
Browser Security 101: Protecting Your Online Activity
Browser Security 101: Protecting Your Online Activity In today’s interconnected world, browser security has become paramount for both individuals and organizations. As we conduct more of our daily act...

Top 10 Free and Open-Source Tools for MSSPs
Top 10 Free and Open-Source Tools for MSSPs In the rapidly evolving landscape of cybersecurity, Managed Security Service Providers (MSSPs) face increasing challenges in protecting their clients’...

Critical Veeam Vulnerability (CVE-2025-23114) Exposes Backup Servers t...
Critical Veeam Vulnerability (CVE-2025-23114) Exposes Backup Servers to Remote Code Execution On February 4, 2025, a critical security vulnerability identified as CVE-2025-23114 was disclosed, affecti...

Top 10 Cybersecurity Podcasts You Must Follow in 2025
Top 10 Cybersecurity Podcasts You Must Follow in 2025 In the fast-paced world we live in, staying updated on the latest cybersecurity trends can be challenging. Podcasts are an easy and accessible way...

February 2025 Android Updates by Google; Severe Flaws in VMware & ...
February 2025 Android Updates by Google; Severe Flaws in VMware & Microsoft’s Azure AI Recent days have brought a wave of critical security updates from major tech players, addressing vulnerabilit...

IntelBroker Strikes HPE Again, Cardinal Health Breach, and U.S. ISP Ro...
IntelBroker Strikes HPE Again, Cardinal Health Breach, and U.S. ISP Root Access Sale SOCRadar’s Dark Web Team has identified alarming cyber threats this week, including a second alleged data leak from...
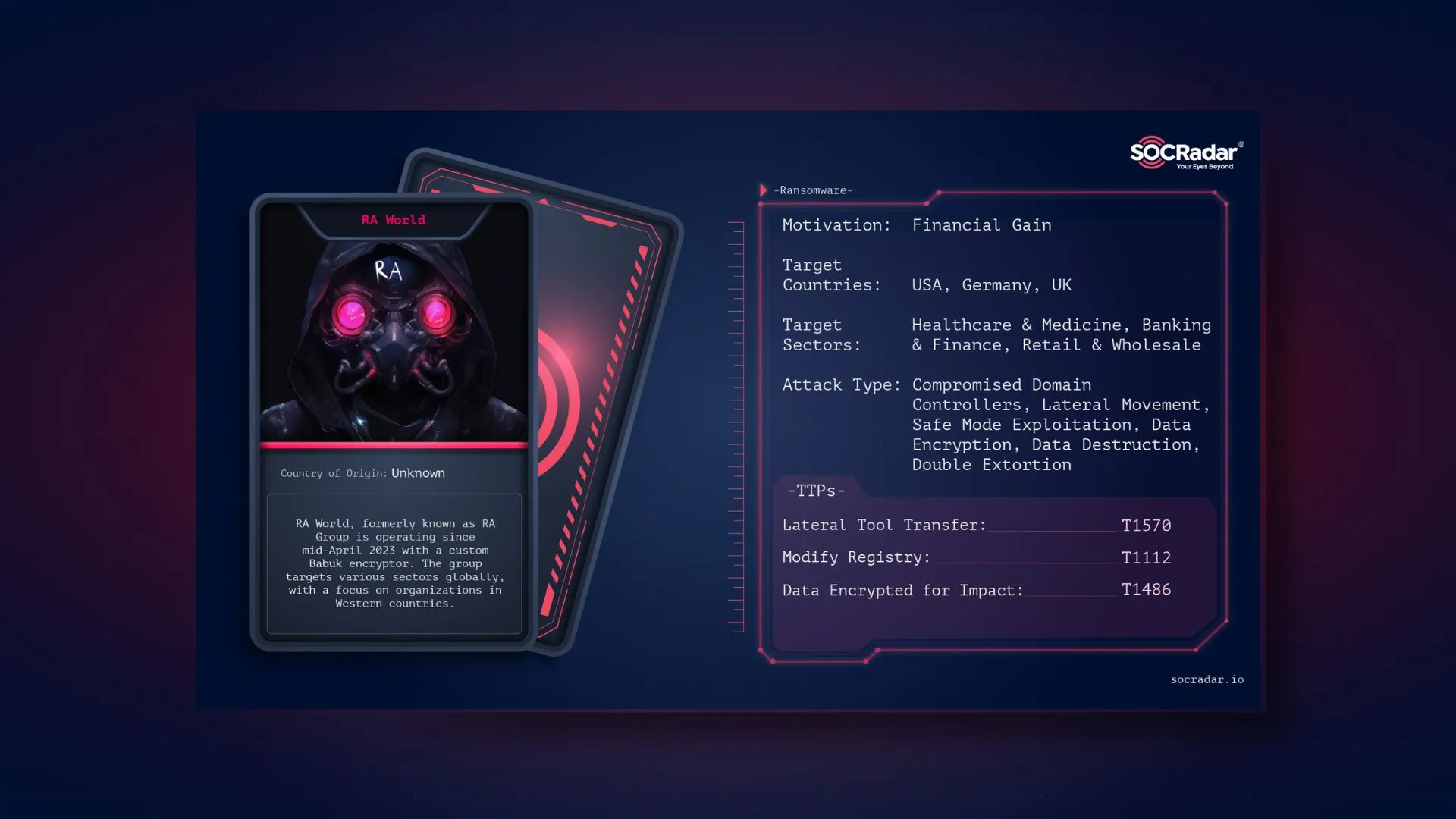
Dark Web Profile: RA World
Dark Web Profile: RA World RA World is believed to be a rebranded iteration of the ransomware operation previously known as RA Group. This is because it employed the same extortion and encryption tech...

CISA Warns of Backdoor in Contec CMS8000 Patient Monitors
CISA Warns of Backdoor in Contec CMS8000 Patient Monitors The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical advisory regarding a backdoor discovered in the Contec CMS80...

The Role of Firewalls in Modern Computer Security
The Role of Firewalls in Modern Computer Security Firewalls are an essential part of modern computer security, acting as network protection’s first line of defense. Via regulating incoming and o...

How to Spot and Avoid Malicious Apps on App Stores
How to Spot and Avoid Malicious Apps on App Stores The increasing integration of mobile applications into daily life has created significant security challenges that affect individuals, organizations,...

Dark Web Profile: Termite Ransomware
Dark Web Profile: Termite Ransomware The dark web, a hidden part of the internet, remains a source of growing cyber threats, with ransomware being one of the most prominent. Among these threats, Termi...

Why Threat Intelligence is a Game-Changer for Pentesting & Red Tea...
Why Threat Intelligence is a Game-Changer for Pentesting & Red Teaming ...

Operation Talent: FBI Takes Down Cracked.io and Nulled.to in Global Cy...
Operation Talent: FBI Takes Down Cracked.io and Nulled.to in Global Cybercrime Crackdown In a significant blow to cybercrime, the FBI, in collaboration with international law enforcement agencies, has...

TorNet Backdoor: A Stealthy Cyber Threat Targeting Poland and Beyond
TorNet Backdoor: A Stealthy Cyber Threat Targeting Poland and Beyond Put in peril by financial motives, an actor described as a financial threat actor has been conducting an ongoing malicious campaign...

Top 10 Exploited Vulnerabilities of 2024
Top 10 Exploited Vulnerabilities of 2024 Organizations face a relentless battle against vulnerabilities that threaten their critical assets, and 2024 has proven to be no exception. Cybersecurity teams...

Is DeepSeek Safe? A Q&A on the Cybersecurity Risks of the AI Platform
Is DeepSeek Safe? A Q&A on the Cybersecurity Risks of the AI Platform [Update] March 3, 2025: “DeepSeek’s Training Data Exposed Nearly 12,000 Live API Keys” [Update] February 4, 2025: “Malicious ...

Top 10 Threat Intelligence Conferences to Attend in 2025
Top 10 Threat Intelligence Conferences to Attend in 2025 The rapidly evolving cybersecurity landscape demands constant vigilance, innovation, and collaboration. For professionals in threat intelligenc...

Operation Digital Eye: Exploiting Visual Studio Code Tunnels for Advan...
Operation Digital Eye: Exploiting Visual Studio Code Tunnels for Advanced Intrusions Operation Digital Eye is a cutting-edge cyber campaign executed by Chinese Advanced Persistent Threat (APT) groups....

Dark Web Profile: FunkSec
Dark Web Profile: FunkSec [Update] January 4, 2024: “Update: FunkSec Expands Their Operation and Teams Up With Other Cyber Criminals” A new ransomware group, FunkSec, has gained attention after taking...

The Meeten Campaign: Realst Stealer’s Return Under Guise of Meeting Ap...
The Meeten Campaign: Realst Stealer’s Return Under Guise of Meeting Apps The cybersecurity landscape faces constant evolution, and recent threats highlight the urgency of vigilance. One such sophistic...































