
An Overview of Intelligence Requirements in CTI
Security, in general, is a complex domain where you need to keep in mind a variety of factors. In a complex field like this, the role of intelligence cannot be overstated. It is impossible to know what to do without seeing in front of you. Therefore, intelligence plays a huge role. It is the backbone of any planning around securing something. It allows you to see the upcoming threats. Collection, analysis, and dissemination of information, that classic cycle, enables decision makers to anticipate threats, prevent attacks, and respond effectively to crises instead of watching the world burn down petrified.
But how can you know what you need to know? Let’s say you are certain of those needs. What is your justification behind that conclusion? Let’s explore intelligence requirements in cyber security.
What is “Intelligence Requirements”?
Without planning what you need, it is impossible to achieve those needs. Having a clear blueprint is essential because this allows you to see your goals, resources, potential obstacles, and helps you build a strategy, even before you start anything. You are creating a guide that will help you throughout your journey.
When you need to collect intelligence, the importance of planning increases even more. You have limited sources, and you have real threats targeting you. Wasting resources on unrelated intelligence will cause you trouble. Spreading money to gather all the intelligence will bury you under piles of information. Before any intelligence gathering begins, you need to define intelligence requirements.
An intelligence requirement is a piece of information to support operational activities. They guide the collection, analysis, and dissemination of the produced intelligence.
Those requirements ensure that your operation has a proper goal and an action plan to actualize that goal.
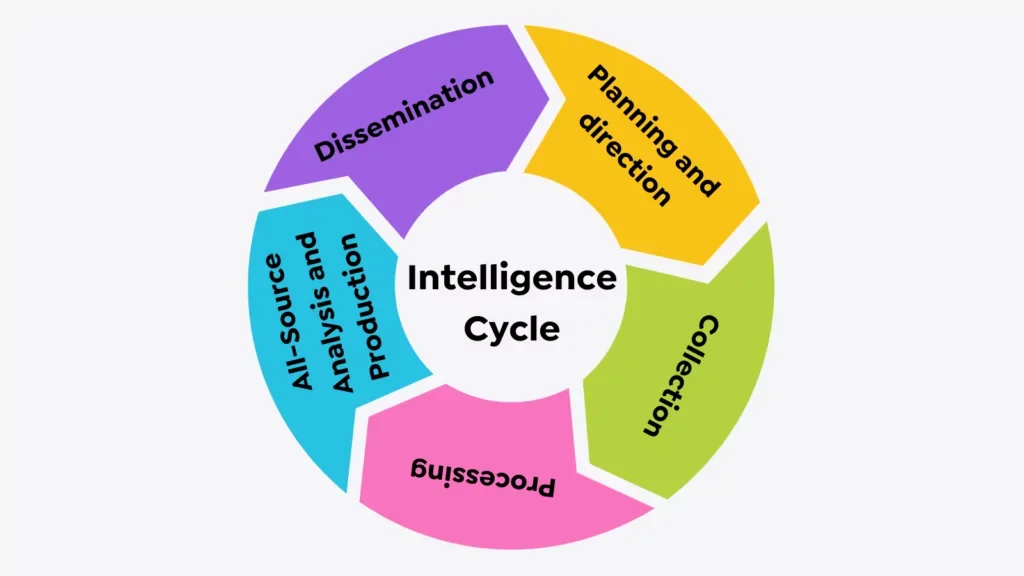
Intelligence Cycle
The intelligence cycle is a continuous process used to collect, analyze, and disseminate information. It consists of five main steps.
- Everything starts with Planning and Direction, which involves defining information needs, setting objectives, and organizing resources.
- Next, the Collection step comes. You gather raw data from various sources.
- During the Processing step, the collected data is put into a usable format.
- Then, Analysis and Production follow, where the processed data is evaluated and interpreted to produce actionable intelligence reports.
- When everything is finished, the final intelligence is shared with the stakeholders.
For more detailed information on the intelligence cycle, you can check our article here.
During the first phase of the intelligence cycle, Planning and Direction, you create a road map for your operation. Here, you create the necessary intelligence requirements for the stakeholders to use.
Why Do You Need Intelligence Requirements?
The amount of information you can collect from different sources is vast, and processing this information is hard, if not impossible. The worst part is the majority of that information is not even related to your organization or cause. You need intelligence requirements to avoid surprises and unexpected developments.
Without clear guidance, you can spend excessive amounts of money while trying to create the correct intelligence and waste your resources along the way anyway. This will prevent you from investing that capital to the right need.
If you don’t set up proper requirements, you can collect too much information. Everyone would like to be aware of all the threats targeting themselves but if you don’t draw sharp lines, you will be collecting useless information and slow down your processes.
Are you curious about which threat actors are targeting your industry? Check our Operational Intelligence module.
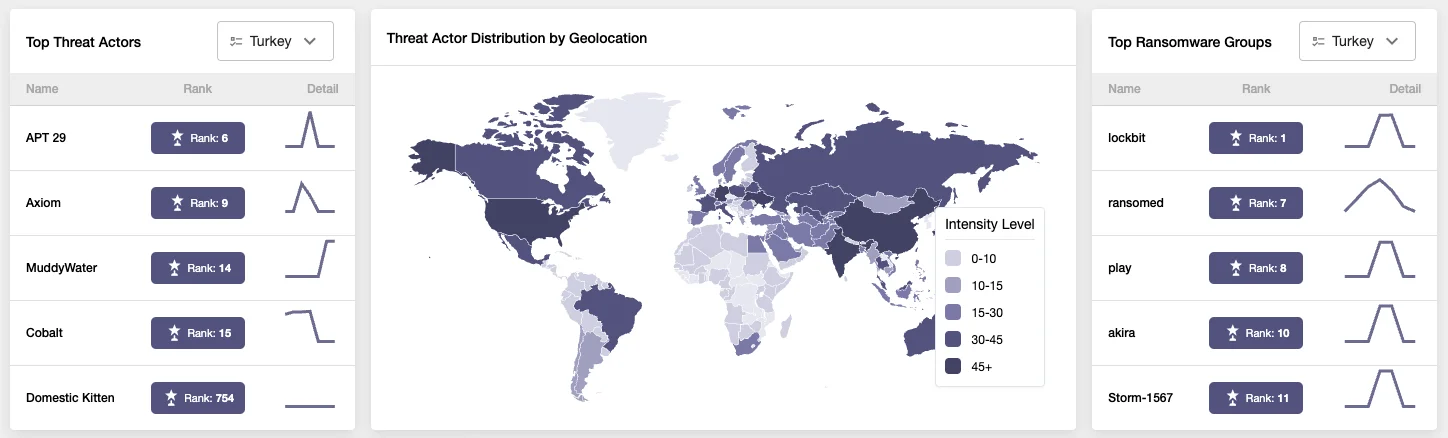
Operational Intelligence Module
Lastly, if you don’t set up proper requirements for your intelligence needs, you can collect completely wrong information that has nothing to do with your needs or organization. You won’t be able to see the significance of threats targeting you and won’t be able to protect yourself.
Having precise intelligence requirements is crucial to streamline the process, reduce costs, avoid information overload, and ensure the accuracy of the intelligence gathered.
Examples of Good and Bad Intelligence Requirements
Maybe you already saw intelligence requirements, and maybe you are trying to create them for your needs. As always, there are good and bad examples out there, and we’ll have a look at them now.
The base of intelligence requirements is your needs. These requirements will satisfy those needs and allow you to make decisions so you will know where to allocate your resources or how to design your security system.
“Intelligence from the dark web” is not a proper requirement. What intelligence? Which part of the dark web? What do you want to follow? Why do you want intelligence from the dark web? You must be able to answer these questions. With this form, that requirement is too general. Hundreds of posts are published every day on dark web forums and threat actors’ Telegram channels. These posts are published on a variety of topics. The source is vast, and the request is vague. If you try to collect information after this request, you will only clutter your inbox and slow down your workflow.
Your domain names, your IP addresses, and emails are not intelligence requirements. They are identifiers, useful for gaining insight into your company‘s structure and operations as well as tracking activity, but not intelligence requirements.
“I want to know about the APT groups, they are dangerous.” Yes, they are, but this is not an intelligence requirement. You don’t need all the information about APT groups because finding out about all the threats is not intelligence, it is just noise.
What is a good intelligence requirement, then? The intelligence requirement you are trying to formulate should focus on specific things. If you have a general idea in your mind, you can ask wh-questions to make them more focused. Who? When? Why? Where?…
“Which vulnerabilities should I worry about?” is a general question but can be developed to create a good requirement for gathering useful intelligence.
“I am in the finance sector, and our friends on the other side of the street were hit by a phishing attack. I worry about social engineering techniques targeting our sector.” This is a real worry for the stakeholders and a true need to be satisfied in order to protect that organization from phishing attacks. This worry or demand focuses the intelligence-gathering efforts on a specific threat domain targeting the organization. Finding out about the threat actors targeting that sector won’t be enough to satisfy this need. Threat actors targeting the finance sector with social engineering attacks and their techniques are the satisfactory product in this case. With proper refinement, that need can be turned into a good intelligence requirement.
“What kind of vulnerabilities are exploited in the software we use?” is again a proper request to get information on which will strengthen the security structure of an organization. If you can develop this request, that organization will be able to take the necessary actions.
Getting swift information on vulnerabilities is important in order to take the necessary steps as soon as possible. Updating software will keep the threat actors away from your organization. But when you go online, the vast amount of information on the web is only creating an obstacle for you. It gets harder to find the necessary information you need. In these kinds of moments where you need to act fast, SOCRadar’s Vulnerability Intelligence module can help you.
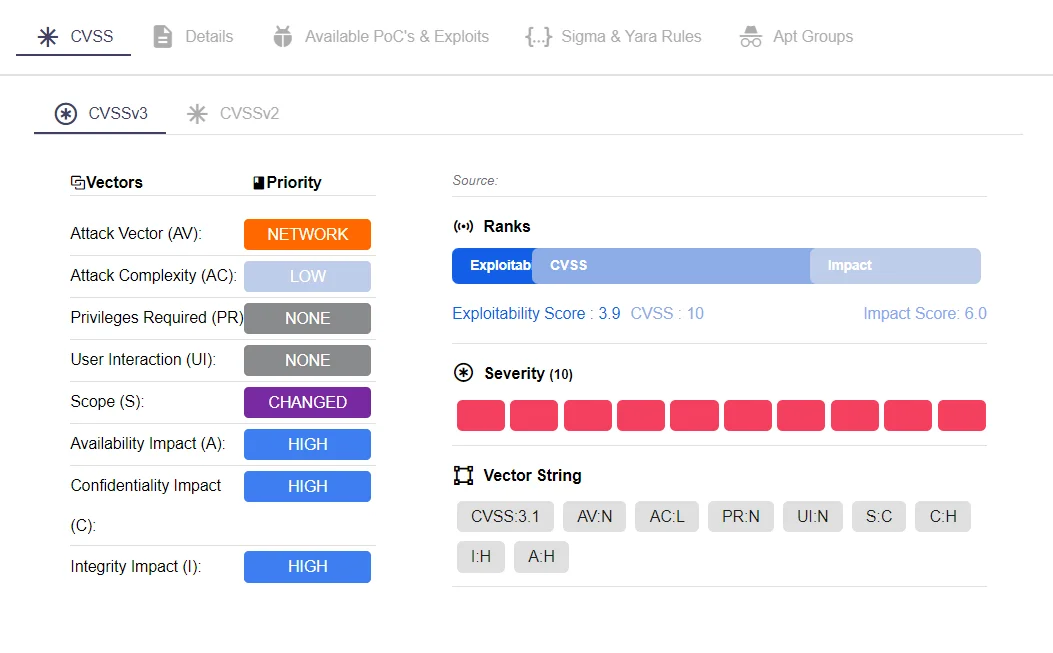
SOCRadar Vulnerability Intelligence Module
You can zoom out and ask questions regarding the general threat landscape of your sector, region or country. Some of the information you get from these kinds of general requests can be unrelated to your needs but they might help you to understand your environment better.
Formulating Intelligence Requirements
As we said earlier, the intelligence requirements are actually the needs of a stakeholder. The stakeholder needs X intelligence to achieve Y because of Z. You can zoom in or out to formulate this logic on different levels.
For example, the SOC team needs technical intelligence to decrease the false-positive rate in order to create more time to investigate real threats in detail.
You can apply the “The stakeholder needs X to achieve Y because of / for Z” method for the management team as well. The management needs strategic intelligence to understand risks posed by new developments in the use of AI by threat actors in order to decide if new investments are necessary.
After gathering the necessary information, it is time for the feedback. Are the stakeholders happy? Did these requirements fulfill their needs? In a very focused scenario like above, the stakeholder can be the security operations center. In a more general sense, they can be the management of a company. Regardless of the level of the stakeholders, receiving feedbacks is vital.
By communicating with the right stakeholders (the true users of the generated intelligence) and turning this into a cycle on its own, you can refine these requirements even further and improve your CTI operation.
If we need to create a step-by-step look at the whole cycle, it may look something like this:
- Creating the definition of the “needs” by keeping the foundations of those needs in mind. The stakeholder needs X intelligence to achieve Y because of Z.
- Formulating the steps that need to be taken in order to satisfy the needs. You can zoom in or out depending on the who’s needs you are trying to satisfy.
- Taking action.
- Receiving feedback.
Conclusion
The “unknown unknowns” term was used by Donald Rumsfeld, the former U.S. Secretary of Defense, during a 2002 press briefing. He used the phrase to describe the limitations of intelligence and the unpredictability of future events. There are known knowns, which are the things we know that we know. Then, there are known unknowns. The things we know, we do not know. There are also unknown knowns, things we do not know we know. And finally unknown unknowns. Things we do not know that we do not know.
In order to overcome the obstacles of their operations, the CIA doesn’t collect all the information in the world and then tries to find a needle in a haystack. They have certain requirements set before starting gathering any information.
Even though the scenarios above are basic examples, you will be able to see the importance of planning before starting your CTI journey. The main logic behind this is to minimize the effort and maximize the benefit. If you want accurate intelligence and targeted notifications in your mailbox while protecting your organization, you can try SOCRadar. You wouldn’t be wasting time with unnecessary information.



































