
Cyber Threat Intelligence for Supply Chain Security
Modern supply chains are more connected than ever, forming the backbone of global commerce. However, this interconnectivity also makes them prime targets for cyberattacks. As cyber threats grow in sophistication, organizations must adapt by leveraging cyber threat intelligence for supply chain security. By understanding the risks and proactively addressing vulnerabilities, businesses can build resilience and maintain operational continuity.
Illustration of supply chain. Generated By Dall-E
The Importance of Supply Chain Security
Supply chain security has become a critical concern in today’s interconnected world. The complexity of supply chains, often involving numerous third-party vendors and partners, creates multiple points of vulnerability. Attackers frequently exploit these weak links to gain access to sensitive systems, making supply chain breaches one of the most significant threats to businesses.
A single compromised vendor can lead to widespread consequences. High-profile incidents, such as breaches targeting essential business platforms, have demonstrated the devastating impact of these attacks. Companies face operational downtime, significant financial losses, and long-term reputational damage. Moreover, the ripple effects of a supply chain breach can extend beyond the organization, disrupting partners and customers alike.
Ensuring supply chain security is no longer just about safeguarding proprietary data. It’s about maintaining customer trust, regulatory compliance, and, ultimately, the continuity of business operations. Organizations must recognize that their security is only as strong as the weakest link in their supply chain.
The Role of Cyber Threat Intelligence in Strengthening Supply Chain Security
Cyber threat intelligence is a game-changer for securing modern supply chains. With the increasing sophistication of attacks, organizations cannot afford to rely on reactive measures. Proactive security, powered by actionable intelligence, is essential for staying ahead of emerging threats.
Threat intelligence empowers businesses to anticipate potential risks by providing real-time insights into the threat landscape. For example, it can help detect suspicious activity across supply chain networks before it escalates into a full-blown attack. Additionally, continuous monitoring of vulnerabilities enables organizations to address weaknesses promptly, minimizing the attack surface.
Advanced threat intelligence tools, like SOCRadar’s Supply Chain Intelligence module, take this a step further by offering a comprehensive view of an organization’s entire ecosystem. These tools allow businesses to:
- Assess risks posed by third-party vendors and partners.
- Monitor supply chain networks for suspicious activities or vulnerabilities.
- Respond swiftly and effectively to incidents, minimizing impact.
By integrating such tools into their cybersecurity strategy, organizations can better protect their supply chains from potential threats. This proactive approach not only enhances security but also builds resilience, ensuring that supply chains remain robust and operational even in the face of challenges.
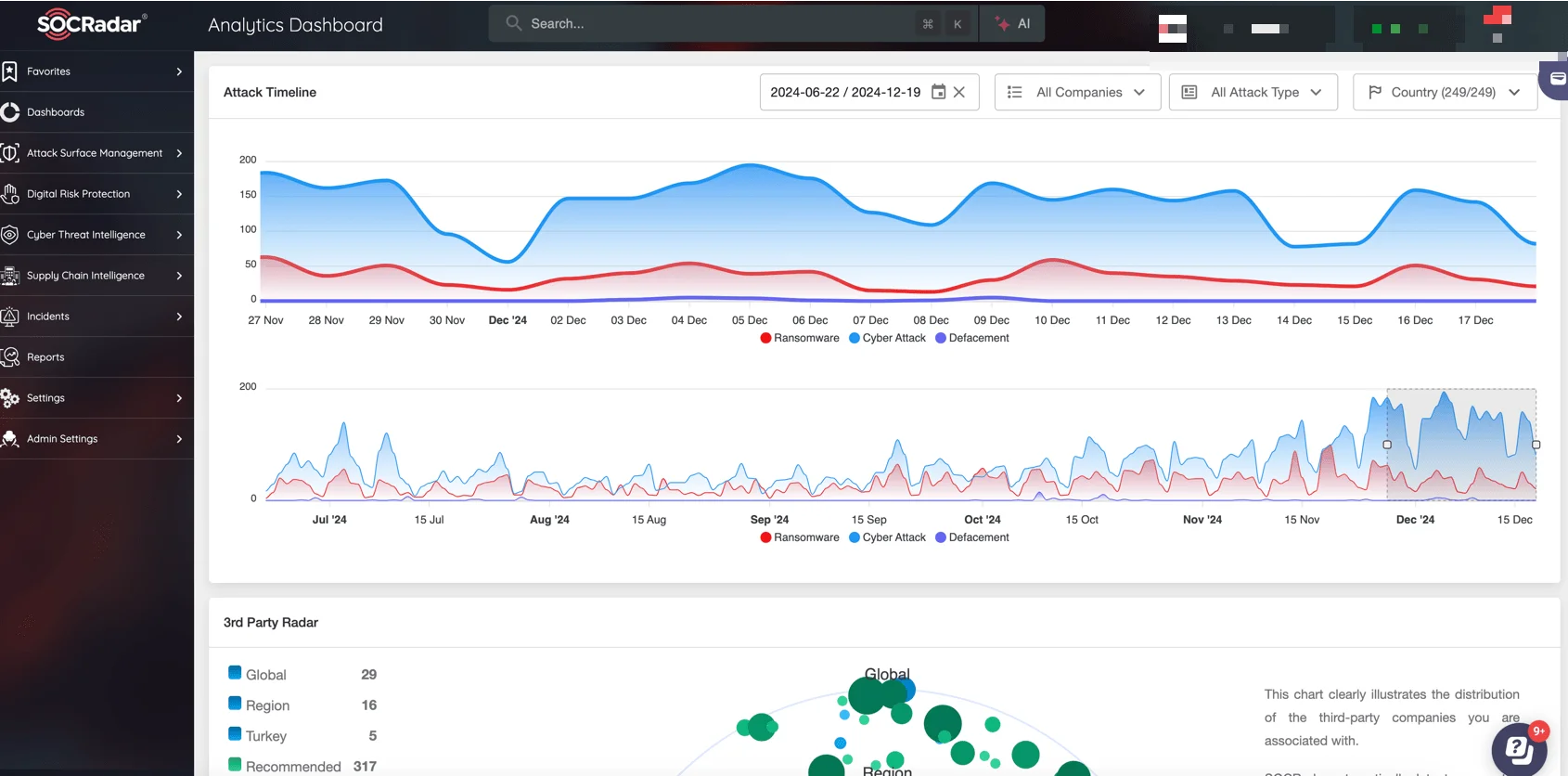
SOCRadar’s Supply Chain Intelligence simplifies third-party mapping, offering full visibility into supply chain activities.
Key Components of Effective Threat Intelligence
Effective supply chain protection requires a holistic approach, combining technology, processes, and collaboration. Here are the expanded components of an effective threat intelligence strategy for supply chain security:
Risk Assessment
A thorough risk assessment is the cornerstone of any effective supply chain security strategy. This involves identifying vulnerabilities across every layer of the supply chain, including third-party vendors, software dependencies, and cloud-based applications. Advanced tools help evaluate risk levels by analyzing historical breaches, misconfigurations, and weak access controls. Continuous re-assessment is essential as new vulnerabilities emerge and supply chain dynamics evolve.
Continuous Monitoring
Real-time threat monitoring is critical in detecting malicious activity before it escalates. Advanced solutions such as machine learning-powered tools and behavioral analytics enable organizations to spot anomalies, such as unauthorized access attempts or unusual API behavior. Continuous monitoring provides actionable insights, allowing for swift response and mitigation to minimize potential damage.
Collaboration with Vendors
Supply chains are inherently interconnected, making collaboration with vendors and partners essential. Sharing threat intelligence across the ecosystem fosters a unified approach to cybersecurity. Establishing clear security expectations through Service-Level Agreements (SLAs), conducting regular security audits, and facilitating real-time information exchange with vendors create a stronger, collective defense against cyber threats.
Zero-Trust Architecture
The zero-trust model, which operates on the principle of “never trust, always verify,” is a critical component of modern supply chain security. By enforcing strict access controls, continuously verifying users and devices, and limiting privileges, organizations can significantly reduce the risk of unauthorized lateral movement within networks. This approach is especially effective in combating insider threats and compromised credentials.
Proactive Threat Hunting
Proactive threat hunting goes beyond traditional monitoring by actively searching for potential threats within the network and across the supply chain. Using tools like AI-driven analytics and leveraging threat intelligence feeds, organizations can identify Indicators of Compromise (IOCs) and respond to emerging risks before they evolve into active attacks.
Incident Response Planning
Preparedness is key to minimizing the impact of supply chain attacks. A well-defined incident response plan ensures that organizations can respond quickly and effectively to breaches. This includes identifying key stakeholders, establishing communication protocols, and conducting regular simulation exercises to test response readiness.
Regulatory Compliance
Many industries have specific regulations and compliance requirements that govern supply chain security. Adhering to frameworks like GDPR, CCPA, or ISO 27001 ensures that organizations maintain a baseline level of security while avoiding potential legal and financial penalties. Compliance efforts also enhance trust with partners and customers.
Employee Awareness and Training
Employees are often the first line of defense against supply chain threats. Regular training on recognizing phishing attempts, secure credential management, and the importance of reporting suspicious activity can drastically reduce human error-related breaches. A culture of cybersecurity awareness empowers the workforce to contribute actively to the organization’s overall security posture.
Technology Integration
Integrating advanced tools like Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), and Supply Chain Risk Management (SCRM) platforms provides a comprehensive defense mechanism. These technologies enable automation, real-time visibility, and streamlined incident response, significantly enhancing overall supply chain resilience.
By implementing these interconnected strategies, businesses can build a robust and adaptable supply chain capable of withstanding sophisticated cyberattacks. Combining proactive measures with continuous innovation ensures that organizations stay ahead of evolving threats in an increasingly complex digital ecosystem.
Implementing Threat Intelligence for Supply Chain Protection
The implementation process begins with assessing the existing security framework and identifying areas of improvement. Advanced tools, such as AI-powered threat detection and response systems, play a vital role in this process. Training employees and third-party vendors is equally important, as human error remains a significant factor in supply chain vulnerabilities.
By leveraging solutions like SOCRadar’s real-time analytics dashboard, organizations can gain immediate visibility into global cyber threats and adjust their defenses accordingly. This level of preparedness ensures the integrity of the supply chain while fostering trust among partners.
Case Studies: Threat Intelligence Enhancing Supply Chain Security
Real-world examples highlight the transformative impact of cyber threat intelligence. A ransomware attack on a third-party logistics provider was thwarted by proactive monitoring and immediate action, protecting sensitive customer data. Similarly, continuous security validation helped another organization detect and mitigate vulnerabilities in its software supply chain, preventing a widespread breach.
One of the most significant examples of a supply chain attack occurred in 2020 with the SolarWinds compromise, which highlighted the devastating impact a single vulnerability can have across interconnected systems. In this incident, malicious actors infiltrated SolarWinds‘ Orion software, embedding a backdoor that allowed unauthorized access to numerous organizations globally, including government agencies and private enterprises.
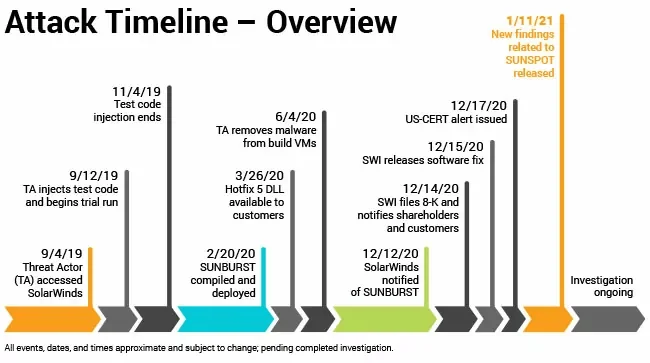
Timeline of the SolarWinds Supply Chain Attack (Source: SolarWinds)
This breach was not just about one company—it underscored how cybercriminals can exploit trusted third-party tools to gain access to sensitive data. The attack went undetected for months, emphasizing the critical need for real-time monitoring and proactive threat detection within the supply chain. Organizations affected had to implement robust measures, such as patching systems, revoking compromised certificates, and adopting zero-trust security architectures to limit the damage.
The SolarWinds case serves as a wake-up call for businesses relying on third-party vendors and APIs. It showcases the importance of cyber threat intelligence in identifying unusual behavior, detecting vulnerabilities early, and enabling swift mitigation. Tools like SOCRadar’s Supply Chain Intelligence module provide real-time visibility and actionable insights, helping organizations stay ahead of such sophisticated threats while maintaining the integrity of their supply chains.
Conclusion
The stakes for supply chain security have never been higher. Cyber threat intelligence offers a comprehensive approach to addressing these challenges, providing organizations with the tools and insights needed to stay ahead of attackers. Solutions like SOCRadar’s Supply Chain Intelligence Module empower businesses to navigate the complex threat landscape with confidence, ensuring operational continuity and safeguarding sensitive information.
By prioritizing supply chain cybersecurity, organizations not only protect their assets but also enhance trust and resilience in an increasingly interconnected world.




































