Dark Web Market: STYX Market
Greed may be a timeless driver of cybercrime, but in 2025, it’s the structure, scale, and specialization of dark web marketplaces that elevate this motivation into a full-fledged ecosystem. One such ecosystem is STYX Marketplace — a relatively new, yet already influential, dark web platform catering to financially motivated threat actors. While many marketplaces offer a mix of illicit goods, STYX focuses sharply on fraud, laundering, and monetizing stolen data through a well-structured marketplace and a tightly integrated Telegram presence.
What Is STYX Market?
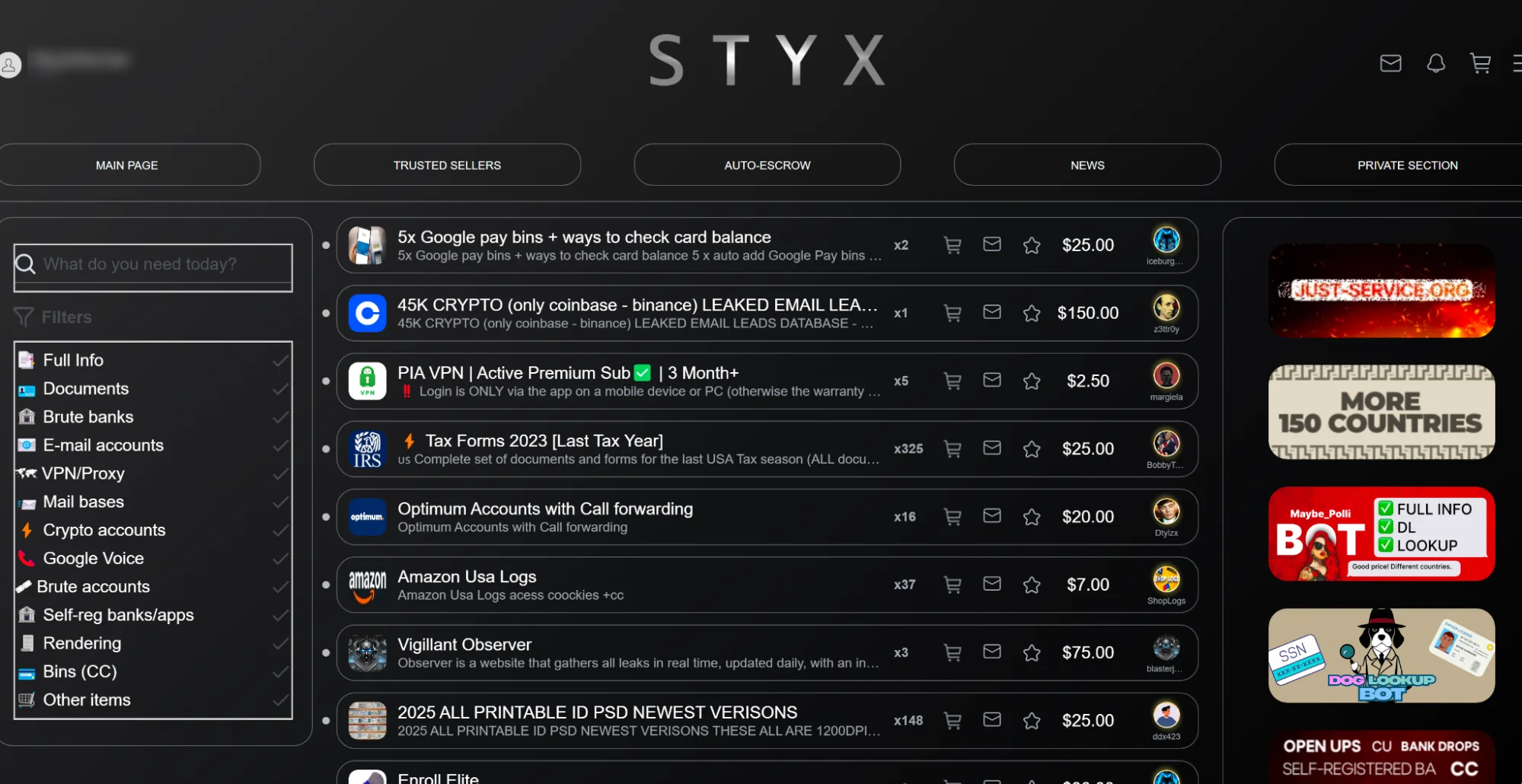
Launched in 2023, STYX Market is a darknet marketplace focused heavily on the trade of stealer logs, remote access credentials, and bot data. While not as mature as long-established hubs like BriansClub or Russian Market, STYX has carved out a firm position among cybercriminals seeking fresh and categorized data.
The market operates on the clearnet and features an accessible, user-friendly interface designed for ease of navigation. The primary audience? Data brokers, Initial Access brokers (IABs), and threat actors looking for footholds into corporate environments.
Despite its relatively recent launch, the platform has seen fast growth–mirroring the increased demand for stolen credentials harvested through stealer malware like RedLine, Raccoon, Vidar, and LummaC2. Its operational model appears to be geared toward automation, scalability, and ease of use—providing daily data imports and API integrations for high-volume buyers.
Key Offerings and Features of STYX Market
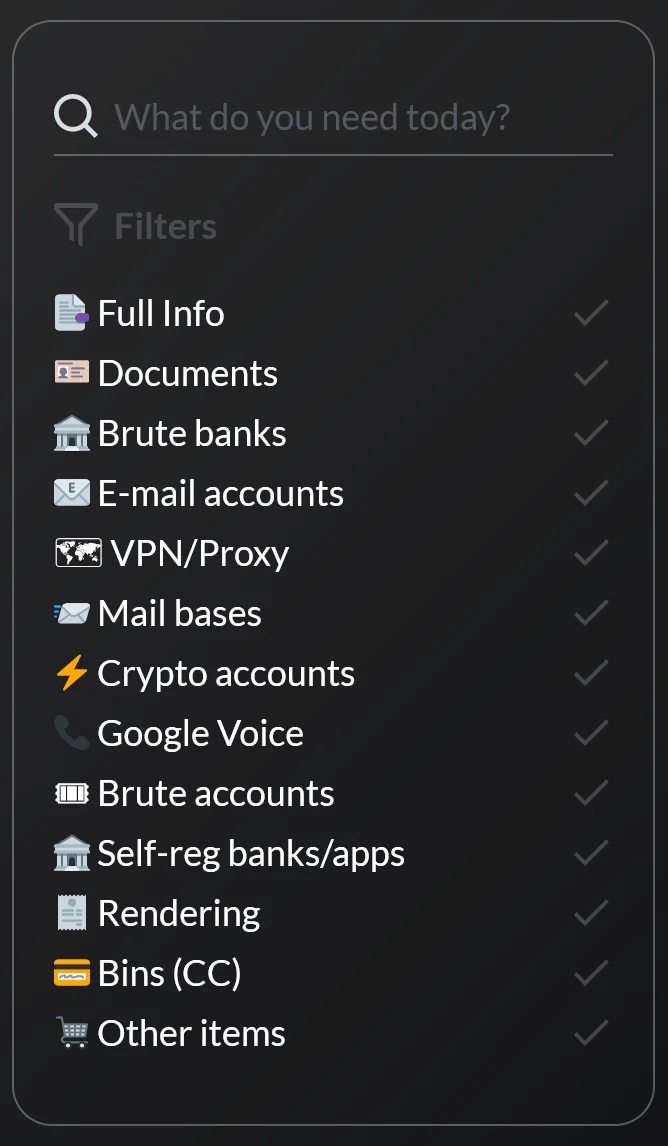
STYX Market has positioned itself beyond the scope of traditional carding platforms. Rather than focusing on outdated CVV dumps or basic payment data, it caters to modern cybercriminal needs with a diversified portfolio of digital assets. From access credentials and forged documents to cryptocurrency wallets and brute-forced accounts, the marketplace offers a wide array of illicit products tailored for fraud, identity theft, and financial crime. This versatility makes STYX a go-to source not only for low-tier actors but also for more advanced threat groups seeking specialized data.
Stealer Logs and Host Fingerprints
At the core of STYX’s operation lies its vast library of stealer logs—exfiltrated data from infected machines. These logs often include login credentials, browser cookies, saved form data, crypto wallet information, and other valuable artifacts used in account takeovers and fraud.
Access to Digital Accounts and Services
The marketplace includes access to brute-forced or stealer-extracted logins for financial platforms, cryptocurrency exchanges, email providers, messaging apps, and voice services like Google Voice. Categories such as “Brute Banks,” “Self-Reg Banks/Apps,” and “Crypto Accounts” reflect the market’s financial exploitation focus.
Fullz and Identity Document Packages
Beyond login data, STYX offers full identity profiles—often referred to as “Full Info”—which may contain scanned IDs, passports, utility bills, and other documents. These assets support KYC bypass, account verification fraud, and synthetic identity creation.
Money Laundering Services
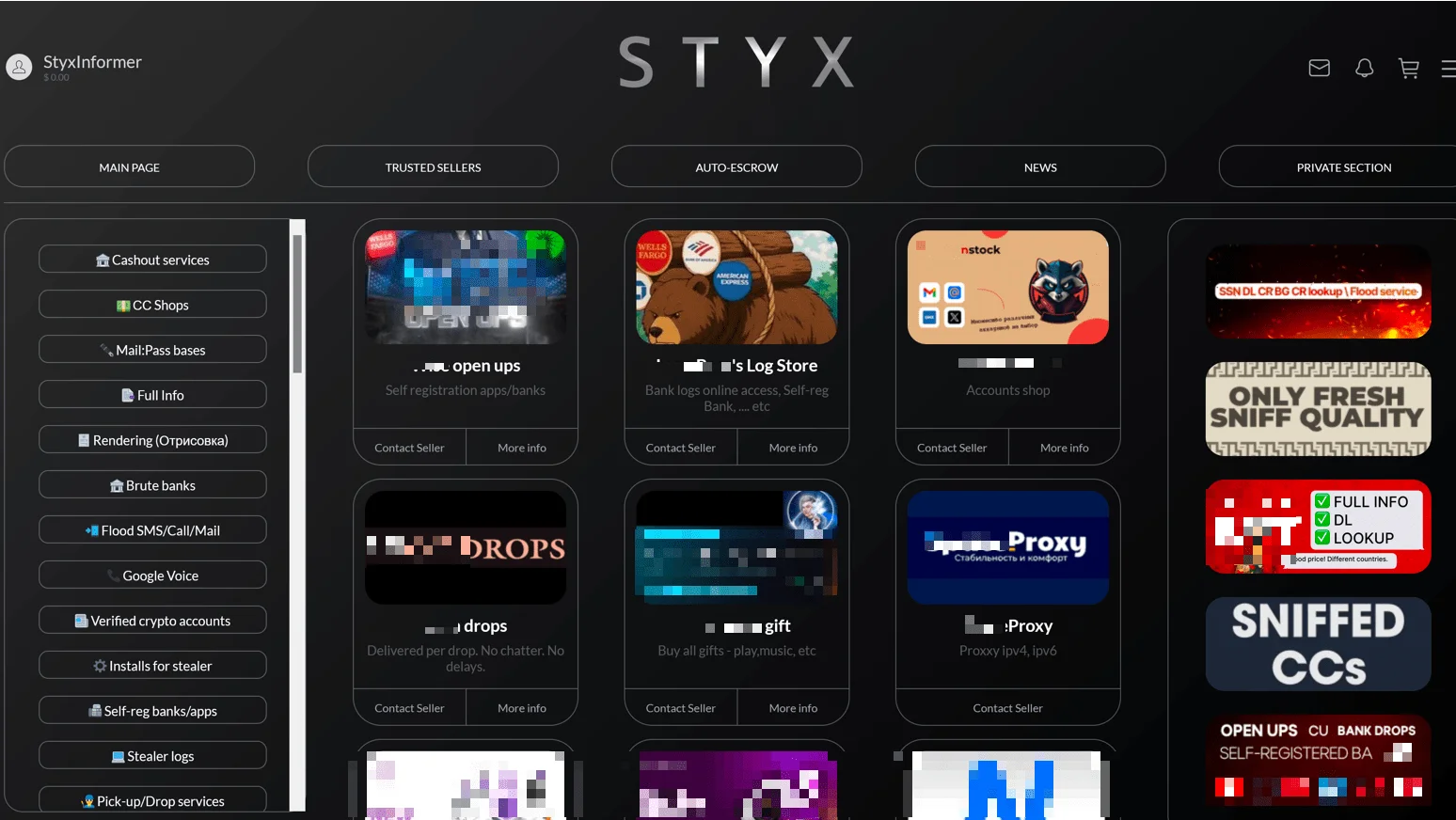
STYX Market also connects buyers with illicit financial services. These offerings include money laundering and cash-out support–enabling actors to convert stolen digital assets into usable fiat or cryptocurrency, often via intermediaries or underground financial networks.
BIN Listings and Payment Metadata
While not focused on raw carding data, the market includes searchable BINs (Bank Identification Numbers) associated with stolen accounts.
Why Is STYX Market Gaining Popularity?
STYX Market’s surge in reputation isn’t accidental. Its growth reflects broader trends in cybercrime–namely the shift from outdated carding tactics toward scalable, data-driven operations. Below are the primary factors fueling its popularity:
- Fresh, Structured Data: Unlike noisy Telegram channels or outdated dump forums, STYX offers constantly updated logs pulled directly from stealer panels—organized, searchable, and ready to use.
- Low Entry Barriers: Account creation is simple with no verification needed. Many listings are priced as low as $3–$5, making it accessible even to low-tier actors.
- Direct Buyer-to-Seller Model: STYX minimizes reliance on moderators or middlemen. Buyers interact directly with vendors, streamlining transactions and cutting delays.
- Advanced Filtering Options: Listings come with technical metadata—IP address, OS version, installed software, geolocation, and even antivirus presence—allowing precision targeting based on campaign needs.
- Corporate Access Credentials: Beyond personal logins, the platform offers access to business infrastructure like VPNs, RDPs, SaaS tools (Slack, Zoom, Trello), and internal dashboards–attracting initial access brokers.
- Financial Crime Support: STYX doesn’t just sell data—it supports the full fraud cycle. Cash-out services, money laundering networks, and crypto mixer listings make it a one-stop shop for financial cybercrime.
- Telegram Integration: Most vendors operate through Telegram, with separate channels for product listings, support, and customer reviews–making real-time communication easy.
- Trusted Vendor Ecosystem: The platform’s “Trusted Sellers” section highlights long-term, verified actors–many of whom have deep darknet footprints dating back years.
STYX Market’s Threat Implications
While the platform avoids more overt criminal services (like ransomware or card cloning tutorials), the data it offers has enormous potential for follow-up attacks.
- Credential Stuffing: STYX provides a playground for brute-force and automated access attempts across industries.
- Initial Access Brokerage: Logs with SaaS, VPN, or RDP access are sold cheaply, often later ending up in ransomware affiliate programs.
- Targeted Phishing & Recon: The stolen session cookies and email data in the logs help actors craft highly targeted phishing campaigns or impersonation attacks.
- Identity Theft: Cryptocurrency wallet files, autofill data, and PII fields create an ideal setup for personal and financial identity fraud.
How Can SOCRadar Help?
As marketplaces like STYX continue to evolve, organizations need more than just firewalls and endpoint protection—they need visibility into where their data is being traded, abused, or weaponized. That’s where SOCRadar comes in.
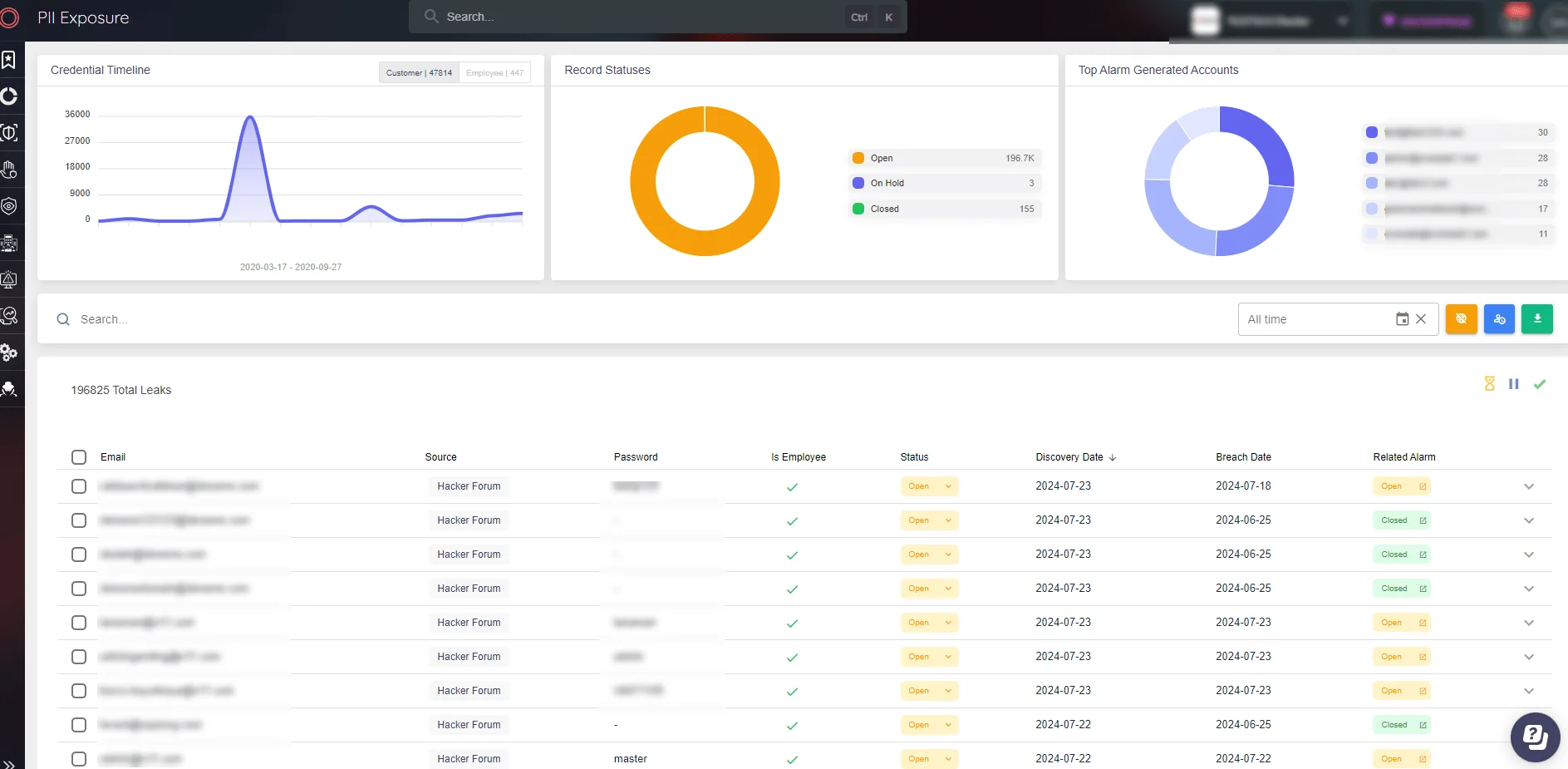
- Dark Web Monitoring: SOCRadar continuously monitors dark web markets, Telegram channels, and hidden forums where compromised credentials, financial records, and personal information are sold. If your brand, domain, or data appears in a STYX listing, you get alerted in real-time.
- Credential Leak Detection: With STYX’s focus on stealer logs and access credentials, SOCRadar’s leaked credential monitoring identifies if employee or customer data has been compromised—helping security teams act before threat actors do.
- Vendor and Threat Actor Profiling: Through the Threat Actor Intelligence module, SOCRadar tracks STYX vendors across multiple platforms. By mapping their activity, reputation, and connected campaigns, organizations can better understand who is targeting them and how.
- Fraud Protection: STYX vendors often offer cash-out, laundering, and synthetic identity kits. SOCRadar helps financial institutions detect fraudulent transactions and proactively monitor for abuse linked to known underground actors and tactics.
- Takedown Services: Whether it’s phishing domains, malicious lookalike shops, or exposed PII, SOCRadar’s takedown service works to remove harmful content from the web—reducing brand abuse and data exposure risks.
- Attack Surface Visibility: With leaked logs often exposing access to corporate assets like VPNs, SaaS tools, and cloud dashboards, SOCRadar’s ASM (Attack Surface Management) module gives you a real-time view of what threat actors could see or exploit externally.
- Actionable Intelligence, Not Just Alerts: SOCRadar doesn’t just provide threat data—it contextualizes it. With clear risk ratings, severity levels, and incident timelines, teams can prioritize what matters most and respond faster.
Conclusion
STYX Market represents the evolution of cybercriminal economies—fast, modular, and focused on data. While it lacks the legacy status of Russian Market or the boldness of BriansClub, its current trajectory suggests STYX will play a central role in the infostealer-as-a-service ecosystem in 2025 and beyond.
Security teams must elevate their visibility across the Dark Web to counteract threats from platforms like STYX. Monitoring, response, and credential hygiene are no longer optional—they are baseline defenses in an increasingly hostile digital landscape.