
Global DDoS Attack Landscape: Insights from Q1 2024
Distributed Denial of Service (DDoS) attacks continue to escalate in frequency and complexity, posing significant threats across various sectors, particularly the financial industry. Q1 2024 has seen a 50% year-over-year increase in DDoS attacks and an 18% rise from the previous quarter. This uptick underscores the growing danger these attacks present to businesses and organizations globally.
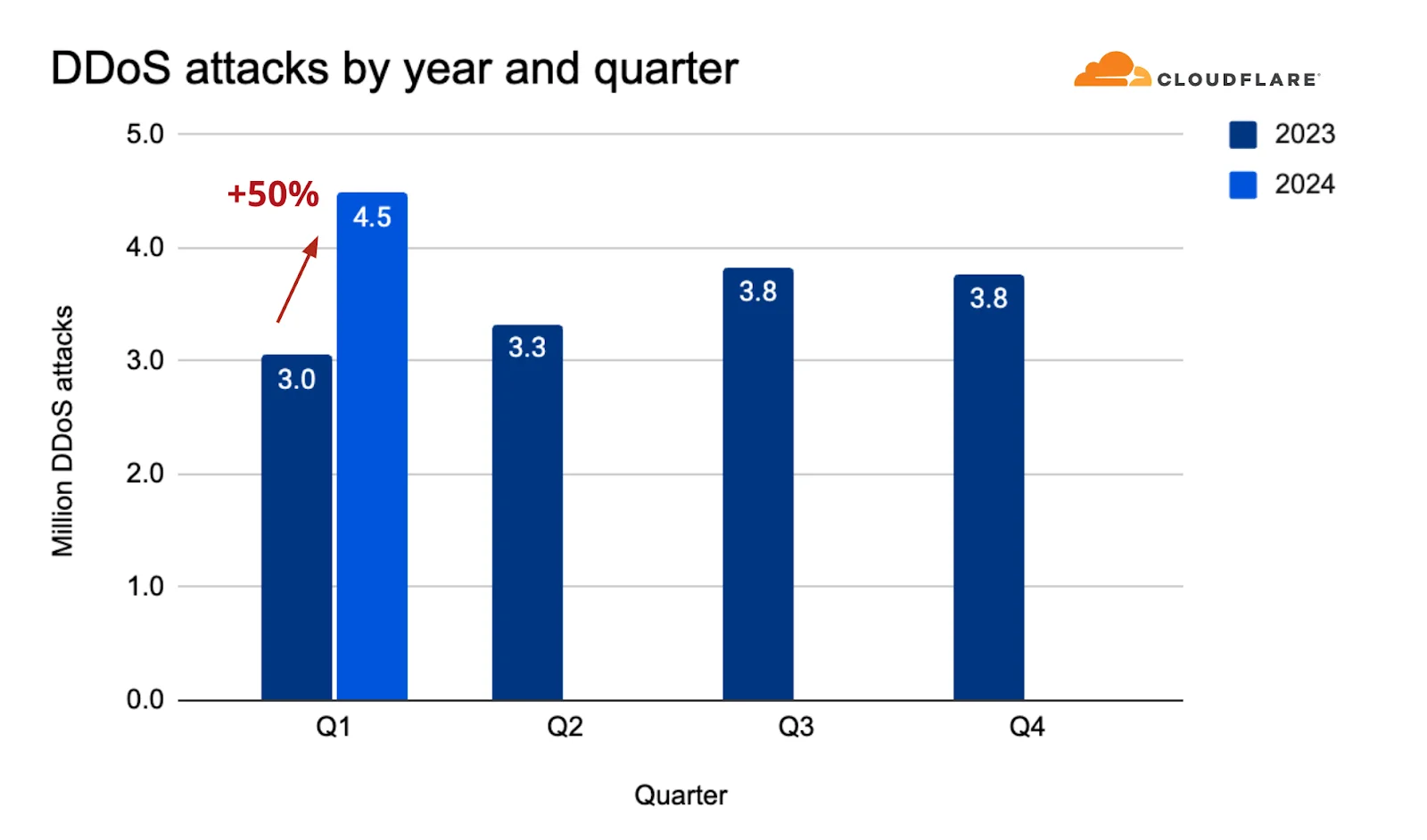
DDoS attacks increase per year and quarter (source: Cloudflare report)
DDoS attacks overwhelm network resources by flooding them with traffic, making them unable to function properly. Common targets include online shopping sites, online casinos, and any business reliant on web-based services. Financial institutions are especially vulnerable due to the high stakes involved.
Recent trends point to the involvement of powerful botnets, such as those powered by Mirai-variant malware, which have been responsible for some of the largest attacks to date. In late 2023, an attack peaked at 350 million packets per second, which was once considered record-breaking but is now becoming more common. The previous year’s rapid reset attacks that exploited HTTP/2 highlight the increasing sophistication and scale of cybersecurity threats.
DDoS Attack Trends Q1 2024
Q1 2024 saw a 29% increase in the number of DDoS attacks compared to the same period in 2023, according to DDoS-Guard. January 2024 emerged as the busiest month for Layer 7 (L7) attacks, while a significant rise in Layer 3-4 (L3/4) attacks was observed in March, surpassing the combined totals of January and February.
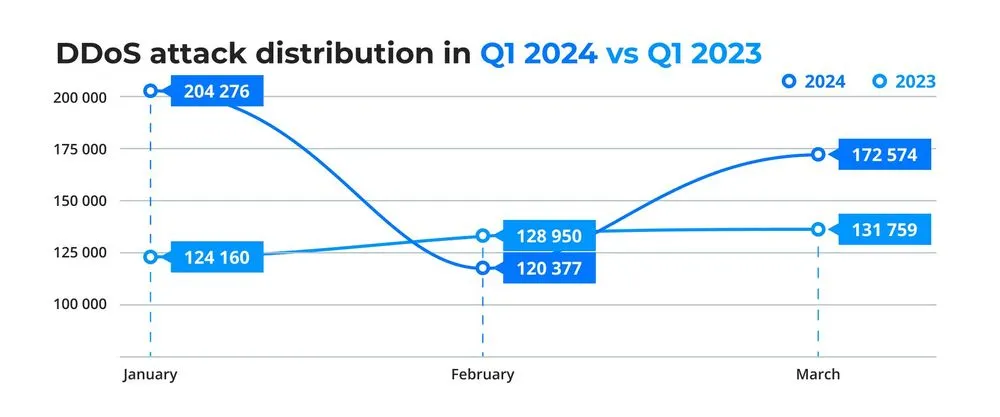
DDoS attack distribution (source: DDoS-Guard)
The power and scale of DDoS attacks continue to escalate. What were considered top-level attacks in previous years are now typical. This increase in attack volume is largely driven by compromised Internet of Things (IoT) devices. For instance, an early 2024 attack reached a peak of 350 million packets per second (PPS), a volume that was record-breaking in 2021 but is now commonplace.
Rise of Botnets
According to Qrator Q1 2024 DDoS Attacks Statistics and Overview report, the largest recorded botnet grew significantly, involving 51,400 devices, up from 16,000 in the previous quarter. However, this figure was still lower than the same period in 2023, when a botnet contained 131,628 devices.

AI illustration of Botnets
On February 19th, this extensive network launched a DDoS attack against the online betting industry, affecting entities in nine countries: Indonesia, the United States, Russia, Colombia, China, India, Brazil, the Philippines, and Germany.
Mirai-Variant Botnet Record-Breaking Attack
The largest recorded DDoS attack in Q1 2024 was a Mirai-variant botnet assault, reaching an unprecedented 2 terabits per second. This massive attack targeted an Asian hosting provider, demonstrating the increasing scale and capability of modern botnets. A noteworthy aspect of this variant is its contribution to broader attack statistics: it launches four of every 100 HTTP DDoS attacks and two of every 100 L3/4 DDoS attacks.
Recently, attackers exploited Ivanti vulnerabilities, CVE-2023-46805 and CVE-2024-21887, which manipulate crafted requests to execute malicious scripts, recruiting compromised systems into Mirai’s botnet for further nefarious activities like DDoS attacks.
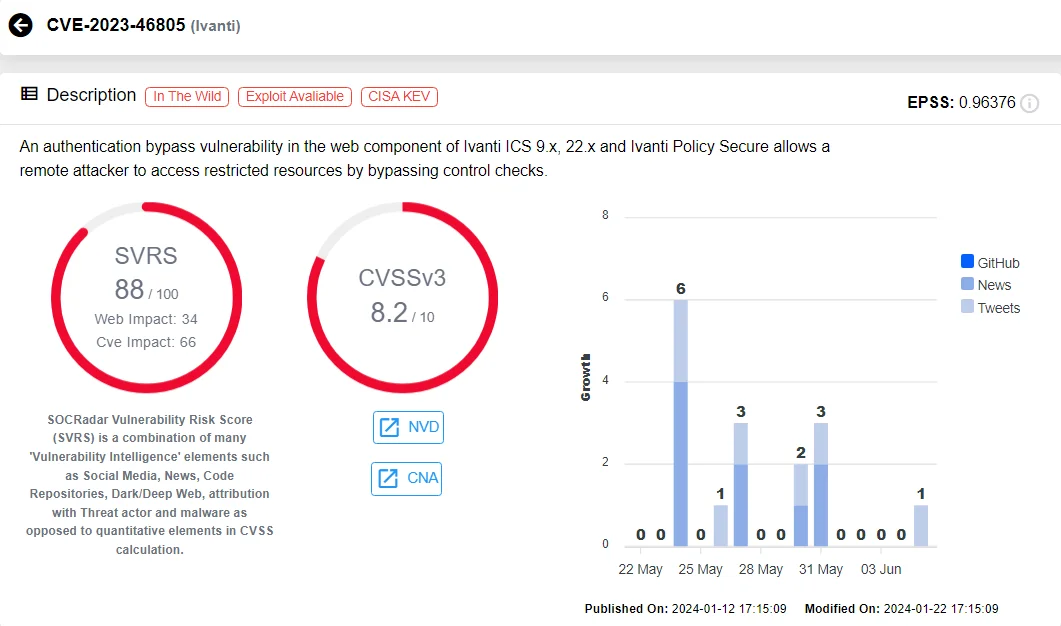
The vulnerability card of CVE-2023-46805 (SOCRadar Vulnerability Intelligence)
The Top DDoS Attack Vectors in Q1: HTTP-based Attacks Take the Lead
In Cloudflare’s DDoS Threat Report for the Q1 2024, HTTP DDoS attacks have notably become the most dominant attack vector, constituting 37% of all DDoS attacks monitored during this period. This surge underscores a strategic shift among cyber attackers who now favor exploiting the application layer by inundating web services with HTTP requests to disrupt server operations.
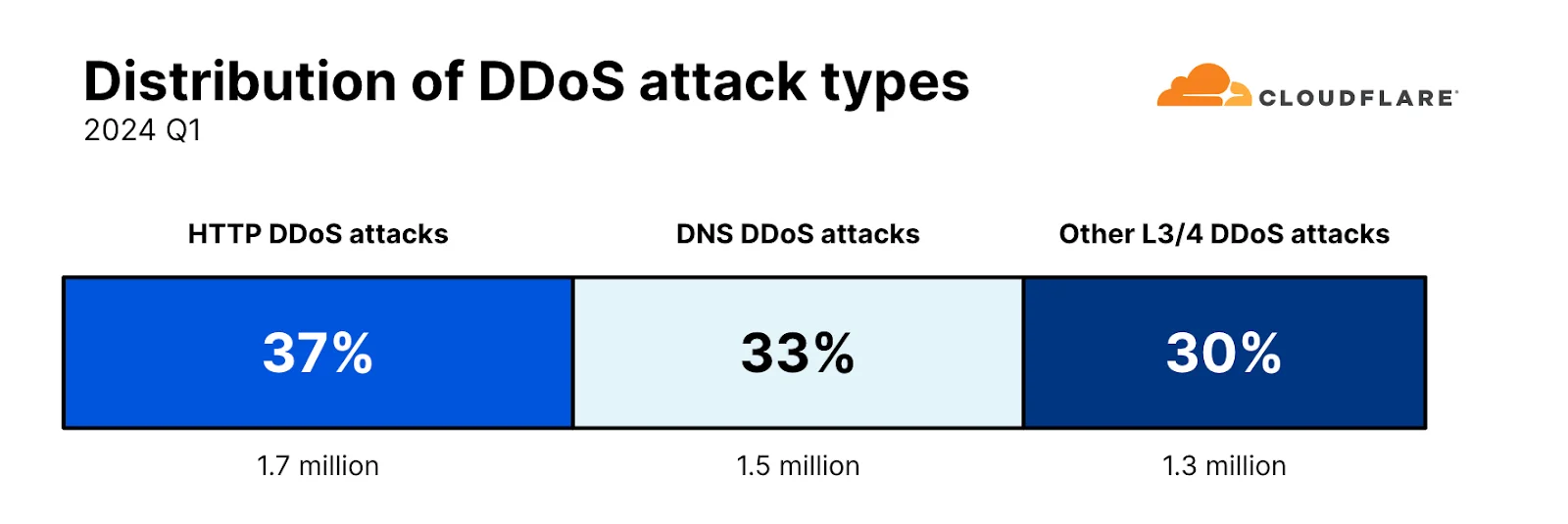
DDoS attack types according to Cloudflare report
The increasing reliance on HTTP DDoS attacks reflects their efficacy in simulating legitimate web traffic, making it challenging for defenses to screen out malicious activities without impacting normal user access. Notably, attackers have optimized their tactics to employ both GET and POST request floods, which strain server resources and render websites slow or completely unreachable for legitimate users.
The report also highlights a worrying trend of these attacks growing not only in frequency but also in sophistication, with adversaries continually adapting their methods to bypass conventional security measures. This trend necessitates advancements in web application firewalls and real-time traffic analysis to effectively mitigate the impact of these high-volume and disguised traffic attacks.
Geographical Distribution of DDoS Attacks in Q1 2024
In Q1 2024, a detailed analysis of the geographical distribution of DDoS attacks showcased distinctive trends and sources. The United States stood out as the predominant contributor, generating 20% of all HTTP DDoS attack traffic. This was followed by other significant contributors like China, Germany, Indonesia, and Brazil, each adding substantially to the global threat landscape.
At the network layer, Cloudflare’s data centers in the US were the primary recipients of over 40% of L3/4 DDoS attack traffic, indicating a high concentration of network-based threats in the region. Following the US, Germany, Brazil, Singapore, and Russia also reported significant amounts of such traffic, highlighting their roles as major targets or transit hubs for DDoS attacks, if you want to learn more about the state of cyber security in different countries, check out SOCRadar’s country reports.
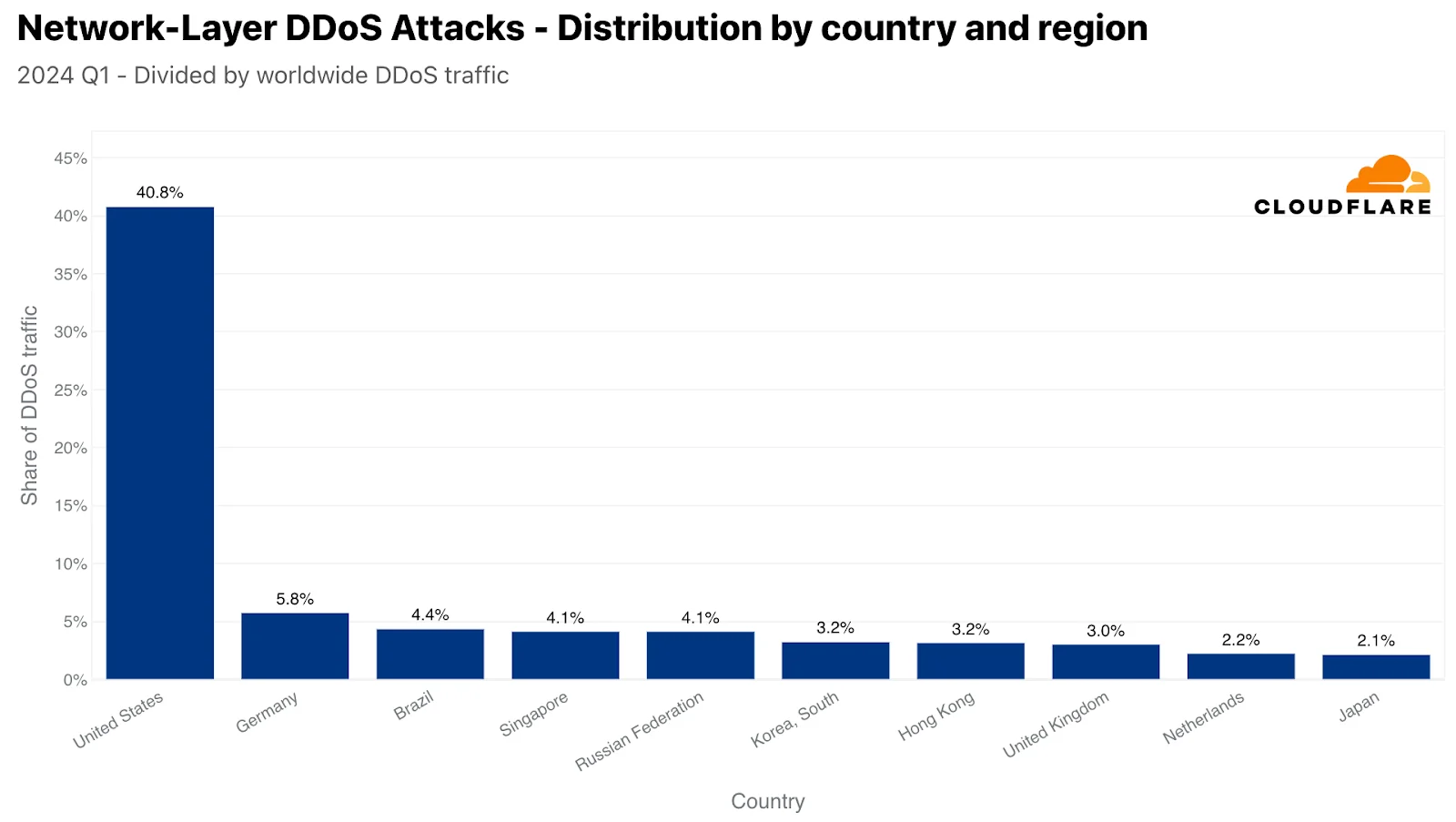
Network layer DDoS attacks distribution (source: Cloudflare report)
Interestingly, when considering the intensity of the attacks relative to the normal internet traffic, smaller countries showed disproportionate levels of DDoS activities. Gibraltar emerged as an unexpected leader in the proportion of HTTP DDoS attack traffic, while Zimbabwe topped the charts for L3/4 DDoS attacks, with an astounding 89% of its network traffic being attack-related.
Leveraging SOCRadar’s DoS Resilience
To effectively defend against DDoS attacks, understanding their operational mechanisms and the tactics commonly used by attackers is crucial. Utilize the free SOCRadar Labs-DoS Resilience tool to assess the robustness of your domain or subnet against DoS attacks. This service helps identify both strengths and vulnerabilities in your defenses. Based on the insights gained from the DoS Resiliency analysis, you can further enhance your security posture using the SOCRadar Attack Surface Management module, tailored to address your specific needs.
 SOCRadar DoS Resilience Module
SOCRadar DoS Resilience Module
For additional details on DDoS attacks and strategies for mitigation, consider visiting our blog post which provides a comprehensive overview.
Conclusion
The DDoS Threat Report from Q1 2024 paints a concerning picture of the current state of cyber threats. With HTTP-based attacks taking the forefront and botnets growing in size and sophistication, it is clear that the challenge is not just persistent but also evolving.
Leveraging tools like SOCRadar’s DoS Resilience can provide crucial insights into vulnerabilities, helping organizations fortify their defenses against these disruptive attacks. For a deeper understanding of mitigation strategies and the latest DDoS trends, exploring additional resources and staying informed through expert analyses is essential.

































