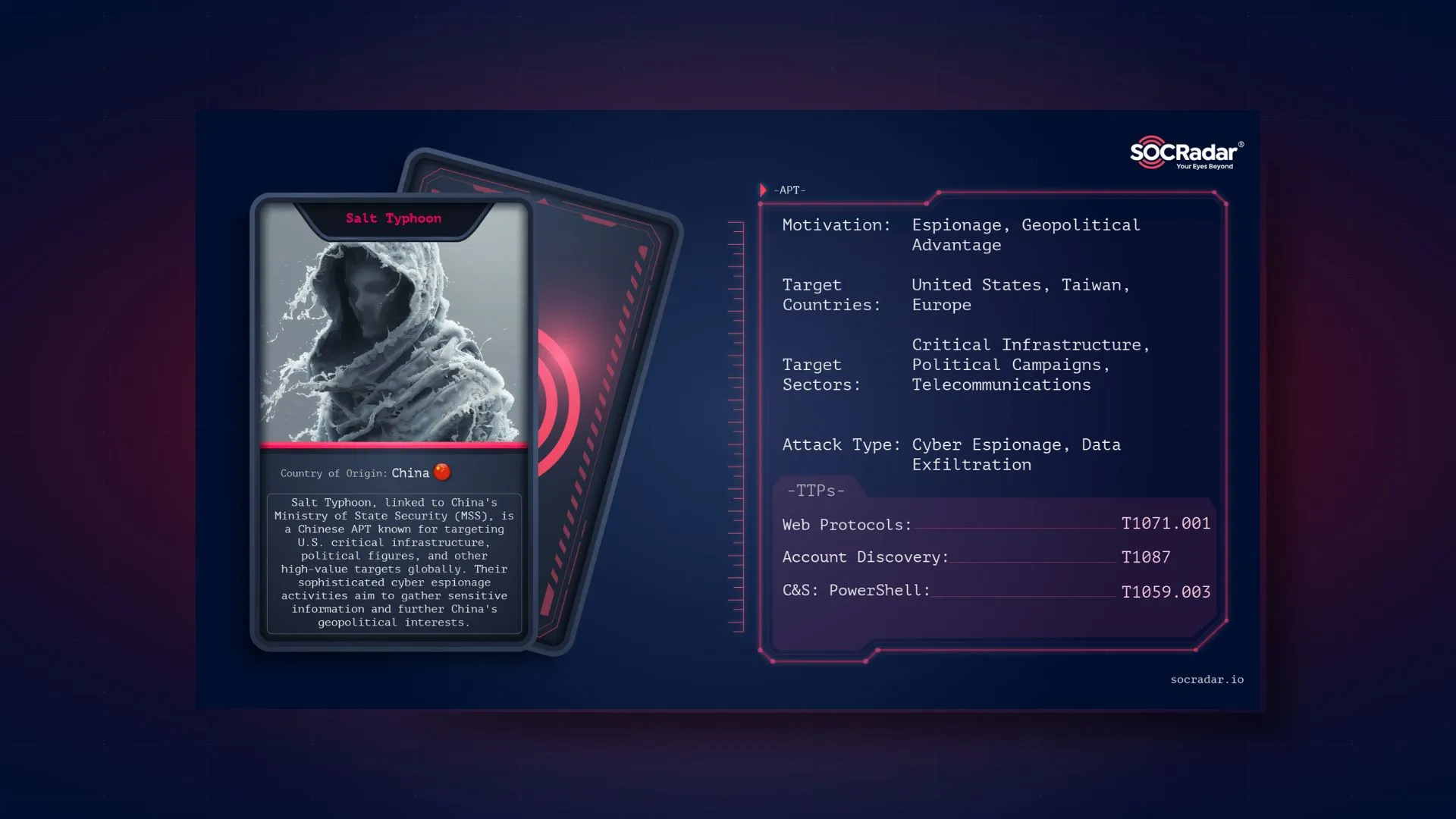
Dark Web Profile: Salt Typhoon
Dark Web Profile: Salt Typhoon [Update] February 15, 2025: “Salt Typhoon Exploited Cisco Router Flaws and Breached Telecoms” Salt Typhoon, a Chinese state-sponsored Advanced Persistent Threat (APT), h...

Critical Ivanti CSA Auth Bypass (CVE-2024-11639) Patched Alongside Oth...
Critical Ivanti CSA Auth Bypass (CVE-2024-11639) Patched Alongside Other High-Impact Flaws Ivanti recently released critical security updates to address several high-impact vulnerabilities in its prod...

Cryptojacking Campaign Targets Docker and Kubernetes: Surge in Contain...
Cryptojacking Campaign Targets Docker and Kubernetes: Surge in Container-Based Attacks A recent surge in cryptojacking campaigns has targeted unsecured Docker and Kubernetes environments, exploiting m...

December 2024 Patch Tuesday Update – One Actively Exploited Zero-Day, ...
December 2024 Patch Tuesday Update – One Actively Exploited Zero-Day, Multiple Critical RCEs; SAP Updates [Update] January 2, 2025: “PoC Exploit Available for Critical CVE-2024-49112 “LDAP Nightmare” ...

What Makes SOCRadar a Game-Changer in Threat Intelligence
What Makes SOCRadar a Game-Changer in Threat Intelligence Today, when cyber threats are advancing at a rate never seen before, it’s no longer enough to rely on static tools or fragmented solutions. Bu...

Termite Ransomware Attack on Blue Yonder: What You Need to Know
Termite Ransomware Attack on Blue Yonder: What You Need to Know In late November 2024, Blue Yonder, a critical provider of supply chain management solutions, fell victim to a ransomware attack attribu...

OpenWrt’s Attended SysUpgrade (ASU) Vulnerability Exposes Routers to M...
OpenWrt’s Attended SysUpgrade (ASU) Vulnerability Exposes Routers to Malicious Firmware Attacks OpenWrt, a popular open-source Linux-based embedded operating system, recently discovered a critical vul...

Dark Web Profile: Ymir Ransomware
Dark Web Profile: Ymir Ransomware The emergence of Ymir ransomware adds a new layer to the cybersecurity landscape, featuring advanced tactics that challenge traditional security defenses. Originating...

Top Software Weaknesses of 2024 by MITRE (Critical Insights for Every ...
Top Software Weaknesses of 2024 by MITRE (Critical Insights for Every Organization) The 2024 CWE Top 25 Most Dangerous Software Weaknesses list provides an essential roadmap for identifying the most p...

Renault India Breach, 147M Stealer Logs, Cardinal Health Leak, Univers...
Renault India Breach, 147M Stealer Logs, Cardinal Health Leak, University ESXi & Saudi Company Access Sales In the last week, SOCRadar’s Dark Web Team has identified multiple critical cyber threat...

Mitel MiCollab PoC Exploit Links CVE-2024-41713 and Zero-Day, Exposing...
Mitel MiCollab PoC Exploit Links CVE-2024-41713 and Zero-Day, Exposing Sensitive Files [Update] January 8, 2025: “CISA Adds Mitel MiCollab Vulnerabilities to KEV Catalog” Cyberattacks tar...

Top 10 Major Cyber Attacks Targeting E-Commerce Industry
Top 10 Major Cyber Attacks Targeting E-Commerce Industry The e-commerce industry has transformed global commerce, offering convenience and accessibility to millions of consumers worldwide. However, th...
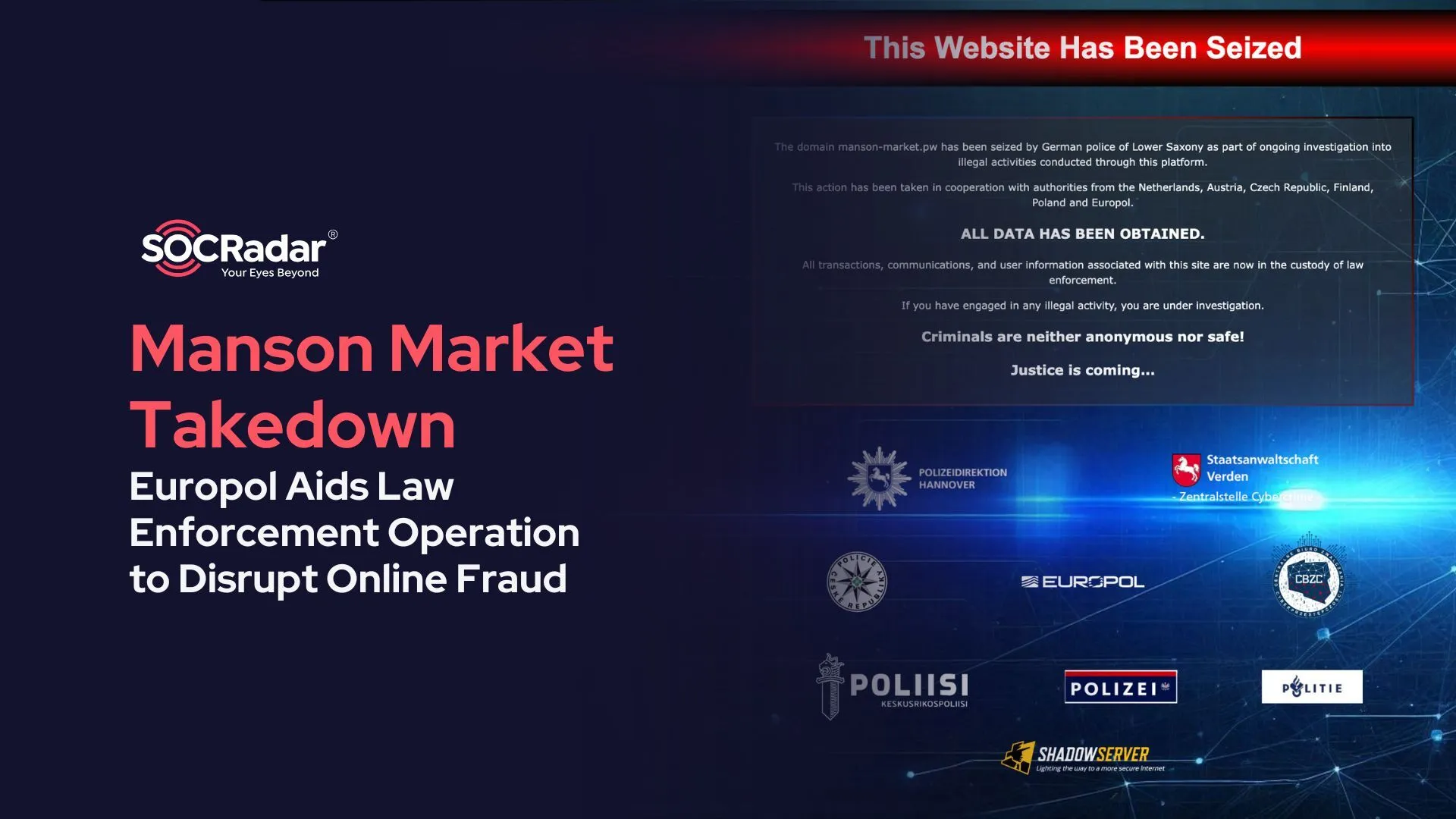
Manson Market Takedown: Europol Aids Law Enforcement Operation to Disr...
Manson Market Takedown: Europol Aids Law Enforcement Operation to Disrupt Online Fraud The digital age has opened the way for increasingly sophisticated cybercriminal networks. These groups target ind...

How Tariffs Impact Supply Chain Security and Strategies to Mitigate Ri...
How Tariffs Impact Supply Chain Security and Strategies to Mitigate Risks Recent announcements regarding new tariffs on China, Mexico, and Canada highlight a looming shift in global trade dynamics. Wi...

Veeam Service Provider Console (VSPC) Users Urged to Patch CVE-2024-42...
Veeam Service Provider Console (VSPC) Users Urged to Patch CVE-2024-42448 and CVE-2024-42449 Veeam has recently released patches addressing two serious security vulnerabilities in its Service Provider...

Old Cisco ASA Vulnerability (CVE-2014-2120) Fuels Androxgh0st Botnet A...
Old Cisco ASA Vulnerability (CVE-2014-2120) Fuels Androxgh0st Botnet Activity Cisco has issued a fresh warning regarding CVE-2014-2120, a decade-old vulnerability in its Adaptive Security Appliance (A...

The Role of Predictive Analytics in Preventing Cyber Attacks
The Role of Predictive Analytics in Preventing Cyber Attacks Digital threats of today require cybersecurity strategies to anticipate and neutralize cyber attacks before they occur. This is where predi...

International Operation Dismantles MATRIX: A Sophisticated Encrypted M...
International Operation Dismantles MATRIX: A Sophisticated Encrypted Messaging Service The importance of international collaboration in the fight against cybercrime has once again been demonstrated. M...

Most Exploited Vulnerabilities of 2023 (Insights to Define Cybersecuri...
Most Exploited Vulnerabilities of 2023 (Insights to Define Cybersecurity in 2025) As we near the close of 2024, cybersecurity remains a top priority for organizations navigating an increasingly hostil...

Nordic Threat Landscape Report 2024: Ransomware, Phishing, and Dark We...
Nordic Threat Landscape Report 2024: Ransomware, Phishing, and Dark Web Insights As a digital hub of innovation and economic stability, the Nordic Region—comprising Denmark, Finland, Iceland, Norway, ...

































