Inside the Minds of Hackers: Using Dark Web Intelligence to Supercharge Pentesting & Red Teaming
In 2024, cybersecurity threats surged to unprecedented levels, with the average cost of a data breach climbing to nearly $5 million – a 10% increase over the previous year. From phishing attacks to credential theft, the reality is clear: it’s no longer a matter of if an organization will face a breach, but when.
Despite heavy investments in firewalls, endpoint protection, and compliance audits, traditional security strategies often fall short. Why? Because attackers aren’t using playbooks; they’re adapting, evolving, and using unconventional methods to exploit gaps that conventional defenses overlook. Penetration Testing and Red Teaming, once the cornerstone of proactive security, also risk becoming predictable if they rely solely on standard tools and hypothetical attack scenarios.
That’s where Dark Web Intelligence changes the game. By tapping into real-world data from stealer logs, ransomware leaks, hacker forums, and exposed credentials, security teams can simulate the exact tactics adversaries use. This approach isn’t just smarter, but also more authentic, actionable, and effective. It enables organizations to assess their defenses through the eyes of an attacker, turning threat intelligence into a force multiplier for Pentesting and Red Teaming efforts.
The Shift from Traditional to Intelligence-Driven Security
Cyber threats are evolving faster than ever. As we mentioned, in 2024, the average cost of a data breach hit $5 million, marking a significant financial burden for businesses across all sectors. But the price tag doesn’t stop at incident response, it extends to long-term consequences like damaged reputation, eroded customer trust, and stiff regulatory penalties.
Why Cyber Threat Intelligence is Critical Today
While Pentesting and Red Teaming remain essential components of any cybersecurity strategy, relying solely on these traditional methods often leads to blind spots. Structured assessments may identify known vulnerabilities or misconfigurations, but they typically operate within a predefined scope, leaving hidden assets, unconventional attack paths, and real-world tactics unexplored.
Want to make Red Teaming feel like a real adversary is at the gates? The SOCRadar Threat Hunting module helps you do just that. By pulling in data from stealer logs, combo lists, and underground chatter, it uncovers attack patterns and emerging threats. Think of it as your offensive security team’s intel arm – ready to help you strike first, rather than only react.
How Threat Actors Stay Ahead & Why You Should Too
Threat actors aren’t confined by rules or tools; they innovate constantly. From exploiting leaked credentials and exposed APIs to weaponizing public documents, they target organizations using techniques that evolve faster than most defenses. The Dark Web, in particular, offers them a treasure trove of data: stealer logs, ransomware leaks, exposed configurations, and insider insights.
Security teams must adopt the same mindset. Dark Web Intelligence allows defenders to proactively identify risks that traditional tools miss, like exposed credentials, subdomains, or misconfigured third-party services. It flips the script: instead of waiting for a breach, organizations can anticipate where it might happen and simulate those scenarios in controlled environments.
Turning these insights into action is key to staying ahead of potential threats, and that’s exactly where SOCRadar’s Advanced Dark Web Monitoring makes a difference. It shines a light on hidden threats targeting industries like finance, insurance, and IT, offering real-time alerts on underground activity and sensitive data leaks. Activate your free demo today and stay one step ahead of your adversaries.
And if you’re wondering whether your organization’s data has already been compromised, don’t guess; run a Free Dark Web Report with SOCRadar Labs. In seconds, you’ll find out if your sensitive information is circulating in hacker forums, leak sites, or Telegram channels.
Penetration Testing vs. Red Teaming & Where They Fall Short
Pentesting and Red Teaming serve different purposes, but both can fall short without real-world context. To truly test defenses, simulations need to reflect how attackers actually operate today.
The Pentesting Playbook: Strengths & Weaknesses
Penetration Testing (Pentesting) is a critical security assessment method designed to uncover vulnerabilities before attackers do. It typically involves ethical hackers using structured methodologies and specialized tools like Metasploit, SQLMap, Nessus, Cobalt Strike, BEEF, and Burp Suite to identify misconfigurations, unpatched systems, and security gaps.
However, Pentesting operates within a defined scope, often following a checklist-based approach that prioritizes compliance and known vulnerabilities. While effective for identifying technical flaws, it struggles to replicate the unpredictability of real-world cyber threats, where attackers don’t follow a predefined playbook. Threat actors evolve constantly, leveraging new tactics, tools, and exposed data that traditional Pentesting often fails to account for.
Red Teaming: Thinking Like an Adversary
Red Teaming takes a more adversarial approach by simulating real-world attack scenarios rather than just identifying vulnerabilities. Instead of working within fixed parameters, Red Teams act as actual threat actors would – deploying tactics such as:
- Spear-phishing campaigns to gain initial access.
- Credential stuffing & password spraying using real leaked data.
- Lateral movement & privilege escalation to expand access.
The key difference? Red Teams don’t just look for vulnerabilities – they test an organization’s ability to detect, respond to, and recover from attacks. However, for these simulations to be truly effective, they need real-world intelligence and not hypothetical threats.
That’s where Dark Web leaks and hacker forums come into play. By leveraging stolen credentials, exposed subdomains, and insider discussions from underground communities, Red Teams can design highly realistic attack scenarios. Instead of relying on assumptions, they can use actual compromised data to mirror the exact techniques that adversaries would use in a real breach.
How Dark Web Intelligence Elevates Pentesting & Red Teaming
Tapping into Dark Web intelligence gives security teams a clearer view of what attackers already know. From leaked credentials to forgotten subdomains, it transforms simulations into reality checks.
Finding Exposed Credentials Before Hackers Do
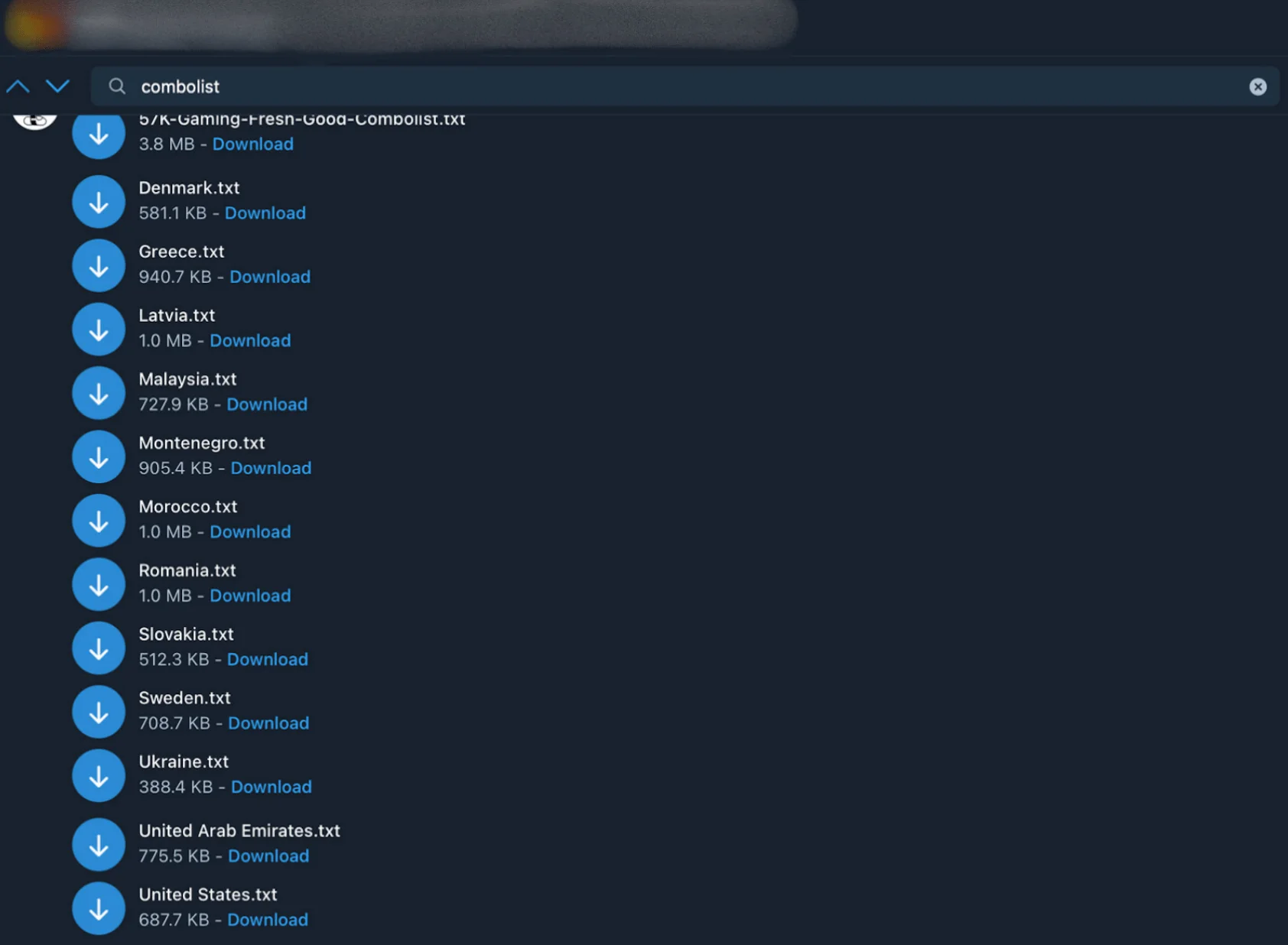
Stealer logs and combo lists from Dark Web marketplaces provide a direct glimpse into real-world compromises. These logs contain credentials, browser histories, system configurations, and more – offering insights into the exact tools and data attackers use to breach organizations.
For Pentesting and Red Teaming, this data is gold. Imagine discovering a combo list with emails like [email protected] and passwords like 123ExampleJosh! – a clear sign of weak credential hygiene. This not only exposes individual accounts but also reveals systemic weaknesses, like flawed Active Directory policies or predictable naming conventions.
With this information, security teams can create customized wordlists tailored to the target organization. Platforms like LinkedIn and Hunter.io help map employee structures, while public combo lists can be filtered to find reused corporate credentials. A simple Python script can then turn this raw data into a targeted wordlist, powering realistic simulations that closely mimic actual attacks.
Uncovering Hidden Attack Surfaces
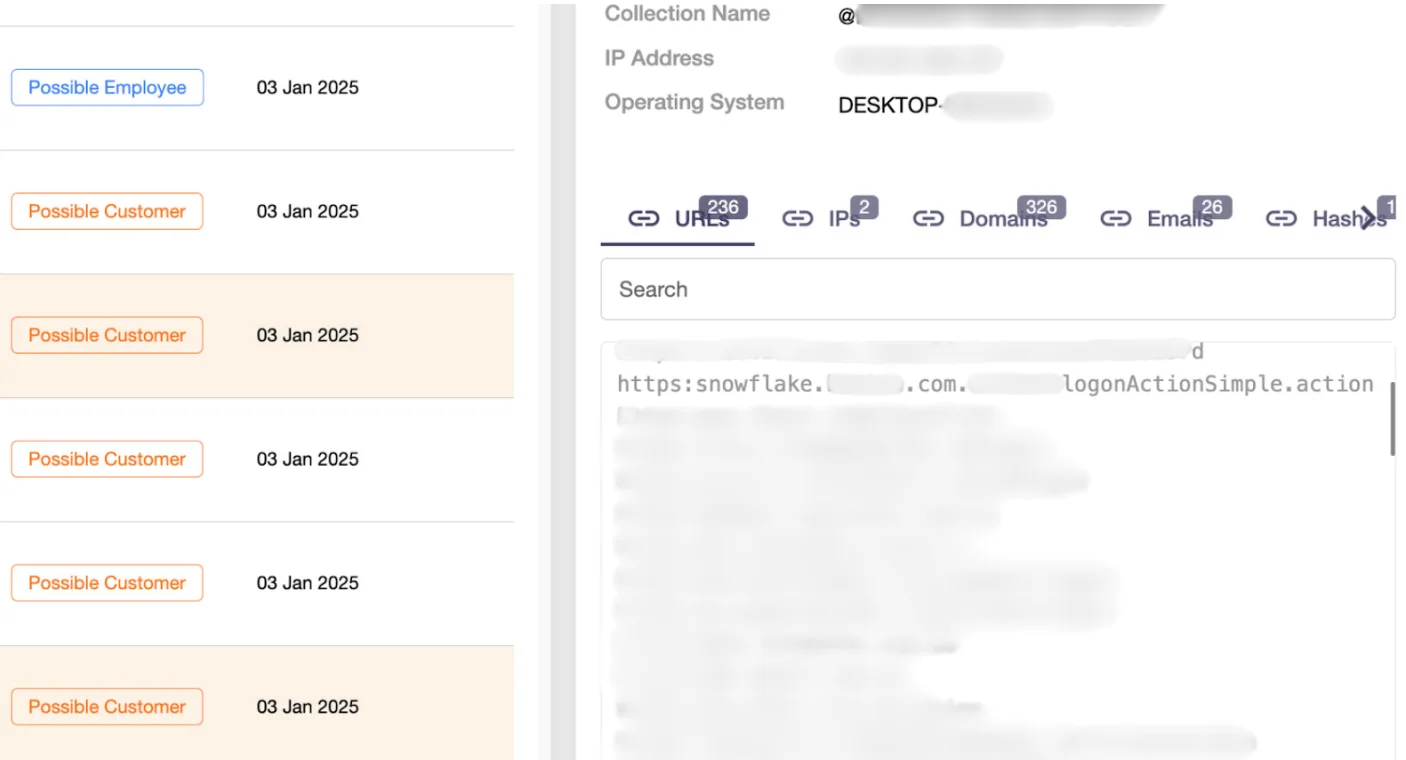
Before launching a Pentest, teams often use standard enumeration methods – DNS lookups, WHOIS records, brute-forcing tools. But these techniques miss a lot. Internal subdomains, third-party integrations, or forgotten portals are easily overlooked.
Dark Web stealer logs fill in the gaps. These often include:
- URLs of accessed web applications.
- Saved credentials.
- Cookies and browser bookmarks.
From this, Red Teams can discover subdomains like portal.companyname.com or internal dashboards not visible through standard recon methods. Browser history and cookie data might also reveal third-party services, such as hubspot.companyname.com, exposing additional entry points.
To efficiently process this data, tools like sqlite3 can extract relevant URLs, revealing the full extent of an organization’s exposed digital surface.
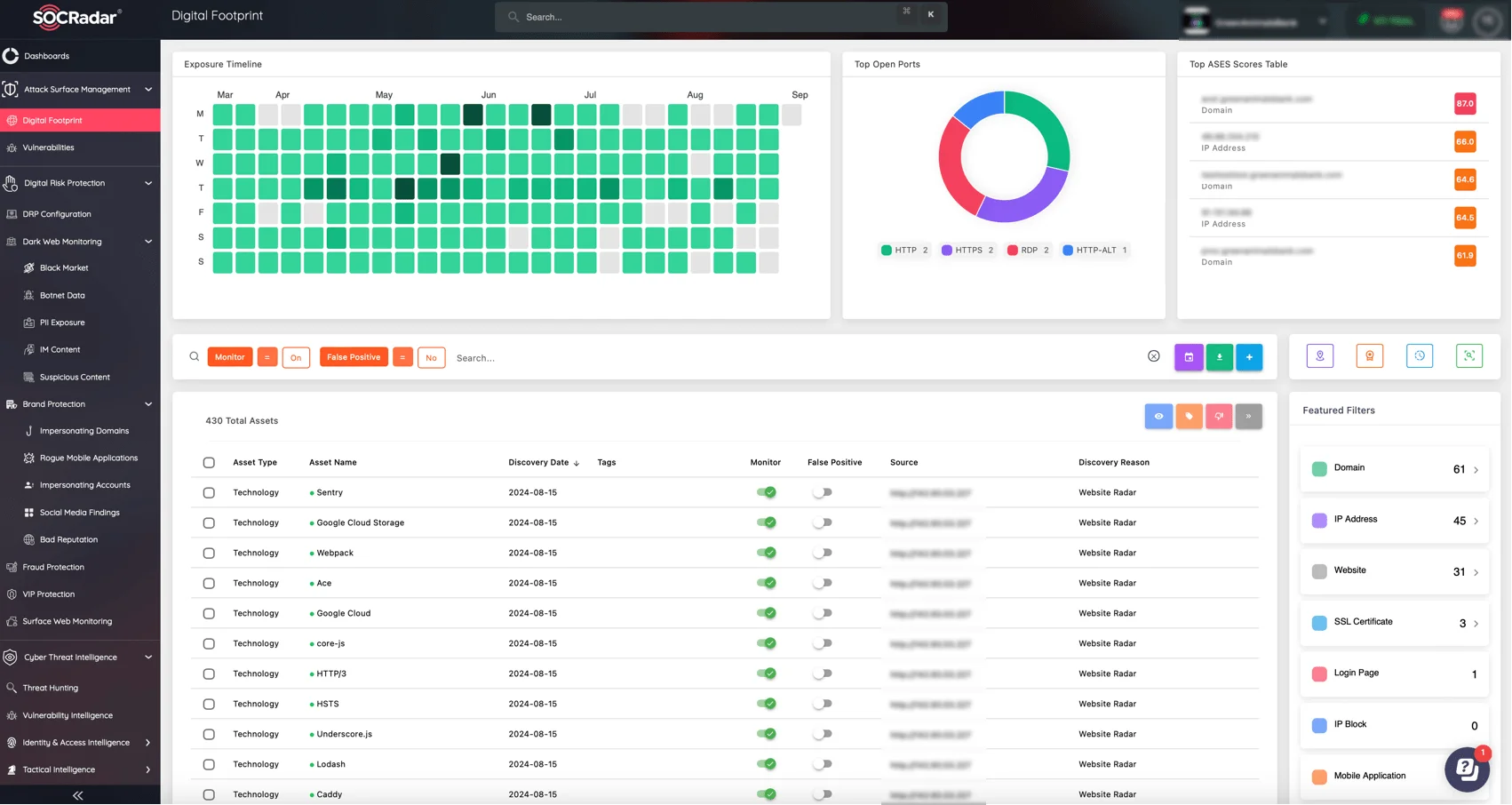
How do you test what you can’t see? That’s the problem most Red Teams face when traditional reconnaissance misses the mark. SOCRadar’s Attack Surface Management helps you uncover the blind spots – forgotten subdomains, unmonitored APIs, and exposed external assets. When paired with Dark Web intelligence, it transforms static testing into dynamic defense mapping.
Ransomware Leaks & Hacker Forums: Turning Stolen Data Into Defensive Insights
Ransomware leaks and hacker forums are sources of chaos, as well as insight. Used correctly, this data helps defenders understand real attack strategies before they’re used again.
What Happens When Ransomware Groups Leak Corporate Secrets?
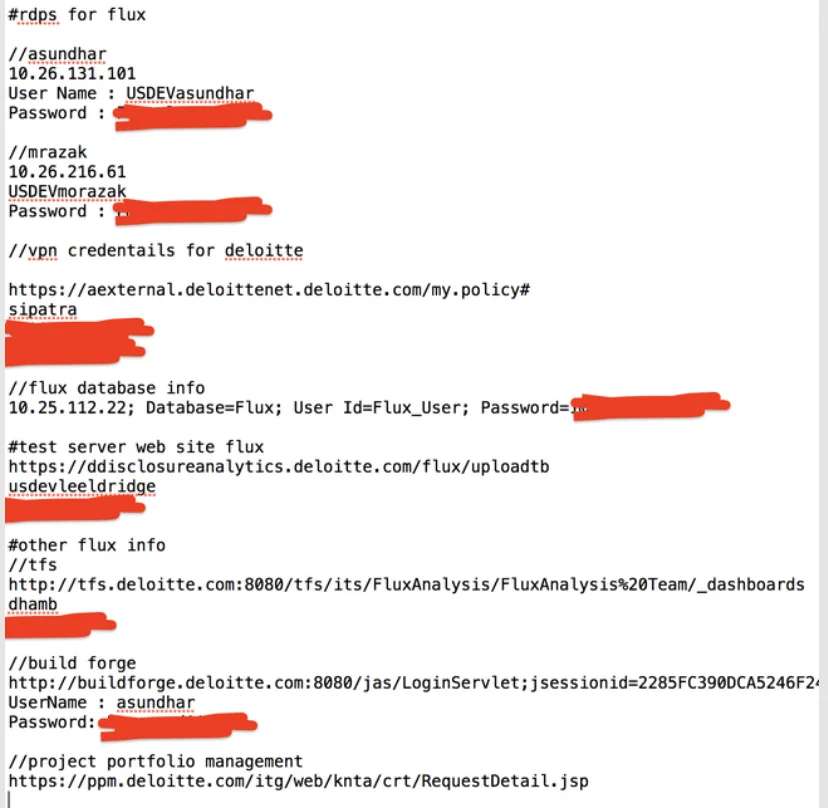
Ransomware groups like LockBit 3.0, ALPHV BlackCat, and Cl0p no longer just encrypt files – they leak sensitive data publicly. These dumps often include VPN credentials, cloud configurations, and internal emails, giving attackers a detailed blueprint for follow-up attacks.
For example:
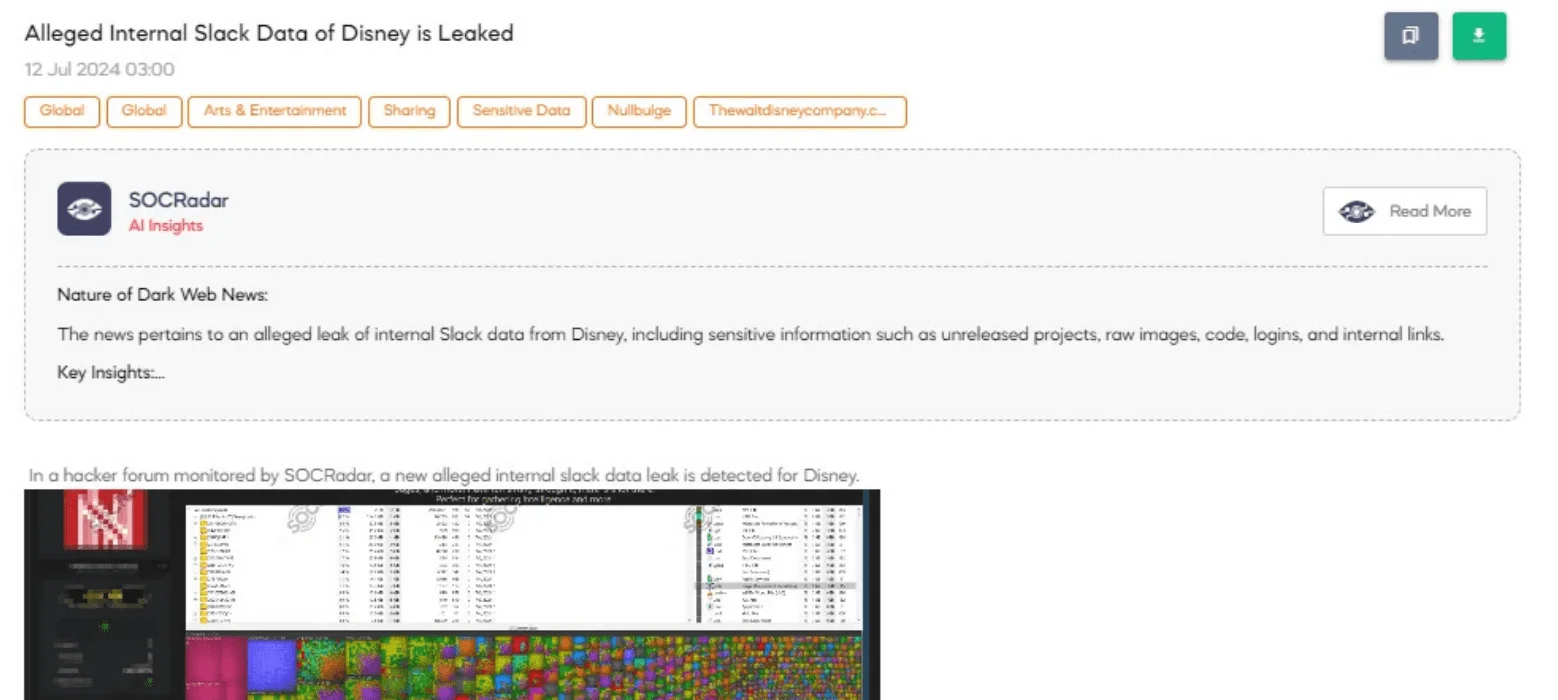
- Disney’s Slack breach revealed 1.1TiB of internal communications, AWS access keys, and sensitive project data.
- Deloitte suffered a GitHub exposure where VPN usernames and passwords were accidentally published.
This is both a problem, but also an opportunity. By analyzing these leaks, Red Teams can profile threat actors, simulate their behaviors, and test defenses using the exact same tactics adversaries rely on.
Leverage SOCRadar Labs’ Threat Actor Intelligence to take this further. With details on associated malware, CVEs, and ATT&CK techniques, security teams can align Red Team scenarios with the real threats targeting their industry, making simulations more targeted, relevant, and effective.
Exploiting Weaknesses in Public Code Repositories
Public repositories on GitHub and GitLab often contain hardcoded API keys, credentials, and misconfigured files – a goldmine for attackers. In the EmeraldWhale operation, threat actors uncovered over 15,000 cloud service credentials by scanning unsecured Git configuration files.
These kinds of oversights can grant unauthorized access to critical systems, and worse, go unnoticed for months. For Red Teams, replicating this tactic helps uncover similar exposures within their own organizations, helping to close gaps before attackers do.
Realistic Phishing Simulations – Leveraging Leaked Data for Maximum Impact
Phishing attacks succeed because they feel real. By using leaked data to inform simulations, organizations can make training exercises as convincing and as effective as the threats they aim to stop. Phishing simulations should reflect the tactics of real attackers, not generic email templates. Dark Web data makes that possible.
The Evolution of Phishing: Why Traditional Simulations Don’t Cut It
Phishing isn’t just about fake emails anymore – it’s hyper-targeted, context-aware, and psychologically manipulative. And the Dark Web provides attackers with everything they need to craft the perfect lure.
Stealer logs often reveal file paths, desktop contents, and even internal documents, allowing attackers to reference specific projects or filenames that boost email credibility. Imagine receiving an email referencing a file that actually exists on your system – it doesn’t just feel real, it is real.
Crafting Next-Level Phishing Scenarios
By combining leaked credentials, exposed email addresses, and internal workflows, Red Teams can create next-level phishing simulations that mirror real-world tactics. These campaigns test not only employee awareness but also organizational processes – like incident reporting, internal response time, and escalation paths.
SOCRadar Labs’ Phishing Radar tracks new domain registrations and flags suspicious lookalikes in real time. Whether you’re building a phishing simulation or looking to stop a real one, this tool injects real-world data into your scenarios, sharpening user awareness where it counts.
Securing the Future: Intelligence-Led Pentesting & Red Teaming
The gap between simulated attacks and real-world threats is narrowing fast. Intelligence-led testing ensures your defenses evolve just as quickly, by using the same data adversaries rely on.
Why Intelligence-Driven Security Is the Only Way Forward
In today’s threat landscape, hypothetical simulations don’t cut it anymore. Attackers aren’t guessing – they’re using real credentials, leaked documents, and insider data to plan and execute their breaches. If your simulations aren’t grounded in the same reality, you’re training for the wrong fight.
By integrating Dark Web Intelligence into Pentesting and Red Teaming, cybersecurity teams gain a strategic edge. Instead of assuming potential vulnerabilities, they simulate real attack paths based on leaked credentials, exposed APIs, ransomware dumps, and phishing infrastructure.
Organizations already adopting this approach are seeing tangible benefits – identifying weak MFA implementations, correcting misconfigured cloud environments, and even removing sensitive files from public platforms before they’re weaponized. This isn’t theory – it’s practice, and it’s working.
Next Steps – How Organizations Can Integrate Threat Intelligence
Integrating threat intelligence into your security stack doesn’t require a complete overhaul. Here’s how to start:
- Monitor the Dark Web for exposed credentials and sensitive leaks tied to your domain.
- Use threat actor profiling to guide Red Team exercises and simulate attacks aligned with real adversaries.
- Map your attack surface using data from stealer logs and public sources to uncover shadow assets.
- Incorporate leaked data into phishing simulations and lateral movement scenarios for realism.
Each of these steps deepens your understanding of how attackers think, and more importantly, how your organization would respond.
For a comprehensive breakdown of these strategies and deeper insights into how Dark Web Intelligence can power up your security operations, check out the full whitepaper: Why Is Threat Intelligence the Key to Effective Pentesting and Red Teaming.
Conclusion
Cyber threats are becoming more sophisticated, targeted, and data-driven – and your defenses need to be as well. Relying solely on standardized Pentesting or Red Teaming leaves critical gaps, especially when attackers have access to leaked credentials, exposed infrastructure, and insider data.
By integrating Dark Web Intelligence, security teams can simulate threats more accurately, identify blind spots more effectively, and build defenses that reflect the real world, not just compliance requirements.
Now’s the time to act. Equip your Pentesting and Red Teaming strategies with the intelligence they need to stay ahead. The threats are real – but so are the tools to stop them.