
EvilProxy Account Takeover Campaign Targets Key Executives
An escalating threat, named EvilProxy, combines advanced Adversary-in-the-Middle (AitM) phishing with sophisticated Account Takeover (ATO) methods to efficiently nab credentials protected with multi-factor authentication (MFA) and session cookies.
In the last six months, researchers have observed a significant increase in successful cloud account takeovers that specifically target high-profile executives in prominent firms. The attacks employed EvilProxy, which is a reverse proxy-based phishing tool.
This trend is propelled by the growing adoption of MFA within organizations. Notably, research reveals that a minimum of 35% of compromised users in the past year had MFA activated.
MFA Phishing-as-a-Service: Another Frontier for Threat Actors
Threat actors have started a growing market that provides MFA Phishing-as-a-Service (PhaaS), using open-source kits. As a result, even inexperienced and less skilled threat actors can gain access to phishing kits for various online platforms such as Gmail, Microsoft, Twitter, and more.
The phishing interfaces that circulate the landscape enable attackers to launch malicious campaigns with customizable features such as proxy identification and geofencing. EvilProxy is one such phishing interface that effectively facilitates Business Email Compromise (BEC) and account takeover attacks.
It was previously reported that EvilProxy is sold on a subscription basis to threat actors. The attacks against specific services cost $150 for ten days and $400 for a month. Google attacks are offered for a higher price, ranging from $250 for ten days to $600 for a month.
Modus Operandi of EvilProxy Attacks
Researchers have reported an ongoing campaign that utilizes EvilProxy to target Microsoft 365 user accounts. This campaign has sent approximately 120,000 phishing emails to global organizations between March and June 2023.
The threat actors sent phishing emails containing links to malicious Microsoft 365 phishing sites. They used sender addresses impersonating trusted services such as Concur, DocuSign, and Adobe.

From the malicious URL, a multi-step infection chain is initiated. To start, user traffic is redirected through an open, legitimate redirector such as youtube[.]com and bs.serving-sys[.]com.
![Example of a malicious URL using Youtube[.]com for redirection, EvilProxy](https://socradar.io/wp-content/uploads/2023/08/evilproxy-example-url.png)
To spread traffic, malicious cookies and 404 redirects may be used to redirect user traffic several more times, lowering the risk of detection.
During the attack, the attackers also took steps to conceal user email addresses from automated scanning tools. They accomplished this by applying specialized encoding to the email addresses. Additionally, they exploited compromised legitimate websites to upload PHP code, which facilitated the decryption of these email addresses.
Although the encoding methods varied in each attack wave, the decoding principle remained consistent. Attackers utilized predefined decoding patterns, as illustrated in the image below:
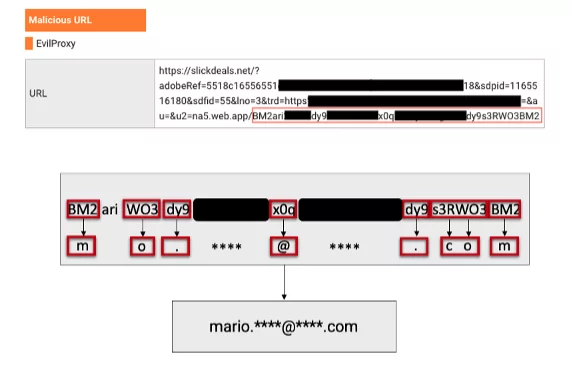
Following the decryption process, users were eventually directed to an EvilProxy phishing framework. The landing page serves as a reverse proxy, imitating recipient branding and attempting to deal with third-party identity providers. If necessary, these pages may request MFA credentials to facilitate a successful authentication on behalf of the victim, validating the credentials gathered as legitimate.
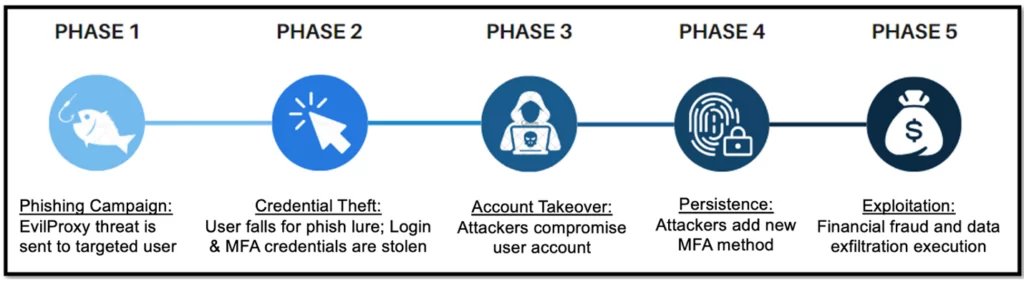
After breaching a victim’s account, the attackers proceeded to establish persistence within the organization’s cloud environment. Using a native Microsoft 365 app, they manipulated MFA, adding their own authentication method, with the preferred method being “Authenticator App with Notification and Code.”
EvilProxy Attack Flow Changes According to Geolocation
Researchers observed that the specified attack flow changes when user traffic originates from specific geographical locations. Traffic from Turkish IP addresses, in particular, was redirected to legitimate websites, eluding the attackers.
While it could be caused by the proxy service’s use of a safe-listing mechanism, it can also suggest that the orchestrators of the EvilProxy campaign may have connections to Turkey. Notably, multiple VPNs globally also faced limitations when attempting to access these malicious phishing sites.
Over 100 Organizations Have Been Targeted in EvilProxy Attacks
Globally, more than 100 organizations were targeted in EvilProxy attacks, collectively encompassing 1.5 million employees.
Nonetheless, not every user ensnared by the initial BEC phishing ploy fell prey to malicious intent. The threat actors prioritized exclusively the high-profile targets, like C-level executives and VPs within prominent firms, disregarding those deemed of lesser significance to their objectives.
These “VIP” individuals are particularly coveted by threat actors due to their potential reach to sensitive data and financial resources.
SOCRadar VIP Protection: A Secure Shield Against Account Takeover
CEOs, CFOs, and other key executives are common targets in account takeover attacks as threat actors often seek to exploit their personal data and online presence.
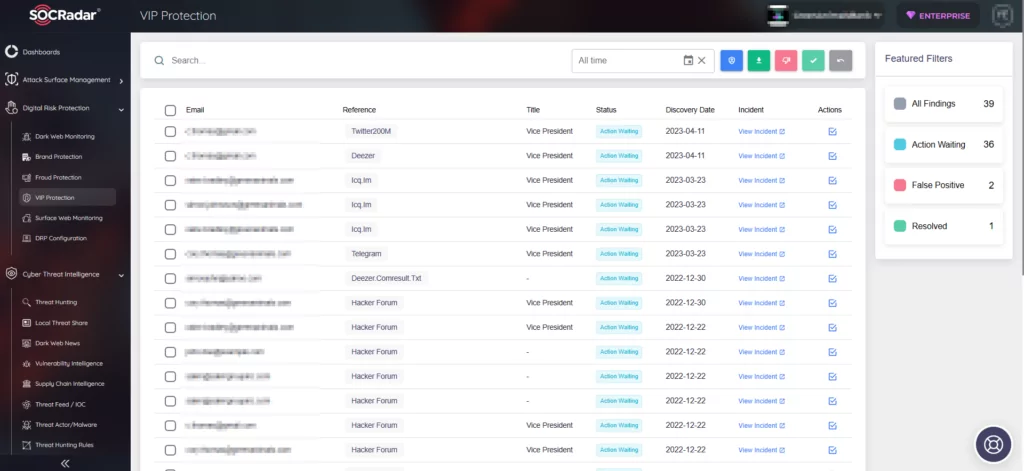
SOCRadar’s VIP Protection feature aids in recognizing compromised credentials linked to key executives. This significantly reduces the inherent risks linked to impersonation, which could potentially lead to unauthorized access or fraudulent transactions within the organization or among third-party entities like suppliers.




































