
An Overview of the Nominet Security Breach Tied to Ivanti VPN Vulnerab...
An Overview of the Nominet Security Breach Tied to Ivanti VPN Vulnerability (CVE-2025-0282) [Update] January 17, 2025: “PoC Exploit Released for Ivanti Connect Secure CVE-2025-0282 Vulnerability...

Dux Human Health Breach, U.S. Credit Card Sale, Boulanger Database Lea...
Dux Human Health Breach, U.S. Credit Card Sale, Boulanger Database Leak, and More SOCRadar’s Dark Web Team has monitored concerning activity on hacker forums over the past week, revealing significant ...

Major Cyber Attacks in Review: December 2024
Major Cyber Attacks in Review: December 2024 December 2024 saw a series of significant cyber attacks that targeted multiple industries, from healthcare to telecommunications. Ransomware groups like Bl...

Ivanti Zero-Day Exploited in Connect Secure, SonicWall SSL VPN and SSH...
Ivanti Zero-Day Exploited in Connect Secure, SonicWall SSL VPN and SSH Vulnerabilities, KerioControl Flaw [Update] February 17, 2025: “SPAWNCHIMERA Malware Actively Exploiting CVE-2025-0282̶...

The Role of Cybersecurity in Protecting Critical Infrastructure: Focus...
The Role of Cybersecurity in Protecting Critical Infrastructure: Focus on Energy and Water Sectors Critical infrastructure serves as the foundation of modern society, encompassing the systems and asse...

End of the Year Report 2024: Uncovering Global Cyber Threats and Trend...
End of the Year Report 2024: Uncovering Global Cyber Threats and Trends As we close the chapter on 2024, the global cybersecurity landscape reveals a year of unprecedented challenges and transformativ...

Gravy Analytics Breach Puts Millions of Location Records at Risk and H...
Gravy Analytics Breach Puts Millions of Location Records at Risk and Highlights Privacy Threats In an alarming security event, Gravy Analytics, a location data broker, has allegedly fallen victim to a...

Turla Cyber Campaign Targeting Pakistan's Critical Infrastructure
Turla Cyber Campaign Targeting Pakistan’s Critical Infrastructure Among the most notorious cyber threat actors, the Turla group has garnered attention for its sophisticated and complex cyber att...

The Importance of Cyber Hygiene: Best Practices for Employees to Preve...
The Importance of Cyber Hygiene: Best Practices for Employees to Prevent Data Breaches Cyber hygiene has never been more crucial in the current digital era. Because cyber dangers are getting more comp...

Comprehensive Guide to IoC Enrichment and SOCRadar's New IoC Enrichmen...
Comprehensive Guide to IoC Enrichment and SOCRadar’s New IoC Enrichment Module The ability to quickly and accurately identify potential threats is crucial. Indicator of Compromise (IoC) enrichment is ...

Black Basta’s Tactical Evolution: Deploying Zbot, DarkGate, and Bespok...
Black Basta’s Tactical Evolution: Deploying Zbot, DarkGate, and Bespoke Malware In the ever-escalating landscape of cyber threats, Black Basta has emerged as a formidable ransomware group, continually...
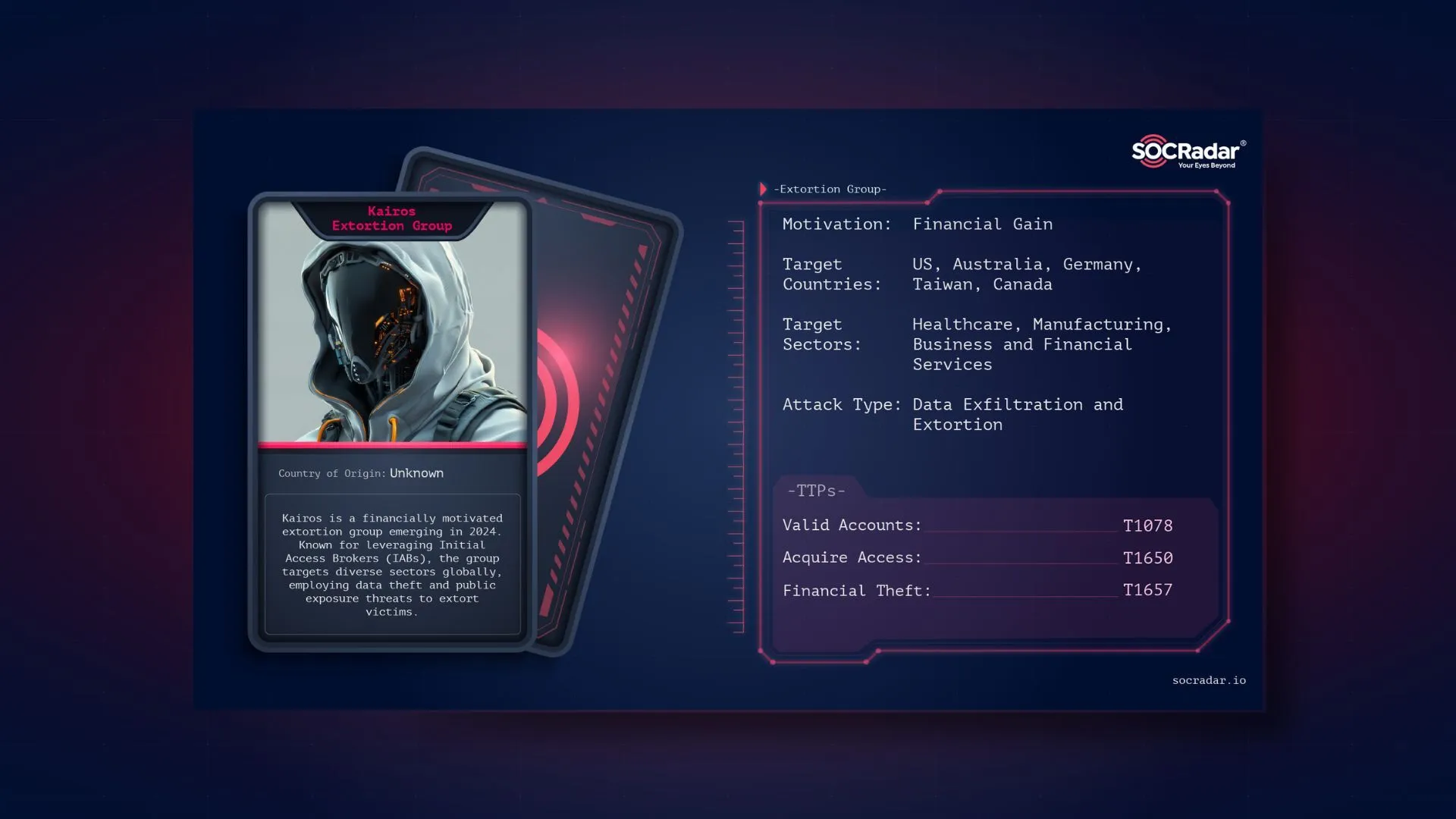
Dark Web Profile: Kairos Extortion Group
Dark Web Profile: Kairos Extortion Group Kairos is a low-profile but rising cyber extortion group that has been active since late 2024. Unlike many of its counterparts, Kairos does not rely on ransomw...

Hacker Forums Reveal ICAO Leak, SonicWall Vulnerability, and Other New...
Hacker Forums Reveal ICAO Leak, SonicWall Vulnerability, and Other New Exploit Sales Recent findings from SOCRadar’s Dark Web Team spotlight a series of alarming cyber threats surfacing on hacke...

Cybersecurity in 2025: A Look Back at 2024’s Biggest Cyber Attacks &am...
Cybersecurity in 2025: A Look Back at 2024’s Biggest Cyber Attacks & Lessons for the Future The year 2024 saw a surge in high-profile cyber attacks across various industries, exposing the vulnerab...

Dark Web Monitoring Tools and How They Benefit Businesses
Dark Web Monitoring Tools and How They Benefit Businesses Now as we all know, in depths of the internet lies the Dark Web, a hidden network where cybercriminals thrive. Here, stolen credentials, finan...

Cerberus Unchained: The Multi-Stage Trojan Banking Campaign Targeting ...
Cerberus Unchained: The Multi-Stage Trojan Banking Campaign Targeting Android Devices The Cerberus Android banking trojan has reemerged in a sophisticated multi-stage attack campaign targeting banking...

The WarmCookie Malware Campaign: A Sneaky Threat Posed by Fake Browser...
The WarmCookie Malware Campaign: A Sneaky Threat Posed by Fake Browser Updates The WarmCookie malware campaign poses a significant threat by deceiving users into downloading malicious software under t...

SOCRadar’s Integrated Takedown Management: A New Era of Online Threat ...
SOCRadar’s Integrated Takedown Management: A New Era of Online Threat Mitigation SOCRadar’s Integrated Takedown Management offers a new way for brands to protect themselves from a growing number of di...

Welcome to SOCRadar’s 2024 Saudi Arabia Threat Landscape Report!
Welcome to SOCRadar’s 2024 Saudi Arabia Threat Landscape Report! As a leading economic powerhouse in the Middle East and a global energy leader, Saudi Arabia has become an increasingly attractive targ...

Critical Vulnerabilities in Progress WhatsUp Gold (CVE-2024-12108, CVE...
Critical Vulnerabilities in Progress WhatsUp Gold (CVE-2024-12108, CVE-2024-12106); PoC Available for Oracle WebLogic Flaw Three severe vulnerabilities have recently been uncovered in WhatsUp Gold, a ...
































