
Dark Web Profile: Moonstone Sleet
Moonstone Sleet AKA Storm-1789, a newly identified North Korean Advanced Persistent Threat (APT) group, has been making waves with its targeted cyberattacks that blend espionage with financial motivations. Operating under the umbrella of North Korea’s state-sponsored cyber programs, Moonstone Sleet has demonstrated sophisticated capabilities in leveraging social engineering, deploying custom malware, and conducting ransomware operations to support espionage and fund national interests.
This profile dives into Moonstone Sleet’s tactics, techniques, and objectives, shedding light on its methods and the potential risks it poses to global organizations.
Who is Moonstone Sleet?
Moonstone Sleet is a North Korean state-sponsored threat actor linked to a series of targeted attacks against technology companies, financial institutions, and cryptocurrency platforms. The group is believed to have emerged in early 2024 and operates as part of North Korea’s cyber-espionage apparatus, which seeks to bolster the regime’s economy while gathering intelligence to support its geopolitical objectives.
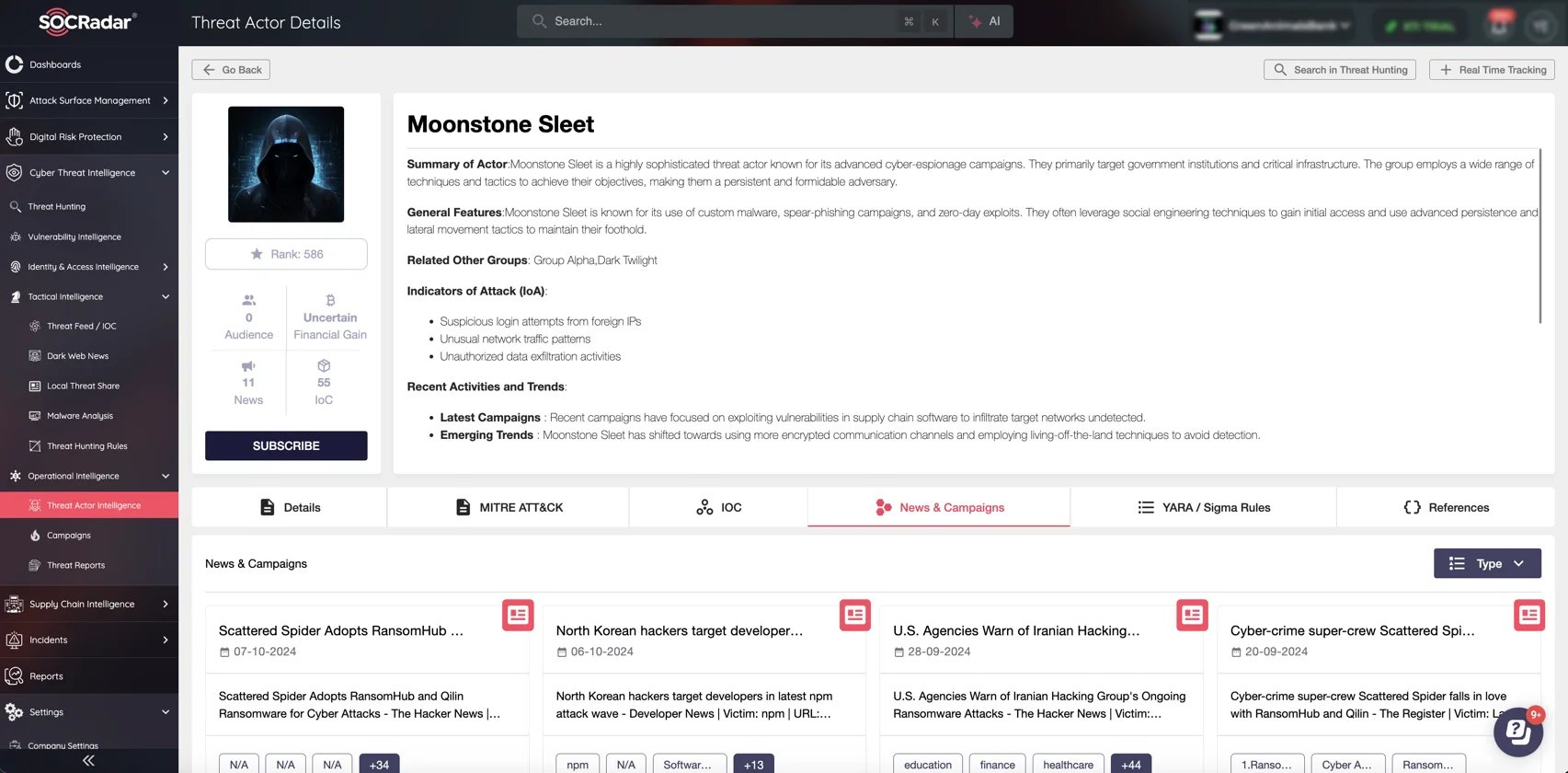
Threat Actor Details of Moonstone Sleet on SOCRadar Threat Actor Intelligence
Using sophisticated spear-phishing campaigns and advanced reconnaissance, Moonstone Sleet targets organizations across the globe, often masquerading as reputable entities to infiltrate networks. The group is known for its deceptive tactics, such as fake job offers and fraudulent project collaboration requests, aimed at gaining initial access to victims’ systems.
How Moonstone Sleet Operates
Moonstone Sleet employs a combination of social engineering, custom malware, and ransomware to achieve its objectives. The group frequently uses fake LinkedIn job offers or phishing emails to lure victims into opening malicious attachments or clicking on compromised links. Once inside a network, the group relies on a variety of custom tools and techniques to maintain persistence and exfiltrate data.
Microsoft has also linked Moonstone Sleet to FakePenny, Key Tools and Techniques
- FakePenny Malware: a new custom ransomware deployed in April 2024, marking a significant evolution in the group’s methods. Unlike typical North Korean ransomware campaigns with smaller ransom demands, Moonstone Sleet’s FakePenny attacks demanded $6.6 million in Bitcoin, signaling a shift toward large-scale financial extortion. While financial gain was the primary motive, these attacks also carried a dual purpose of espionage, reinforcing the group’s multifaceted strategy.
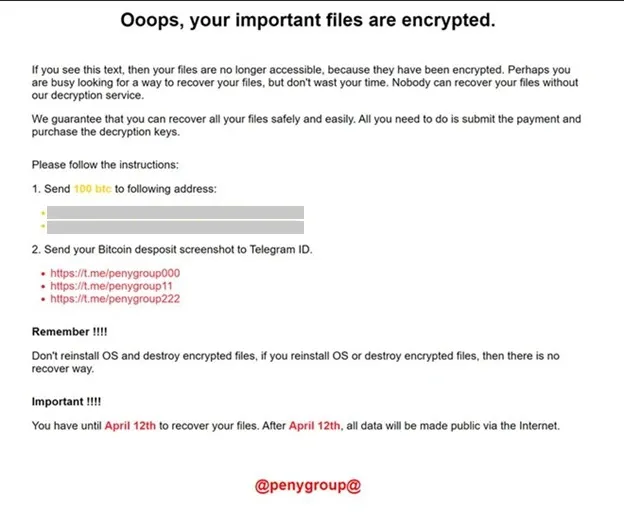
Ransomware note from FakePenny (Microsoft)
- Ransomware Operations: Moonstone Sleet uses ransomware not only for extortion but also as a smokescreen to mask its primary espionage activities. This dual-purpose approach increases operational complexity, making it harder for organizations to discern the group’s true intentions.
- Cobalt Strike and Other Red Team Tools: Leveraged for command-and-control communication and maintaining a foothold in compromised systems.
- Malicious Software Packages: The group leverages trojanized applications and open-source packages to target development environments and software supply chains, broadening its attack surface while compromising high-value networks.
Trojanized PuTTY: A Gateway for Intrusion
Microsoft has observed Moonstone Sleet employing trojanized versions of PuTTY, a widely used open-source terminal emulator, to infiltrate target systems. This sophisticated tactic exemplifies the group’s ability to exploit trusted tools for malicious purposes, leveraging social engineering and advanced payload delivery mechanisms.
How the Trojanized PuTTY Works
Moonstone Sleet typically delivers trojanized PuTTY via phishing campaigns on platforms such as LinkedIn, Telegram, or freelance developer websites. Victims receive a ZIP file containing two components: a modified PuTTY executable (putty.exe) and a text file (url.txt) with an IP address and a password. When users input the provided credentials into the PuTTY application, it decrypts and executes an embedded payload, initiating a multi-stage malware attack.
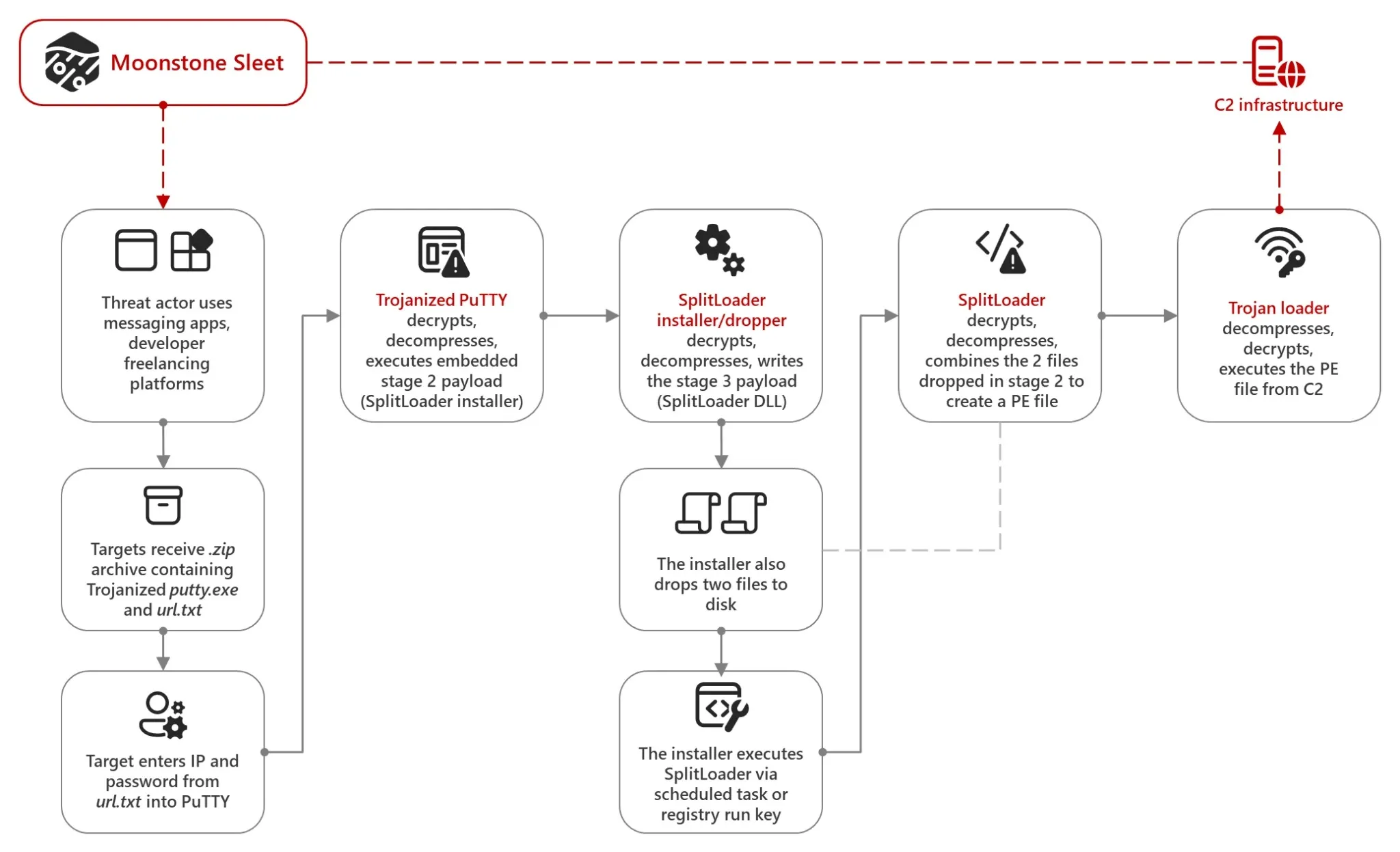
Trojanized PuTTY Attack flow (Microsoft)
Malware Execution Stages
- Stage 1 – Trojanized PuTTY
The modified PuTTY decrypts and executes an embedded second-stage payload. - Stage 2 – SplitLoader Installer
The payload decompresses and writes additional files to disk, creating a foothold in the system through scheduled tasks or registry run keys. - Stage 3 – SplitLoader DLL
The installer decrypts and combines two encrypted files into another executable file. - Stage 4 – Trojan Loader
The loader contacts the command-and-control (C2) server to download and execute further malicious payloads, facilitating long-term persistence and data exfiltration.
This layered attack chain demonstrates Moonstone Sleet’s technical proficiency and adaptability in achieving its objectives, which include data theft, espionage, and network disruption.
Infrastructure Evolution
Initially sharing tactics and infrastructure with another North Korean group, Diamond Sleet, Moonstone Sleet has since developed its own bespoke infrastructure. Despite this evolution, overlapping techniques, such as the use of trojanized PuTTY, indicate a shared pool of resources and methodologies among North Korean APT groups.
Recent Campaigns
Malicious Tank Game and Fake Companies
One of Moonstone Sleet’s most elaborate campaigns involves DeTankWar, a malicious tank game used to infiltrate victims’ systems. Beginning in February 2024, the group masqueraded as game developers, contacting victims via email or social media under the guise of seeking investors or collaborators.
To lend legitimacy, Moonstone Sleet created an ecosystem of fake websites and social media accounts, often linked to a fictitious company named C.C. Waterfall. Victims were directed to download the game, which upon installation, loaded malware capable of stealing browser data and other sensitive information. If deemed valuable, attackers performed additional actions, such as credential theft and further network reconnaissance.
This campaign highlights Moonstone Sleet’s creativity and resourcefulness, using sophisticated social engineering to bypass initial defenses. The fake tank game approach represents an evolution of tactics aimed at both individual and organizational targets in the IT and defense sectors.
Supply Chain Exploits in Open Source Ecosystems
Moonstone Sleet has also focused on exploiting open-source software supply chains, publishing malicious npm packages to target developers and organizations. In late 2023 and early 2024, the group released multiple harmful packages in the npm registry, masquerading as legitimate utilities. Checkmarx identified that these packages were designed to execute payloads immediately upon installation, employing obfuscation techniques and targeting both Windows and Linux systems.
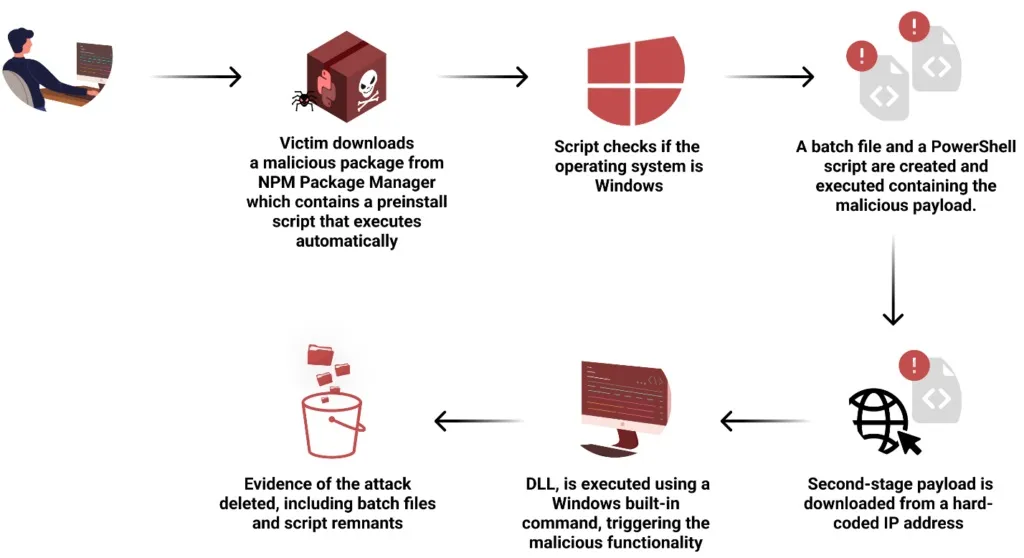
Payload Execution (Checkmarx)
Unlike similar North Korean operations like Jade Sleet, Moonstone Sleet relied on a streamlined single-package approach that included OS-specific malicious code. The packages downloaded encrypted files from remote servers, decrypted them using XOR operations, and executed them via trusted binaries like rundll32.exe. These methods reflect Moonstone Sleet’s growing sophistication in leveraging open-source ecosystems for malicious purposes.
“Stressed Pungsan” Campaign Using Trojanized npm Packages
In July 2024, Datadog uncovered a campaign involving two trojanized npm packages, “harthat-hash” and “harthat-api,” uploaded by the user “nagasiren978.” These packages mimicked legitimate tools and contained pre-install scripts that downloaded malicious DLLs from a Command-and-Control (C2) server. Once installed, the DLLs executed through rundll32.exe, leveraging anti-debugging and anti-reverse engineering techniques to evade detection.
While Datadog internally referred to this activity as “Stressed Pungsan,” its connection to Moonstone Sleet remains speculative. The Tactics, Techniques, and Procedures (TTPs) behind the malicious packages, such as the use of trojanized software and exploitation of developer environments, align closely with known Moonstone Sleet operations.
Despite the incomplete or experimental nature of the payloads, the campaign reflects a broader pattern of North Korean-aligned threat actors targeting software development ecosystems. If tied to Moonstone Sleet, it would further highlight the group’s focus on supply chain compromises and the exploitation of open-source platforms to infiltrate and disrupt high-value organizations.
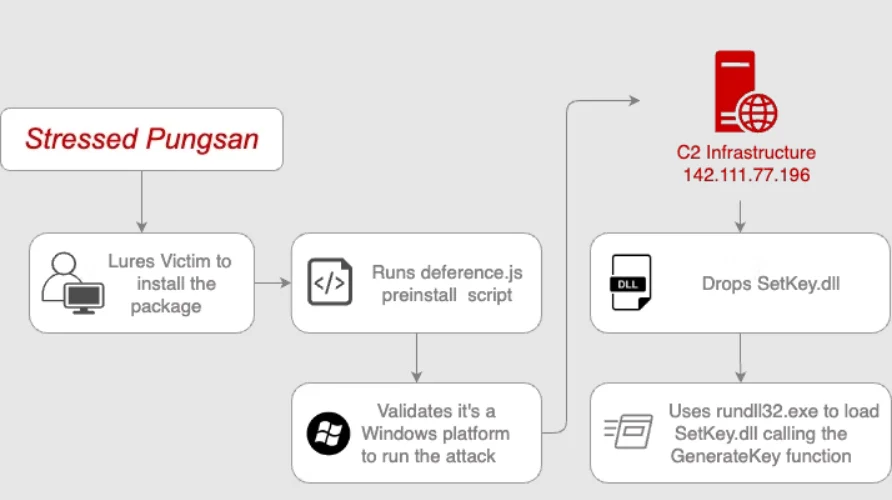
“Stressed Pungsan” attack flow (DATADOG security labs)
Motivations and Objectives
Moonstone Sleet’s activities align closely with North Korea’s dual objectives: financial gain and geopolitical intelligence gathering. The group’s ransomware attacks often serve as a cover for more strategic espionage operations, where sensitive data from financial, defense, and technology sectors is exfiltrated to support national interests.
Notable TTPs
| Tactic | Technique | MITRE ID | Description |
| Initial Access | Phishing: Spearphishing Link | T1566.002 | Fake job offers and collaboration requests lure victims into opening malware. |
| Supply Chain Compromise | T1195 | Trojanized npm packages and open-source libraries compromise developer environments. | |
| Execution | User Execution: Malicious File | T1204.002 | Malicious files (e.g., ZIP archives containing trojanized PuTTY) execute payloads on victim systems. |
| Command and Scripting Interpreter | T1059 | Malicious scripts in npm packages use system interpreters like rundll32.exe to execute DLL payloads. | |
| Persistence | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 | Malware establishes persistence through registry modifications or scheduled tasks. |
| Credential Access | OS Credential Dumping | T1003 | Credentials are extracted from LSASS or other system processes using tools like Mimikatz. |
| Input Capture: Keylogging | T1056.001 | Keystrokes are captured to steal credentials. | |
| Discovery | System Network Connections Discovery | T1049 | Malware maps network connections to identify potential targets for lateral movement. |
| Account Discovery: Domain Account | T1087.002 | Information on domain accounts is gathered for privilege escalation. | |
| Lateral Movement | Exploitation of Remote Services | T1210 | Exploiting vulnerable systems for lateral access within the target network. |
| Remote Services: SMB/Windows Admin Shares | T1021.002 | Movement within the network is achieved through compromised Windows shares. | |
| Collection | Data from Local System | T1005 | Browser data and other sensitive files are exfiltrated from local systems. |
| Command and Control | Application Layer Protocol | T1071 | Communication with C2 servers occurs via HTTP(S) or custom protocols. |
| Impact | Data Encrypted for Impact | T1486 | FakePenny ransomware encrypts victim data for extortion purposes. |
| Disk Wipe | T1561 | Disk-wiping techniques are used in ransomware to obscure espionage operations. |
How Can You Defend Against Moonstone Sleet and Similar APT Attacks?
Defending against Advanced Persistent Threats (APTs) like Moonstone Sleet requires a multi-layered security approach that combines proactive monitoring, robust defenses, and incident response readiness. Here are key strategies to mitigate the risks posed by this North Korean threat actor:
Email and Web Filtering
Since Moonstone Sleet often uses spear-phishing emails and malicious links to gain initial access, organizations must implement robust email filtering systems.
- Anti-phishing tools: Deploy solutions that detect and block phishing attempts, especially those containing malicious links or attachments.
- URL filtering: Prevent employees from accessing known malicious websites linked to Moonstone Sleet campaigns.
- Employee training: Regularly educate employees on how to recognize and report phishing attempts.
Endpoint Detection and Response (EDR)
Moonstone Sleet’s tactics often involve malware and custom tools like FakePenny ransomware and trojanized PuTTY. Strong endpoint defenses are essential.
- EDR solutions: Deploy tools capable of detecting suspicious activity such as abnormal file execution or registry modifications.
- Behavioral analysis: Use advanced analytics to identify malicious patterns indicative of APT activity.
Network Segmentation and Zero Trust Architecture
To prevent lateral movement once attackers infiltrate the network, organizations should adopt strict network segmentation and Zero Trust principles.
- Segment networks: Isolate sensitive data and critical infrastructure to minimize the risk of widespread access.
- Zero Trust security: Ensure all users and devices are verified before being granted access to any part of the network.
- Anomaly detection: Continuously monitor internal network communications to identify and block unauthorized lateral movement.
Credential Management and Multi-Factor Authentication (MFA)
Moonstone Sleet exploits stolen credentials to escalate privileges. Strong authentication mechanisms can help mitigate this risk.
- Enforce MFA: Apply multi-factor authentication to all critical systems, particularly those connected to sensitive data.
- Credential monitoring: Use dark web monitoring tools, such as SOCRadar’s Dark Web Monitoring, to detect if credentials have been exposed online.
- Password policies: Require strong, unique passwords and regularly rotate them to reduce the risk of credential-based attacks.
Dark Web Monitoring and Threat Intelligence
Moonstone Sleet often targets high-value organizations, making threat intelligence and dark web monitoring crucial.
- Dark Web Surveillance: Utilize tools like SOCRadar’s Dark Web Monitoring to detect if sensitive data or credentials related to your organization are being sold or discussed in underground forums.
SOCRadar’s Dark Web Monitoring
- Real-time threat intelligence: Stay informed about emerging TTPs (tactics, techniques, and procedures) used by Moonstone Sleet and similar groups.
- Proactive defenses: Use insights from threat intelligence to strengthen defenses and anticipate attacker moves.
Phishing Domain Takedown
Moonstone Sleet frequently uses phishing to compromise accounts. Protect your organization’s reputation and customers by eliminating fraudulent domains.
- SOCRadar Integrated Takedown Service: Identify and dismantle phishing domains and fake websites targeting your organization.
- Domain monitoring: Detect domain spoofing attempts in real time to prevent phishing campaigns from gaining traction.
Incident Response and Data Recovery
Moonstone Sleet’s use of ransomware and wiper malware highlights the importance of having a strong incident response plan.
- Incident Response Plan: Develop and test a comprehensive IR plan that includes steps for containment, eradication, and recovery.
- Backup strategy: Regularly back up critical data and store it in secure, off-network locations.
- Data recovery: Implement fast recovery procedures to minimize downtime and operational impact in the event of an attack.
Conclusion
Moonstone Sleet represents an evolution in North Korea’s cyber capabilities, blending innovative attack vectors with traditional espionage techniques. By targeting software supply chains, IT infrastructures, and high-value organizations, the group poses a significant threat to global cybersecurity.
To counter such adversaries, organizations must adopt proactive defenses, including robust endpoint protection, supply chain monitoring, and threat intelligence tools like those provided by SOCRadar. As Moonstone Sleet’s campaigns continue to evolve, vigilance and collaboration among the security community are critical to mitigating the risks they present.





































