
Alarming Dark Web Leak: B1ack's Stash Releases 4 Million Stolen Credit...
Alarming Dark Web Leak: B1ack’s Stash Releases 4 Million Stolen Credit Cards for Free The Dark Web marketplace B1ack’s Stash has stirred concerns by leaking 4 million stolen credit card de...

EagerBee: Advanced Backdoor Attacks on Middle Eastern Governments and ...
EagerBee: Advanced Backdoor Attacks on Middle Eastern Governments and ISPs In recent years, the cybersecurity landscape has witnessed a surge in sophisticated and highly targeted cyberattacks, with th...

Massive Swiss Medical Leak, Binance Phishing Panel, and WhatsApp Ban S...
Massive Swiss Medical Leak, Binance Phishing Panel, and WhatsApp Ban Service Found SOCRadar’s Dark Web Team has uncovered several alarming cyber threats circulating on hacker forums this week. Key dis...

Top 10 Advanced Persistent Threat (APT) Groups That Dominated 2024
Top 10 Advanced Persistent Threat (APT) Groups That Dominated 2024 Advanced Persistent Threats (APTs) are among the most sophisticated and persistent cyber adversaries in the world. Unlike ordinary cy...

Palo Alto Firewall Vulnerability (CVE-2025-0108) Under Attack – Are Yo...
Palo Alto Firewall Vulnerability (CVE-2025-0108) Under Attack – Are You at Risk? [Update] February 19, 2025: “Escalating Exploitation of CVE-2025-0108” Palo Alto Networks has addressed a n...
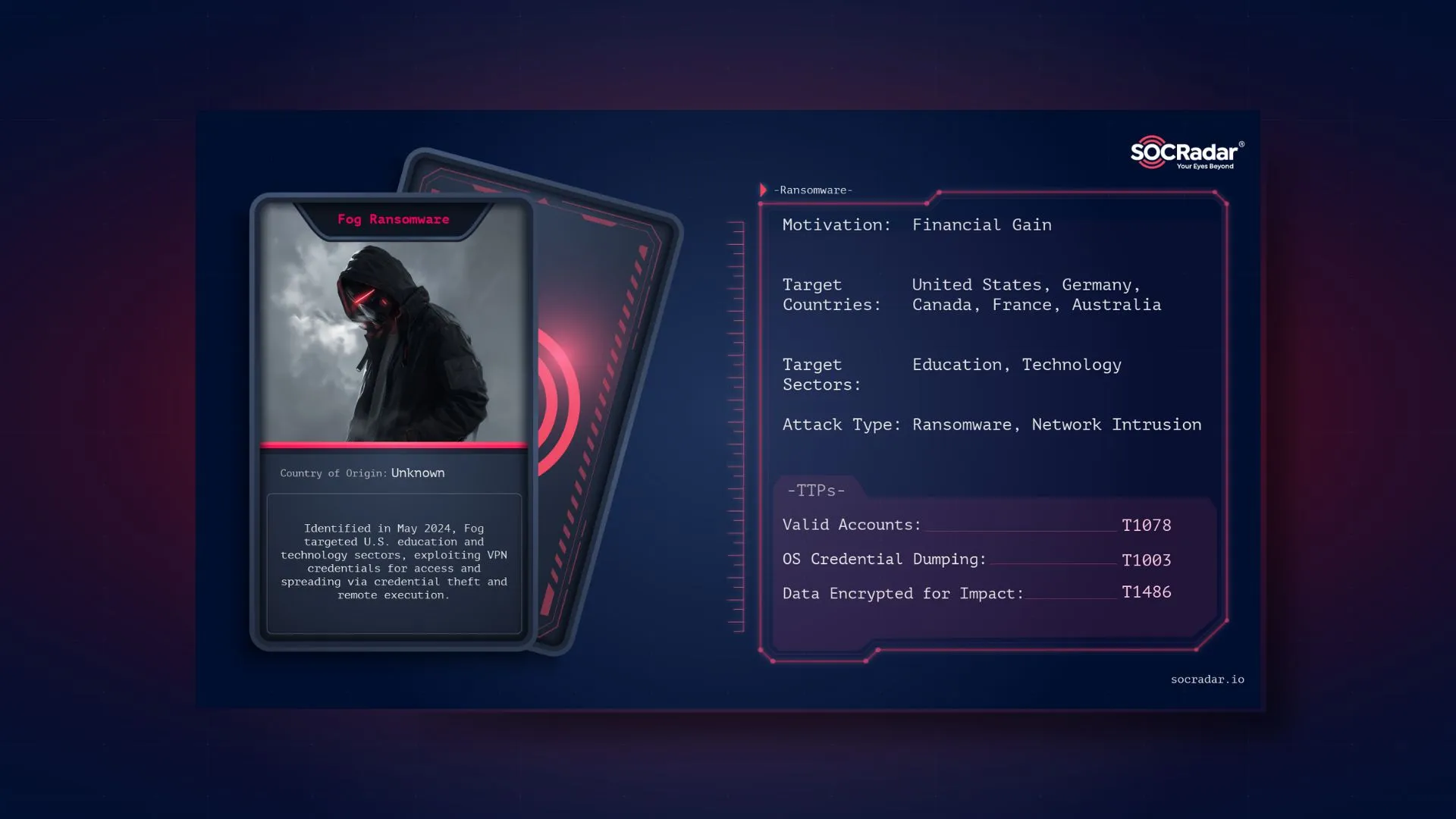
Dark Web Profile: Fog Ransomware
Dark Web Profile: Fog Ransomware Fog Ransomware emerged in April 2024, was first detected in the wild in early May, primarily targeting US based educational institutions targeting both Windows and Lin...

Ivanti Security Update Addresses Severe Vulnerabilities in ICS, IPS, a...
Ivanti Security Update Addresses Severe Vulnerabilities in ICS, IPS, and ISAC (CVE-2025-22467, CVE-2024-38657, CVE-2024-10644) In response to newly identified vulnerabilities, Ivanti has released secu...

Lazarus Group’s Latest Cyber Espionage Tactics Involving LinkedIn
Lazarus Group’s Latest Cyber Espionage Tactics Involving LinkedIn The Lazarus Group, a North Korean government-backed hacking team, has increased its spying efforts by taking advantage of work network...

February 2025 Patch Tuesday: Microsoft Fixes 63 Vulnerabilities, Inclu...
February 2025 Patch Tuesday: Microsoft Fixes 63 Vulnerabilities, Including Two Actively Exploited Zero-Days Microsoft’s latest Patch Tuesday update for February 2025 delivers important security ...

International Operation Targets 8Base and Phobos Ransomware Gangs
International Operation Targets 8Base and Phobos Ransomware Gangs In a coordinated global effort, law enforcement agencies have successfully dismantled the dark web infrastructure of the 8Base ransomw...

Key Insights from the 2024 End-of-Year Report: Preparing for Cyber Thr...
Key Insights from the 2024 End-of-Year Report: Preparing for Cyber Threats in 2025 The cyber threat landscape in 2024 witnessed an unprecedented surge in sophisticated attacks, with cybercriminals lev...

Major Cyber Attacks in Review: January 2025
Major Cyber Attacks in Review: January 2025 In January 2025, high-profile cyber incidents affecting industries ranging from healthcare and telecommunications to AI and finance made headlines. From the...

Dread: The Dark Web’s Reddit-Like Forum
Dread: The Dark Web’s Reddit-Like Forum Dark web forums are crucial gathering points for cybercriminals, facilitating illegal trade, data breaches, and financial fraud. According to SOCRadar’s Annual ...

Massive OpenAI Leak, WordPress Admin Exploit, Inkafarma Data Breach
Massive OpenAI Leak, WordPress Admin Exploit, Inkafarma Data Breach SOCRadar’s Dark Web Team has detected a wave of cyber threats on hacker forums this week, including an alleged leak of millions of O...

The Escalating Threat of the Dark Web to Small and Medium Enterprises ...
The Escalating Threat of the Dark Web to Small and Medium Enterprises (SMBs) The Dark Web poses significant threats to Small and Medium-sized Businesses (SMBs) because it serves as a marketplace for c...

What You Need to Know About Non-Human Identities?
What You Need to Know About Non-Human Identities? Meta CEO Mark Zuckerberg recently stated that AI will replace mid-level engineers by 2025, taking over coding tasks to allow human developers to focus...
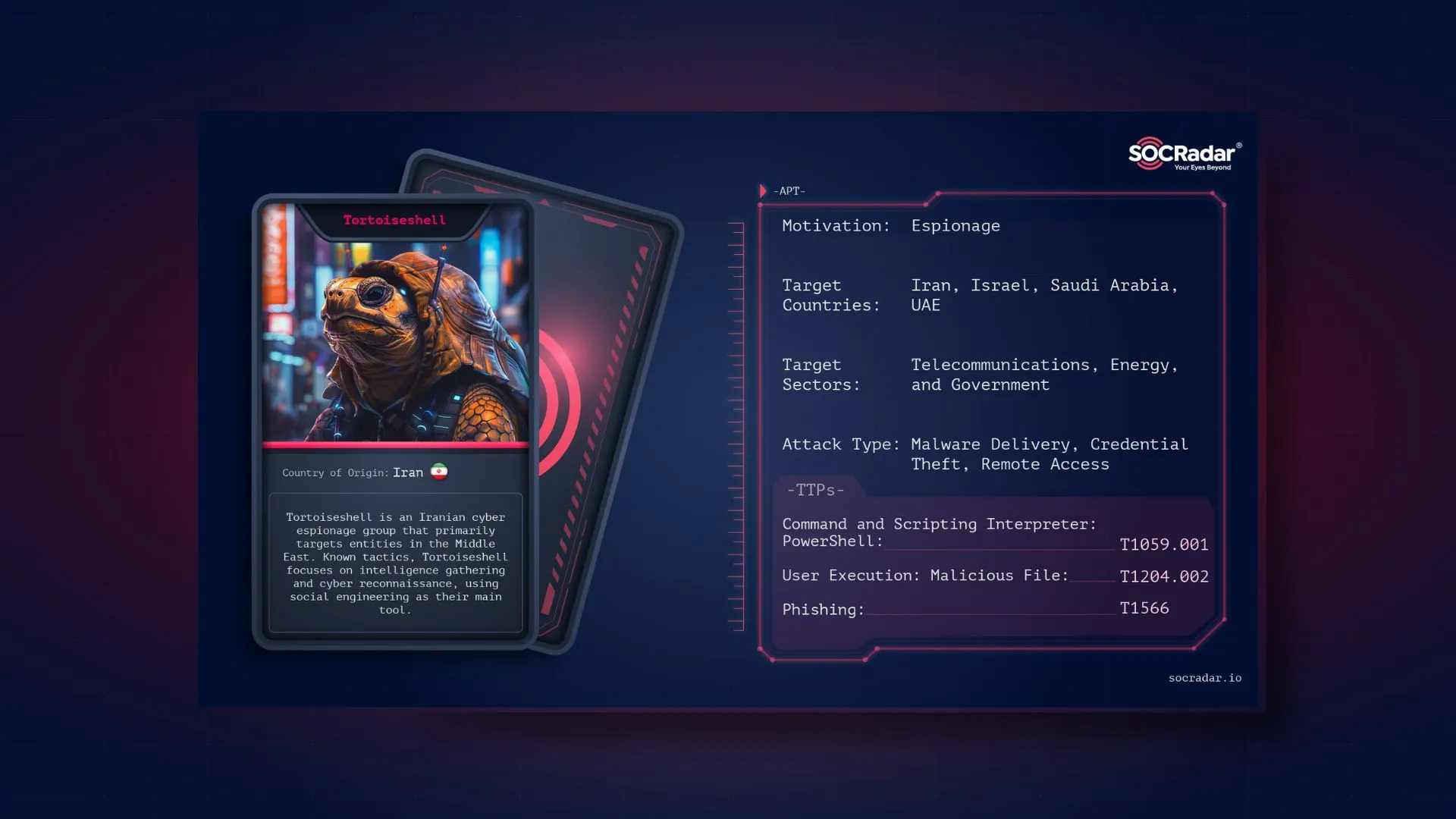
Dark Web Profile: Tortoiseshell APT
Dark Web Profile: Tortoiseshell APT In recent years, Iran has ramped up cyber campaigns to safeguard national interests, deter adversaries, and conduct espionage. These operations are carried out by u...

The Hidden Risks of Public Wi-Fi Networks: A Guide for Laptop Users
The Hidden Risks of Public Wi-Fi Networks: A Guide for Laptop Users Coffee shops, airports, hotels, and other public places often offer free Wi-Fi, which is a great perk for people who use laptops in ...

Critical Cisco ISE Vulnerabilities Patched: CVE-2025-20124 & CVE-2025-...
Critical Cisco ISE Vulnerabilities Patched: CVE-2025-20124 & CVE-2025-20125 Cisco has issued a security advisory regarding two critical vulnerabilities in its Identity Services Engine (ISE), CVE-2...

CISA Adds Apache OFBiz, Microsoft .NET, and Paessler PRTG Vulnerabilit...
CISA Adds Apache OFBiz, Microsoft .NET, and Paessler PRTG Vulnerabilities to the KEV Catalog The Cybersecurity and Infrastructure Security Agency (CISA) has recently updated its Known Exploited Vulner...
































