
Beyond Phishing: Top 10 Data Breach Sets
In recent years, there has been a significant increase in the amount of sensitive data available, making cybercrime more of a risk even for people who aren’t very tech-savvy. Stealer logs and data breaches, easily found on dark web markets, Telegram channels, and secret forums, hold stolen login details for many online services.
As many incidents show, this easy access to stolen data has serious consequences. It used to be that most hacking started with human mistakes, but now it’s much more complicated. Data breaches often expose vast amounts of sensitive information, causing more problems.
Hackers get this stolen data either by buying it or by scraping stealer logs and other data, sometimes even giving it away for free. Big players in BreachForums, USDoD, and IntelBroker are always releasing new data leaks with lots of sensitive info that can affect anyone or any organization.
Even their attack plans often start with another data leak. For example, USDoD regularly scrapes stealer logs to get sensitive details about key people, making their phishing attempts more convincing.
Stealer logs especially, like Redline and Raccoon, are a significant danger. They hold lots of stolen data from hacked devices, like internet history, cookies, visited websites, apps installed, and user info. Initial Access Brokers (IABs) then use or sell these logs to launch different attacks, from ransomware to tricking people and Remote Access Trojans (RATs).
In this growing world of cyber threats, organizations and individuals must stay alert to these ever-changing dangers from stolen data and stealer logs, mainly how they’re used on the deep and dark web.
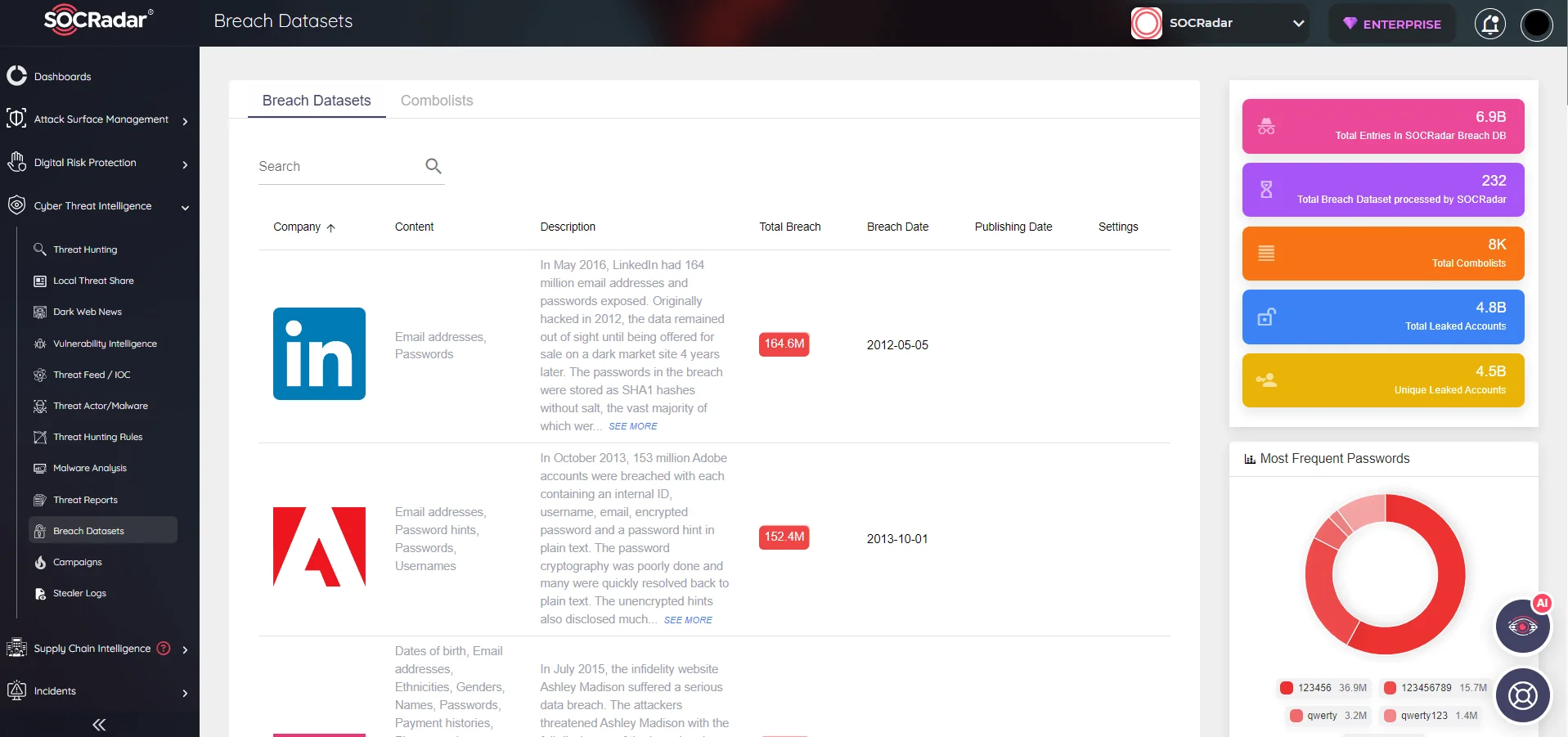
SOCRadar Breach Datasets monitors collection of data sets and contents to alert its users
Data breach sets are collections of breached data that are often compiled, organized, and traded on the dark web or other illicit forums.These sets can contain a wide range of information from various breaches, and they are often sold or distributed by cybercriminals for malicious purposes such as identity theft, financial fraud, or phishing attacks.
Today, we’re diving into the top breached datasets that are sold or shared as a collection and what they contain to better grasp the whole situation.
Evite Breach, 160M
In April 2019, Evite, the website specializing in online invitation management, discovered a breach in their systems. After an investigation, they uncovered unauthorized access to a database archive that dated back to 2013. The compromised data encompassed a total of 101 million distinct email addresses, primarily belonging to invite recipients. Moreover, members of the platform had their names, phone numbers, physical addresses, dates of birth, genders, and passwords stored in plain text exposed as well.
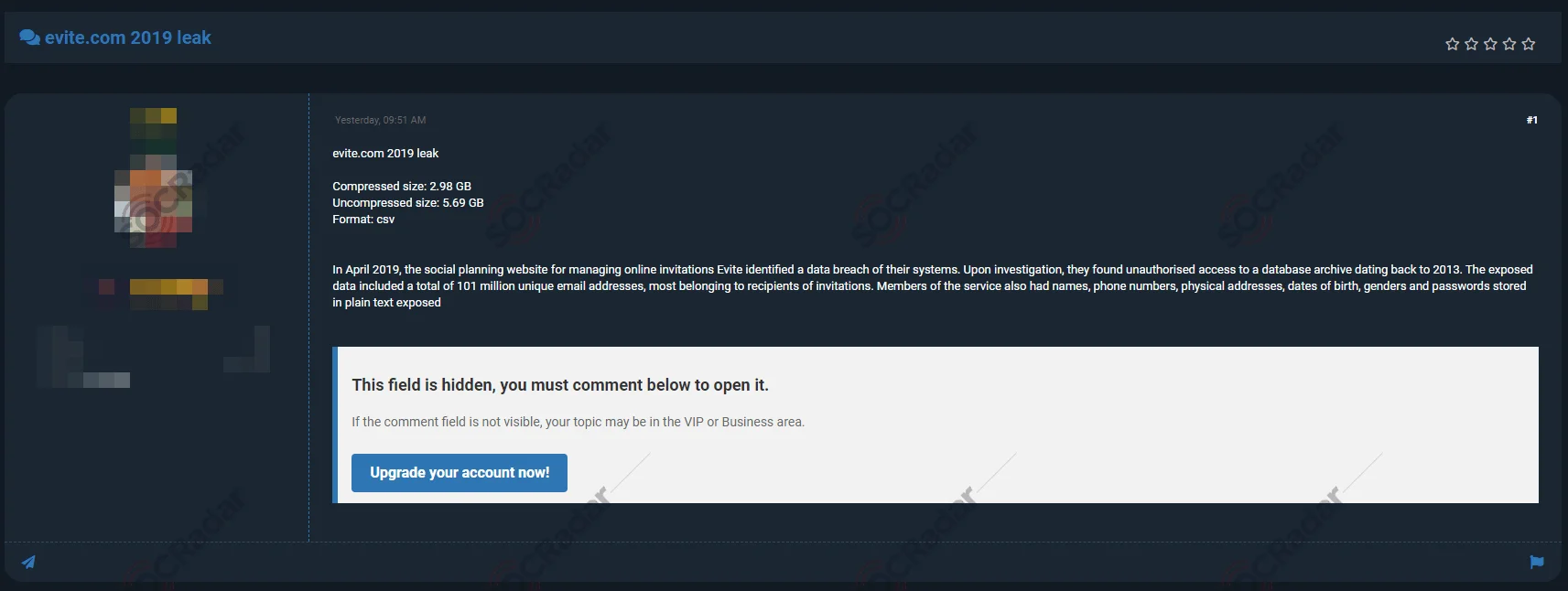
A post in a hacker forum, sharing the data leak from evite.com
Breached Data Types:
- Names
- Phone numbers
- Physical addresses
- Dates of birth
- Genders
- Passwords (stored in plain text)
Dubsmash Breach, 162M
Dubsmash, an iOS and Android video messaging app based in New York, announced on Monday, February 25, 2019, that a breach in December 2018 exposed 162 million user accounts globally. The compromised data includes personally identifiable information such as user locations, usernames, passwords, phone numbers, names, and additional details. According to Dubsmash’s statement, this user information has been available for sale on the dark web since early February.
Breached Data Types:
- Email addresses
- Geographic locations
- Names
- Passwords
- Phone numbers
- Spoken languages
- Usernames
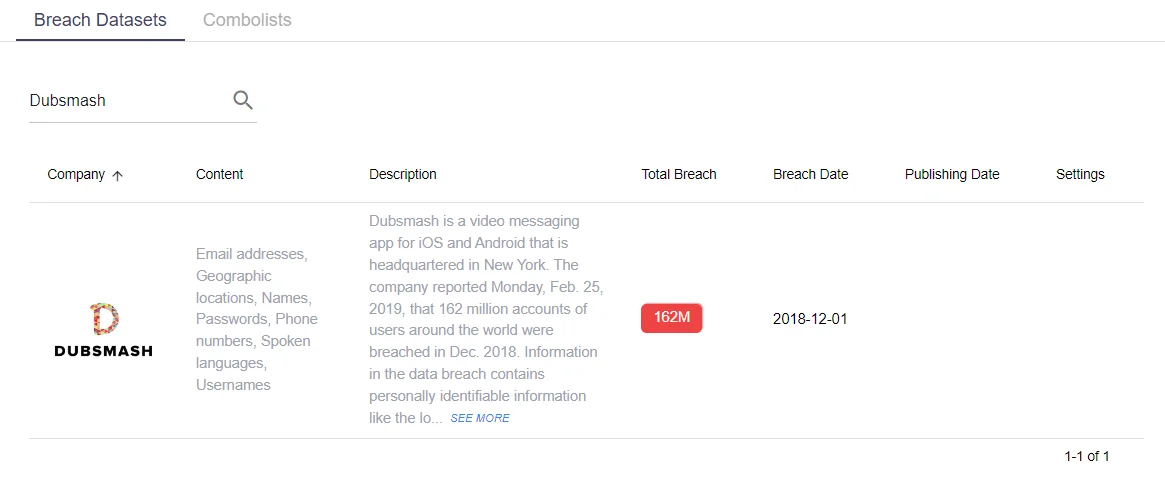
In SOCRadar Platform, you may search for specific breaches and its content information
VNG Zing Breach, 163m
In 2018 VNG issued an apology for the exposure of sensitive information from hundreds of millions of customer accounts. This data package, comprising 163 million Zing ID accounts, was shared on a foreign forum known as TTO. The Ministry of TT-TT in Vietnam is addressing the disclosure of this information on Facebook. Additionally, even the Facebook CEO disclosed that Vietnam is among the top 10 countries with a significant amount of information on the platform.
Breached Data Types
- Usernamed
- Passwords
Linkedin Breach, 164.6M
Back in May 2016, LinkedIn faced a data breach where 164 million email addresses and passwords were exposed. This breach actually happened in 2012, but the data stayed hidden until it was put up for sale on a dark market website four years later. The passwords from the breach were stored as SHA1 hashes without salt, and most of them were cracked shortly after the data was made public.
Breached Data Types:
- Email addresses
- Passwords
Zynga Breach, 172M
Zynga, an online game developer, experienced a system breach in September 2019, where hackers accessed data from over 200 million user accounts. A hacker known as GnosticPlayers claimed responsibility for the breach affecting games like Words with Friends and Draw Something on Android and iOS platforms. The breach exploited a vulnerability, granting access to a database containing user credentials. Initially, it was estimated that 200 million users were affected, but Zynga’s own database verification indicated that 173 million accounts were breached. Zynga took steps to secure affected accounts and notified impacted users accordingly.
Breached Data Types:
- Email addresses
- Passwords
- Phone numbers
- Usernames
Breached Databases on Cit0Day, 226M
Over 23,000 breached databases have been released for download across various hacking forums and Telegram channels, marking what threat intelligence analysts consider the largest leak of its kind. The database compilation reportedly stems from Cit0Day.in, a private service promoted on hacking forums to fellow cybercriminals. Cit0day functioned by amassing breached databases and granting access to usernames, emails, addresses, and even unencrypted passwords to other hackers for a fee, either on a daily or monthly basis.
Breached Data Types:
- Usernames
- Emails
- Addresses
- Cleartext passwords
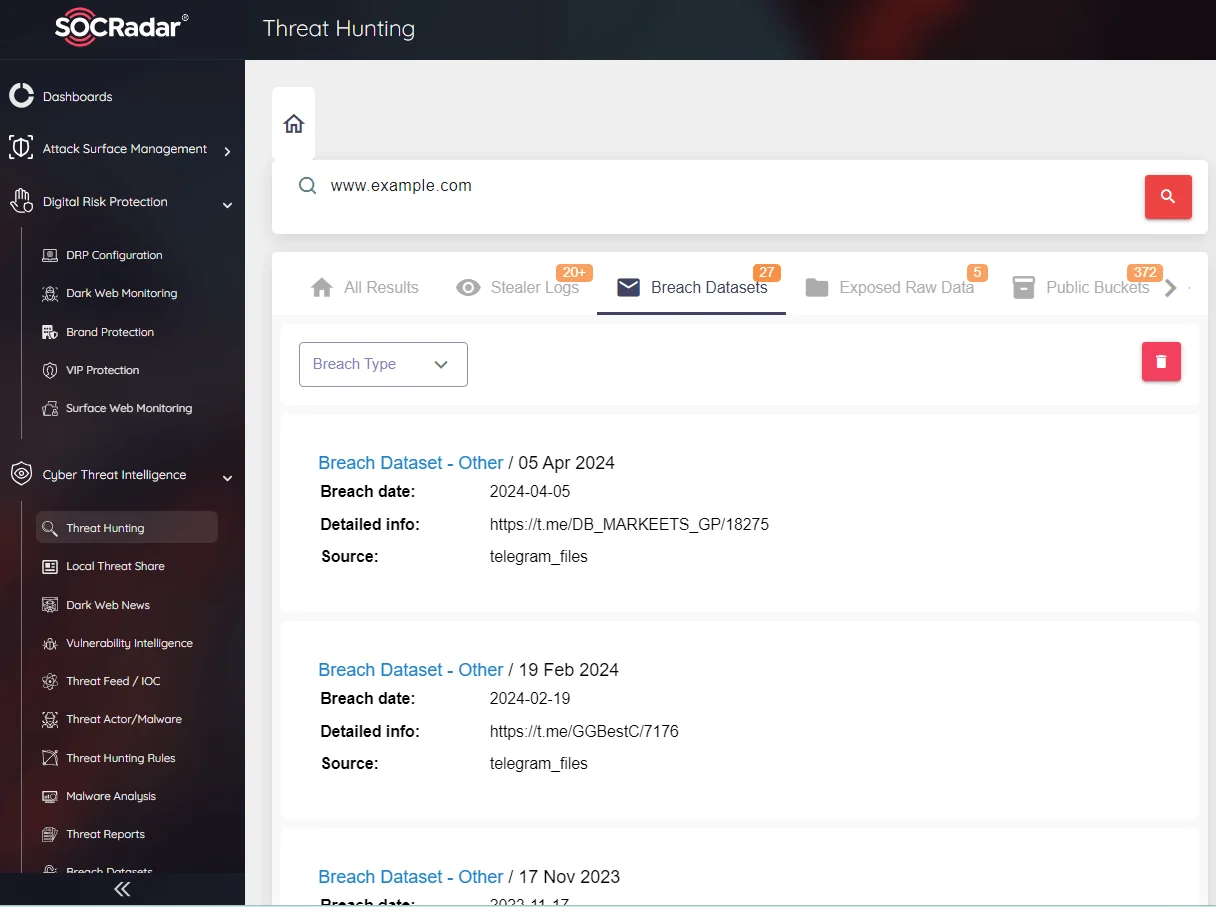
It’s also possible to search for specific domains, e-mails or relevant information on Stealer logs and Breach Datasets in SOCRadar Threat Hunting
Deezer Breach 244,3 M
In September 2019, Deezer, the music streaming platform, experienced a data breach affecting 257 million users. This breach resulted in the exposure of sensitive information such as full names, email addresses, dates of birth, genders, IP addresses, locations, and usernames. The breach occurred because a third party inadvertently exposed the data through a publicly accessible backup.
Breached Data Types:
- Full name
- Email address
- Dates of birth
- Gender
- Location
- Username
- IP Address
Wattpad Breach, 271M
Wattpad is an online platform where users can share their own stories on a wide range of subjects. It’s highly popular, ranking as the 150th most visited website globally. In June 2020, Wattpad suffered a security breach, exposing 271 million user accounts. This included password hashes protected by bcrypt for 145 million users, and 44 million using sha256 encryption.
Breached Data Types:
- Full name
- Phone number
- Facebook ID
- Tumblr password
- Password
- Email address
- Username
- Date of birth
Facebook Breach, 533M
During April 2021, a substantial dataset comprising over 500 million Facebook users became accessible for free download. At the time, this dataset represented around 20% of Facebook’s user base and is believed to have been acquired through exploiting a vulnerability that Facebook claims to have fixed in August 2019. The main significance of this data lies in linking phone numbers to user identities; while each entry included a phone number, only 2.5 million entries also contained an email address. The majority of entries included names and genders, with a significant number also containing dates of birth, locations, relationship statuses, and employers.
Breached Data Types:
- Dates of birth
- Email addresses
- Employers
- Genders
- Geographic locations
- Names
- Phone numbers
- Relationship statuses
Collection #1 Breach, 773M
In January 2019, a significant compilation of credential stuffing lists (pairings of email addresses and passwords utilized to take over accounts on different platforms) was found being circulated on a well-known hacking forum. This data encompassed nearly 2.7 billion entries, consisting of 773 million distinct email addresses coupled with the passwords linked to those addresses from other breached services.
Breached Data Types:
- Email addresses
- Passwords
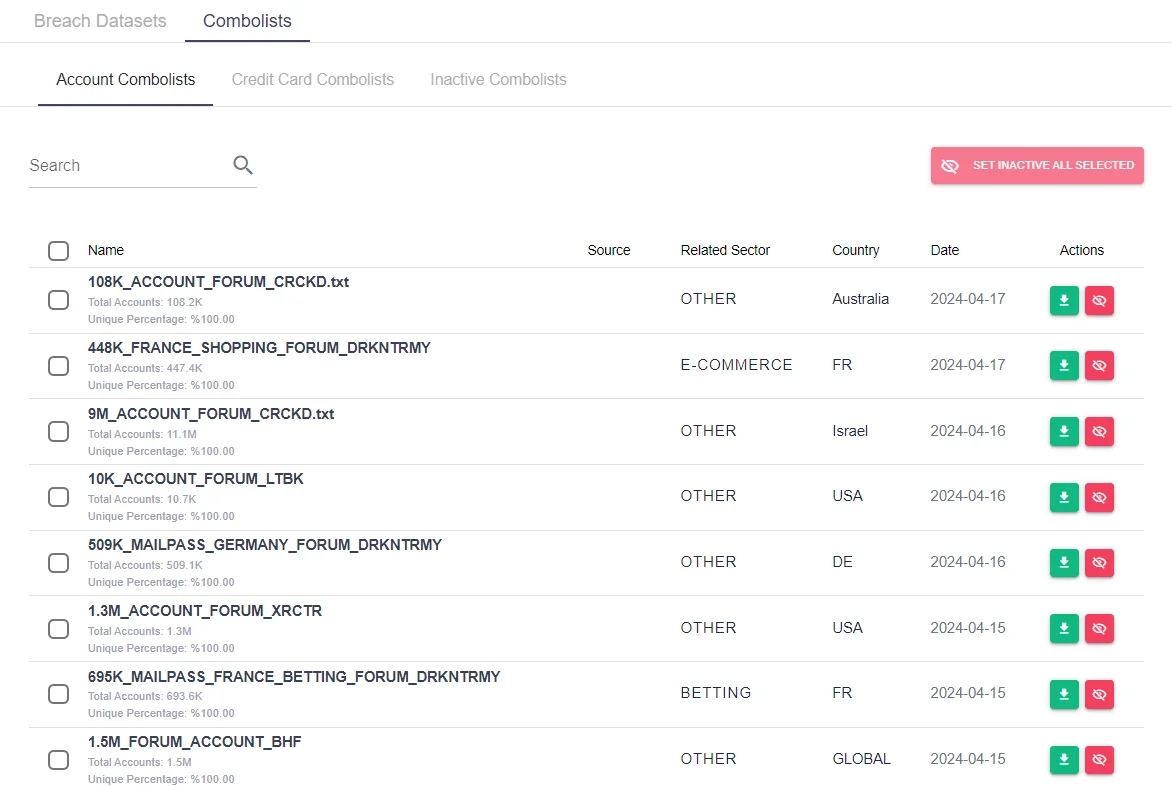
Combolists that are designed and cleaned for specific purposes are also listed in SOCRadar Platform
Table of Breaches
| Breach Name | Number of Affected Users | Types of Data Exposed |
| Evite Breach | 160 million | Names, phone numbers, physical addresses, dates of birth, genders, passwords (plain text) |
| Dubsmash Breach | 162 million | Email addresses, geographic locations, names, passwords, phone numbers, spoken languages, usernames |
| VNG Zing Breach | 163 million | Usernames, passwords |
| LinkedIn Breach | 164.6 million | Email addresses, passwords |
| Zynga Breach | 172 million | Email addresses, passwords, phone numbers, usernames |
| Cit0Day Breach | 226 million | Usernames, emails, addresses, cleartext passwords |
| Deezer Breach | 244.3 million | Full names, email addresses, dates of birth, genders, IP addresses, locations, usernames |
| Wattpad Breach | 271 million | Full name, email address, dates of birth, gender, location, username, IP address |
| Facebook Breach | 533 million | Dates of birth, email addresses, employers, genders, geographic locations, names, phone numbers, relationship statuses |
| Collection #1 Breach | 773 million | Email addresses, passwords |
These breaches are listed in SOCRadar Platform as Data Breach Sets
The highlighted data breaches showcase the widespread and significant impact of cyberattacks on various platforms and services. These breaches have exposed sensitive personal information such as names, email addresses, passwords, phone numbers, and even cleartext passwords in some cases. The sheer scale of the breaches, with millions to billions of user accounts affected, emphasizes the urgency of implementing robust cybersecurity measures.



































