
AlienFox Toolkit Targets Cloud Web Hosting Frameworks to Steal Credentials
Cybercriminals are using a new toolkit called AlienFox to steal login credentials and sensitive data from cloud-based email services by scanning for misconfigured servers. The toolkit is available for purchase through a private Telegram channel.
Reports indicate that the malware targets at least 18 cloud services, including well-known web hosting frameworks like Laravel, Drupal, Joomla, Magento, Opencart, Prestashop, and WordPress.
The malware can steal API keys, OAuth tokens, and other authentication tokens once it identifies a vulnerable server.
The AlienFox toolkit has been classified as a cloud spammer’s Swiss army knife, and it is believed to have been developed by a group of cybercriminals operating in Eastern Europe.
The Three Versions of AlienFox
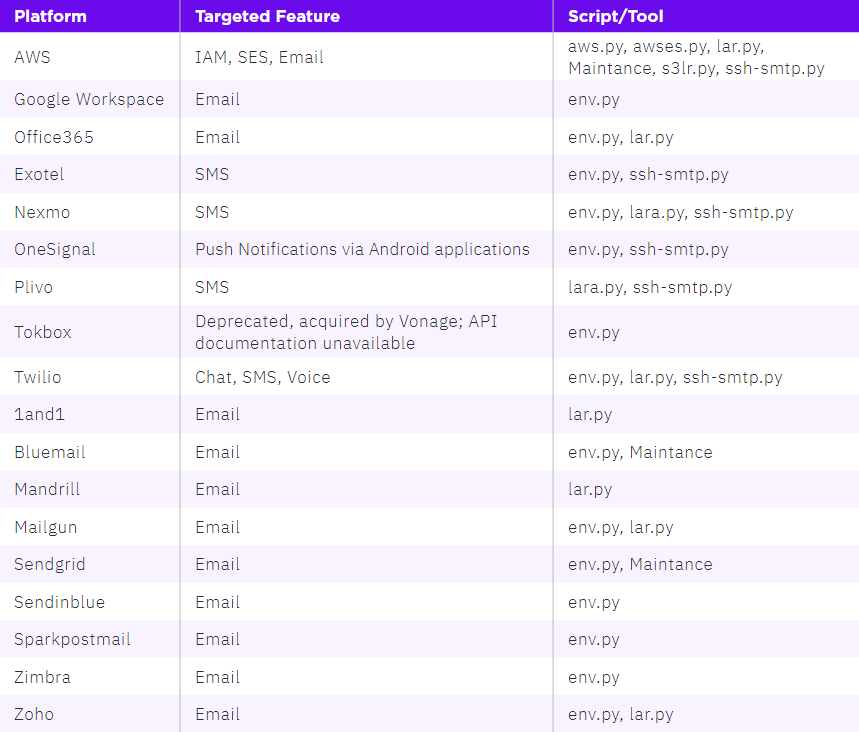
Researchers have uncovered three versions of AlienFox so far: v2, v3, and v4. With each version, the toolkit enhances its capabilities. Based on SentinelOne’s analysis, the versions are detailed below:
AlienFox v2, the toolkit’s first known version, extracts credentials from web server configuration or environment files. The s3lr.py script contains the core utility.
Other scripts included are awses.py and ssh-smtp.py. The awses.py script automates activities such as sending/receiving messages and elevating a privilege persistence profile on AWS SES (Simple Email Services) by utilizing the AWS SDK Boto3 Python client. The second script validates SSH configurations on the webserver to find vulnerabilities, and it potentially tries to exploit CVE-2022-31279, a rejected vulnerability in the Laravel PHP framework.
AlienFox v3 has four variations under it, created between February and April 2022. This version includes a Lar.py script, which extracts keys and secrets from compromised Laravel .env files. The script then logs that information to a text file, along with additional information about the server and tags to indicate whether the data was obtained using a configuration parser or a regular expression.
AlienFox v4, the latest version, differs from the previous ones in that each tool is assigned a numerical identifier. The ALIENFOXV4.py script in the root directory acts as a bootstrap for the tool scripts.
Tools 5, 6, 7, and 8 collect target lists. The other tools check if the targets are misconfigured or have a security vulnerability, and they improve the overall functionality of the AlienFox toolkit. There is again a script to focus on AWS and SES. Another tool in version 4 uses the cms.py script to check sites for the presence of web hosting frameworks. There are also cryptocurrency wallet crackers for Bitcoin and Ethereum, as well as an Amazon account checker tool.
Secure Your Cloud Storage with SOCRadar’s Cloud Security Module
Organizations should monitor interactions with their cloud services and adhere to the least privilege principle. Following best practices for cloud configuration management and monitoring the condition of cloud environments are also essential.
SOCRadar’s Cloud Security Module (CSM) has been developed to enhance the security of customers’ cloud storages.
The module can detect the status of cloud buckets, whether they are “public,” “private,” or “protected,” and users are alerted with a “Cloud Bucket Detected” message when new storage is discovered.
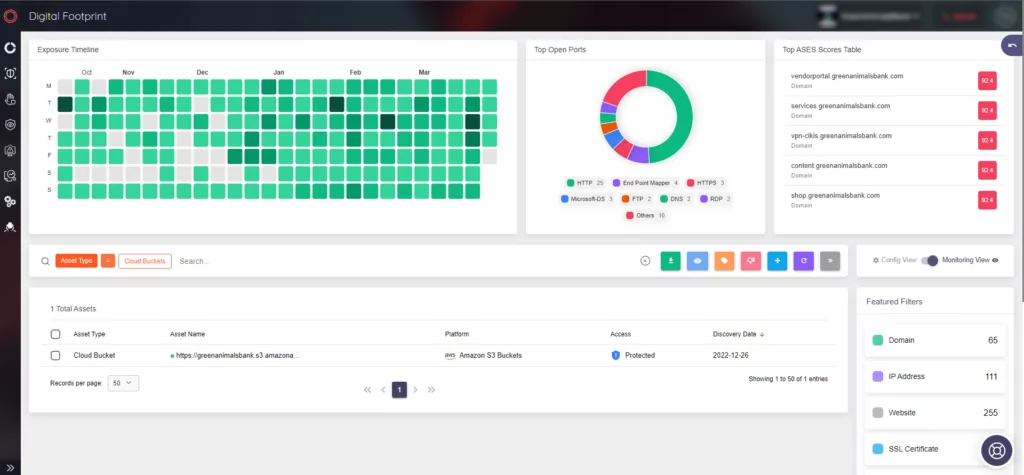
With CSM, the status of users’ cloud buckets is constantly monitored, and any changes are alerted to users, ensuring the security of their data.
IoCs
In their report, SentinelOne provided a detailed list of IoCs.
- showdenwashere@hotmail[.]com
- whm@sending[.]today
- root@youez
- ‘User-agent’:’Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko)
Chrome/81.0.4044.129 Safari/537.36′
- https://rtvsmkqfa3clrvgj6f- 9fd73c.ingress-daribow.easywp[.]com/wp-admin/v1/1.php
- https://rentry[.]co/3cii9/raw
SHA-1 hash of an Androxgh0st-related sample
- c0184407dcbec911a325d41e9a9ef1dbed524fe5
- 41a2cab42a08adf93b5ada1eafb75d5b4f496853
- 3cb5b4182ef6e8174f87c8ed3551f91b72c47370
- 17592a2fdb8dae9c4c88f1fbf7e9c632129f98df
- ab8d480c090ab8be0cdb0ff5bc0f59972845b125
- 15ade0df5b4e6a82ceec429a2673fd1ed011eb93
- aa8be80db30c4f5a49c3e75254ef6d0101c37987
- 064734bc43ee2d83e8a275293d17fc925620bba1
- 9381c30e29089639249e67b62f61c6df4869c6c1
- fd5228889cd12f343236f7d51c98fab4db6c4763
- fd3375553dda2347c0b383d8e800bfe4f93d3af0
- f4ef68d3d2b58a58a82e00ebeaaed556e03328af
- 23abd146befe761337e5155a116138acf81331d9
- f5af939480fc86a086bc589047444b1c448ebb09
- ac265c12a4f08378e2519e290b0c45a1adc7156f
- Of1583b56dd02fc200c7dae0d3c9b32b4278846b
- 74c4cfa0edae5e87001c901214789cb0f0087031
- ec5b2efe8eadfac7ceca545e25f06240bbf16960
- 9eb13d9a678cd2e78da41563b7461887ce5997b6
- 25bbda606c72e81fac9abe76e0f00f9cd12770e4
- e786fc1fdfcb7be28650383eb33cdf6c90f1d033
- 8e6e18ba7e251d31b46d17535010a8c583345b23
- b3559eeac9a9caa840cc96980fe0bbd1c7da37d3
- 40df29a738fd5cab0face169d8a8426dff7d2d10
- e663e24fc6aadbaae5bbf722a84097a6127f4066
- c2f51b44e26e4aca40beb887ac4d36f3e091e26a
- 4266bdb139ae6d22ddf98501cc3af280aa488b42
- 329328dc57acece8c47ab5c73f7b9c7e4e09981a
- fc08c15dfd6074d80e1f8d777fb49f8c14b4af20
- aa4672621f81f601882ad13f26d37dc8218bb06a
- 07289c56e65a98a85bc794374949aae98b819823
- 4ab401d4c490460fd457151f643b5ec7e594cd41
- 7848e53133f4470c29e33ee6dd87f8f326c5fa38
- 7d7bad6282531521b9103817a38bff3a34b89428
- 15129436f5bab6c3eea9b2dfc4d0f0043438e013
- 15aec55e56225700766d79b6fb9d212cced21951
SHA-1 hash of a sample setting an AWS admin persistence profile
- ebdc60f33d22c4256ca6ab4058059db1d618ec11
- 894fd799168f9ff11e74ee37d5bec35387feef24
- 28de7d7fcd18471f53737fd8a3df3a23a34cf758
- 3ddb8dc53b6151ea036db3d2a5f34e5f5b39e044
- ceda47dd1aacc515d8bdda04299ab1ebf1ba0d73
- 23abd146befe761337e5155a116138acf81331d9
- ac265c12a4f08378e2519e290b0c45a1adc7156f
- b8dc12cc600aced9d34c463c5bf5edb53db605fb
- 45a0675088afdcf2ec059510fc2a4905957c2a69
SHA-1 hash of an AlienFox ZIP archive
- c3464926cf2075595c77dc5b3fbcf1f014c8046b
- fc0479a3d1188384613f437f28e28614a6118e94
- 5c9993e5d7468551c60e6dab488eccea7f4ef007
- ece7e6727d2daa254e4d4a6be62744d6f3a2a2ef
- afb7b010bafb9f7faf2b528f128ff24da94e0190
- 959e377131762ccb879c36c53e3b71473d3b72fd
- 48afb7ac8fdf6a8da47601806a8028c61dad2eb7
Yara Rules
rule cw_androxgh0st_strings
{
meta:
author = “Alex Delamotte @ SentinelLabs”
description = “Rule based on Androxgh0st file contents.”
reference = “https://s1.ai/AlienFox”
strings:
$a = “asu = androxgh0st().get_aws_region(text)” ascii wide
$b = “nam = input(‘x1b[1;37;40mInput Your List : ‘)” ascii wide
$c = “def jembotngw2(sites):” ascii wide
$d = “def nowayngntd():”
ascii wide
$e = “def makethread(jumlah):”
ascii wide
condition:
any of them
}
rule cw_boto_broad_persistence
{
meta:
author = “Alex Delamotte @ SentinelLabs”
description = “Detect (Boto3 OR samples referencing Telegram channels) AND AWS persistence login
profile.”
reference = “https://s1.ai/AlienFox”
strings:
$a = “boto3.client(‘ses’”
$a1 = “https://t.me”
$b = “arn:aws:iam::aws:policy/AdministratorAccess”
$c = “iam.create_login_profile(UserName=”
condition:
($a or $a1) and ($b or $c)
}




































