
Alleged Adobe Database Leak, DJI Access Sale, and DDoS Attacks on Poli...
Alleged Adobe Database Leak, DJI Access Sale, and DDoS Attacks on Polish Websites The SOCRadar Dark Web Team discovered several alarming posts on hacker forums and Telegram channels, indicating seriou...

Suspicious Domains Exploiting the Recent CrowdStrike Outage!
Suspicious Domains Exploiting the Recent CrowdStrike Outage! [Update] July 23, 2024: “Researchers Warn of Phishing Scenarios Exploiting the CrowdStrike Outage by Cybercriminals”, “Exploiting Real Time...

CrowdStrike Update Causing Blue Screen of Death and Microsoft 365/Azur...
CrowdStrike Update Causing Blue Screen of Death and Microsoft 365/Azure Outage [Update] August 7, 2024: “New Root Cause Analysis” [Update] July 19, 2024: “Official Statement from the CrowdStrike CEO a...

Critical Vulnerabilities in SolarWinds ARM, Serv-U, and Cisco SSM On-P...
Critical Vulnerabilities in SolarWinds ARM, Serv-U, and Cisco SSM On-Prem, Secure Email Gateway Products [Update] August 9, 2024: “Proof-of-Concept Exploit Available for CVE-2024-20419 Vulnerabi...

Executive Interview: Emerging Trends and Effective Strategies from GCI...
Executive Interview: Emerging Trends and Effective Strategies from GCISO Dan Maslin In our ongoing series of CISO interviews, we are excited to share insights from Dan Maslin, the Group Chief Informat...

SOCRadar’s Global Ransomware Report 2024: Gain Insights Into Worldwide...
SOCRadar’s Global Ransomware Report 2024: Gain Insights Into Worldwide Ransomware Trends As 2024 passes by, ransomware remains a major concern for organizations across the globe. In order to see the t...

Shedding Light on France's Cyber Threat Landscape
Shedding Light on France’s Cyber Threat Landscape In an era of dynamic change in digital threats, there is more need for knowledge of regional cybersecurity challenges than ever. Therefore, it is with...

Key Threat Intelligence Sources to Access Current Threat Insights
Key Threat Intelligence Sources to Access Current Threat Insights Using various threat intelligence sources can make the difference between preventing an attack and falling victim to one. An AI illus...

The 2024 Mid-Year Cybersecurity Review Report
The 2024 Mid-Year Cybersecurity Review Report In a time when cyber threats continue to escalate in sophistication and frequency, understanding the evolving landscape is more crucial than ever. Therefo...

Latest Dark Web Leaks: Disney Slack, U.S. Credit Cards, 1TX Vendor Dat...
Latest Dark Web Leaks: Disney Slack, U.S. Credit Cards, 1TX Vendor Database The SOCRadar Dark Web Team has identified several significant data breaches and cyber threats involving prominent organizati...

Major Cyber Attacks Targeting the Automotive Industry
Major Cyber Attacks Targeting the Automotive Industry Due to its growing connectivity and perceived vulnerabilities, the Automotive Industry is increasingly targeted by cyberattacks, like data breache...

Top 10 SOAR Platforms
Top 10 SOAR Platforms Security Orchestration, Automation, and Response (SOAR) platforms have become critical tools for improving security operations. These platforms integrate and automate security wo...

Microsoft Fixes CVE-2024-38112 After Over a Year of Exploitation; Zero...
Microsoft Fixes CVE-2024-38112 After Over a Year of Exploitation; Zero-Click Threat of CVE-2024-38021 [Update] August 21, 2024: “Researchers Reveal Technical Details of CVE-2024-38021, Urge Reas...

Major Cyber Attacks in Review: June 2024
Major Cyber Attacks in Review: June 2024 June 2024 has been a whirlwind of significant cyber attacks targeting high-profile organizations worldwide. Following the ongoing Snowflake-related issues, the...

July 2024 Patch Tuesday Fixes 139 CVEs, Actively Exploited Zero-Days; ...
July 2024 Patch Tuesday Fixes 139 CVEs, Actively Exploited Zero-Days; CISA Highlights Citrix Updates [Update] September 17, 2024: “PoC Exploit Available for CVE-2024-38080 in Windows Hyper-VR...

Cyber Security Aspect of the 2024 NATO Summit
Cyber Security Aspect of the 2024 NATO Summit [Update] July 11, 2024: “Washington Summit Declaration” The idea of building alliances was already important for increasing the security of kingdoms and l...

Pi-hole RCE Exploit, Netflix Scam Pages, Rockwell Access Sale, and Mas...
Pi-hole RCE Exploit, Netflix Scam Pages, Rockwell Access Sale, and Massive Password Leak The SOCRadar Dark Web Team has identified multiple critical cyber incidents, highlighting ongoing threats to va...

Top 50 Cybersecurity Statistics in 2024 (Essential Insights on Ransomw...
Top 50 Cybersecurity Statistics in 2024 (Essential Insights on Ransomware, Phishing, Industry Trends, and More) Welcome to our roundup of the Top 50 Cybersecurity Statistics in 2024. As cyber threats ...

Dark Peep #15: The Perfect Heist Partner
Dark Peep #15: The Perfect Heist Partner Welcome back to Dark Peep, your backstage pass to the wildest cyber drama on the dark web. In this blockbuster fifteenth edition, the FBI’s raid on BreachForum...
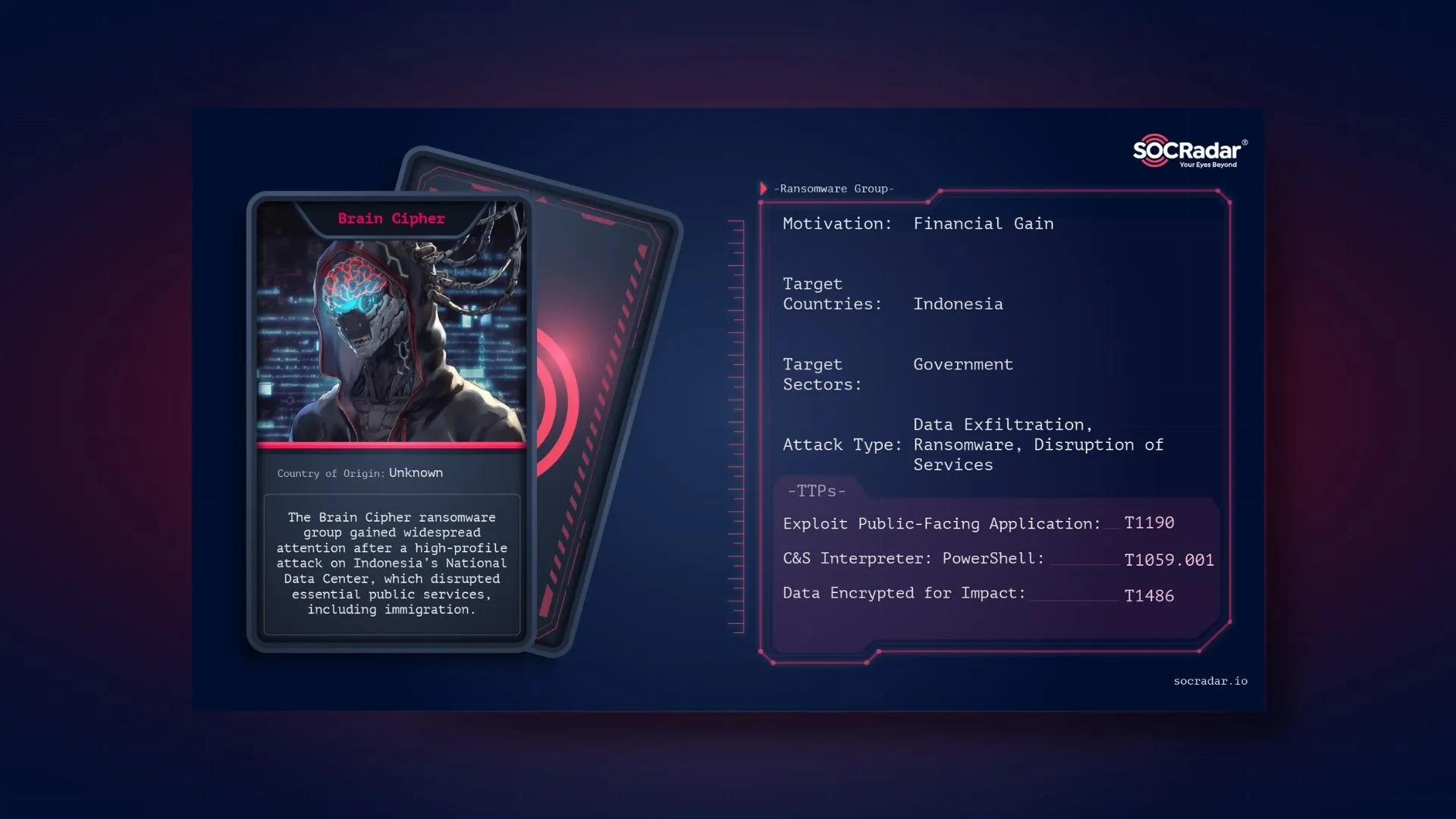
Dark Web Profile: Brain Cipher
Dark Web Profile: Brain Cipher The Brain Cipher ransomware group gained widespread attention after a high-profile attack on Indonesia’s National Data Center (Pusat Data Nasional – PDN), which disrupte...
































