
Google’s New ZIP Domain Could Be Used for Phishing and Malware Attacks
Security researchers have found how attackers could potentially exploit the new ZIP TLD offered by Google. A new phishing toolkit uses the ZIP domain to appear legitimate and displays fake WinRAR and Windows File Explorer windows in the browser.
Google released its new TLDs in early May, which are intended to provide better representation for certain areas. However, two TLDs, .zip and .mov, pose a security risk because they are file extensions; some websites will automatically convert a string ending in “.zip” into a clickable link. Attackers can exploit this to carry out phishing schemes and distribute malware.
How Do Attackers Initiate ZIP Domain Attacks?
Attackers may use social engineering to persuade users to click it if a website can convert malicious[.]zip to a link. Once a user clicks on the link, their browser will try to open the https://malicious[.]zip site. The site may redirect users to a phishing page or prompt them to download malware.
Mr.d0x, a security researcher, has published the “File Archivers in the Browser”phishing toolkit that demonstrates these attacks on GitHub. The kit has two samples built by researchers to emulate the WinRAR file archiver software and the Windows 11 File Explorer window in the browser.
Attackers can use the toolkit or the same method to create fake WinRAR and File Explorer windows that will appear on ZIP domains to trick users into thinking they have opened a .zip file.
Capabilities of the Toolkit: File Archivers in the Browser
The researchers made the fake WinRAR window more believable by adding a fake Scan button that claims the files are safe.
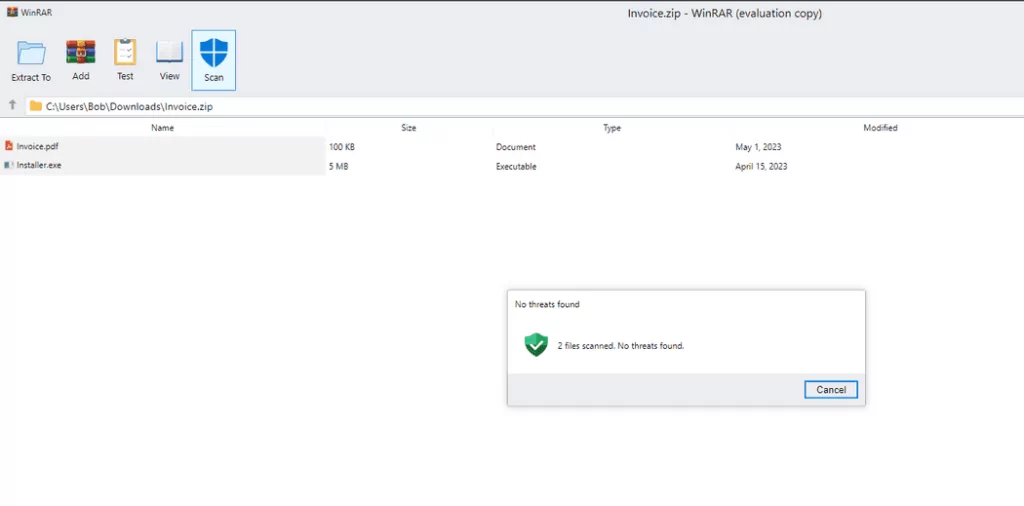
Even though the toolkit still shows the browser address bar, it can still deceive some users into thinking it is a legitimate WinRAR archive. With creative CSS and HTML, the toolkit can be further improved.
Threat actors can use this phishing toolkit to steal credentials and deliver malware. For instance, if a user clicks on a PDF file within the fake WinRAR window, they may be redirected to a page that asks for their login credentials to view the file.
Since Windows does not display file extensions by default, users will only see a PDF file icon in their downloads folder and might unknowingly double-click it, executing the malware.
An interesting aspect is how Windows searches for files and, if not found, tries to open the searched string in the file browser. This is possible because the directory address bar in Windows File Explorer can also be used to search a URL. The website will open if the string matches a legitimate domain; otherwise, Bing search results will be displayed.
By registering a ZIP domain with the same name as a common file, a malicious actor can trick Windows into opening their website when someone searches for that file.
If the website hosts the “File Archivers in the Browser” phishing kit, the user may believe that WinRAR is displaying a genuine ZIP archive.
Introducing new top-level domains (TLDs) offers attackers additional avenues for phishing. It is strongly advised that organizations block .zip and .mov domains, as they are currently being exploited for phishing and are expected to be increasingly targeted.
Strengthen Phishing Defense with SOCRadar
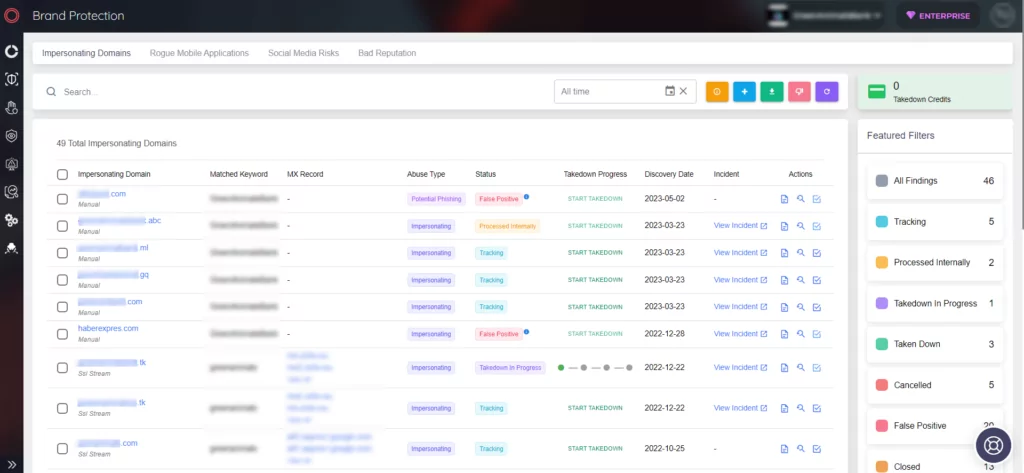
Phishing attacks can originate from various sources, irrespective of the apparent security of a website. To mitigate the impact of phishing on your company, it is vital to constantly monitor network activity and effectively manage your digital assets, minimizing the potential attack surface.
Powered by AI, SOCRadar’s Phishing Domain Detection comprehensively examines millions of domains from leading domain registrars. This proactive approach helps identify malicious domains that specifically target your brand and your entire company network.



































