DepositFiles Config File Exposes Multiple Databases: Users’ Privacy at Risk
DepositFiles, a well-known web hosting service, left its environment configuration file publicly accessible, leading to unauthorized access.
A configuration file is a crucial component of any system, it holds essential values and settings necessary for specific environmental functioning. The research team at Cybernews discovered that DepositFiles’ configuration file contained highly sensitive information, encompassing credentials for multiple databases, email, payment systems, and social media accounts.
The exposed configuration file included:
- Redis database credentials
- “Billing” and “Uploads” database credentials
- Abuse and Support mail credentials
- Payment wall secret key
- Twitter, Facebook, and VKontakte credentials
- Google App ID and Secret
- Payment service credentials (including password, username, and endpoint)
- DF Android, DF iOS, PHP unit client, DF VPN app IDs, and salt
According to researchers, the indexing of another sensitive file indicates that the environment configuration file was exposed since February 2023.
What Could Hackers Do with the Exposed DepositFiles Data?
The exposed data presents a severe threat to both DepositFiles’ user privacy and the company’s integrity. The vast amount of information could lead to distributed denial-of-service (DDoS) attacks, ransomware deployment, or financial losses. Additionally, cybercriminals could exploit the exposed data to gain control over DepositFiles’ official communication channels, complicating the company’s ability to inform clients about data breaches or potential attacks.
The specific risks posed by the exposed information are outlined below:
The Dangers of Exposed Database Credentials:
The exposed Redis database credentials could lead to data breaches, manipulation, and unauthorized access to sensitive information. If linked to the company’s broader infrastructure, attackers could escalate privileges and target other vital systems.
The credentials for the databases “billing” and “uploads” were exposed, which most likely contained sensitive financial information. Attackers could exploit the contents of these databases through various cyberattacks, such as identity theft, financial fraud, and phishing.
Email Credentials and Social Media Accounts at Risk:
With access to abuse and support mail credentials, cybercriminals could read confidential correspondence and use trusted accounts to send phishing emails to clients and third-parties. The exposed social media account credentials may allow attackers to hijack DepositFiles’ online presence.
Potential Misuse of Google App ID and Secret:
Attackers could exploit the exposed Google App ID and Secret to gain unauthorized access to DepositFiles’ Google services and APIs, and potentially compromise sensitive data. According to the researchers, an attacker can also imitate the company’s app or service using the exposed credentials.
The Vulnerability of Payment Systems:
The leaked payment wall secret key and payment service credentials open the door to fraudulent transactions, changes to payment settings, or access to sensitive payment data.
DF Android, DF iOS, PHP unit client, DF VPN App IDs, and Salt Exposure:
DF Android and DF iOS represent “data flow” for the respective operating systems they are used on. On the other hand, a PHP unit client serves as a development environment, enabling the execution and testing of PHP-based software. Additionally, DF VPN offers a secure data flow connection, while salt acts as a security measure applied to passwords before encryption and storage.
The publicly accessible config file revealed these application and system identifiers, exposing the company to risks from malicious API requests and unauthorized access to sensitive resources.
Conclusion of the DepositFiles Breach
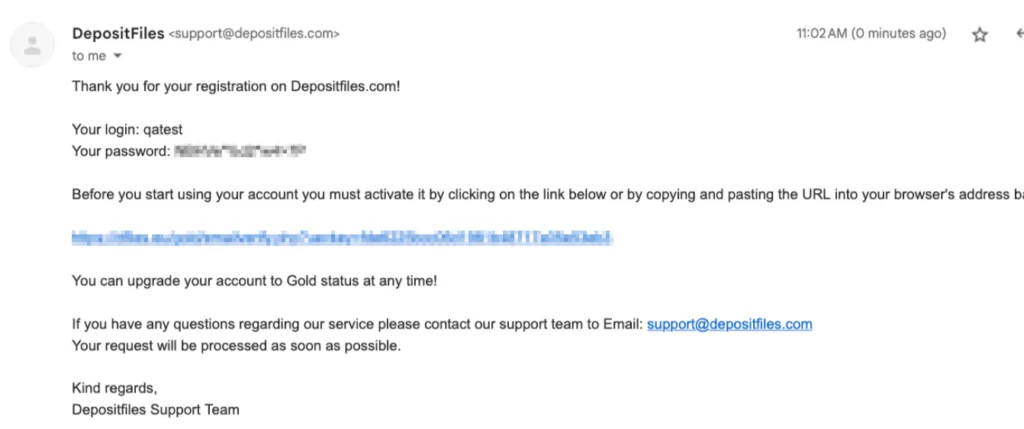
It is said the issue has been fixed, yet, the security practices that led to this type of breach remain questionable. Moreover, since the configuration file exposed database access, it is highly probable that all members’ passwords have been obtained. Additionally, when SOCRadar researchers examined the databases, they discovered that DepositFiles stored passwords in clear text format. This creates a major risk, especially for users who reuse passwords on other platforms, as it could result in account takeover attacks.
How Can SOCRadar Help?
SOCRadar brings you the power to monitor hacker forums and black markets across both the surface and dark web, ensuring you stay instantly informed about sales of databases, vulnerabilities, and other concerning activities relevant to your organization, country, or industry.