Cactus Ransomware Employs Unique Encryption Techniques to Avoid Detection
Researchers discovered a new ransomware group called Cactus, operating since at least March 2023. Cactus steals data and encrypts files like other ransomware operations but uses a different method to avoid detection.
Cactus, according to researchers, gains initial access to the victim network by exploiting known vulnerabilities in Fortinet VPN appliances. Using the vulnerabilities, the threat actor gained access to the networks of major commercial organizations.
How Does Cactus Ransomware Operate?
Cactus sets itself apart from other ransomware operations by using encryption to safeguard its binary. The actor uses a batch script to obtain the encryptor binary using 7-Zip. To avoid detection, the attackers utilize a batch script and 7-Zip to acquire the encryptor binary; they then deploy the encryptor binary with an execution flag and remove the original ZIP archive.
The Kroll researchers identified three primary execution modes. To establish persistence and store data in the C:ProgramDatantuser.dat file, attackers use the -s (setup) and -r (read configuration) command line arguments. The encryptor later accesses the file using the -r command line argument.
The attackers supply a unique AES key via the -i (encryption) command line argument to perform file encryption. This key is required to decrypt the ransomware’s configuration file and the public RSA key used to encrypt files. The HEX string containing the key is hardcoded into the encryptor binary, and decoding it reveals encrypted data that can be unlocked using the AES key.
Upon executing the binary with the appropriate -i parameter key, data can be accessed, and the malware can search for files and initiate a multi-thread encryption process.
Use of Different Extensions Before and After Encryption
The ransomware researcher Michael Gillespie stated that Cactus employs different file extensions for targeted files depending on its processing state.
Before encryption, Cactus changes the file extension to CTS0, and after encryption, it changes the extension to CTS1. Additionally, Cactus has a quick mode. The ransomware encrypts files twice and adds a new extension after each process (.CTS1.CTS7) when run in both quick and normal modes.
Cactus Ransomware: Tactics and Techniques
After gaining access to the network, the attackers utilize a scheduled task to maintain persistent access through an SSH backdoor that could be accessed from the command and control server.
Kroll investigators found that Cactus utilized SoftPerfect Network Scanner (netscan) to search for valuable targets on the network.
To carry out more extensive reconnaissance, the attacker employed PowerShell commands to enumerate endpoints, locate user accounts by inspecting successful logins in the Windows Event Viewer, and ping remote hosts. Cactus ransomware also made use of a modified version of the open-source PSnmap Tool, a PowerShell equivalent of the nmap network scanner.
The ransomware operators employ multiple remote access methods, including legitimate tools such as Splashtop, AnyDesk, and SuperOps RMM, as well as Cobalt Strike and the Go-based proxy tool Chisel.
After achieving privilege escalation on a machine, Cactus operators run a batch script that removes the most commonly used antivirus products.
As with most ransomware operations, Cactus steals data from its victims. The threat actor then transfers the stolen files directly to cloud storage using the Rclone tool. Following data exfiltration, the attackers use a PowerShell script called TotalExec to automate the encryption process, a technique that the Black Basta ransomware group has frequently used.
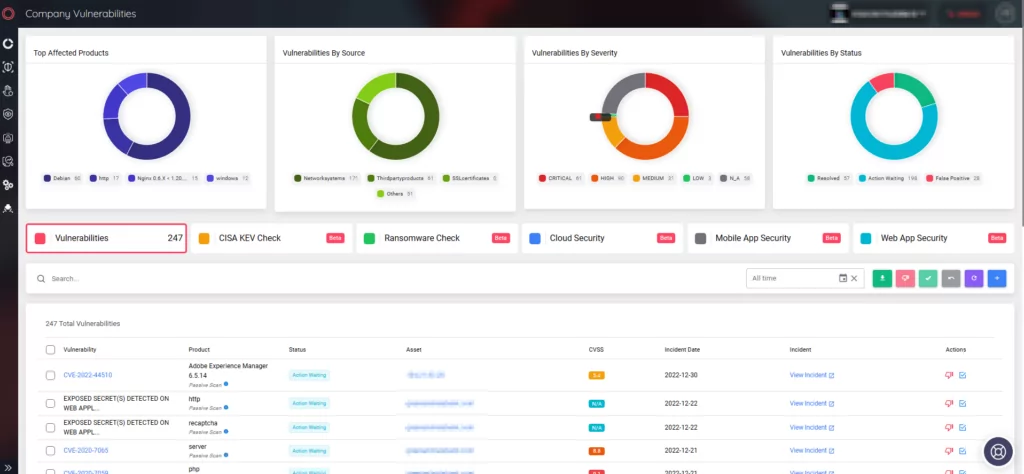
Despite threatening to publish the stolen files, it does not appear that Cactus set up a leak site, as evidenced by the ransom note below:
Akira Ransomware Attacks 16 Companies with Unique Negotiation System
In addition to Cactus, another ransomware group called Akira has also been causing havoc.
Akira ransomware, launched in March 2023, has attacked at least 16 companies worldwide from various industries, such as education, finance, real estate, manufacturing, and consulting.
It uses a PowerShell command to delete Windows Shadow Volume Copies on a device and then encrypts files that have certain file extensions:
powershell.exe -Command "Get-WmiObject Win32_Shadowcopy | Remove-WmiObject"The ransomware encrypts files by appending the .akira extension to the file’s name and leaves a ransom note named “akira_readme.txt” in each computer folder.
During encryption, certain files are excluded by the encryptor, including those found in specific folders such as the Recycle Bin, System Volume Information, Boot, ProgramData, and Windows. Additionally, Windows system files with .exe, .lnk, .dll, .msi, and .sys file extensions are not encrypted. It also uses the Windows Restart Manager API to close processes that might prevent encryption.
Each victim of Akira ransomware receives a unique negotiation password to access the ransomware gang’s Tor site, which features a chat system for victims to communicate and negotiate with the attackers.
If the victim fails to agree, the ransom note threatens to sell personal information, trade secrets, databases, and source codes to multiple threat actors.
Akira has leaked data from four victims, with the size of the leak ranging from 5.9 GB to 259 GB. The ransom demanded by the gang varies from $200,000 to millions, but they may reduce the amount for companies who just want to prevent data leaks and don’t require decryption.
Mitigate Ransomware Threats with SOCRadar
SOCRadar Extended Threat Intelligence (XTI) provides its users with the most recent feed. The platform continuously tracks both existing and emerging threats and alerts your organization in the event of any impact. You can view information about threat actors, updates in their activity, and all malware threats on the Threat Actor/Malware tab on the SOCRadar platform.
Be sure to upgrade all vulnerable instances to prevent threat actors from exploiting vulnerabilities. SOCRadar’s Company Vulnerabilities page allows you to monitor any alarms related to vulnerable instances.