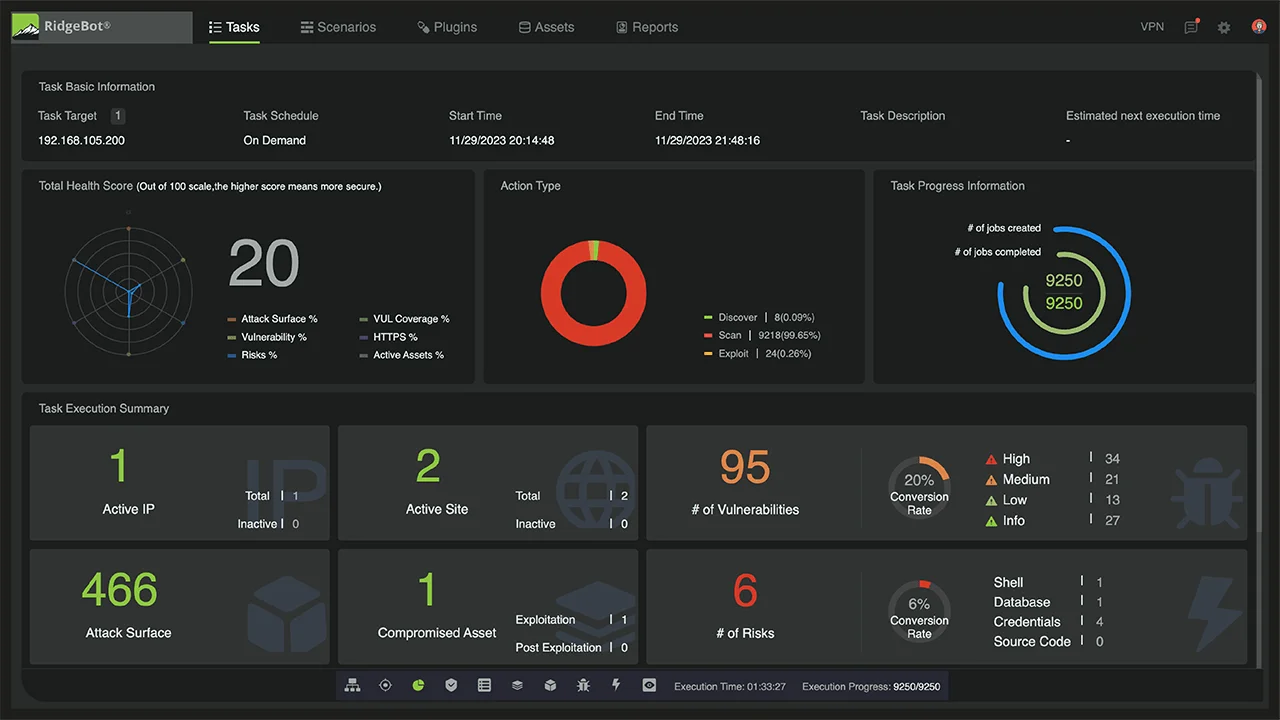
RidgeBot automates penetration testing and provides detailed visualizations of attack paths to help organizations identify vulnerabilities.
Key Features:
- RidgeBot automates the entire penetration testing process, offering continuous security assessments without needing extensive manual input.
- The platform provides clear visualizations of attack paths, illustrating how vulnerabilities can be exploited to compromise systems. This helps security teams better understand the attack surface and related risks.
- RidgeBot validates vulnerabilities by simulating real-world attack scenarios, ensuring that security measures are effective against potential exploits.
- Users can modify testing tasks dynamically, adding new targets or vulnerabilities during the process, which enhances flexibility and thoroughness.
- RidgeBot categorizes risks based on the impact of the identified vulnerabilities, helping organizations prioritize remediation efforts more effectively.
RidgeBot is a valuable BAS tool for organizations seeking to proactively enhance their cybersecurity defenses through continuous testing and real-time attack simulations.
6. vPenTest
vPenTest, developed by Vonahi, integrates Breach and Attack Simulation (BAS) into its comprehensive penetration testing platform, providing pre- and post-breach simulations to help organizations assess their security posture.
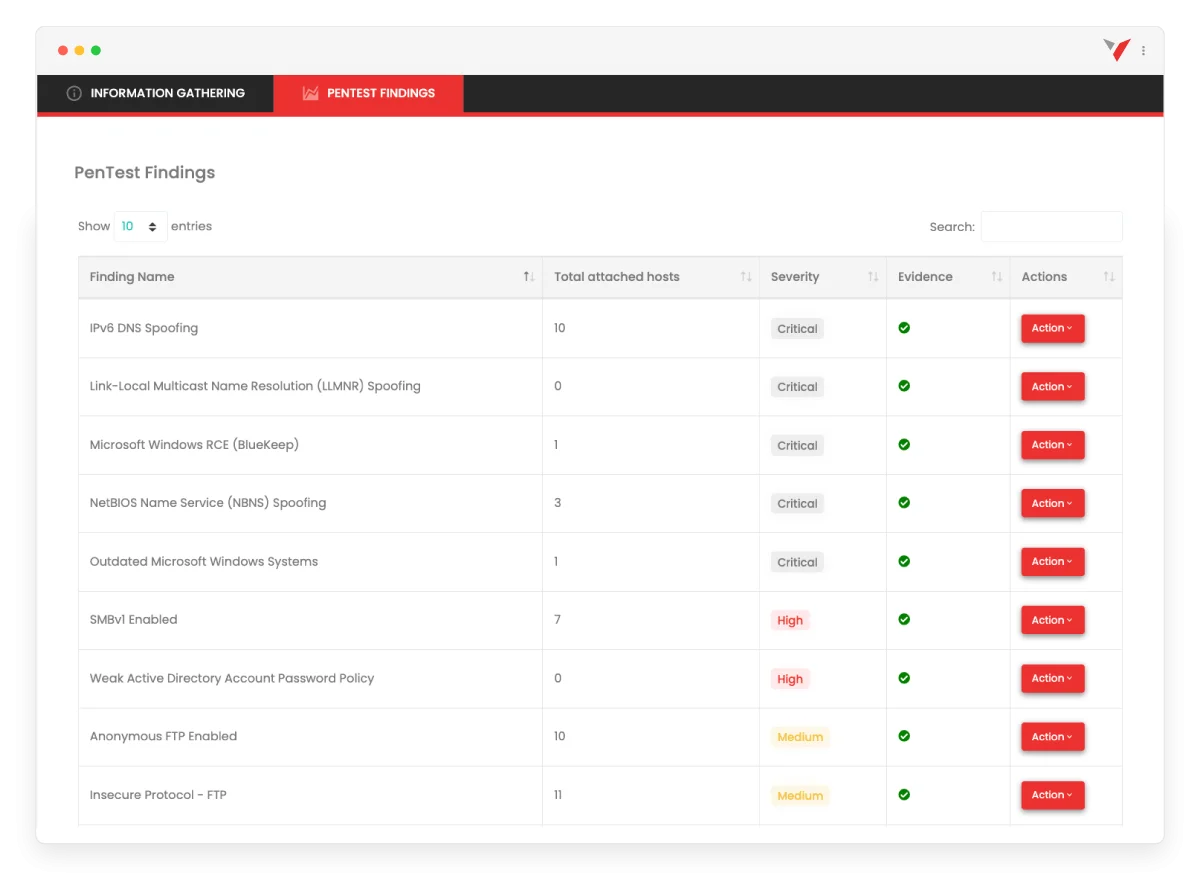
vPenTest automates penetration testing and simulates pre- and post-breach attack scenarios to identify vulnerabilities.
Key Features:
- vPenTest simulates attack scenarios both before and after a breach, enabling organizations to identify vulnerabilities and evaluate how well their defenses perform in various situations.
- By automating many aspects of penetration testing, vPenTest reduces the risk of human error and increases efficiency. This allows for faster and more consistent assessments compared to traditional testing methods.
- The platform uses a wide array of attack techniques, such as open-source intelligence gathering, exploitation, and post-exploitation, to thoroughly test security controls. Simulations include real-world scenarios like password-based attacks and Man-in-the-Middle (MitM) attacks.
- vPenTest provides detailed logs to track the progress of tests, enabling organizations to correlate findings with their incident response processes.
vPenTest enhances penetration testing with BAS features, allowing organizations to continuously validate their security posture and stay ahead of evolving threats.
7. Scythe
Scythe is an adversary emulation platform crafted to replicate real-world cyberattacks, enabling organizations to identify their vulnerabilities and strengthen their security measures. Thereby, it is listed among popular choices for Breach and Attack Simulation (BAS).
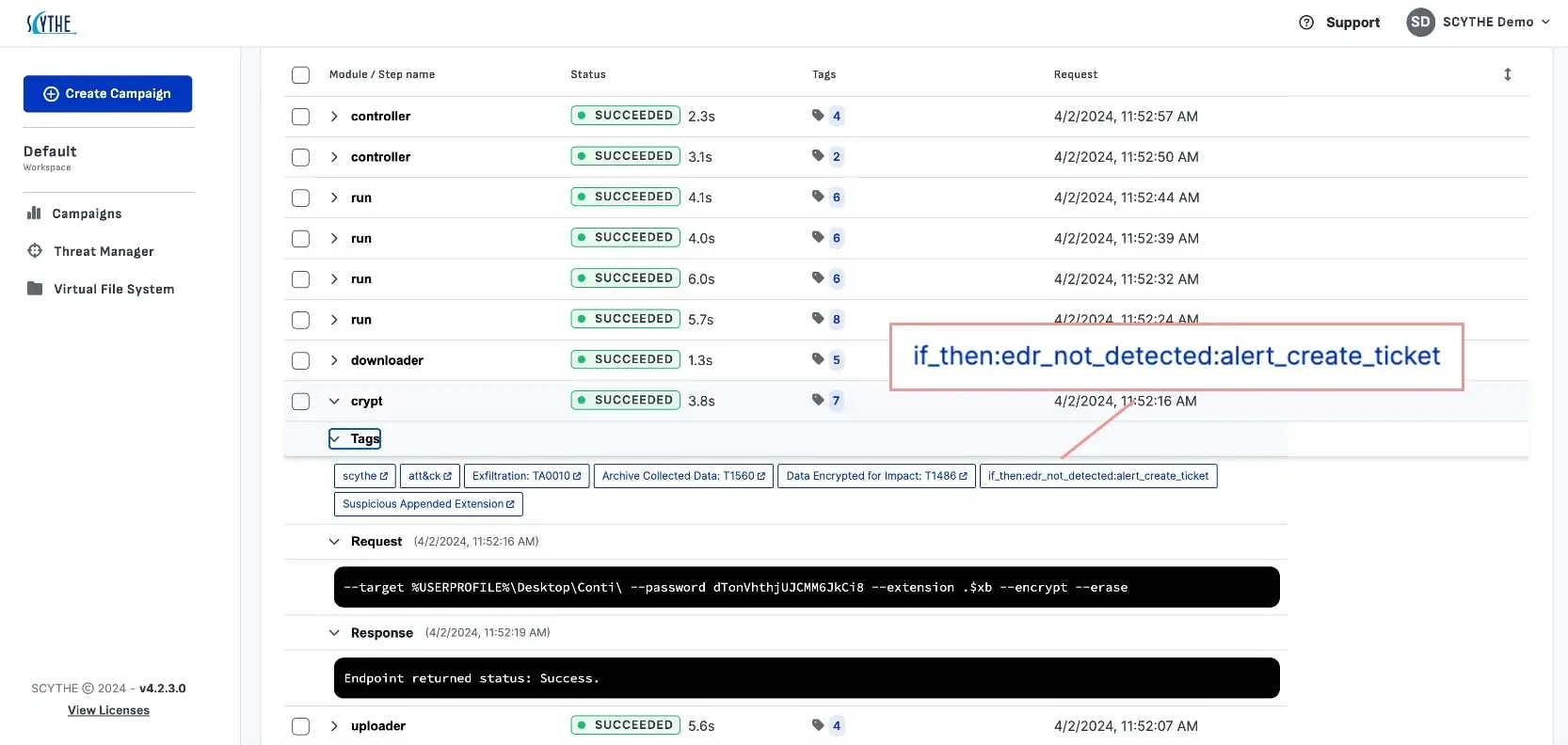
Scythe enables realistic adversary emulation to help organizations identify vulnerabilities and enhance their defense strategies.
Key Features:
- Scythe replicates real attacker Tactics, Techniques, and Procedures (TTPs), allowing organizations to assess vulnerabilities in a realistic environment.
- Scythe’s command-by-command simulation feature helps with real-time adjustments during detection engineering and purple team exercises, optimizing security measures.
- The platform’s extensive threat library prepares organizations to handle both known and emerging threats effectively.
- Scythe offers a no-code integration framework for seamless connection with existing security tools, enhancing operational efficiency.
- Scythe fosters collaboration between red and blue teams to document, analyze, and improve security measures.
- Scythe generates detailed, customizable reports with prioritized recommendations, helping users remediate critical vulnerabilities quickly.
Scythe offers both SaaS and on-premises solutions, making it a versatile tool for organizations aiming to boost their cybersecurity defenses through continuous adversary emulation.
8. IBM Security Randori Recon
IBM Security Randori Recon helps organizations continuously monitor and assess their external attack surfaces, identifying vulnerabilities and misconfigurations that attackers could exploit.
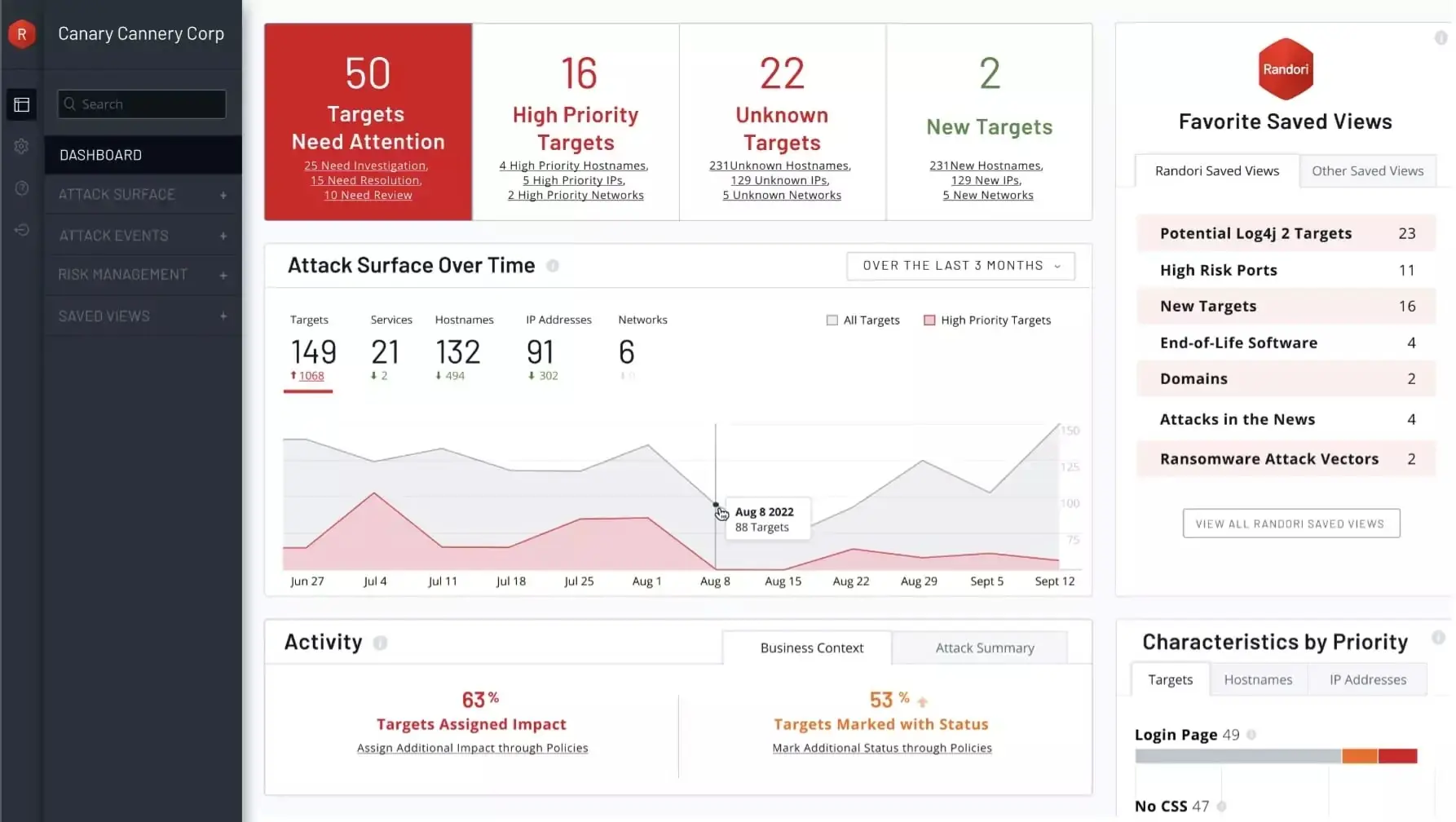
IBM Security Randori Recon continuously tests external attack surfaces for vulnerabilities and misconfigurations, providing real-time insights.
Key Features:
- The platform operates without prior information, closely mimicking real-world attack scenarios to identify both known and hidden vulnerabilities in an organization’s security defenses.
- Randori runs automated, real-world attack simulations, helping organizations validate their defenses against evolving threats.
- The platform maps both visible and hidden assets, including shadow IT, providing a thorough view of the entire attack surface.
- Randori ranks vulnerabilities based on their likelihood of being targeted, enabling teams to focus on the most critical threats.
- Organizations receive timely notifications of new vulnerabilities and misconfigurations, allowing proactive remediation.
- The platform integrates with existing security tools like SIEM, SOAR, and EDR, enhancing overall security operations and validating their effectiveness.
Randori Recon’s black-box approach and continuous monitoring make it a powerful tool for organizations looking to stay ahead of potential cyber threats.
9. Validato
Validato is a SaaS platform designed to help organizations of all sizes simulate, validate, and optimize their security controls against real-world cyber threats. By delivering enterprise-grade Breach and Attack Simulation (BAS) capabilities, Validato democratizes advanced security testing for both SMEs and large enterprises.
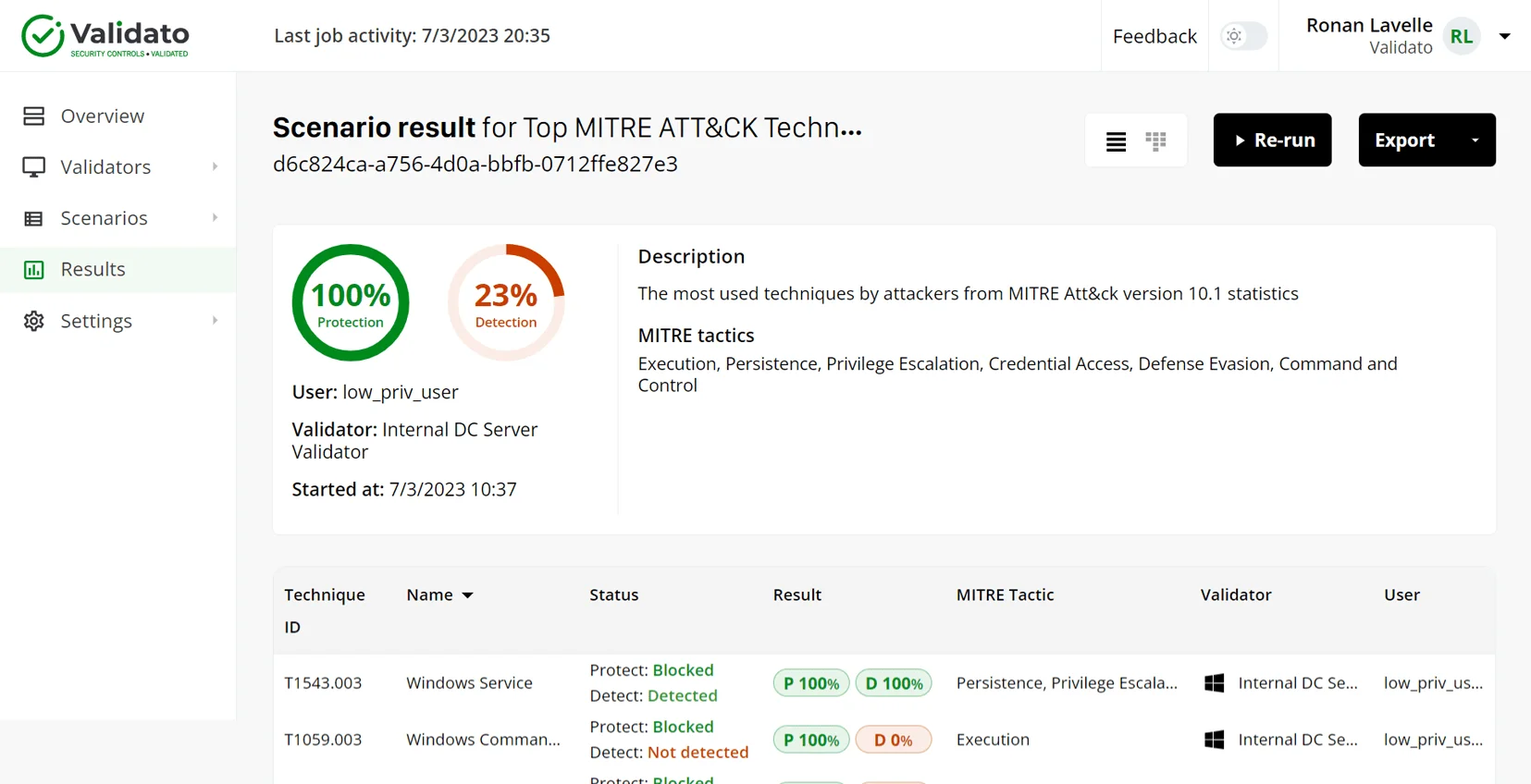
Validato simplifies automated threat testing while ensuring comprehensive security control validation.
Key Features:
- Validato leverages frameworks like MITRE ATT&CK to emulate cyberattack methods, testing how effectively security controls detect and respond to threats.
- The platform provides actionable data to assess the performance of security measures, ensuring organizations can identify and address gaps in their defenses.
- Simulations run without disrupting operational environments, allowing for seamless testing in live systems.
- Unlike one-time penetration tests, Validato offers ongoing evaluations, helping organizations stay ahead of evolving cyber threats.
- Validato employs a structured approach, starting with host-level controls and advancing to scenarios like lateral movement and data exfiltration.
- By tailoring its pricing to organizational size, Validato ensures mid-sized enterprises can afford comprehensive security validation.
With a focus on continuous, data-driven validation, the platform offers a scalable and cost-effective alternative to traditional red team exercises. Its flexible licensing model ensures affordability by aligning costs with organizational size, making comprehensive cybersecurity accessible to a broader range of businesses.
10. Infection Monkey
Infection Monkey, developed by Akamai Guardicore, is an open-source Breach and Attack Simulation (BAS) tool. Like other BAS solutions, it allows users to simulate real-world attack scenarios, but emphasizing the tactic of lateral movement across networks to uncover gaps in defenses that might enable malware attacks.
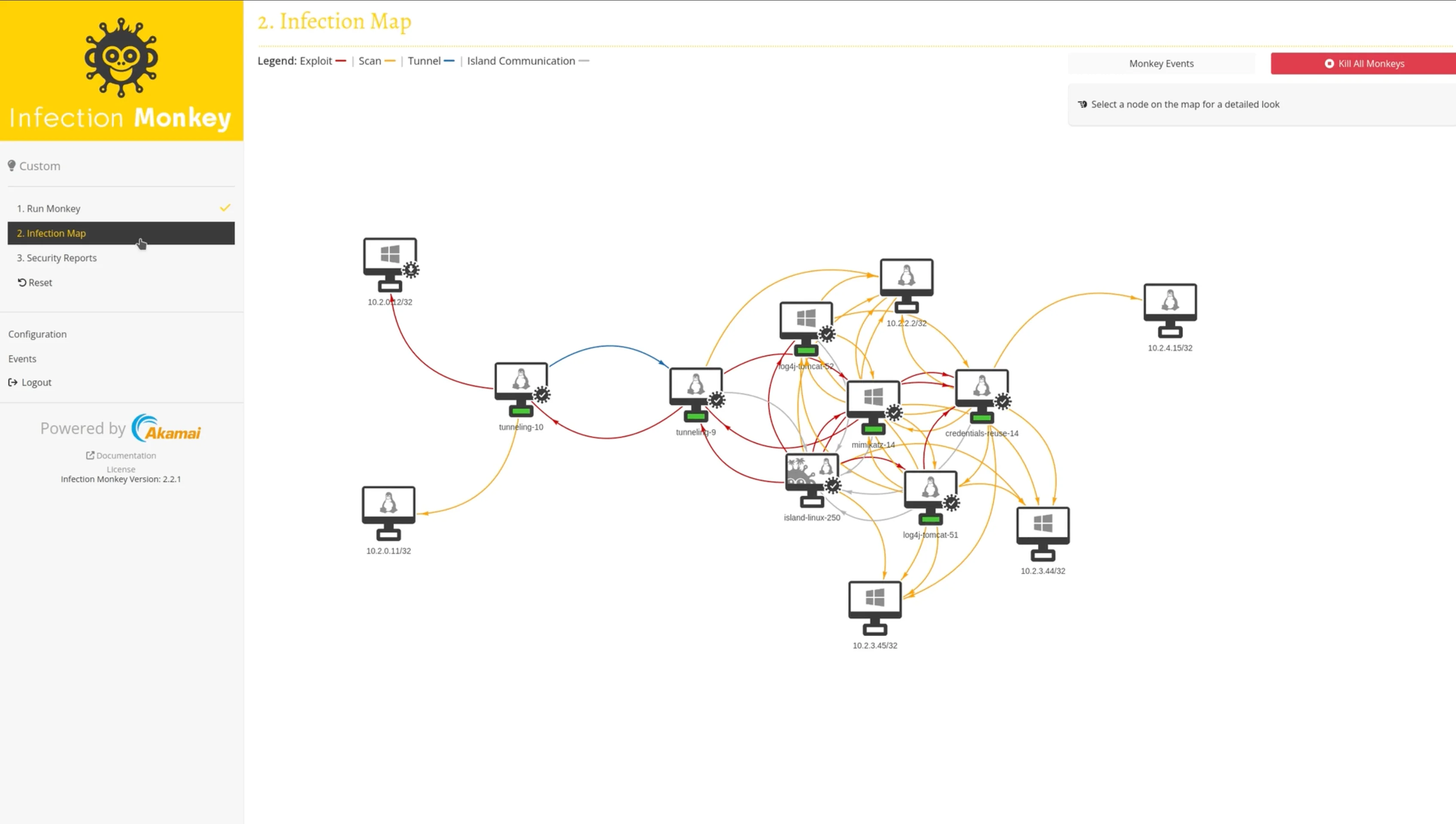
Infection Monkey is an open-source platform that simulates adversarial behavior to identify vulnerabilities and improve network defenses.
Key Features:
- Infection Monkey simulates malware and adversary behavior, focusing on lateral movement to test how attackers could breach systems and spread across the network.
- It emphasizes testing for ransomware and malware spread, providing insights into how well security controls can prevent and respond to such threats.
- The tool maps attack techniques to the MITRE ATT&CK framework, providing a clear view of how adversaries might exploit known vulnerabilities.
- Infection Monkey offers real-time insights into potential weaknesses, helping organizations assess where their defenses may fail against lateral attacks.
- As an open-source solution, Infection Monkey allows organizations to regularly simulate attacks without any costs, making it accessible for continuous testing.
- Infection Monkey supports modern and legacy systems, including Windows 2003, CentOS 6, RHEL5, and cloud environments like AWS, Google Cloud, and Microsoft Azure.
Infection Monkey offers robust, continuous testing capabilities across a variety of environments, making it a versatile tool for organizations aiming to identify vulnerabilities and enhance their cybersecurity strategies.
Combining BAS and ASM for Complete Cybersecurity Defense
Continuous monitoring for adapting security strategies to new risks is a crucial feature of BAS tools, but combining it with a comprehensive Attack Surface Management (ASM) solution can provide even deeper insights.
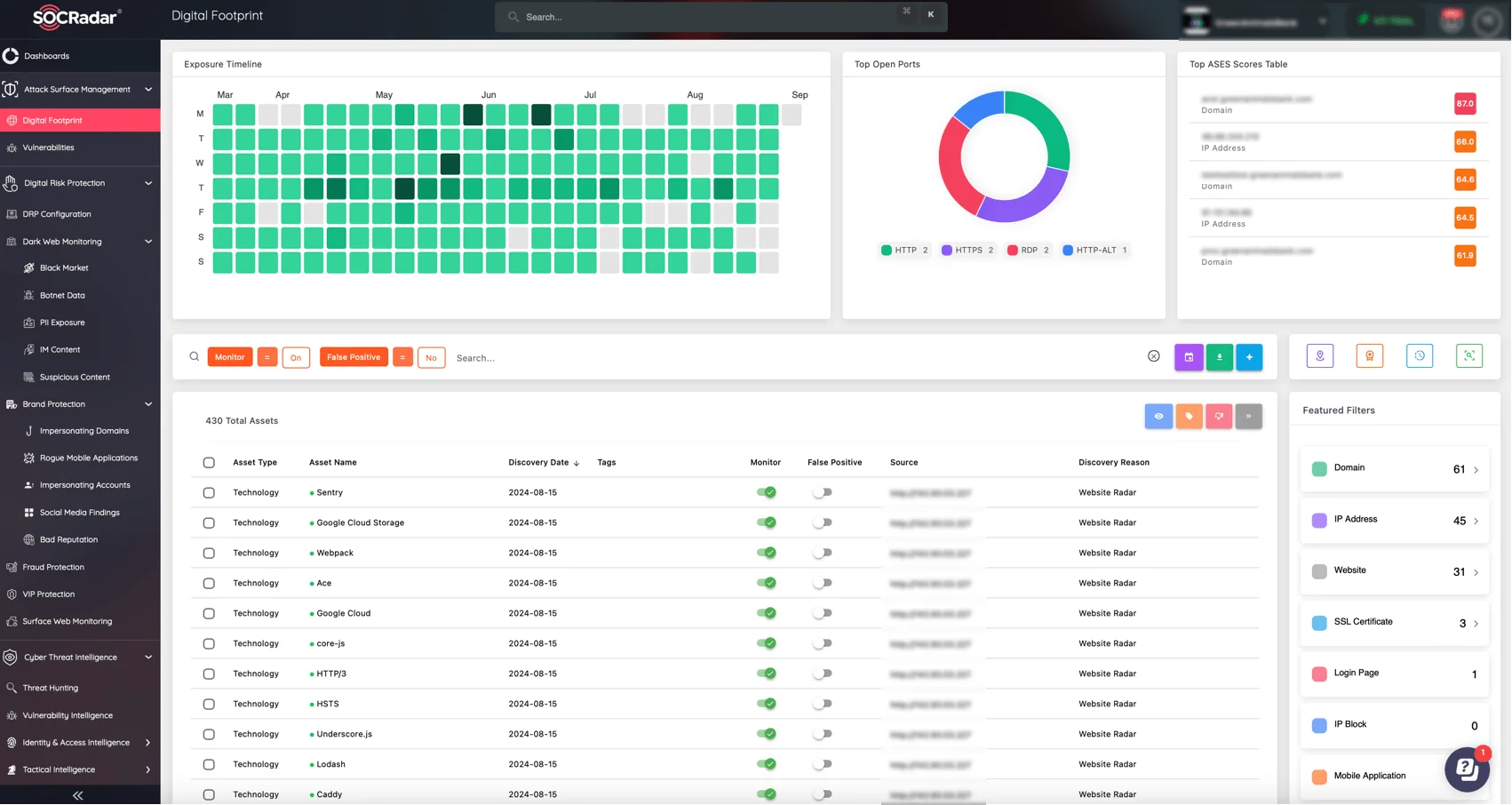
SOCRadar’s Attack Surface Management (ASM) module provides a comprehensive digital footprint view, helping organizations identify exposed assets, vulnerabilities, and misconfigurations across their entire attack surface.
SOCRadar’s ASM module allows organizations to continuously monitor and assess their entire attack surface, identifying exposed assets and vulnerabilities before attackers can exploit them. Integrating both types of solutions ensures that organizations can proactively manage risks while continuously validating their security defenses.
Conclusion
Breach and Attack Simulation (BAS) software typically allow organizations to anticipate how attackers might exploit their vulnerabilities before a real breach occurs. These platforms help teams continuously test their security controls, ensuring they are resilient in the face of evolving tactics. From simulating ransomware to validating endpoint defenses, they provide organizations with a proactive approach to protecting their digital assets.
However, while BAS solutions offer a strong foundation, combining them with broader monitoring strategies can elevate your defenses even further. SOCRadar’s Attack Surface Management (ASM) module, for instance, not only monitors your exposed assets but also tracks threats across the broader cyber landscape. By cross-matching potential risks with your specific vulnerabilities, it sends out alarms with actionable insights, helping you respond swiftly to threats that directly impact your organization. This layered approach ensures that organizations are not just prepared for simulations, but are also equipped to tackle real-world threats as they emerge.
By merging continuous validation with proactive monitoring and predictive insights, organizations can build a more robust cybersecurity posture, ensuring that their defenses remain one step ahead of cybercriminals. The combination of BAS and ASM tools provides the comprehensive coverage needed to protect against both known and unknown threats in an increasingly complex digital environment.





































