
Dark Peep #18: If It’s Easy for You, It’s Easy for Hackers
Some dark web stories are scary, some are shocking, and then there are the ones that make you go “Wait… what?” This is one of those.
In this edition, cybercriminals never seem to run out of surprises, and this time, they’ve been especially creative—or just incredibly lazy. From ransomware gangs raising their own “taxes” to scammers playing musical chairs with Telegram usernames, the dark web has been buzzing with activity. Meanwhile, crypto fraudsters are hijacking X accounts, and an insider claims they can swap phone numbers like trading cards. Oh, and let’s not forget IntelBroker, who just stepped down as BreachForums owner right before the FBI came knocking on other forums’ doors—pure coincidence, right?
It’s been a busy few weeks in the cybercrime world, and as always, if it’s easy for you, it’s easy for hackers.

Hacker thought it would be easy—turns out, not that easy (Generated By DALL-E)
RansomHub’s New Business Model: Pay More, Get… the Same?
It’s that time again—price hikes, but in the ransomware industry. RansomHub has just announced an earth-shattering change: increasing its own cut from ransom payments, bumping it up from 10% to 15%. Affiliates, once enjoying a generous 90% share, will now have to settle for 85%.
So, what do they get in return for this extra 5% cut? Absolutely nothing. It’s the “pay more for the same service” business model in full effect.
In other words, RansomHub is boosting its revenue without offering anything extra in return. Inflation has officially hit the cybercrime economy. At this rate, ransomware gangs might start considering unionizing.
RansomHub: A Global Gang or Just Another Russian Operation?
RansomHub claims to be a collective of hackers from around the world, but its operations suspiciously resemble a traditional Russian ransomware setup. Coincidence? Maybe… maybe not.
- Attacks on CIS countries, Cuba, North Korea, and China are strictly off-limits.
- Their list of targeted companies closely mirrors those of other Russian ransomware groups.
- The “Right Protection” section enforces strict affiliate rules, warning that breaking agreements will result in bans.
RansomHub keeps its affiliates on a tight leash, but will they stick around after this pay cut? Or will they jump ship to rival Ransomware-as-a-Service (RaaS) groups offering better deals? Even in the dark web underworld, free market competition is alive and well.
A Breach or Just Poor Security? Price Hikes and Effortless Breaches
Fresh off the news that RansomHub increased its ransom collection fee from 10% to 15%, the group claims to have breached Highland Park Independent School District in Dallas, Texas, and Wayne-Westland Community School District in Metro Detroit, Michigan. But if their latest statement is to be believed, they didn’t exactly have to break a sweat.
“Everyone knows that the password is ‘password’ and one shared account for all staff… Thank you for making our job so easy.”
According to RansomHub’s claims, this wasn’t a sophisticated ransomware attack, nor did it require advanced malware or zero-day exploits. Instead, they suggest that weak authentication practices opened the door for them. Whether this was due to a credential compromise from a stealer log, a phishing attack, or simple social engineering remains unclear.
A Lesson in Cybersecurity: If It’s Easy for You, It’s Easy for Hackers
While it’s tempting to be critical, many organizations still struggle with identity security. Shared credentials and weak passwords are common pitfalls, and in sectors like education, where IT resources can be stretched thin, security often takes a backseat to accessibility.
This is where proactive credential monitoring becomes crucial. SOCRadar’s Identity & Access Intelligence module provides a strong solution to detect and mitigate credential compromise risks before they escalate into full-blown security incidents. With this module, organizations can:
- Identify Compromised Credentials: Track exposed credentials across data leaks, stealer logs, and the dark web.
- Mitigate Security Risks: Take action before threat actors exploit stolen login information.
A Wake-Up Call, Not Just a Breach
If RansomHub’s claims are accurate, this incident highlights how crucial identity security is—not just for preventing ransomware, but for stopping unauthorized access in the first place. Whether the attack stemmed from leaked credentials, a phishing scheme, or poor security practices, one thing is clear: strong authentication measures and proactive monitoring are essential in today’s threat landscape.
LockBit’s Love Letter to the FBI: A Birthday Wish or a Threat?
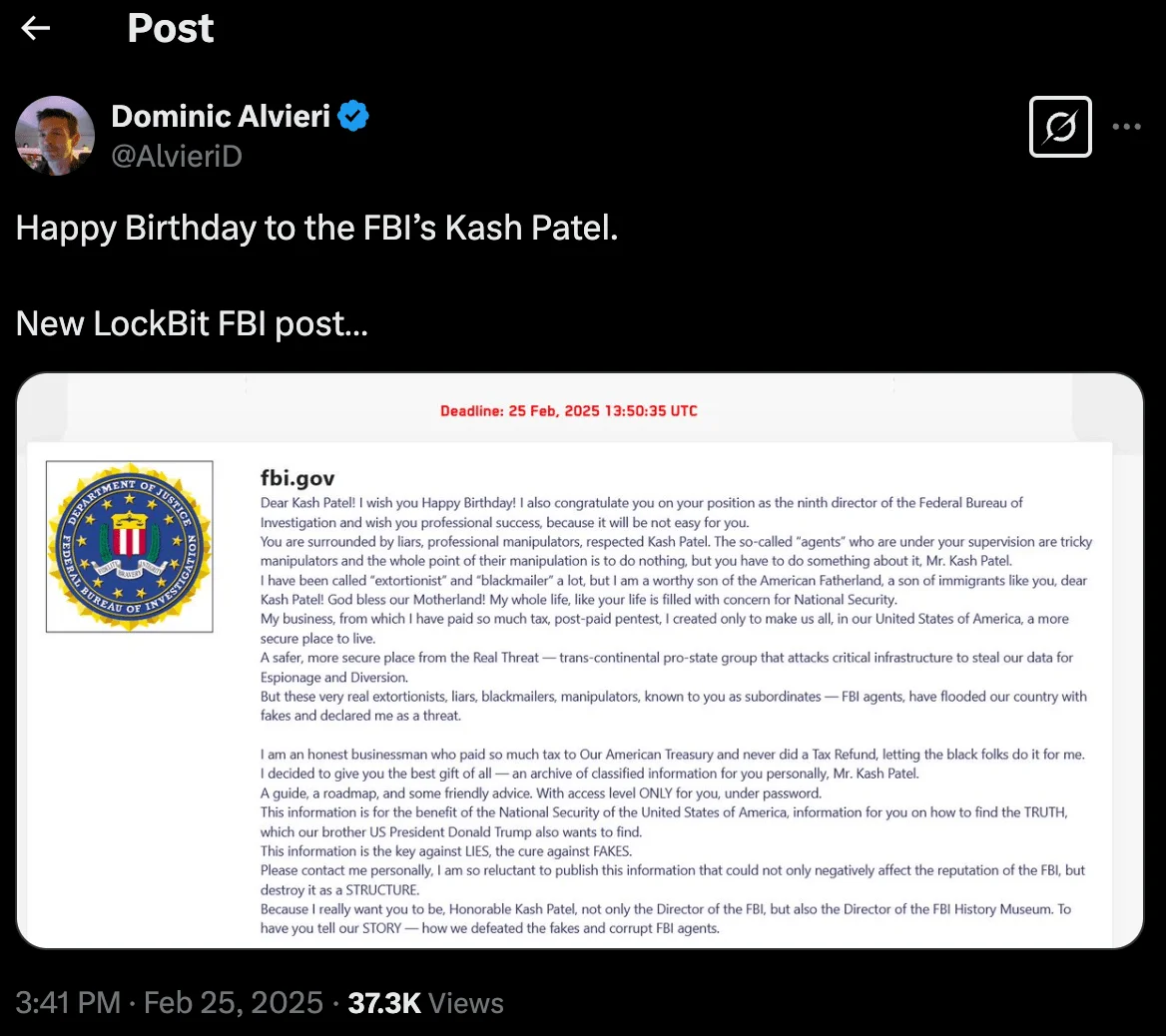
LockBit’s statement
The LockBit ransomware gang has targeted new FBI Director Kash Patel with a bizarre message, claiming to have “classified information” that could “destroy” the agency.
Disguised as a birthday greeting, the message accuses FBI agents of deception while portraying LockBit as a legitimate “business.” To back their claims, they uploaded a password-protected archive allegedly containing sensitive data.
Whether this is a real leak or just another ransomware publicity stunt, LockBit’s goal remains the same—to create chaos and spread fear.
Telegram Username Sniping: Cybercriminals Playing Musical Chairs
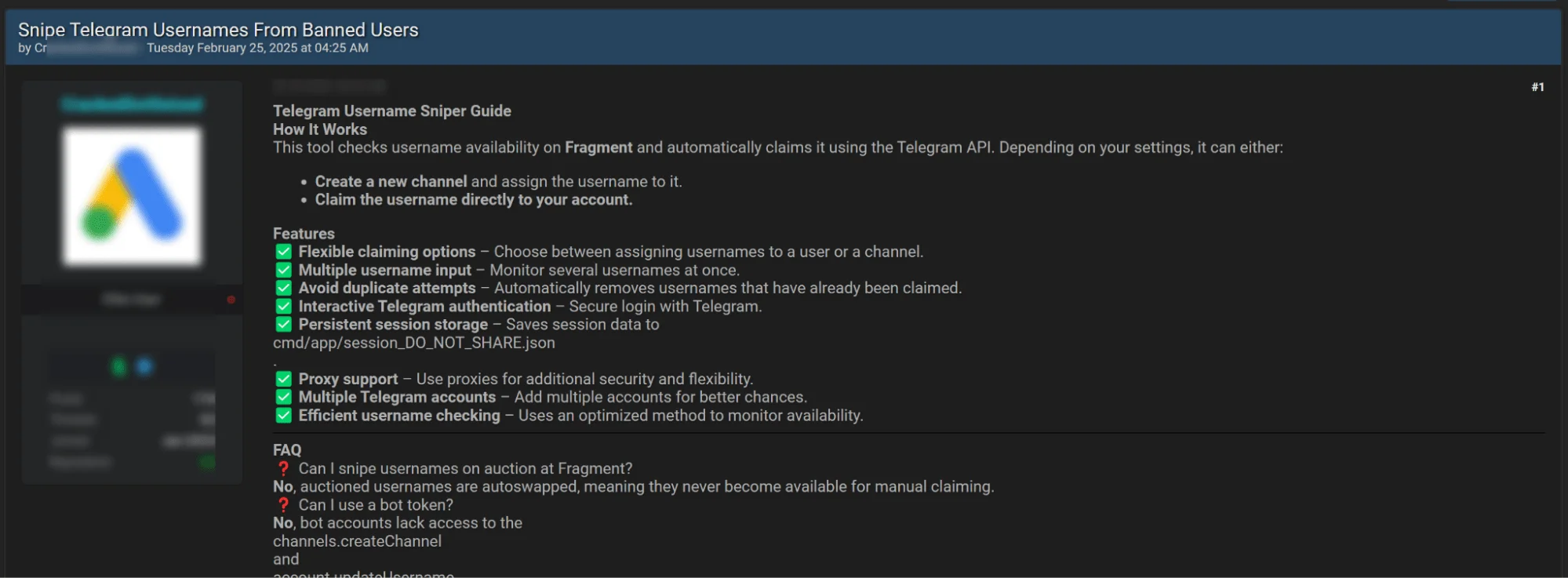
Hacker forum post about the tool that snipes Telegram usernames from banned users, detailing its features and usage.
Picture this: a game of musical chairs, but instead of chairs, it’s Telegram usernames, and instead of kids, it’s cybercriminals racing to snatch up abandoned identities. The moment someone gets banned or disappears, hackers swoop in like vultures on a fresh meal.
A threat actor has shared a tool that automates this username scavenging, claiming names from banned users via the Telegram API. No need for skill or effort—just set it up, wait, and profit. The best part? They don’t even need to hack anything; they’re just taking what’s left behind.
And the business model? Simple. Steal a name, impersonate the original user, scam people, or sell it off to the highest bidder. It’s digital identity theft with zero effort—the cybercrime version of finding a lost wallet and keeping the cash.
Crypto Scammers Hijack X Accounts—Even Tor Couldn’t Escape
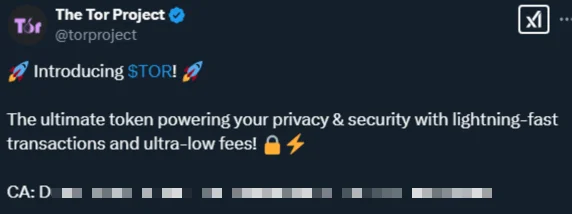
Compromised Tor Project X account promoting a fake $TOR cryptocurrency
Crypto scammers are hijacking major X accounts to push their schemes, and the latest victim list includes Time, NASA, and The Tor Project. Because nothing says “trust this crypto contract” like a hacked account suddenly promoting it.
Insider SIM Swap
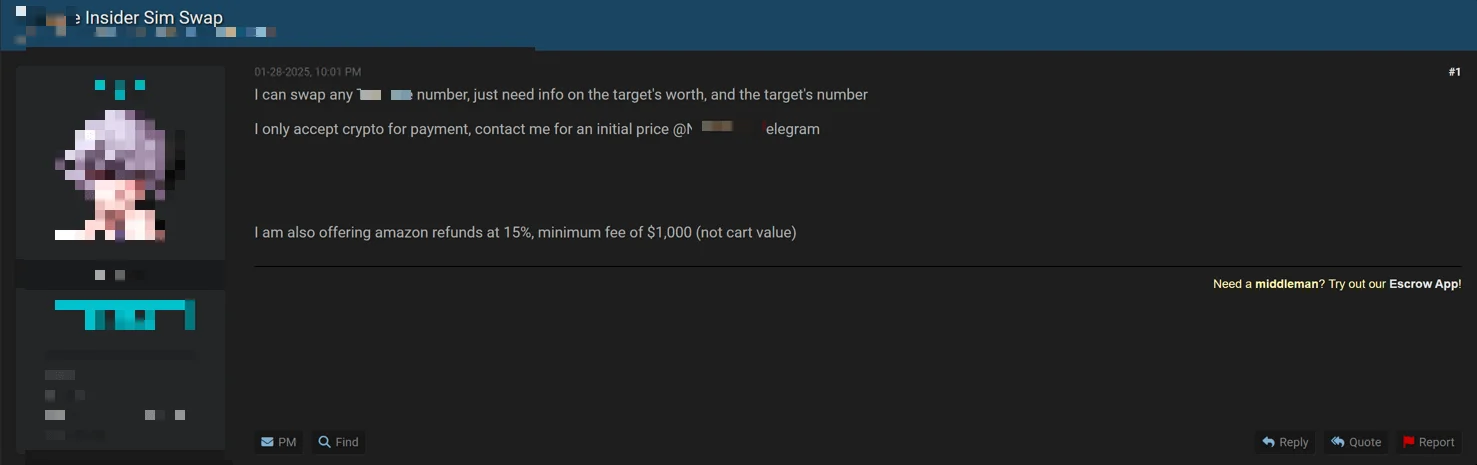
Dark web post advertising insider SIM swap services for a major telecom provider.
A certain widely used telecom provider, operating across the U.S. and multiple countries in Europe, seems to have an insider problem. A threat actor confidently claims, “I can swap any number,” as long as you provide the target’s phone number and their financial worth. No need for fancy hacking—just a well-placed insider flipping SIMs like pancakes. Payment? Crypto only—because even fraudsters don’t trust chargebacks.
French IDs for Sale—Or Just Another Cybercrime Mirage?
Hacker forum post advertising a French ID card generator for the highest bidder
A new threat actor on a hacker forum claims to have a French identity card generator, ready to go to the highest bidder. The catch? No samples, no proof, just vibes. Whether this is the next big forgery tool or just another scammer selling thin air, one thing’s for sure—someone’s about to make a very questionable investment.
IntelBroker Steps Down as BreachForums Owner—Just Bad Timing or Something More?
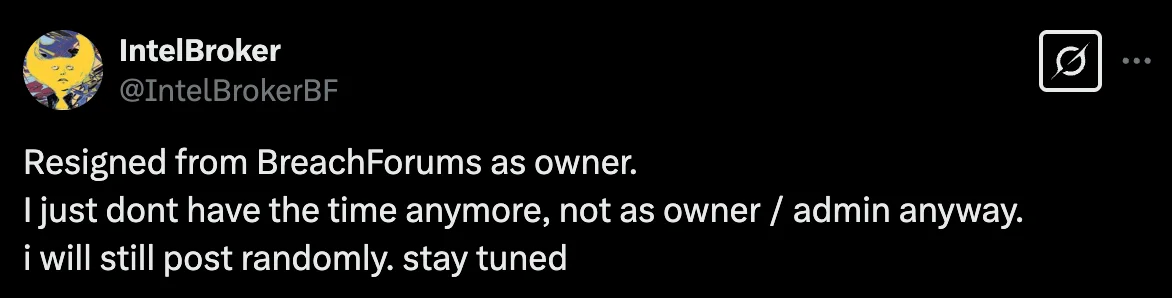
IntelBroker’s statement
In the last days of January, IntelBroker threat actor announced they were stepping down as the owner of BreachForums, claiming “I just don’t have time anymore.” Because, of course, running a cybercrime forum is just another commitment you drop—like an abandoned side project or that online course you swore you’d finish.
But the timing is… interesting. This decision came right after ShinyHunters returned to the forum, though oddly not as the new owner. Even more curious? It happened just days before the FBI’s Operation Talent, which took down Cracked.io and Nulled.to in a global cybercrime crackdown.
So, was this a simple case of losing interest, or did they see the storm coming and decide to take a step back? IntelBroker says they’ll still “post randomly”—only time will tell if they stick around or quietly disappear.





































