
The Evolution of Ransomware: From Simple Encryption to Double Extortion Tactics
The evolution of ransomware represents one of the most significant transformations in the cybersecurity landscape over the past three decades. From its humble beginnings in the 1990s as a relatively crude form of digital extortion, ransomware has evolved into a sophisticated, multi-billion dollar threat. What started with the AIDS Trojan in 1989 – a primitive attack that required victims to mail $189 to a post office box in Panama – has morphed into highly coordinated operations employing advanced encryption, double-extortion tactics, and cryptocurrency payments.
This dramatic evolution reflects not only technological advancement but also the changing nature of cybercrime itself, as opportunistic individuals have given way to professional criminal enterprises operating with business-like efficiency. Through examining key ransomware strains and watershed moments from the 1990s to 2024, we can trace how this threat has fundamentally reshaped cybersecurity practices and forced organizations to rethink their approach to data protection.
The Origins of Ransomware: The AIDS Trojan
With the introduction of the AIDS Trojan, often referred to as PC Cyborg, in 1989, ransomware first appeared. This was the world’s first recorded instance of ransomware. The Trojan was sent to participants in the worldwide AIDS conference held in Stockholm by the World Health Organization using 20,000 contaminated floppy disks. The malware was created by Dr. Joseph Popp and was inserted in an AIDS questionnaire that was on the disks.
The software seemed innocent at first, but after 90 reboots, the malware encrypted file names and showed a demand for ransom. In order to restore access to their systems, victims were told to deposit $189 to a P.O. Box in Panama. Although the attack was novel at the time, it was archaic by today’s standards. It was problematic for victims to comply because the ransomware encrypted file names rather than their contents and the payment methods depended on overseas money orders.

AIDS Ransomware ransom note
Although few victims paid the ransom, the attack attracted a lot of attention due to its influence rather than its financial success. In some cases, victims lost important research data as a result of erasing and rebuilding their computers. Thankfully, a decryptor was created that allowed victims to retrieve their files without having to pay.
Even though the AIDS Trojan was a groundbreaking cyber attack, it was still a singular occurrence. In the 1980s and 1990s, ransomware was not a common danger because there were few digital payment choices and no extensive interconnected networks. These years were crucial for the malware’s development, laying the groundwork for later decades’ more advanced and destructive ransomware efforts.
The Early Days of Ransomware Evolution (2004–2007)
2004–2005
A significant turning point in the history of ransomware occurred in the early 2000s, when GPCoder became a prominent forerunner of contemporary ransomware outbreaks. GPCoder was discovered in 2005 and encrypted important data files, including databases, spreadsheets, and documents. Its tactics included placing ransom notes in impacted directories requesting a $200 payment by Western Union or premium text messages, even though it wasn’t officially classified as ransomware at the time. This strategy laid the groundwork for upcoming ransomware attacks.
2005–2006
The use of RSA asymmetric encryption was a major advance introduced by Archievus in 2005. It only affected files in the “My Documents” folder, and in order to decrypt their data, victims had to pay certain purchases. In its thorough instructions, Archievus cautioned victims against depending on outside assistance or system backups, reiterating themes that are still present in ransomware emails today. Despite its technological advancements, its influence was restricted by a crucial design flaw: all victims were given the same decryption password.
2007: The Emergence of Locker Ransomware
Locker ransomware variations were introduced in 2007, dramatically changing the ransomware battlefield. These attacks, in contrast to encryption-based strains, sought to completely lock victims out of their devices by turning off necessary features like the keyboard and mouse. These variations, which frequently targeted Russian users, coerced victims into complying by using aggressive tactics, such as showing adult images. Early ransomware developers used a variety of monetization techniques, as seen by the requests for payment made via premium-rate phone calls or SMS messages.
Cryptocurrencies and RaaS
Threat actors have continuously changed as cybercrime has developed in order to boost revenues and avoid discovery. Vundo, a ransomware that encrypted victims’ files and demanded payment to decrypt them, first surfaced in 2009.
The emergence of cryptocurrency in 2010 further changed the game by giving criminals a decentralized, frequently untraceable way to make payments. Because it allows for instantaneous cross-border payments, Bitcoin in particular became the currency of choice for ransomware, making it more difficult for law enforcement to trace down illegal activities.

A guy in a hoodie holding bitcoin, generated by ImageFX
With the introduction of Ransomware-as-a-Service (RaaS) in 2012, the ransomware business model grew. This approach was first used by the Reveton ransomware, which pretended to be law enforcement and threatened victims with legal repercussions unless they paid the ransom. This development not only made it easier for ransomware to spread, but it also made it easier for new hackers to enter the market by lowering the technical obstacles.
Scareware was a profitable strategy that year. Scareware, in contrast to conventional ransomware, used psychological manipulation to demand money in order to evade alleged punishment and display fictitious law enforcement warnings. Scareware is a distinct phenomenon in the cybercrime ecosystem, although having similar intentions to ransomware. This is due to its reliance on deception based on fear.
To read more about the relationship between cybercrime and cryptocurrencies, you can visit our blog The Intricate Relationship Between Cybercrime and Cryptocurrency.
Ransomware is on the Rise
Ransomware underwent substantial change between 2013 and 2016, which led to the rise of contemporary ransomware as a recurring worldwide threat. Ransomware attacks grew in scope at this time, targeting not only Windows computers but also other operating systems and various devices. The introduction of CryptoLocker, a ransomware strain that illustrated the destructive power of encryption-based extortion, was significant in 2013. CryptoLocker, which was distributed by botnets and phishing emails, locked victims’ files using public-private key encryption and required payment within a short time frame, initially $300 in Bitcoin or MoneyPak.
With CryptoLocker, ransomware underwent a sea change. In terms of implementation, it served as a model for ransomware variants to come. The FBI believed victims had paid more than $27 million by the end of 2015. The creation of ransomware exploded as a result of this amount, and in the years that followed, many variations emerged.
The emergence of CryptoLocker also demonstrated the expanding cooperation between cybersecurity companies and law enforcement. The infrastructure supporting CryptoLocker was taken down in 2014 by a multinational operation that included private businesses and organizations including US-CERT and Europol. Its operator, Evgeniy Mikhailovich Bogachev, a Russian national, was charged but not caught, yet the takedown greatly reduced the impact of CryptoLocker.
The CryptoLocker era demonstrated the versatility and tenacity of ransomware perpetrators, as well as the vital necessity of international collaboration in order to successfully battle cybercrime. Even if the initial strain was eliminated, the fundamental strategies it brought about still influence ransomware activities today.
With major strains like Locky and Petya signifying notable developments in both scale and sophistication, ransomware had become a formidable cyberthreat by 2016. When Locky was initially revealed that year, it immediately became well-known for its aggressive distribution strategies, which included extensive phishing efforts.
A paradigm leap in ransomware functionality was brought about by Petya. Petya targeted the Master Boot Record (MBR) and the Master File Table (MFT), in contrast to its predecessors, which mostly encrypted individual files. It showed that it could more successfully render organizations inoperable by preventing victims from accessing their entire system, and it demanded larger ransoms in exchange for access being restored.
Other ransomware outbreaks like Cerber, TeslaCrypt, and Jigsaw also proliferated at this time, which helped make 2016 known as “the year of ransomware.” These variations indiscriminately infected computers by taking use of flaws in phishing tactics, exploit kits, and malicious ads. All of these actions combined to drive the ransomware economy, and for the first time, the total amount of extortion payments may have surpassed $1 billion USD.
Government Actors are on the Stage: NotPetya and WannaCry
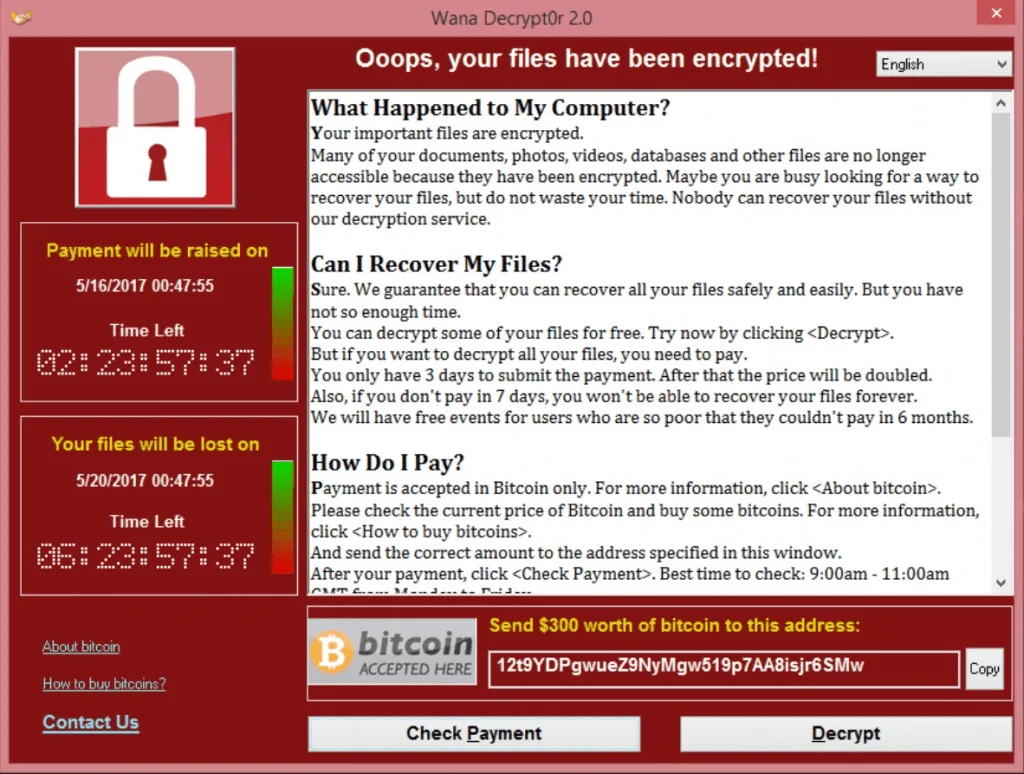
WannaCry ransom note
Another significant turning point in the development of ransomware and its wider ramifications for cybersecurity and geopolitics was the events of 2017. The devastating potential of ransomware was demonstrated by two well-known instances, WannaCry and NotPetya, which also brought a new level of sophistication to cyber operations, including state-sponsored initiatives.
After infecting hundreds of thousands of systems across more than 150 countries, WannaCry quickly gained international attention. WannaCry spread on its own as a worm by using the EternalBlue exploit, a flaw in Microsoft’s Server Message Block (SMB) protocol that was released by the NSA. Security researcher Marcus Hutchins discovered a kill switch, which stopped the attack’s spread and lessened its impact despite its worldwide reach. Because there were no working decryption keys, users were unable to recover their data. By the end of the year, several governments had blamed WannaCry on North Korea, underscoring its significance as a precursor to ransomware in state-sponsored cyberattacks.
In a very short time, NotPetya appeared with a radically different goal but a superficially similar method of operation. Although it was disguised as ransomware, it was more of a wiper, making data unrecoverable even if the ransom was paid. Along with other flaws, the assault took advantage of EternalBlue. It was disseminated through a hacked update for M.E.Doc, a popular accounting program in Ukraine. Initially focusing on Ukrainian infrastructure, such as the financial, energy, and government sectors, NotPetya swiftly expanded beyond Ukraine and interfered with many businesses’ international operations. Under the pretense of financial extortion, malware could be used as a tool for geopolitical disruption, as demonstrated by the attack’s early 2018 attribution to Russian state actors.
These events highlighted important developments in cybersecurity. They showed how vulnerabilities that were initially created for intelligence reasons may be turned into weapons and used globally. Furthermore, a time when cyber technologies were essential to international conflict and strategy was heralded by the blurring of the boundaries between state-sponsored operations and regular cybercrime. NotPetya highlighted ransomware’s potential for wider geopolitical impact, changing how countries and businesses viewed cybersecurity in the years that followed, while WannaCry made ransomware a widely recognized issue.
If you are curious about state-sponsored cybercrime, we collected other notable state-sponsored actions here.
Ransomware Operators Targeting Big Players
By 2018, ransomware operations had progressed from indiscriminate attacks to more targeted high-value entities, including transportation networks, healthcare providers, state and local governments, and industrial companies. This change, which is sometimes called “big game hunting,” signaled a strategic flip in which attackers targeted organizations with significant resources and vital operations in an effort to increase their earnings. The ensuing effects on the affected firms were severe and included financial pressure, reputational damage, and operational difficulties.
At about the same time, different data exfiltration techniques were included into ransomware strategies, making them more complex. Strains like GrandCrab RaaS, which combined file encryption with data extortion abilities, served as prime examples of this progression. Before encrypting the victim’s systems, attackers used these tools to extract credentials, private files, screenshots, and other important data, increasing the threat and possible leverage for ransom demands.
Explore SOCRadar’s Ransomware Intelligence module and gain comprehensive insights with detailed group profiles, MITRE Visualizer, and actionable IOCs. These insights will empower you to stay ahead of evolving threats and enhance your cybersecurity strategy.
Explore SOCRadar’s Ransomware Intelligence module
Emergence of Double Extortion Techniques
The Maze ransomware started using double extortion even more. In addition to encrypting the victims’ files, this strategy included stealing private information and threatening to release it until a further ransom was paid. Because even businesses with strong recovery systems ran the risk of their stolen data being made public, this innovation made standard backup plans inadequate. Other ransomware groups soon adopted the strategy, which increased the pressure on victims to abide by the demands of the ransom.
Between 2019 and 2020, specific leak sites started to appear on the dark web as part of this development. These platforms increased the financial and reputational harm done to victims by acting as open repositories of stolen data. Leak sites gave cybersecurity researchers useful insight that allowed them to track ransomware activities and target organizations, even if they also encouraged more attacks by disclosing credentials and private data.
Double or Triple Extortion?
By 2020, ransomware strategies have advanced further with the introduction of “triple extortion.” By adding additional levels of pressure, such as focusing on the people whose data was stolen or threatening secondary assaults like distributed denial-of-service (DDoS) operations, this tactic expanded on double extortion. A shift toward attacks on critical infrastructure was also signaled by the emergence of ransomware that targets industrial control systems (ICS) and operational technology (OT), such as the EKANS (Snake) malware.
SOCRadar’s Advanced Dark Web Monitoring equips organizations with vital insights into hidden threats targeting key industries such as finance, insurance, and information technology, which have faced significant risks over the past year. By providing real-time monitoring of underground chatter and sensitive data exposure, SOCRadar empowers proactive defenses against Dark Web threats.
Activate your free trial today to safeguard your organization’s most valuable assets.
SOCRadar’s Advanced Dark Web Monitoring
LockBit and Increase in RaaS
RaaS ransomware significantly changed by 2020, with organizations like LockBit serving as prime examples. By making it possible for thieves with different levels of expertise to rent advanced tools and infrastructure, this strategy “democratized” ransomware operations. The robustness of RaaS ecosystems guaranteed quick recoveries and ongoing attacks even in the face of law enforcement’s victories, such as taking down LockBit’s website. Because of the flexibility these platforms promoted, affiliates were able to introduce new ransomware strains with no interference.
For more information on LockBit, you can visit Dark Web Profile: LockBit 3.0 Ransomware.

Lockbit Shutdown Image
Concurrently, the Conti ransomware prioritized data exfiltration over encryption, redefining extortion tactics. Since 2020, they have frequently used network intrusion, sensitive data theft, and the fear of public exposure to compel payments. This approach worked well because businesses had to deal with increased financial demands as well as reputational and regulatory issues.
The 2021 attack on the Colonial Pipeline illustrated the serious real-world repercussions of ransomware. Widespread gasoline shortages resulted after the six-day suspension of a vital energy pipeline, highlighting the vulnerability of vital infrastructure. The ransom payment brought to light the challenging choices that companies must make when under pressure, weighing the possibility of giving attackers more confidence against the need to restore operations.
Colonial Pipeline, Source
New Criminal Business: Initial Access Brokers
Significant advancements in the strategies and frameworks enabling ransomware operations were observed in the cybercriminal ecosystem by the early 2020s. RaaS expansion was made possible by the emergence of Initial Access Brokers (IABs) as key actors. IABs simplified operations for well-established ransomware gangs and reduced hurdles for novice attackers by selling access to hacked networks. The ransomware landscape evolved quickly as a result of this collaboration, which freed up threat actors to concentrate on more effectively launching and controlling their assaults.
In 2023 double extortion as well as triple extortion became even more popular. Distributed denial-of-service (DDoS) attacks and even regulatory exploitation, such reporting breaches to the SEC to put pressure on victims, were popular for the attackers in addition to data encryption and threats of public disclosure. Because of these multifaceted tactics, ransomware attacks became more complex, forcing defenses to deal with adversaries who were becoming more creative and resourceful.
The operational models of ransomware also underwent change. Threat organizations changed their identities and implemented more efficient payment methods in an effort to avoid penalties. Many took a businesslike approach to their harmful activities by implementing customer support-like procedures, such as self-service help desks, to improve victim compliance. These patterns highlight the ongoing rise in ransomware operations’ organizational maturity and technical sophistication.
SOCRadar researchers also conducted an in-depth analysis of initial access brokers. To read it, you can visit our blog post here.
The Future
The tactics used by the ransomware evolution have changed significantly as a result of increased pressure from global law enforcement and sophisticated cybersecurity safeguards. Recent events demonstrate a more active and flexible strategy to get over these obstacles.
By the end of 2023, prominent ransomware organizations had changed their strategies to stay profitable and put pressure on their victims. This involved taking advantage of regulatory frameworks, utilizing public disclosures, and implementing novel negotiation techniques. For example, strategies like as focusing on insurers or taking use of third-party disclosures show a tendency to minimize dependence on direct ransom payments and maximize impact.
Additionally, an increasing emphasis on multi-stage extortion tactics was evident in the latter months of 2023. After the hack, groups like Royal and Akira intensified their attacks in an effort to obtain more control over their victims. Similar to this, AlphV showed a readiness to spread threats outside of the main target, indicating a larger trend in ransomware ecosystems toward more inventive and expansive forms of extortion.
The development of ransomware techniques emphasizes how important it is for businesses to stay on guard against breaches as well as to be ready for the sophisticated and enduring threats that may surface years after the first compromise.
Hyper-targeted, multi-layered extortion attempts powered by AI-driven automation and reconnaissance will become more prevalent in ransomware in the future. Threat actors will progressively take advantage of new weaknesses in operational technology systems and the Internet of Things, particularly in supply chains and key infrastructure, which will have a domino impact on entire industries.
In an effort to undermine the ransomware business, governments will enforce more stringent laws regarding ransom payments and reporting, possibly making payouts illegal.
However, the widespread use of AI technologies will be the most significant development. The ransomware landscape will become more complex as AI models become the foundation of future applications.





































