Critical and High Vulnerabilities in Citrix ADC and Citrix Gateway (CVE-2023-3519, CVE-2023-3466, CVE-2023-3467)
What are the vulnerabilities in Citrix, when were they released, what are they used for, and why are they so important?
Citrix ADC and Citrix Gateway have critical vulnerabilities (CVE-2023-3519, CVE-2023-3466, CVE-2023-3467) that pose severe risks, including unauthenticated remote code execution, privilege escalation, and reflected cross-site scripting. These flaws can lead to unauthorized access, data breaches, and system compromise. Prompt action is crucial to secure affected systems by applying updates and mitigations to prevent potential exploits.
The vulnerabilities’ significance stems from their potential to cause significant damage, as attackers can remotely execute code without user interaction, making it essential for organizations to act swiftly to safeguard their networks and sensitive data.
How critical are the Citrix vulnerabilities?
The vulnerabilities detected in Citrix ADC and Citrix Gateway are critical and high in severity. CVE-2023-3519, rated as critical (severity 9.8), allows unauthenticated remote code execution, enabling attackers to execute arbitrary code on the affected system without any privilegeor user interaction.
CVE-2023-3466 (severity 8.3) and CVE-2023-3467 (severity 8.0) are rated high, allowing for reflected cross-site scripting and privilege escalation to root administrator, respectively. These vulnerabilities pose significant risks, including unauthorized access, data breaches, and potential system compromise. Organizations must take immediate action to apply updates and mitigations to safeguard their networks and sensitive information.
Which products and systems are affected by Citrix vulnerabilities? Which versions are affected?
The vulnerabilities impact the following products and their respective versions:
Affected Products:
- Citrix ADC (Application Delivery Controller)
- Citrix Gateway (used for secure application delivery and remote access solutions)
Citrix ADC Versions affected:
- 13.1 before 13.1-49.13
- 13.0 before 13.0-91.13
- 13.1-FIPS before 13.1-37.159
- 12.1-FIPS before 12.1-65.36
- 12.1-NDcPP before 12.65.36
Citrix Gateway Versions affected:
- 13.1 before 13.1-49.13
- 13.0 before 13.0-91.13
- 13.1-FIPS before 13.1-37.159
- 12.1-FIPS before 12.1-65.36
- 12.1-NDcPP before 12.65.36
If you are using any of the above-mentioned versions of Citrix ADC or Citrix Gateway, it is crucial to take immediate action to secure your systems by applying the relevant updates and mitigations recommended by Citrix.
Are there any IOCs that the SOC Teams can use to prevent exploitation of the vulnerabilities on internet-exposed servers?
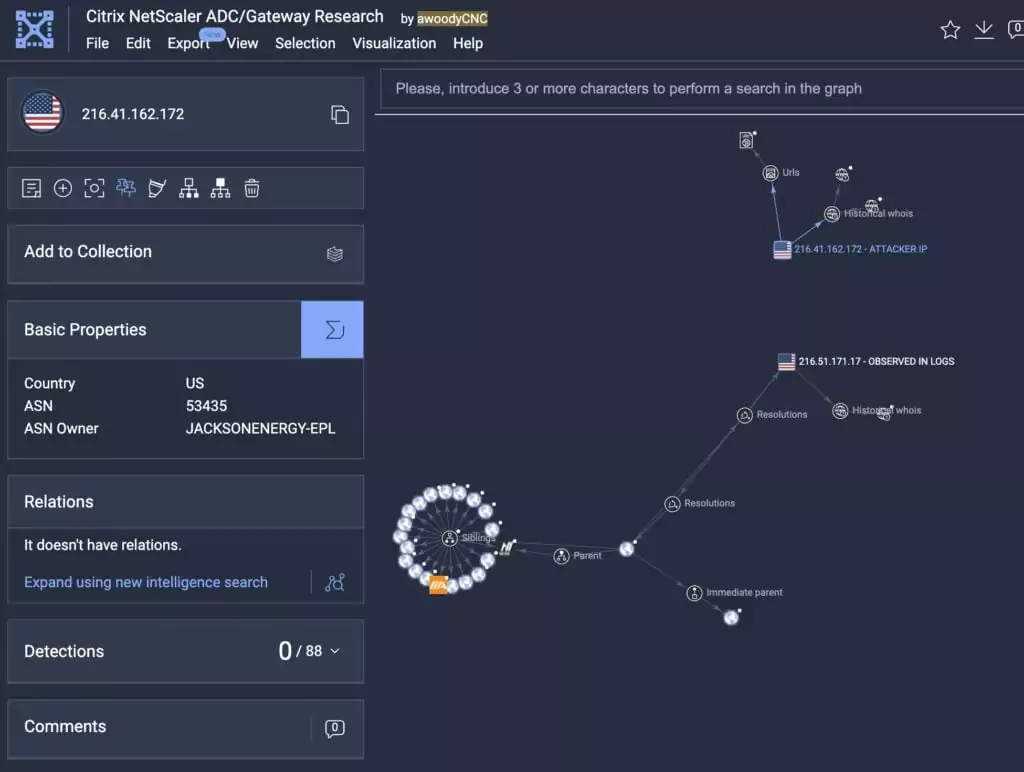
Regarding the CVE-2023-3519 vulnerability, two IPs were identified as indicators of compromise (IoC):
- 216[.]41[.]162[.]172
- 216[.]51[.]171[.]17
Florian Roth shared the following graph on Twitter, which is also available on VirusTotal. The graph shows the first IP address (216[.]41[.]162[.]172) as the source of a successful exploitation attempt, while the second IP address (216[.]51[.]171[.]17) was observed in logs.
How to protect your digital assets from precedence/exploitation of vulnerabilities?
To protect from the vulnerabilities in Citrix ADC and Citrix Gateway, the primary and most effective step is to apply the relevant patches and updates provided by Citrix. This will help to address the specific security flaws and close the vulnerabilities in the affected versions.
Additionally, if you are using NetScaler ADC and NetScaler Gateway version 12.1, which has reached its End of Life, it is recommended to upgrade to supported versions.
Stay informed about future updates and security bulletins by subscribing to Citrix’s notifications.
For further technical assistance, contact Citrix Technical Support. You could visit the Citrix Support page for contact details.
Are there any additional solutions other than patching?
In addition to patching, there are some additional measures that organizations can take to enhance their security posture and mitigate the risks associated with these vulnerabilities:
Network Segmentation: Implement network segmentation to limit the exposure of critical systems and services to potentially vulnerable devices. This can help contain the impact of any potential attacks.
Access Controls: Review and enforce proper access controls to restrict unauthorized access to Citrix ADC and Citrix Gateway. Ensure that only authorized users have the necessary privileges to access these systems.
Monitoring and Logging: Implement comprehensive monitoring and logging mechanisms to detect any suspicious activities or attempted exploits. Real-time monitoring can help identify potential threats early.
Web Application Firewall (WAF): Deploy a Web Application Firewall to protect against web-based attacks, such as the reflected cross-site scripting vulnerability (CVE-2023-3466).
Vulnerability Scanning: Regularly perform vulnerability scanning and assessments to identify and address any other potential vulnerabilities in the network and systems.
Endpoint Protection: Ensure that endpoint security solutions, such as antivirus and intrusion detection systems, are up to date and properly configured on all devices accessing Citrix ADC and Citrix Gateway.
Security Awareness Training: Educate employees and users about the importance of security best practices, such as recognizing phishing attempts and avoiding suspicious links.
While patching is crucial, a layered approach to security is always recommended. Organizations should continuously evaluate their security measures and adopt a proactive stance to protect against potential exploits and cyber threats.
How can you detect if the systems have been compromised?
In the notification published by CISA for CVE-2023-3519, they recommend taking the following steps to check for signs of compromise:
- Check for files newer than the last installation.
- Modify the -newermt parameter with the date that corresponds to your last installation:
- find /netscaler/ns_gui/ -type f -name *.php -newermt [YYYYMMDD] -exec ls -l {} ;
- find /var/vpn/ -type f -newermt [YYYYMMDD] -exec ls -l {} ;
- find /var/netscaler/logon/ -type f -newermt [YYYYMMDD] -exec ls -l {} ;
- find /var/python/ -type f -newermt [YYYYMMDD] -exec ls -l {} ;
- Check http error logs for abnormalities that may be from initial exploit:
- zgrep ‘.sh’ /var/log/httperror.log*
- zgrep ‘.php’ /var/log/httperror.log*
- Check shell logs for unusual post-ex commands, for example:
- grep ‘/flash/nsconfig/keys’ /var/log/sh.log*
- Look for setuid binaries dropped:
- find /var -perm -4000 -user root -not -path “/var/nslog/*” -newermt [YYYYMMDD] -exec ls -l {} ;
- Review network and firewall logs for subnet-wide scanning of HTTP/HTTPS/SMB (80/443/445) originating from the ADC.
- Review DNS logs for unexpected spike in internal network computer name lookup originating from the ADC (this may indicate the threat actor resolving host post-AD enumeration of computer objects).
- Review network/firewall logs for unexpected spikes in AD/LDAP/LDAPS traffic originating from the ADC (this may indicate AD/LDAP enumeration).
- Review number of connections/sessions from NetScaler ADC per IP address for excessive connection attempts from a single IP (this may indicate the threat actor interacting with the webshell).
- Pay attention to larger outbound transfers from the ADC over a short period of session time as it can be indicative of data exfiltration.
- Review AD logs for logon activities originating from the ADC IP with the account configured for AD connection.
- If logon restriction is configured for the AD account, check event 4625 where the failure reason is “User not allowed to logon at this computer.”
- Review NetScaler ADC internal logs (sh.log*, bash.log*) for traces of potential malicious activity (some example keywords for grep are provided below):
- database.php
- ns_gui/vpn
- /flash/nsconfig/keys/updated
- LDAPTLS_REQCERT
- ldapsearch
- openssl + salt
- Review NetScaler ADC internal access logs (httpaccess-vpn.log*) for 200 successful access of unknown web resources.
For more detailed information, refer to the CISA announcement.
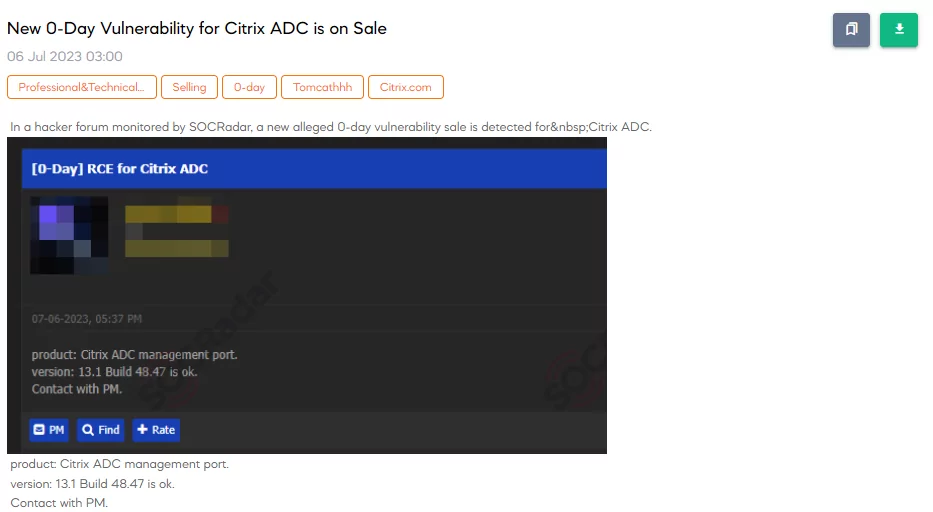
Citrix RCE Exploit Sale Revealed on Dark Web Before Vendor Announcement
Just prior to the vendor’s official announcement, a dark web post revealed the sale of an exploit for a remote code execution (RCE) vulnerability associated with Citrix. The alleged exploit is said to impact versions equal to or lower than 13.1-48.7.
Is There Any Example of Exploit Code?
Although there is no proof-of-concept (PoC) exploit for medium level XSS issue CVE-2023-3466; for CVE-2023-3519, after two weeks of CVE code for the vulnerability being reserved, first PoCs have started to emerge:
Dejavu of the Infamous CVE-2019-19781?
The RCE vulnerability detected in the Citrix products brings to mind the infamous CVE-2019-19781, which sent shockwaves through the cybersecurity community when it was disclosed in 2019. This similarity raises deep concerns, as the previous incident demonstrated the devastating impact such vulnerabilities can have on organizations and users worldwide.
Combine SOCRadar XTI Solutions to Battle Critical Vulnerabilities
In conclusion, it is crucial for organizations to take immediate action and address the critical vulnerabilities in Citrix ADC and Citrix Gateway. Updating to the latest releases, ensuring the upgrade of unsupported versions, and subscribing to Citrix security bulletins for future updates are essential steps to protect against potential exploits. Additionally, by leveraging SOCRadar’s vulnerability management capabilities and Extended Attack Surface Management (EASM), organizations can enhance their security posture, gain visibility into their extended attack surface, and proactively mitigate risks.